- 01 November 2023 (7 messages)
-
I just noticed the version of WDK and SDK updated recently
-
compiler still outputs the binary files, but ApiValidator returns error code
-
🤔
-
 Did you update it manually? 🤨
Did you update it manually? 🤨
By default, it's up to the latest version in HyperDbg -
yes, I had changed
-
I guess the problem is that my host os version does not update to win 11
-
- 03 November 2023 (1 messages)
-
 https://github.com/HyperDbg/HyperDbg/pull/297
https://github.com/HyperDbg/HyperDbg/pull/297
This is an incredibly significant contribution, @xmaple555. Hats off really. 👍👍👌Update string as parameter for string functions in script engine by xmaple555 · Pull Request #297 · HyperDbg/HyperDbgDescription strlen ? { if(strlen("12345") == 5){ printf("%d", strlen("12345")); } } strcmp !epthook ntwritefile script { if (strcmp("Notepad.exe",$pnam...
- 06 November 2023 (20 messages)
-
can we replace string with wstring for the related command functions ? I want to support wstring for script engine, but I noticed there are a lot of functions involved to be changed
-
 Hi,
Hi,
What do you mean by realted command functions? What kind of functions? 🤨 -
like HyperDbgCheckMultilineCommand
-
HyperDbg/hyperdbg/hyperdbg-cli/hyperdbg-cli.cpp at 94dba4945533a9ad2feb78da5734636ebcacecf6 · HyperDbg/HyperDbg
State-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
change string to wstring
-
 Yep, you can change it. That's a good idea. Up until December I have the plan of fixing all warnings (and enable treat warnings as error) in HyperDbg, so probably I need to re-test every functionality, thus, I will re-test script engine as well.
Yep, you can change it. That's a good idea. Up until December I have the plan of fixing all warnings (and enable treat warnings as error) in HyperDbg, so probably I need to re-test every functionality, thus, I will re-test script engine as well. -
 And also, if everything goes well, we will release a new version of HyperDbg in the coming days to support applying events instantly.
And also, if everything goes well, we will release a new version of HyperDbg in the coming days to support applying events instantly. -
 Which mean, HyperDbg no longer continues the debuggee for some time to apply events and all the events like !epthook, !monitor, !syscall, etc. will be applied instantly thus preserve the system state (context).
Which mean, HyperDbg no longer continues the debuggee for some time to apply events and all the events like !epthook, !monitor, !syscall, etc. will be applied instantly thus preserve the system state (context). -
 This one would be huge step in the project timeline. Because it's known to be the worst design issue of HyperDbg which will be fixed soon. 😎
This one would be huge step in the project timeline. Because it's known to be the worst design issue of HyperDbg which will be fixed soon. 😎 -
-
how about only support English character for wide string for now?
-
because it needs to change a lot of code to support other language
-
🙃
-
 Do you mean that you want to keep it as it is for now? Because right now it supports ASCII characters. Or any special change?
Do you mean that you want to keep it as it is for now? Because right now it supports ASCII characters. Or any special change? -
what I meant is if we need to do like this
? {
if(wcscmp(L"中文",$pname) == 0){
printf("the two strings are same");
}else {
printf("the two strings are not same");
}
} -
 Got it, but is it even possible to support this without supporting the entire wsting? 🤔
Got it, but is it even possible to support this without supporting the entire wsting? 🤔 -
yes there is wstring version of memcpy function
-
 You mean that cannot support sth like this right now:
You mean that cannot support sth like this right now:
? {
if(strcmp(L"中文",$pname) == 0){
printf("the two strings are same");
}else {
printf("the two strings are not same");
}
}
but if user specifies a buffer that has a wide-char string, then it is supported.
Am I get it correctly? -
only supported for English alphabet
? {
if(wcscmp(L"only English",$pname) == 0){
printf("the two strings are same");
}else {
printf("the two strings are not same");
}
} -
 Yes. That would be okay. 👍
Yes. That would be okay. 👍 - 07 November 2023 (1 messages)
-

- 08 November 2023 (43 messages)
-
 Hello!
Hello!
https://www.youtube.com/watch?v=idFUiURTUr4
Above are my results for the past week, it remains to finish some things and that's it. -
 @Nitr0_G Made this initial GUI for HyperDbg, and RedDbg. Here's the very first demo. Let us know, if you have any feedback.
