- 01 August 2025 (9 messages)
-

-
 Hey 👋
Hey 👋
What was your script? It's an error from the kernel which means that your monitor is executed and applied but for some reasons the script interpreter from the VMX root-mode is not able to run the script. -
 Script i am trying to run:
Script i am trying to run:
!monitor r 0x7ff7d0159b98 l 0x8 pid 0x4030 script{
teb = $teb;
clientPid = dq(teb+0x40);
printf("\n Access_at: %llx FROM addr: %llx, rsp_return _add: %llx, TID: %d, _TEB: %llx, clientPid: %d\n",$context,@rip,poi(@rsp),$tid,$teb,clientPid);
kThread = $thread;
kProcess = dq($thread + 0x220);
printf("\n _eTHREAD/_Kthread: %llx , _KProcess/_Eprocess of acer: %llx \n",$thread,kProcess);
} -

-
 The script works for me, it shouldn't be a problem for the VMI mode too.
The script works for me, it shouldn't be a problem for the VMI mode too. -
 Is it something that happens just a few time or all of your messages are blocked by this error?
Is it something that happens just a few time or all of your messages are blocked by this error? -
 I mean if you change 'clientPid = dq(teb+0x40);' to 'clientPid = $pid;', wouldn't it solve the problem?
I mean if you change 'clientPid = dq(teb+0x40);' to 'clientPid = $pid;', wouldn't it solve the problem? -
 I think the error happens because the target address that you pass to the 'dq' function is incorrect (at least in some cases). If it's the case, could you also check the address using the 'check_address' function before 'dq'ing it?
I think the error happens because the target address that you pass to the 'dq' function is incorrect (at least in some cases). If it's the case, could you also check the address using the 'check_address' function before 'dq'ing it?
https://docs.hyperdbg.org/commands/scripting-language/functions/memory/check_addresscheck_address | HyperDbg DocumentationDescription of the 'check_address' function in HyperDbg Scripts
-
 Joined.
Joined. - 02 August 2025 (8 messages)
-
 Hi Thanks for your replies.
Hi Thanks for your replies.
This works a few times but most of the times it gets blocked. -
 I am trying to find access from all processes and not only from same process.
I am trying to find access from all processes and not only from same process. -
 Ok I shall do that . Thanks for mentioning it. I shall modify the script to add check_address before dq'ing it. 👍
Ok I shall do that . Thanks for mentioning it. I shall modify the script to add check_address before dq'ing it. 👍 -

-
 Yeah, it's not a problem with HyperDbg. HyperDbg just queries Windows about TEB and if Windows returns NULL, then nothing we can do about it.
Yeah, it's not a problem with HyperDbg. HyperDbg just queries Windows about TEB and if Windows returns NULL, then nothing we can do about it. -
 Sure.
Sure. -
 Joined.
Joined. -
 Hey,
Hey,
I added a new command for the SMI-related functionalities of triggering and reading counts of SMIs to HyperDbg. If you want to test it, you can 'git pull' the 'dev' branch.
Here's the documentation:
https://docs.hyperdbg.org/commands/extension-commands/smi
Code:
https://github.com/HyperDbg/HyperDbg/pull/538!smi (trigger and show System Management Interrupt functionalities) | HyperDbg DocumentationDescription of '!smi' command in HyperDbg.
- 10 August 2025 (4 messages)
-
 FYI, HyperDbg now saves/restores XMM registers on each VM-exit and VM-entry (the code is merged to the 'dev' branch).
FYI, HyperDbg now saves/restores XMM registers on each VM-exit and VM-entry (the code is merged to the 'dev' branch).
https://github.com/HyperDbg/HyperDbg/pull/541Save and restore XMM registers on VM-exits by SinaKarvandi · Pull Request #541 · HyperDbg/HyperDbgChanged Fix the problem with restoring XMM registers (EPTHOOK causes process instruction execution exception。 #468) (link) The 'hyperhv' project now has build optimizations enabled
-
 It will definitely have a negative influence on the overall performance of HyperDbg. Based on our previous discussions in the group, I remember Artem mentioning that there is no way to force MSVC not to use XMM registers for various optimization tasks (such as zeroing memory).
It will definitely have a negative influence on the overall performance of HyperDbg. Based on our previous discussions in the group, I remember Artem mentioning that there is no way to force MSVC not to use XMM registers for various optimization tasks (such as zeroing memory).
Therefore, it seems that this performance penalty is inevitable for us. It was also reported to cause problems for regular usage of HyperDbg when XMM registers are used:
https://github.com/HyperDbg/HyperDbg/issues/468EPTHOOK causes process instruction execution exception。 · Issue #468 · HyperDbg/HyperDbg//test.asm .CODE myFloatOperation PROC xorps xmm0,xmm0 movsd xmm0, qword ptr [rdx] movaps xmm2, xmm0 ;put it here movsd qword ptr [rcx],xmm2 ret myFloatOperation ENDP END //main.cpp EXTERN_C void m...
-
 Also, the hyperhv project originally had optimizations disabled by default. However, since we are now restoring the XMM registers, we no longer need to worry about MSVC compiler optimizations. As a result, optimizations are now enabled, which will hopefully improve overall performance and cover the performance penalty.
Also, the hyperhv project originally had optimizations disabled by default. However, since we are now restoring the XMM registers, we no longer need to worry about MSVC compiler optimizations. As a result, optimizations are now enabled, which will hopefully improve overall performance and cover the performance penalty. -
 Since this change might introduce stability or performance issues, please test it from the dev branch on your debuggee systems and let us know if you encounter any problems, so we can address them before releasing v0.15.
