- 01 July 2024 (9 messages)
-
 Joined.
Joined. -
 No. Unfortunately, the stepping mechanism only works in the Debugger Mode (not VMI Mode).
No. Unfortunately, the stepping mechanism only works in the Debugger Mode (not VMI Mode). -
 Not sure if I understand. Can you elaborate on what to be addressed in ntoskrnl? 🤔
Not sure if I understand. Can you elaborate on what to be addressed in ntoskrnl? 🤔 -
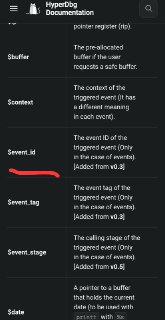
is there a kernel base address variable?(example @rax)
-
 You can use the 'lm' command to get the base address of different modules.
You can use the 'lm' command to get the base address of different modules.
https://docs.hyperdbg.org/commands/debugging-commands/lmlm (view loaded modules) | HyperDbg DocumentationDescription of the 'lm' command in HyperDbg.
-
Joined.
-
 @HughEverett
@HughEverett
1: kHyperDbg> !monitor x 017CA56B l 10 script {
> printf("%s %s DYN CALL TO %x\n",$date, $time, dd(eax+8));
> }
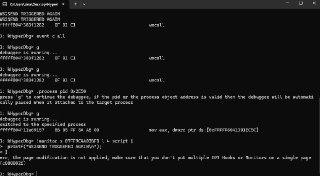
err, the page modification is not applied, make sure that you don't put multiple EPT Hooks or Monitors on a single page (c0000026)
1: kHyperDbg> g
debuggee is running...
fffff801`17de1282 0F 01 C1 vmcall
0: kHyperDbg> events
no active/disabled events -
 shall i remove monitor different way than event c all ?
shall i remove monitor different way than event c all ? -
 (i applied different script before on same addr)
(i applied different script before on same addr) - 02 July 2024 (11 messages)
-
 Joined.
Joined. -
 Hi,
Hi,
sorry for the late reply
Actually there is a design issue with HyperDbg that whenever you clear an event, it cannot be removed immediately. Instead HyperDbg first disables the event and when you continue the debuggee (using the 'g' command) it removes it from the EPT page tables. So, you need to continue debuggee before applying next EPT hook. This design issue will be solved in the future but if you cannot continue the debuggee for any reason or you need to apply your new event immediately, then you can simply disable it (event d all) and HyperDbg won't trigger it for you anymore. -
 But if you removed it and you continue debuggee and pause it again, if the error happens again (while the hook is removed) it's potentially a bug that needs to be investigated.
But if you removed it and you continue debuggee and pause it again, if the error happens again (while the hook is removed) it's potentially a bug that needs to be investigated. -
 yea.. i ran debugger again after clearing
yea.. i ran debugger again after clearing -
 So, it still shows this error? 🤨
So, it still shows this error? 🤨 -
 lemme try again
lemme try again -
 yup.. its repeating
yup.. its repeating
hook 1
1: kHyperDbg> !monitor x 760858a0 l 4 script {
> printf("WS2SEND TRIGGERED\n");
> }
1: kHyperDbg> g
debuggee is running...
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
WS2SEND TRIGGERED
fffff804`33ca1282 0F 01 C1 vmcall
0: kHyperDbg> event c all
0: kHyperDbg> g
debuggee is running...
fffff804`33ca1282 0F 01 C1 vmcall
events empty
1: kHyperDbg> events
no active/disabled events
here i forgot to switch process
1: kHyperDbg> !monitor x 760858a0 l 4 script {
> printf("WS2SEND TRIGGERED AGAIN\n");
> }
err, invalid address (c0000005)
address may be paged-out or unavailable on the page table due to 'demand paging'
please refer to https://docs.hyperdbg.org/tips-and-tricks/considerations/accessing-invalid-address for further information
1: kHyperDbg> process pid 22e0
press 'g' to continue the debuggee, if the pid or the process object address is valid then the debuggee will be automatically paused when it attached to the target process
1: kHyperDbg> g
debuggee is running...
switched to the specified process
ntkrnlmp!KiSwapThread+0x81b:
fffff804`36c4164b 45 33 C0 xor r8d, r8d
hook2
0: kHyperDbg> !monitor x 760858a0 l 4 script {
> printf("WS2SEND TRIGGERED AGAIN\n");
> }
err, the page modification is not applied, make sure that you don't put multiple EPT Hooks or Monitors on a single page (c0000026)
0: kHyperDbg>Accessing Invalid Address | HyperDbg DocumentationConsiderations for accessing memory in different modes
-
 Ah, got it. Could you create a GitHub issue for this? I'll try to investigate it hopefully tomorrow.