@Nitr0_G Made this initial GUI for HyperDbg, and RedDbg. Here's the very first demo. Let us know, if you have any feedback. -
no amd processor to run RedDbg 🥲
-
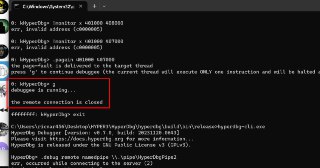
 Finally, the new instant event mechanism is ready. Right now, HyperDbg applies events instantly without continuing the debugger. This means you won't lose the current context and it guarantees to keep the system state (registers, and memory) untouched while applying events (like !epthook, !monitor, !syscall, etc.).
Finally, the new instant event mechanism is ready. Right now, HyperDbg applies events instantly without continuing the debugger. This means you won't lose the current context and it guarantees to keep the system state (registers, and memory) untouched while applying events (like !epthook, !monitor, !syscall, etc.). -

-
perfect good move
-
-
 Yep, actually it was the worst design problem of HyperDbg which is now fixed.
Yep, actually it was the worst design problem of HyperDbg which is now fixed. -
-
 Yes. I also merged it as 'v0.7 RC2' to the master branch.
Yes. I also merged it as 'v0.7 RC2' to the master branch. -
-
-
 broo 💀
broo 💀 -

-

-
 HyperDbg is not integrated with Ghidra as long as I know, but you use them together separately.
HyperDbg is not integrated with Ghidra as long as I know, but you use them together separately. -
WTF
-
-
okay thanks
-
 For those who can't build (and test the latest release), you can download github built artifacts here:
For those who can't build (and test the latest release), you can download github built artifacts here:
https://github.com/HyperDbg/HyperDbg/actions/runs/6796257043v0.7 RC2 · HyperDbg/HyperDbg@37c18a3State-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
-
 Probably yes, as we're currently spending our time fixing the fundamental design issues rather than making HyperDbg more transparent. It's generally more transparent than classic debuggers (e.g., windbg) by its nature as it didn't use any OS-made debugging API but still, there are a lot of footprints that advanced anti-hypervisor and and anti-debugging techniques can detect it.
Probably yes, as we're currently spending our time fixing the fundamental design issues rather than making HyperDbg more transparent. It's generally more transparent than classic debuggers (e.g., windbg) by its nature as it didn't use any OS-made debugging API but still, there are a lot of footprints that advanced anti-hypervisor and and anti-debugging techniques can detect it. -
 You're welcome. BTW, you don't need to use that 'eb @rip xx xx xx' loop trick anymore! 🙃
You're welcome. BTW, you don't need to use that 'eb @rip xx xx xx' loop trick anymore! 🙃 -
-
 None
None -
-
-
-
 One new thing came to my mind my right now that I need to test 🤔
One new thing came to my mind my right now that I need to test 🤔
I was thinking about using the INTERRUPT_WINDOW_EXITING field of the VMCS. This configuration bit causes the guest (debuggee) to throw a VM-exit once the guest is ready to receive an interrupt (or exception). If we could inject a series of pages while making this bit active to inject all of them, then it could solve our problem. -
 Not sure if it works, but I try to test it to see if it works this way, or not 🤔
Not sure if it works, but I try to test it to see if it works this way, or not 🤔 -
-
Okay thank you
-
-
-
 If we’re talking about VMX specifically, then it’s kinda hard to work around timing detections
If we’re talking about VMX specifically, then it’s kinda hard to work around timing detections -
 Exactly, but the good (and bad) thing is that Microsoft activated VBS. So, anti-hypervisor methods are no longer able to rely only on microarchitectural side channels.
Exactly, but the good (and bad) thing is that Microsoft activated VBS. So, anti-hypervisor methods are no longer able to rely only on microarchitectural side channels. -
 I don't thing so, this is a never ending cat and mouse fight.
I don't thing so, this is a never ending cat and mouse fight. -
 Tbh, I don’t use them coz i prefer not to pose performance
Tbh, I don’t use them coz i prefer not to pose performance -
 Do games work with VBS?
Do games work with VBS? -
 But we still can make the debugger substantially better in terms of transparency.
But we still can make the debugger substantially better in terms of transparency. -
 Nope, I disable it but I think most of the users won't disable it on their computers and this way anti-cheat makers have to ignore a lot of hypervisor-based detection methods.