Since this change might introduce stability or performance issues, please test it from the dev branch on your debuggee systems and let us know if you encounter any problems, so we can address them before releasing v0.15. - 12 August 2025 (1 messages)
-
 Joined.
Joined. - 13 August 2025 (1 messages)
-
Joined.
- 14 August 2025 (9 messages)
-
 I was trying to add the support for SYSCALL emulation when Intel CET is active:
I was trying to add the support for SYSCALL emulation when Intel CET is active:
https://github.com/HyperDbg/HyperDbg/commit/cdadcfaded6b02c5711da6a49de7a510d3eaf0cdadd CET emulation for syscall extension command · HyperDbg/HyperDbg@cdadcfaState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 It seems that 'RDSSPQ' instruction is used for reading SSP:
It seems that 'RDSSPQ' instruction is used for reading SSP:
https://www.felixcloutier.com/x86/rdsspd:rdsspq -
 But on the other hand, there is RSTORSSP, which is for configuring SSP restore token:
But on the other hand, there is RSTORSSP, which is for configuring SSP restore token:
https://www.felixcloutier.com/x86/rstorssp -
 So, I'm not quite sure if using RSTORSSP is the correct way of configuring SSP. Does anybody have any experience with Intel CET who can tell us how to properly restore the SSP on SYSCALL/SYSRET emulation?
So, I'm not quite sure if using RSTORSSP is the correct way of configuring SSP. Does anybody have any experience with Intel CET who can tell us how to properly restore the SSP on SYSCALL/SYSRET emulation? -

-
 [discord] <unrustled.jimmies> HyperDBG mentioned - [defcon](https://media.defcon.org/DEF%20CON%2033/DEF%20CON%2033%20presentations/Sam%20Collins%20Marius%20Muench%20-%20Playing%20Dirty%20Without%20Cheating%20-%20Getting%20Banned%20for%20Fun%20and%20No%20Profit.pdf) talk
[discord] <unrustled.jimmies> HyperDBG mentioned - [defcon](https://media.defcon.org/DEF%20CON%2033/DEF%20CON%2033%20presentations/Sam%20Collins%20Marius%20Muench%20-%20Playing%20Dirty%20Without%20Cheating%20-%20Getting%20Banned%20for%20Fun%20and%20No%20Profit.pdf) talk
https://cdn.discordapp.com/attachments/962350355839066130/1405641210017874083/Screenshot_2025-08-14_125424.png?ex=689f90e4&is=689e3f64&hm=08859b0b1f4b5a5f45e6618bdbadaf4e2a0d64167447b12cfffc4ba13769854e& -
 👍
👍 -
 [discord] <cowtickle> [reply]: Updated slides here
[discord] <cowtickle> [reply]: Updated slides here -
 [discord] <cowtickle>
[discord] <cowtickle>
https://cdn.discordapp.com/attachments/962350355839066130/1405687248816701522/DEFCON-Slides-Version5-1.pdf?ex=689fbbc4&is=689e6a44&hm=74edcac782e8f98cc580c7b8dd469fca5dfe6af50a60558f6e2dbf23f2a51eed& - 15 August 2025 (1 messages)
-
 Great. Thanks. I know one of the authors, I reached to them for getting feedback.
Great. Thanks. I know one of the authors, I reached to them for getting feedback. - 16 August 2025 (1 messages)
-
 [discord] <unrustled.jimmies> [reply]: After doing some light reading on this, any reason handling it using VMX primitives and letting the cpu do the load on vmentry won't suffice (tigerlake+ as per https://pulsedbg.com/vmx.html) ? More work needs to be done to support CPL0 syscalls (if this is something we want to support) ie assuming all syscalls are called in UM (CPL3)
[discord] <unrustled.jimmies> [reply]: After doing some light reading on this, any reason handling it using VMX primitives and letting the cpu do the load on vmentry won't suffice (tigerlake+ as per https://pulsedbg.com/vmx.html) ? More work needs to be done to support CPL0 syscalls (if this is something we want to support) ie assuming all syscalls are called in UM (CPL3)
Emulating cet:
Disable syscall in EFER. In the #UD,
Syscall: if CET is enabled and active (IA32_U_CET) for the process doing the syscall, we `vmread` the GUEST_SSP `0x0000682a` and as per the syscall behavior set the MSR `IA32_PL3_SSP` to this value and vmwrite GUEST_SSP to 0. Set Bit 20 of VM Entry - `Load CET state`
Sysret: Read back the UM SSP from `IA32_PL3_SSP` and vmwrite GUEST_SSP with this value.
---
But, alternatively to emulating, why not re-enable syscall/sysret and MTF then disable again? Would this not work? - 17 August 2025 (51 messages)
-
Joined.
-
 Well, you're right. I test it now and it works fine! I already tested the exact same approach a few weeks ago, and it didn't work. Guess what was wrong? Looking at your explanation, luckily, you mentioned GUEST_SSP as 0x0000682a. I double checked my previous code, and I saw 0x6c2a, and this was the problem:
Well, you're right. I test it now and it works fine! I already tested the exact same approach a few weeks ago, and it didn't work. Guess what was wrong? Looking at your explanation, luckily, you mentioned GUEST_SSP as 0x0000682a. I double checked my previous code, and I saw 0x6c2a, and this was the problem:
https://github.com/HyperDbg/ia32-doc/blob/6ef251e3e58c759fda025c186ef0f44c556c14c1/out/ia32.h#L22122ia32-doc/out/ia32.h at 6ef251e3e58c759fda025c186ef0f44c556c14c1 · HyperDbg/ia32-docIA32-doc is a project which aims to put as many definitions from the Intel Manual into machine-processable format as possible - HyperDbg/ia32-doc
-
 As you can see, 'ia32-doc' that we use for our VMX and CPU-related definitions seems to have a bug in parsing value in the version that we are using in HyperDbg now.