Nope, I disable it but I think most of the users won't disable it on their computers and this way anti-cheat makers have to ignore a lot of hypervisor-based detection methods. -
When you say timing detections, are you referring to heartbeat?
-
 Not sure what heartbeat is. I’m talking about measuring instructions execution times, specifically the ones which cause vm exits. For instance cpuid causes unconditional exits. You could tweak tsc, sure. But then I’m not sure how to properly synchronise tsc among other cores
Not sure what heartbeat is. I’m talking about measuring instructions execution times, specifically the ones which cause vm exits. For instance cpuid causes unconditional exits. You could tweak tsc, sure. But then I’m not sure how to properly synchronise tsc among other cores - 09 November 2023 (7 messages)
-
 A universal solution is less likely to exist. There's many, many different ways you can detect a running hypervisor. What makes this process more bearable is that hypervisors are becoming a more commonly used thing for ensuring computer security (VBS under Hyper-V, etc). Anti-cheats have to take this into account, because frankly, explaining that a user has to turn this feature and this thing off, go into BIOS and whatnot is unreliable. The future is in masking and hijacking "whitelisted" hypervisors (which has been done)
A universal solution is less likely to exist. There's many, many different ways you can detect a running hypervisor. What makes this process more bearable is that hypervisors are becoming a more commonly used thing for ensuring computer security (VBS under Hyper-V, etc). Anti-cheats have to take this into account, because frankly, explaining that a user has to turn this feature and this thing off, go into BIOS and whatnot is unreliable. The future is in masking and hijacking "whitelisted" hypervisors (which has been done) -
 What anti-cheats prioritize is knowing flaws of commonly used hypervisors for illicit purposes, and abusing them to crash the system. This also happens with something like Hyper-V running, they know this specific case is handled, but might not be handled correctly if it's hijacked.
What anti-cheats prioritize is knowing flaws of commonly used hypervisors for illicit purposes, and abusing them to crash the system. This also happens with something like Hyper-V running, they know this specific case is handled, but might not be handled correctly if it's hijacked. -
 When it comes to timing attacks, there's so many areas you have to take care of, and so many potential cases where it would fail. The most common is measuring the time it takes for cpuid, as said above, you basically wrap a cpuid call with a timer, and check how much time has elapsed.
When it comes to timing attacks, there's so many areas you have to take care of, and so many potential cases where it would fail. The most common is measuring the time it takes for cpuid, as said above, you basically wrap a cpuid call with a timer, and check how much time has elapsed. -
 That's one of the easier ones, but then you have other types as well, like you might try to add a couple of junk instructions to inflate the execution time, and see whether it was actually taken account when you check the elapsed time.
That's one of the easier ones, but then you have other types as well, like you might try to add a couple of junk instructions to inflate the execution time, and see whether it was actually taken account when you check the elapsed time. -
 You could also trigger a context switch, do some extended operations and then compare the time it would take to execute when you cause an unconditional exit
You could also trigger a context switch, do some extended operations and then compare the time it would take to execute when you cause an unconditional exit -
 there's many ways you can do this
there's many ways you can do this -
 for the crashers, it's mostly just looking at behavior of instructions that cause unconditional exits with different ways, checking if exceptions are injected properly, ...
for the crashers, it's mostly just looking at behavior of instructions that cause unconditional exits with different ways, checking if exceptions are injected properly, ... - 10 November 2023 (4 messages)
-
Joined.
-
happy
-
 Joined.
Joined. -
Thank you so much for this ❤️
- 11 November 2023 (10 messages)
-
Joined.
-
does anyone know how to bypass EAC with hyperdbg loaded?
-
Joined.
-
 Here's the description of these instant events.
Here's the description of these instant events.
https://docs.hyperdbg.org/tips-and-tricks/misc/instant-eventsInstant eventsThe instant event mechanism in HyperDbg
-
 Generally, it needs lots of considerations (like pre-allocating pools, broadcasting functions to halted cores in VMX root-mode, etc.). I tried to make these considerations as transparent as possible from the users' perspective; however, the user might encounter some limitations in applying instant events. For example, if the user wants to apply tens of events (say 20 or more) instantly and without continuing the debuggee, then it should tell HyperDbg beforehand to prepare the environment and allocate some pools (using the 'prealloc' command), or if the user wants to apply an event with a large script, again HyperDbg should be notified about it. In most of the regular usages, you won't notice these limitations as it tries to handle and replace buffers automatically when the user continues the debuggee but in any case, if you don't have a normal event then the solution is notifying HyperDbg before applying which is described there.