As you can see, 'ia32-doc' that we use for our VMX and CPU-related definitions seems to have a bug in parsing value in the version that we are using in HyperDbg now. -
 I checked the newer commits (updated branch) and it seems they fixed this problem. So, I think I need to update it now.
I checked the newer commits (updated branch) and it seems they fixed this problem. So, I think I need to update it now. -
 Anyway, thank you very much @unrustled.jimmies. You saved me a lot of time. 🙏
Anyway, thank you very much @unrustled.jimmies. You saved me a lot of time. 🙏 -
 [discord] <unrustled.jimmies> 🫡
[discord] <unrustled.jimmies> 🫡 -
-
 HyperDbg v0.15 is out! ✨🎈
HyperDbg v0.15 is out! ✨🎈
This version comes with a new SMM interrupt (SMI) command, fixing issues with Intel CET emulation for SYSCALL/SYSRET on 11th Gen+ (Tiger/Rocket Lake) CPUs, also saving/restoring XMM registers on VM-exits/entries.
Check it out:
https://github.com/HyperDbg/HyperDbg/releases/tag/v0.15
More information:
https://docs.hyperdbg.org/commands/extension-commands/smi
Enhancement of the '.pe' command:
https://docs.hyperdbg.org/commands/meta-commands/.pe -
 Special thanks to @Alish014 for helping us with enhancing the '.pe' command in this release. ❤️
Special thanks to @Alish014 for helping us with enhancing the '.pe' command in this release. ❤️ -
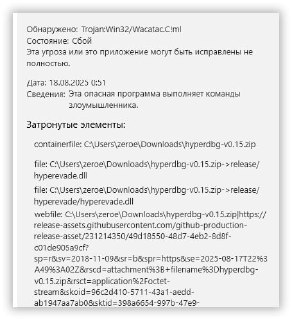
F-ck, MS Defender detect as Trojan:Win32/Wacatac.C!ml in hyperdbg-v0.15.zip
-
 No, Windows defender doesn't detect it for me.
No, Windows defender doesn't detect it for me. -
I download with Ms Edge, windows 10
-

-
 Also, VT doesn't detect it, only one random AV detects it.
Also, VT doesn't detect it, only one random AV detects it. -
 Let me check.
Let me check. -
-
 Edge is also fine for me.
Edge is also fine for me. -
 Maybe MS edge detects it only in your region. It's common that AVs detect certain files in different regions.
Maybe MS edge detects it only in your region. It's common that AVs detect certain files in different regions. -
 But luckily, VirusTotal doesn't show anything this time.
But luckily, VirusTotal doesn't show anything this time. -
ok , its only FYI
-
 For your information, we're not releasing (compiling) binaries of HyperDbg. It's automatically compiled/released from GitHub Actions based on the latest git code.
For your information, we're not releasing (compiling) binaries of HyperDbg. It's automatically compiled/released from GitHub Actions based on the latest git code. -
i download with aria2c.exe. dearch (AV detect again), but hyperdbg-cli.exe work fine.
-
 👍
👍 -
AV dont like hyperevade.dll
) -
 Ah, I see. This DLL contains anti-anti-debugging techniques (to bypass anti-debugging techniques).
Ah, I see. This DLL contains anti-anti-debugging techniques (to bypass anti-debugging techniques). -
need add to Exclude filter?
-
 Probably, they're signature matching certain strings within this DLL.
Probably, they're signature matching certain strings within this DLL. -
 Yeah, but this is a critical problem if they try to flag this DLL. Maybe in future releases, we are needed to make two separate releases (one with the 'hyperevade' project and one without the 'hyperevade' DLL). 🤔
Yeah, but this is a critical problem if they try to flag this DLL. Maybe in future releases, we are needed to make two separate releases (one with the 'hyperevade' project and one without the 'hyperevade' DLL). 🤔 -
i add all folder C:\UTILITY\HyperDBG to Exclude filter
-
thanx
-
 👍
👍 -
hyperevade.dll add some nearly? i see.. hyperdbg-v0.13.2.zip dont contain this file :)
-
 It's added from the previous version (v.0.14).
It's added from the previous version (v.0.14). -
AV detect on hyperevade.dll in hyperdbg-v0.15.zip, but dont detect in hyperdbg-v0.14.1.zip on my windows
-
 Yeah, it's weird. Maybe it's better to exclude this DLL from this release. Let me check.
Yeah, it's weird. Maybe it's better to exclude this DLL from this release. Let me check. -
 Okay, check it again.
Okay, check it again. -
one sec
-
 I temporarily disabled the 'hyperevade' project to find a good solution for it.
I temporarily disabled the 'hyperevade' project to find a good solution for it. -
now av is nothing detect
-
 Great. Thanks for reporting it.
Great. Thanks for reporting it. -
 Hey
Hey
What is the hyperevade project? -
 It's an anti-anti-debugging project for HyperDbg.
It's an anti-anti-debugging project for HyperDbg. -
 Similar to the ScyllaHide in x64dbg.
Similar to the ScyllaHide in x64dbg. -
Sina maybe sent hyperevade.dll to Microsoft for detailed check and exclude signature. I ~10 years ago sent to him and this work.
-
 This might be a good option but I think the best approach would be having two different releases (one with and one without hypervade).
This might be a good option but I think the best approach would be having two different releases (one with and one without hypervade). -
 Since this project might be flagged by other AVs as well as it contains lots of anti-debugging strings, signatures and patterns.