Generally, it needs lots of considerations (like pre-allocating pools, broadcasting functions to halted cores in VMX root-mode, etc.). I tried to make these considerations as transparent as possible from the users' perspective; however, the user might encounter some limitations in applying instant events. For example, if the user wants to apply tens of events (say 20 or more) instantly and without continuing the debuggee, then it should tell HyperDbg beforehand to prepare the environment and allocate some pools (using the 'prealloc' command), or if the user wants to apply an event with a large script, again HyperDbg should be notified about it. In most of the regular usages, you won't notice these limitations as it tries to handle and replace buffers automatically when the user continues the debuggee but in any case, if you don't have a normal event then the solution is notifying HyperDbg before applying which is described there. -
 Another new addition to HyperDbg v0.7 is its support for string comparisons (thanks to @xmaple555 for implementing it!).
Another new addition to HyperDbg v0.7 is its support for string comparisons (thanks to @xmaple555 for implementing it!).
Here's an example of how you can use this string comparison to pause (halt) the debuggee if a special file name (path) is passed to nt!NtCreateFile.
https://docs.hyperdbg.org/commands/scripting-language/examples/pause-the-debugger-conditionallypause the debugger conditionallyAn example of pausing system while a special path is passed to the NtCreateFile
-
 That would probably be against the terms of service of EAC
That would probably be against the terms of service of EAC -
 EAC is already detailed in a lot of RE blogs and found to not be malicious, there's no need to reverse it
EAC is already detailed in a lot of RE blogs and found to not be malicious, there's no need to reverse it -
 Lol
Lol -

- 12 November 2023 (3 messages)
-
 it’s really not
it’s really not -
 the last comprehensive blog or reversal was in 2019
the last comprehensive blog or reversal was in 2019 -
Joined.
- 14 November 2023 (1 messages)
-
Joined.
- 16 November 2023 (4 messages)
-
 HyperDbg now fully supports the concurrent use of other debuggers such as x64dbg and windbg when HyperDbg is loaded.
HyperDbg now fully supports the concurrent use of other debuggers such as x64dbg and windbg when HyperDbg is loaded.
https://docs.hyperdbg.org/commands/debugging-commands/test
To use it, you need to disable breakpoint (#BP) and debug break (#DB) interception of HyperDbg by using the following commands:
4: kHyperDbg> test trap off
4: kHyperDbg> test breakpoint off
To test it, you need to either compile the 'master' branch or use GitHub Artifacts of the 'master' branch. -

-
Joined.
-

- 17 November 2023 (2 messages)
-
Joined.
-
Joined.
- 19 November 2023 (2 messages)
-
 Joined.
Joined. -
 Hi, nice to meet you all
Hi, nice to meet you all - 20 November 2023 (213 messages)
-
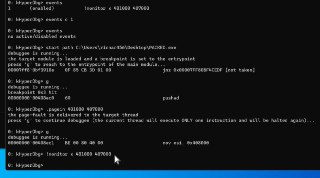
 This was actually right. I change the '.pagein' command to support a range of addresses.
This was actually right. I change the '.pagein' command to support a range of addresses.
The new implementation uses the interrupt-window exiting bit of the VMCS and injects each page once the interrupt-window is open. So, right now you can bring multiple pages (a range of addresses) into the RAM.
https://docs.hyperdbg.org/commands/meta-commands/.pagein -
 @ricnar please check it once you have free time 🙂
@ricnar please check it once you have free time 🙂
It's on the 'dev' branch. -
 and also this demo shows how it works.
and also this demo shows how it works. -
Thanks i will check
-
-
-
-
-
-
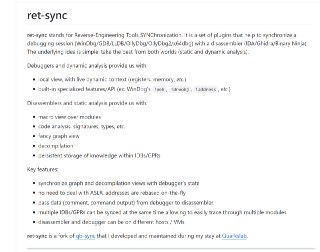
GitHub - bootleg/ret-sync: ret-sync is a set of plugins that helps to synchronize a debugging session (WinDbg/GDB/LLDB/OllyDbg2/x64dbg) with IDA/Ghidra/Binary Ninja disassemblers.
ret-sync is a set of plugins that helps to synchronize a debugging session (WinDbg/GDB/LLDB/OllyDbg2/x64dbg) with IDA/Ghidra/Binary Ninja disassemblers. - GitHub - bootleg/ret-sync: ret-sync is a s...