Since this project might be flagged by other AVs as well as it contains lots of anti-debugging strings, signatures and patterns. -
as u wish , now only MS detect :)
https://www.virustotal.com/gui/file/761d2216b7e3e04045f1239abc92507218362609b89e7425c5b065e5e6706e95?nocache=1 -
 The latest version?
The latest version? -
 Or the previous one?
Or the previous one? -
not in prev release
-
 Ah, and it's probably the most important one. 😅
Ah, and it's probably the most important one. 😅 - 18 August 2025 (25 messages)
-
 [discord] <unrustled.jimmies> [reply]: just tested the MTF method and it works fine as well, as expected.
[discord] <unrustled.jimmies> [reply]: just tested the MTF method and it works fine as well, as expected.
#UD + !MTF_pending -> Enable EFER.SCE, set MTF, set pending flag
MTF + MTF_pending -> Disable EFER.SCE, clear MTF, clear pending (success)
#UD + MTF_pending -> Disable EFER.SCE, clear MTF, clear pending, inject #UD (failed, genuine ud opcode) )
each method has its pros and cons.
https://cdn.discordapp.com/attachments/962350355839066130/1406844152800346112/Screenshot_2025-08-17_203313.png?ex=68a3f137&is=68a29fb7&hm=85547d151bd128f68f7e4b3a9d7cfcad371d8621bf99c4606068872621277581& -
 Yes, it's possible but the problem with this approach is that it's significantly slower. The current implementation handles SYSCALL/SYSRET each with a single VM-exit, but re-enabling the SYSCALL needs two VM-exits (one for #UD and one for MTF).
Yes, it's possible but the problem with this approach is that it's significantly slower. The current implementation handles SYSCALL/SYSRET each with a single VM-exit, but re-enabling the SYSCALL needs two VM-exits (one for #UD and one for MTF). -
 Given that the rate of SYSCALL/SYSRET execution in the system is very high, implementing it this way could have a catastrophic impact on system performance.
Given that the rate of SYSCALL/SYSRET execution in the system is very high, implementing it this way could have a catastrophic impact on system performance. -
 If you see the documentation for the '!syscall' command, we suggested an alternative method for intercepting SYSCALLs (only) and not intercepting SYSRETs for performance reasons:
If you see the documentation for the '!syscall' command, we suggested an alternative method for intercepting SYSCALLs (only) and not intercepting SYSRETs for performance reasons:
https://docs.hyperdbg.org/commands/extension-commands/syscall#alternative-method-for-syscall-interception!syscall, !syscall2 (hook system-calls) | HyperDbg DocumentationDescription of '!syscall, !syscall2' commands in HyperDbg.
-
 [discord] <unrustled.jimmies> yep makes sense, the emulation path is a better choice.
[discord] <unrustled.jimmies> yep makes sense, the emulation path is a better choice.
Just had a quick question on this - https://github.com/HyperDbg/HyperDbg/blob/9bd5ffc7b9644df4d00aef2e6590d46a55d9837b/hyperdbg/hyperhv/code/hooks/syscall-hook/EferHook.c#L347
Have you experienced the case where you got a #UD for a syscall (or any) instruction being tried to execute but it wasn't paged when you tried to read the instruction bytes (even if it was a usermode address)?HyperDbg/hyperdbg/hyperhv/code/hooks/syscall-hook/EferHook.c at 9bd5ffc7b9644df4d00aef2e6590d46a55d9837b · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 Hey.
Hey.
Yes, I remember after some time (let's say 1 hour) it crashes if we didn't inject #PF. But, it was years ago, I'm not sure if still at Win 11 24h2 the similar behavior still happens or not. -
 I'm not sure what the reason was for this page fault, it's a bit weird since if the SYSCALL is executed, then it should already be available in the RAM, so having a #PF at this stage is not reasonable for me. But, maybe the #UD is because of something else (anything other than the SYSCALL itself), but I didn't check. Reproducing it is a bit hard, as it might not happen for even 6 hours.
I'm not sure what the reason was for this page fault, it's a bit weird since if the SYSCALL is executed, then it should already be available in the RAM, so having a #PF at this stage is not reasonable for me. But, maybe the #UD is because of something else (anything other than the SYSCALL itself), but I didn't check. Reproducing it is a bit hard, as it might not happen for even 6 hours. -
 [discord] <unrustled.jimmies> got it.
[discord] <unrustled.jimmies> got it.
makes sense if it happens due to/the cause is at a higher level, i was just wondering if this was due to some weird edge case at the cpu level but after looking at the prioritization of concurrent events 7.9 3a (#PF has higher priority than #UD) and 7.15 3a `this exception is not generated until an attempt is made to retire the result of executing an invalid instruction; that is, decoding and speculatively attempting to execute an invalid opcode does not generate this exception`, it feels like this shouldn't happen due to cpu reasons (ie instruction cache, instructions spanning page boundary where one is present and one isnt etc). -
Joined.
-

-
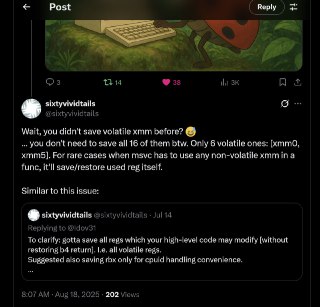
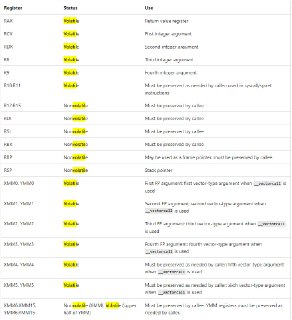
 Interesting tweet. I didn't know about volatile/non-volatile XMM regs. So, I think this will help us a lot to only save/restore first 6 XMM regs.