-
-
-
-
 Yes
Yes -
 yes that's also a really good feature that should be added.
yes that's also a really good feature that should be added. -
-
-
-
-
-
-
-
-
 Sure, that will be added
Sure, that will be added -
-
-
-
-
-
-
-
-
-
-
-
-
 🤔
🤔 -
 Does it work as expected?
Does it work as expected? -
-
-
-
-
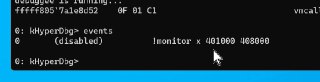
 and also, as you probably noticed, the '!monitor' event is applied instantly without continuing the debuggee.
and also, as you probably noticed, the '!monitor' event is applied instantly without continuing the debuggee. -
-
-
-
-
-
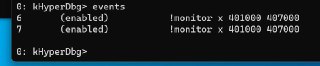
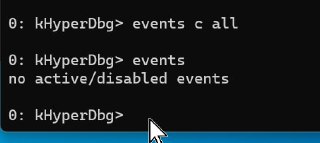
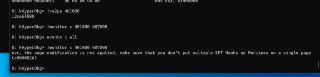
 Did you clear the prev events?
Did you clear the prev events? -
-
-
-
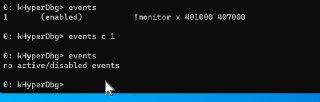
 It's disabled, not removed
It's disabled, not removed -
 You should use 'event c all' to clear them
You should use 'event c all' to clear them -
-
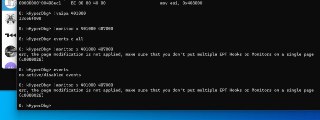
 How ever, clearing events is not applied immediately
How ever, clearing events is not applied immediately -
 Clearing event just disables the event, and after you continue debuggee it will actually be removed from the system
Clearing event just disables the event, and after you continue debuggee it will actually be removed from the system -
 So, basically you don't need to that, just re-enable your previous event
So, basically you don't need to that, just re-enable your previous event -
-
-
-
-
-
-
-
-
 🤔
🤔 -
-
-
-
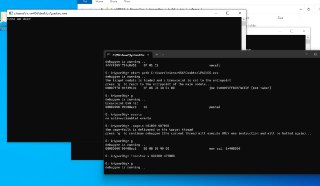
 Can you also check the process? I mean use the '.process' command to see if you're in the target process
Can you also check the process? I mean use the '.process' command to see if you're in the target process -
-
 👍
👍 -
 Did you get what was the last problem?
Did you get what was the last problem? -
 🤔🤔🤔
🤔🤔🤔 -
-
-
-
-
-
-
-
-
-
 This is probably caused by the changes we made for MTRRs because of the changes made for 13 gen processors. I will investigate and fix that.
This is probably caused by the changes we made for MTRRs because of the changes made for 13 gen processors. I will investigate and fix that. -
-
-
-
-
 Does it have any TLS or a separate thread?
Does it have any TLS or a separate thread? -
-
-
-
-
-
 This probably has some technical reasons for this file. 🤔
This probably has some technical reasons for this file. 🤔 -
 Pressing 'g' just continues the target thread with a trap flag
Pressing 'g' just continues the target thread with a trap flag -
 Is there any 'pushf' or 'popf' somewhere?
Is there any 'pushf' or 'popf' somewhere? -
-
-
-
-
-
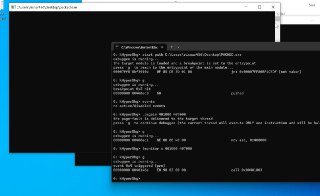
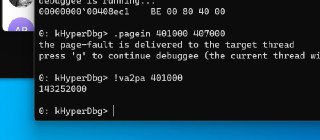
 Can you check the physical address of the target address?
Can you check the physical address of the target address? -
 Like '!va2pa 401000' ?
Like '!va2pa 401000' ? -
 and also the second time again with the '!va2pa 401000'.
and also the second time again with the '!va2pa 401000'. -
 Generally, the EPT hooks are applied on physical address.
Generally, the EPT hooks are applied on physical address. -
-
-
-
-
-
-
-
-
 In the second attempt the GPA (Guest Physical Address) is changed? Am I right?