Interesting tweet. I didn't know about volatile/non-volatile XMM regs. So, I think this will help us a lot to only save/restore first 6 XMM regs. -
 x64 ABI conventions
x64 ABI conventionsLearn more about: x64 ABI conventions
-

-
 I think we've mentioned that before
I think we've mentioned that before -
 👍
👍 -
 I think MSVC doesn't use YMM regs. Am I right? 🤔
I think MSVC doesn't use YMM regs. Am I right? 🤔 -
 So, only saving/restoring XMM0-5 is should be enough.
So, only saving/restoring XMM0-5 is should be enough. -
 Not sure as per ABI, it's just XMM is a lower part of YMM and ZMM registers
Not sure as per ABI, it's just XMM is a lower part of YMM and ZMM registers -
Joined.
-
 [discord] <unrustled.jimmies> [reply]: in addition to the abi pov we also need to consider from a hooking pov as well if folks want to read/modify any of the 16 xmm registers in their !epthook (in that case we'll need to save/restore all 16).
[discord] <unrustled.jimmies> [reply]: in addition to the abi pov we also need to consider from a hooking pov as well if folks want to read/modify any of the 16 xmm registers in their !epthook (in that case we'll need to save/restore all 16). -
 But we don't support modifying XMM registers within script engine. So, basically only MSVC touches XMM registers which if they restore nonvolatile registers properly, then I couldn't think of a state where we need to save/restore all XMM registers.
But we don't support modifying XMM registers within script engine. So, basically only MSVC touches XMM registers which if they restore nonvolatile registers properly, then I couldn't think of a state where we need to save/restore all XMM registers. -
 Can you think of a scenario where we are needed to save and restore all of them?
Can you think of a scenario where we are needed to save and restore all of them? -
 [discord] <unrustled.jimmies> [reply]: can't think of anything atm. for hooking, if we don't support it and its not something to be added, based on reading the abi convention doc, it seems like saving 0-5 is all thats needed.
[discord] <unrustled.jimmies> [reply]: can't think of anything atm. for hooking, if we don't support it and its not something to be added, based on reading the abi convention doc, it seems like saving 0-5 is all thats needed.
anything using 6-15 should save and restore it internally and 0-5 will be handled by AsmVmexitHandler. In the case where the guest was using 256/512 width regs at the point of vmexit, the upper bits shouldn't be touched and thus dont need to be saved/restored as well. -
 [discord] <unrustled.jimmies> actually i see ymm0-5 is also part of the abi as volatile so technically they should be saved as well lol but at this point it might be better to verify hyperhv never uses those registers in vmexits and thus dont save/restore it.
[discord] <unrustled.jimmies> actually i see ymm0-5 is also part of the abi as volatile so technically they should be saved as well lol but at this point it might be better to verify hyperhv never uses those registers in vmexits and thus dont save/restore it. -
 Yeah, I applied the patch. You can check my modifications here:
Yeah, I applied the patch. You can check my modifications here:
https://github.com/HyperDbg/HyperDbg/commit/c655a7705e04373f4dd1bf459bc8660691e26925avoid saving and restoring nonvolatile XMM registers · HyperDbg/HyperDbg@c655a77State-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
- 19 August 2025 (3 messages)
-
 Joined.
Joined. -
Joined.
-
- 20 August 2025 (23 messages)
-
 Hi,
Hi,
Sorry, I don’t know much about hypervisors.
I have two questions:
First, is it possible to hook instructions like xgetbv with a hypervisor?
Second, for frequently accessed memory regions like KUSER_SHARED_DATA, is it possible to set up a memory hook to see where it’s being read from? Whenever I try that, the program just crashes. -
 Hey,
Hey,
HyperDbg doesn't have an event command for detecting xsetbv instructions but you can just put your code here and recompile HyperDbg if you want to detect/change the execution of XSETBV:
https://github.com/HyperDbg/HyperDbg/blob/9bd5ffc7b9644df4d00aef2e6590d46a55d9837b/hyperdbg/hyperhv/code/vmm/vmx/CrossVmexits.c#L21HyperDbg/hyperdbg/hyperhv/code/vmm/vmx/CrossVmexits.c at 9bd5ffc7b9644df4d00aef2e6590d46a55d9837b · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 For the second question, you can use HyperDbg's !monitor command along with the @rip, which shows the location where it tries to read/write, and $context contains the address that is being read or modified:
For the second question, you can use HyperDbg's !monitor command along with the @rip, which shows the location where it tries to read/write, and $context contains the address that is being read or modified:
https://docs.hyperdbg.org/commands/extension-commands/monitor!monitor (monitor read/write/execute to a range of memory) | HyperDbg DocumentationDescription of the '!monitor' command in HyperDbg.
-
 Check this example:
Check this example:
https://youtu.be/PX38N5F3SL8?t=242Dbg3301: HyperDbg 05 03 Memory MonitorView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
 [discord] <unrustled.jimmies> [reply]: Hey man, i totally forgot i added this to my build of hyperdbg a while ago since i needed to hook this as well but you just reminded me. here is the patch if you want it. It should work with something like the following
[discord] <unrustled.jimmies> [reply]: Hey man, i totally forgot i added this to my build of hyperdbg a while ago since i needed to hook this as well but you just reminded me. here is the patch if you want it. It should work with something like the following
https://pastebin.com/r5Lh9M47
```
!xsetbv script {
printf("method:xsetbv, pname: %s, pid: %x, tid: %x, rip: %llx, context: %x, eax: %x, ebx: %x, ecx: %x, edx: %x\n",
$pname, $pid, $tid, @rip, $context, @eax, @ebx, @ecx, @edx);
}
```diff --git a/hyperdbg/hyperhv/code/interface/Dispatch.c b/hyperdbg/hyperhv/code/ - Pastebin.comPastebin.com is the number one paste tool since 2002. Pastebin is a website where you can store text online for a set period of time.