In the second attempt the GPA (Guest Physical Address) is changed? Am I right? -
-
-
 After that you need to press 'g'
After that you need to press 'g' -
 to make sure the effects of the EPT are removed.
to make sure the effects of the EPT are removed. -
-
-
-
-
 If the physical address is changed, then it cannot intercept the 'x' of the '!monitor'
If the physical address is changed, then it cannot intercept the 'x' of the '!monitor' -
 EPT works based on guest physical addresses
EPT works based on guest physical addresses -
-
-
-
 So if the physical address is changed then you should remove that event and re-apply the '!monitor' event.
So if the physical address is changed then you should remove that event and re-apply the '!monitor' event. -
-
-
-
-
 because the physical address didn't change. Uses the same physical address.
because the physical address didn't change. Uses the same physical address. -
-
-
-
 The process didn't closed. Windows just assigns new physical addresses if the process completely closes.
The process didn't closed. Windows just assigns new physical addresses if the process completely closes. -
 Honestly, didn't get what you trying to do 🤔
Honestly, didn't get what you trying to do 🤔
Why do you need clear the event at this stage? Because as long as the process is open, the physical address remains the same. -
-
-
-
-
-
-
-
-
-
 And also one thing to keep in mind is if two processes are open then the second process uses the same physical address.
And also one thing to keep in mind is if two processes are open then the second process uses the same physical address. -
-
-
 Windows allocates the same physical address for both of the processes to avoid resource waste.
Windows allocates the same physical address for both of the processes to avoid resource waste. -
-
-
 I mean in the second process, if the first process is closed, you need to apply a new '!monitor' event.
I mean in the second process, if the first process is closed, you need to apply a new '!monitor' event. -
 Is it the reason for the error?
Is it the reason for the error? -
-
-
 and then what was the error?
and then what was the error? -
-
-
-
-
-
-
 Got it, I have to test it.
Got it, I have to test it. -
-
-
-
-
-
-
 yes
yes -
-
-
-
-
-
-
-
 Thanks, I will check and fix it.
Thanks, I will check and fix it. -
-
 Yes, it's also written in the documentation that it's the responsibility of the user to take care of their EPT hooks in the scenarios when Windows wants to re-map (change) the physical address e.g. when process is closed.
Yes, it's also written in the documentation that it's the responsibility of the user to take care of their EPT hooks in the scenarios when Windows wants to re-map (change) the physical address e.g. when process is closed. -
 Because otherwise HyperDbg doesn't have any clue about Windows memory manager.
Because otherwise HyperDbg doesn't have any clue about Windows memory manager. -
-
 Generally, HyperDbg is supposed to be unaware of the operating system. Though, we in some scenarios we didn't follow this rule. Like in the '.process' command where we actually parse everything based on the _EPROCESS.
Generally, HyperDbg is supposed to be unaware of the operating system. Though, we in some scenarios we didn't follow this rule. Like in the '.process' command where we actually parse everything based on the _EPROCESS. -
 No, it won't. How could we know that?
No, it won't. How could we know that? -
 I mean how could we know that Windows changes the physical address?
I mean how could we know that Windows changes the physical address?
And is it even necessary? Because the physical address remains unaffected in the process lifetime. -
-
 I mean there is no way we could understand that Windows creates a new physical address for the target process.
I mean there is no way we could understand that Windows creates a new physical address for the target process. -
-
-
-
-
-
-
-
 The complexity of implementing it this way is too high. Because as you might know HyperDbg is not able to switch to other processes in vmx-root mode.
The complexity of implementing it this way is too high. Because as you might know HyperDbg is not able to switch to other processes in vmx-root mode. -
-
 That's possible but what if the process is not actually closed? E.g., it modified the page attributes of the .code segment and instructions? In this scenario if another process uses the same physical address, a new physical address will be allocated for the process that modified the code.
That's possible but what if the process is not actually closed? E.g., it modified the page attributes of the .code segment and instructions? In this scenario if another process uses the same physical address, a new physical address will be allocated for the process that modified the code. -
-
-
-
-
-
-
-
-
 I think it's too complex to be handled as a VMX-root based solution. If it was supposed to run in the VMX non-root mode in PASSIVE_LEVEL, it was easy to implement but it's a pain (and not guaranteed to work) if we want to check another process in the VMX root-mode.