-
 I believe they were asking about xgetbv though. And unfortunately there is no dedicated vmexit for that instruction
I believe they were asking about xgetbv though. And unfortunately there is no dedicated vmexit for that instruction -
 And don't worry, we don't know much about hypervisors either
And don't worry, we don't know much about hypervisors either -
 [discord] <unrustled.jimmies> [reply]: ah yeah.
[discord] <unrustled.jimmies> [reply]: ah yeah.
i also wanted to check with you, your ARL nuc didnt support vt-rp/hlat right - https://pulsedbg.com/vmx.html It seems like my 285k doesn't as well. could be a fw issue since i see it has support for it on the ark page. -
 Interesting, I blamed my ARL CPU for being some sort of stripped down mobile version.
Interesting, I blamed my ARL CPU for being some sort of stripped down mobile version.
I can check on that issue with my colleagues. -
 Actually, my CPU is not advertised as HLAT compatible. I'll ask about yours.
Actually, my CPU is not advertised as HLAT compatible. I'll ask about yours. -
 Hey,
Hey,
That would be a great addition. I applied your changes into a new branch. Check this one:
https://github.com/HyperDbg/HyperDbg/tree/xsetbvGitHub - HyperDbg/HyperDbg at xsetbvState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 [discord] <unrustled.jimmies> [reply]: feel free to steal it, i just can't send it myself for the reasons we discussed in dms 🙂
[discord] <unrustled.jimmies> [reply]: feel free to steal it, i just can't send it myself for the reasons we discussed in dms 🙂 -
 👍
👍 -
 I'm not quite familiar with XSETBV/XGETBV and the way that they modify XCR. What kind of situation might it be useful? Is it for detecting modification in Shadow Stacks?
I'm not quite familiar with XSETBV/XGETBV and the way that they modify XCR. What kind of situation might it be useful? Is it for detecting modification in Shadow Stacks? -
 [discord] <unrustled.jimmies> [reply]: Its more used to detect hypervisors like cpuid/rdtsc as far as im aware since its an unconditional vm exit. not aware of any actual purpose functionality wise (in the context of HVs). as an actual x86 instruction, yeah i never really looked into it from this angle.
[discord] <unrustled.jimmies> [reply]: Its more used to detect hypervisors like cpuid/rdtsc as far as im aware since its an unconditional vm exit. not aware of any actual purpose functionality wise (in the context of HVs). as an actual x86 instruction, yeah i never really looked into it from this angle. -
 oh, okay 👍
oh, okay 👍 -
 xgetbv is used to detect which extended features are currently enabled, accessible right from the usermode
xgetbv is used to detect which extended features are currently enabled, accessible right from the usermode -
 f.e. avx512 may be implemented and show up in cpuid, but disabled in xcr0
f.e. avx512 may be implemented and show up in cpuid, but disabled in xcr0 -
 xsetbv is for the os to enable or disable certain extended features
xsetbv is for the os to enable or disable certain extended features -
 Oh, okay. Thanks for the explanation.
Oh, okay. Thanks for the explanation. -
 I think for HyperDbg it would be more of detecting anti-hypervisor methods.
I think for HyperDbg it would be more of detecting anti-hypervisor methods. -
 [discord] <unrustled.jimmies> [reply]: Hey, i totally forgot, i had to patch pulsedbg as well for xsetbv (it wasn't detecting it as a handled vmexit (even tho it did try to handle it so not sure why) so i just patched out the check that errored out if the vmexit was unhandled). this was just a quick thing i was testing that i never got back to (i can try to repro if you want).
[discord] <unrustled.jimmies> [reply]: Hey, i totally forgot, i had to patch pulsedbg as well for xsetbv (it wasn't detecting it as a handled vmexit (even tho it did try to handle it so not sure why) so i just patched out the check that errored out if the vmexit was unhandled). this was just a quick thing i was testing that i never got back to (i can try to repro if you want).
https://cdn.discordapp.com/attachments/962350355839066130/1407862866396315759/Screenshot_2025-08-20_155944.png?ex=68a7a5f8&is=68a65478&hm=9265daec18a0cfff7d394427ea58918b942d6d7f48abbbc5cd656a16f36c18df& -
 Thanks for the finding, I'll check that one
Thanks for the finding, I'll check that one - 21 August 2025 (34 messages)
-
Joined.
-
Hello, HyperDbg is something really great that I’ve just started exploring. I know it always tries hard to hide itself, such as against anti-hypervisor techniques. I have a question: if an anti-cheat software also needs to use VT-x, does that mean I can’t use HyperDbg anymore? Can’t they coexist?
-
 [discord] <unrustled.jimmies> [reply]: I took a quick look into this.
[discord] <unrustled.jimmies> [reply]: I took a quick look into this.