I think it's too complex to be handled as a VMX-root based solution. If it was supposed to run in the VMX non-root mode in PASSIVE_LEVEL, it was easy to implement but it's a pain (and not guaranteed to work) if we want to check another process in the VMX root-mode. -
 That's why HyperDbg even doesn't let the user to specify the 'pid' parameter for the memory READ/WRITE commands while the debugee is halted in the Debugger Mode.
That's why HyperDbg even doesn't let the user to specify the 'pid' parameter for the memory READ/WRITE commands while the debugee is halted in the Debugger Mode. -
 Joined.
Joined. -
 New video from @ricnar:
New video from @ricnar:
https://youtu.be/KVxV6epwMPc?si=1QS54Y-bi01U4Q40 - 21 November 2023 (1 messages)
-
- 22 November 2023 (3 messages)
-
 This one is added (with an 'l' option), like:
This one is added (with an 'l' option), like:
.pagein 0x7fff1234 l 8000 -
 HyperDbg v0.7 is released!
HyperDbg v0.7 is released!
Check out: https://github.com/HyperDbg/HyperDbg/releases/tag/v0.7.0
Starting from HyperDbg v0.7 (this version), events are guaranteed to keep the debuggee in a halt state (in the Debugger Mode); thus, nothing will change during its execution and the context (registers and memory) remain untouched.
Added
- HyperDbg now applies events immediately as implemented in the "instant events" mechanism
- The Event Forwarding mechanism is now supported in the Debugger Mode
- The Event Forwarding mechanism now supports external modules (DLLs)
- event_clear(EventId) function in script engine
- HyperDbg now supports string inputs for strlen and other related functions thanks to @xmaple555
- New semantic tests for the script engine (50 to 59) is added mainly for testing new string and memory comparison functions
- strlen and wcslen functions now support string and wide-character string as the input
- strcmp(Str1, Str2), wcscmp(WStr1, WStr2) and memcmp(Ptr1, Ptr2, Num) functions in script engine thanks to @xmaple555
- The debug break interception (#DB) manipulation option is added to the 'test' command
- The '.pagein' command, now supports address ranges (length in bytes) to bring multiple pages into the RAM
Changed
- Fix the problem with the "less than" and the "greater than" operators for signed numbers thanks to @xmaple555
- Fix the problem checking for alternative names thanks to @xmaple555
- Fix the crash by turning off the breakpoints while a breakpoint is still active thanks to @xmaple555
- Fix the crash on reading symbols on remote debuggee thanks to @xmaple555
- The 'prealloc' command is updated with new instant-event preallocated pools
- Fix wrong removing of EPT Hook (hidden breakpoints)
- The 'event' command, no longer continues debuggee for clearing events, instead just disables the event and removes the effects of the event when debuggee continues
- $id pseudo-register changed to $event_id
- $tag pseudo-register changed to $event_tag
- $stage pseudo-register changed to $event_stage
- Fix adding pseudo-registers with underscore in the script engine
- Fix the boolean expression interpretation in if conditions in the script engine
- HyperDbg now intercepts all debug breaks (#DBs) if it's not explicitly asked not to by using the 'test' command
- Fix '%d' bug in script engineRelease v0.7.0 · HyperDbg/HyperDbgHyperDbg v0.7 is released! If you’re enjoying HyperDbg, don’t forget to give a star 🌟 on GitHub! Please visit Build & Install to configure the environment for running HyperDbg. Check out the Qu...
-
Joined.
- 26 November 2023 (1 messages)
-
- 27 November 2023 (2 messages)
-
Joined.
-
- 30 November 2023 (1 messages)
-
- 01 Nov 2023 (7)
- 03 Nov 2023 (1)
- 06 Nov 2023 (20)
- 07 Nov 2023 (1)
- 08 Nov 2023 (43)
- 09 Nov 2023 (7)
- 10 Nov 2023 (4)
- 11 Nov 2023 (10)
- 12 Nov 2023 (3)
- 14 Nov 2023 (1)
- 16 Nov 2023 (4)
- 17 Nov 2023 (2)
- 19 Nov 2023 (2)
- 20 Nov 2023 (213)
- 21 Nov 2023 (1)
- 22 Nov 2023 (3)
- 26 Nov 2023 (1)
- 27 Nov 2023 (2)
- 30 Nov 2023 (1)