I think you just need to validate the XCR as per the SDM. (in this sample case xcr is 0x7FFFFFFF). But since you execute xsetbv within the context of a #GP/#UD handler that just skips over the bytes of the instruction to a function that returns an error code, you could use that as the signal whether to re-inject a #UD/#GP into the guest as well instead of emulating all the checks.
https://cdn.discordapp.com/attachments/962350355839066130/1407992966198464584/Screenshot_2025-08-21_001447.png?ex=68a81f22&is=68a6cda2&hm=8c4513041963856cf677ed69157183e043d366093ee49aa7cc0197947c4c50bc& -
 [discord] <territory3351> Excuse me, what should I pay attention to when using BroadcastChangeAllMsrBitmapWriteAllCores(DEBUGGER_EVENT_MSR_READ_OR_WRITE_ALL_MSRS)? Why does it have a blue screen in the physical machine?
[discord] <territory3351> Excuse me, what should I pay attention to when using BroadcastChangeAllMsrBitmapWriteAllCores(DEBUGGER_EVENT_MSR_READ_OR_WRITE_ALL_MSRS)? Why does it have a blue screen in the physical machine? -
 [discord] <unrustled.jimmies> [reply]: blue screen? you must not be on the latest windows update 😛
[discord] <unrustled.jimmies> [reply]: blue screen? you must not be on the latest windows update 😛
i hope you enabled full kernel memory dumps. are you able to open it it in windbg and see what !analyze says? -
 [discord] <honorary_bot> [reply]: Thanks, but it's exactly how it is implemented now. Interestingly, I don't see any way for the function to return any status != 0, which would trigger the Unhandled Exit fatal
[discord] <honorary_bot> [reply]: Thanks, but it's exactly how it is implemented now. Interestingly, I don't see any way for the function to return any status != 0, which would trigger the Unhandled Exit fatal -
 [discord] <unrustled.jimmies> [reply]: This is just what im seeing. It skips over 7 or 18 bytes for GP or UD. 7 and 18 bytes are exactly these 2 functions.
[discord] <unrustled.jimmies> [reply]: This is just what im seeing. It skips over 7 or 18 bytes for GP or UD. 7 and 18 bytes are exactly these 2 functions.
https://cdn.discordapp.com/attachments/962350355839066130/1407996592014884886/Screenshot_2025-08-21_005413.png?ex=68a82282&is=68a6d102&hm=53ddadba450c7c2468e7752ee3f6f943d0ab86d71521c379905dffce06f5c90b& -
 [discord] <honorary_bot> Right, this is the way to detect what exception has occured
[discord] <honorary_bot> Right, this is the way to detect what exception has occured -
 [discord] <unrustled.jimmies> yeah this is weird.
[discord] <unrustled.jimmies> yeah this is weird. -
 [discord] <honorary_bot>
[discord] <honorary_bot>
https://cdn.discordapp.com/attachments/962350355839066130/1407996932328128522/image.png?ex=68a822d3&is=68a6d153&hm=297fe25b32426e1ce78f337911e08eab74d69b3622845dece066e69a97d5ccd1& -
 [discord] <unrustled.jimmies> i wonder if it happens in the debug build.
[discord] <unrustled.jimmies> i wonder if it happens in the debug build. -
 [discord] <honorary_bot> So you're saying I can repro that by executing xsetbv with 0x7FFFFFFFFFFFF ? While in Windows?
[discord] <honorary_bot> So you're saying I can repro that by executing xsetbv with 0x7FFFFFFFFFFFF ? While in Windows? -
 [discord] <unrustled.jimmies> yeah, try it and see.
[discord] <unrustled.jimmies> yeah, try it and see. -
 [discord] <honorary_bot> Okay, huge thanks for doing my job while I was sleeping 🙂
[discord] <honorary_bot> Okay, huge thanks for doing my job while I was sleeping 🙂 -
 HyperDbg doesn't support nested-virtualization. You could run HyperDbg on a nested virtualization environment like VMware but HyperDbg itself doesn't allow you to have another hypervisor.
HyperDbg doesn't support nested-virtualization. You could run HyperDbg on a nested virtualization environment like VMware but HyperDbg itself doesn't allow you to have another hypervisor. -
ok,thanks ,I learn a lot from Hypervisor From Scratch ,you explained very detail,thank you!!
-
 Glad it helped! 👍
Glad it helped! 👍 -
 [discord] <unrustled.jimmies> [reply]: are the `check results` getting optimized away and its just going to advance rip and then returning status which would be a negative value?
[discord] <unrustled.jimmies> [reply]: are the `check results` getting optimized away and its just going to advance rip and then returning status which would be a negative value? -
 [discord] <territory3351> [reply]: In Windows 10 22h2 19045.5956 version, calling BroadcastChangeAllMsrBitmapReadAllCores does not crash, but BroadcastChangeAllMsrBitmapWriteAllCores does. Thank you for helping me.
[discord] <territory3351> [reply]: In Windows 10 22h2 19045.5956 version, calling BroadcastChangeAllMsrBitmapReadAllCores does not crash, but BroadcastChangeAllMsrBitmapWriteAllCores does. Thank you for helping me.
https://cdn.discordapp.com/attachments/962350355839066130/1408003169287409684/image.png?ex=68a828a2&is=68a6d722&hm=6e9cdcb0fa50593e06a14c3ac80688f4ba35f3aa15198895f748051f6c3a395d&
https://cdn.discordapp.com/attachments/962350355839066130/1408003169770012783/image.png?ex=68a828a3&is=68a6d723&hm=bd81e70c367e68ecfa7e4504f778dd16dc0d3f9f87cb5409faf74b70141d2a95& -
 [discord] <honorary_bot> [reply]: Yes, it is partially a problem. Have you stepped through xsetbv while in frozen state?
[discord] <honorary_bot> [reply]: Yes, it is partially a problem. Have you stepped through xsetbv while in frozen state? -
 [discord] <unrustled.jimmies> nope, i can try now
[discord] <unrustled.jimmies> nope, i can try now -
 So, it does indeed optimize out a critical piece of the handler. And I probably understand why. I think there is a major oversight in my root vm exit handler. That’s a big one to catch, thank you!
So, it does indeed optimize out a critical piece of the handler. And I probably understand why. I think there is a major oversight in my root vm exit handler. That’s a big one to catch, thank you! -
 [discord] <unrustled.jimmies> [reply]: im guessing the compiler cant make the connection that the RIP can be made to return those 2 negative values since it happens in the #GP. all it sees is it could return 0.
[discord] <unrustled.jimmies> [reply]: im guessing the compiler cant make the connection that the RIP can be made to return those 2 negative values since it happens in the #GP. all it sees is it could return 0. -
 [discord] <unrustled.jimmies> my concern is where else is this happening.
[discord] <unrustled.jimmies> my concern is where else is this happening. -
 Yes, that’s my concern as well
Yes, that’s my concern as well -
 Same here. Gotta load IDA and investigate every piece of code with exception handlers
Same here. Gotta load IDA and investigate every piece of code with exception handlers -
 [discord] <unrustled.jimmies> [reply]: good luck!
[discord] <unrustled.jimmies> [reply]: good luck! -
 [discord] <territory3351> Writemsr 0x80B will cause a crash. Why doesn't MsrHandleWrmsrVmexit use TestBit to filter MSR exceptions like MsrHandleRdmsrVmexit does?
[discord] <territory3351> Writemsr 0x80B will cause a crash. Why doesn't MsrHandleWrmsrVmexit use TestBit to filter MSR exceptions like MsrHandleRdmsrVmexit does?
https://cdn.discordapp.com/attachments/962350355839066130/1408010078316924978/image.png?ex=68a82f12&is=68a6dd92&hm=e4cdfc051fbb1bc81e2a9c8cd3d3b9b413e5142ee90c2dd9ada8fd80f7ff14d1& -
 [discord] <unrustled.jimmies> [reply]: x2apic and vmexiting on all MSRs sounds like a recipe for disaster especially when it does the real wrmsr in vmx root with a custom IDT.
[discord] <unrustled.jimmies> [reply]: x2apic and vmexiting on all MSRs sounds like a recipe for disaster especially when it does the real wrmsr in vmx root with a custom IDT. -
 [discord] <territory3351> [reply]: Yeah, it gives me a headache.😩
[discord] <territory3351> [reply]: Yeah, it gives me a headache.😩 -
 [discord] <honorary_bot> Good morning, @unrustled.jimmies !
[discord] <honorary_bot> Good morning, @unrustled.jimmies !
I figured out what was going on with my xsetbv handler. And it's not the compiler. It's me, as usual. It all started when I decided that I need to regroup my status codes for consistency with PulseEng library. I changed status codes almost a YEAR ago. It turns out that I failed to update status codes in my asm routines, so they were still spitting old status codes that would not match with C code anymore. The xsetbv handler was OK all along, it was just taking unexpected status values from AsmXsetbv proc.
With that said, do you mind checking the fix whenever convenient for you?
https://pulsedbg.com/files/test/uj.zip -
 [discord] <unrustled.jimmies> [reply]: hey, thats great news. i can test the fix.
[discord] <unrustled.jimmies> [reply]: hey, thats great news. i can test the fix. -
 [discord] <rayanfam> @unrustled.jimmies The code you sent is now merged to the 'dev' branch: https://github.com/HyperDbg/HyperDbg/pull/547Xsetbv by SinaKarvandi · Pull Request #547 · HyperDbg/HyperDbg
[discord] <rayanfam> @unrustled.jimmies The code you sent is now merged to the 'dev' branch: https://github.com/HyperDbg/HyperDbg/pull/547Xsetbv by SinaKarvandi · Pull Request #547 · HyperDbg/HyperDbgAdded The !xsetbv event command is added to execution of XSETBV instruction thanks to HyperDbg group members (link) Changed Relocate extension command files into their corresponding VS directory
-
 [discord] <rayanfam> and the documentation page is here: https://docs.hyperdbg.org/commands/extension-commands/xsetbv!xsetbv (hook XSETBV instruction execution) | HyperDbg Documentation
[discord] <rayanfam> and the documentation page is here: https://docs.hyperdbg.org/commands/extension-commands/xsetbv!xsetbv (hook XSETBV instruction execution) | HyperDbg DocumentationDescription of the '!xsetbv' command in HyperDbg.
- 22 August 2025 (1 messages)
-
Joined.
- 25 August 2025 (1 messages)
-
- 28 August 2025 (1 messages)
-
- 30 August 2025 (4 messages)
-
Can this tool be used to monitor memory reading and writing? I want to analyze which address of the game was changed by a cheating program.
-
 !monitor (monitor read/write/execute to a range of memory) | HyperDbg Documentation
!monitor (monitor read/write/execute to a range of memory) | HyperDbg DocumentationDescription of the '!monitor' command in HyperDbg.
-
cool
-
 It's a bit tricky. If the modification rate is too high, it might make the system unresponsive and slow it down. But in general, you can put a monitor hook on the entire buffer address range, no matter how big it is.
It's a bit tricky. If the modification rate is too high, it might make the system unresponsive and slow it down. But in general, you can put a monitor hook on the entire buffer address range, no matter how big it is. - 31 August 2025 (2 messages)
-

-
 @getting458 Let's try to keep the discussions on-topic to benefit everyone here. Appreciate your understanding!
@getting458 Let's try to keep the discussions on-topic to benefit everyone here. Appreciate your understanding!