Ah, got it. Could you create a GitHub issue for this? I'll try to investigate it hopefully tomorrow. -
 here you go https://github.com/HyperDbg/HyperDbg/issues/409Can't set !monitor on same addres, even after event removed. · Issue #409 · HyperDbg/HyperDbg
here you go https://github.com/HyperDbg/HyperDbg/issues/409Can't set !monitor on same addres, even after event removed. · Issue #409 · HyperDbg/HyperDbghook 1 1: kHyperDbg> !monitor x 760858a0 l 4 script { printf("WS2SEND TRIGGERED\n"); } 1: kHyperDbg> g debuggee is running... WS2SEND TRIGGERED WS2SEND TRIGGERED WS2SEND TRIGGERED W...
-
 👍
👍 -
 @HughEverett by the way, is monitor x implemented way different than !epthook ? !etphook is detected by antihack, !monitor is not
@HughEverett by the way, is monitor x implemented way different than !epthook ? !etphook is detected by antihack, !monitor is not - 03 July 2024 (60 messages)
-
 The '!monitor' command just changes the attributes of EPT page tables but the '!epthook' changes both EPT page table attributes and puts 0xcc (int3) breakpoints, but I think your target anti-hack method tries to read/write from the page table and compute the time it takes (probably by using RDTSC/RDTSCP) instructions which is performed normally if you just use '!monitor x' but if you use '!monitor rwx' then probably it detects !monitor too. Please take a look at these documentation explanations:
The '!monitor' command just changes the attributes of EPT page tables but the '!epthook' changes both EPT page table attributes and puts 0xcc (int3) breakpoints, but I think your target anti-hack method tries to read/write from the page table and compute the time it takes (probably by using RDTSC/RDTSCP) instructions which is performed normally if you just use '!monitor x' but if you use '!monitor rwx' then probably it detects !monitor too. Please take a look at these documentation explanations:
Design of !epthook:
https://docs.hyperdbg.org/design/features/vmm-module/design-of-epthook
Design of !monitor:
https://docs.hyperdbg.org/design/features/vmm-module/design-of-monitorDesign of !epthook | HyperDbg DocumentationDesign of !epthook command
-
 I see. Im pretty sure, that antihack finds int3, it even tells you that process was altered, probably some md5 calculations or smth like that.
I see. Im pretty sure, that antihack finds int3, it even tells you that process was altered, probably some md5 calculations or smth like that. -
 Int3 is hidden, if it's a user-mode process check, it shouldn't notice it 🤨
Int3 is hidden, if it's a user-mode process check, it shouldn't notice it 🤨 -
 Antihack sits on ring0
Antihack sits on ring0 -
 If I put either BP or !epthook after some time it pops up telling that process or antihack was altered and shuts down everything. The only thing - it's not instant, I can manage to catch some bps/hooks until that thing finds out them.
If I put either BP or !epthook after some time it pops up telling that process or antihack was altered and shuts down everything. The only thing - it's not instant, I can manage to catch some bps/hooks until that thing finds out them. -
 No difference, it shouldn't notice it from the kernel mode too.
No difference, it shouldn't notice it from the kernel mode too. -
 It probably checks for the time it takes to respond to a memory read which will reveal that HyperDbg is monitoring that special page.
It probably checks for the time it takes to respond to a memory read which will reveal that HyperDbg is monitoring that special page. -
 Otherwise, I can't think of a method to check the memory alteration for !epthook. 🤔
Otherwise, I can't think of a method to check the memory alteration for !epthook. 🤔 -
 Could be... well, anyway I'm fine with monitor, just takes longer time do debug
Could be... well, anyway I'm fine with monitor, just takes longer time do debug -
 Ah, wanted to ask, is it possible to set monitor from script(i mean its possible with current architecture)? I have dynamic calls, which I can calculate only in runtime.
Ah, wanted to ask, is it possible to set monitor from script(i mean its possible with current architecture)? I have dynamic calls, which I can calculate only in runtime. -
 @HughEverett there is no possibility to exit script, right? like return or smth
@HughEverett there is no possibility to exit script, right? like return or smth -
 It's actually possible in the VMM module to apply events immediately, but it's not exported to the user this way. Because the script engine IR generator is in the user-mode. If you want to do it, you can directly modify the source code and apply the event using a custom function. But, it's a really cool feature I think. 🤔
It's actually possible in the VMM module to apply events immediately, but it's not exported to the user this way. Because the script engine IR generator is in the user-mode. If you want to do it, you can directly modify the source code and apply the event using a custom function. But, it's a really cool feature I think. 🤔
I'll add it to the future to-do list but it probably won't be ready soon since it needs fundamental design changes.
One way around it is by using:
event (with a pause() function) + g + new event
So, once your script is running, it continues the debuggee immediately after applying the first event and when your event executes the pause() function, the debugger is paused and the second event will be created. (If you didn't understand what I mean by this, please let me know, I could elaborate it more). -
 Exit script? What do you mean? Like disabling the event? 🤨
Exit script? What do you mean? Like disabling the event? 🤨 -
 There are a couple of functions for disabling/enabling and removing or short-circuiting events here:
There are a couple of functions for disabling/enabling and removing or short-circuiting events here:
https://docs.hyperdbg.org/commands/scripting-language/functions/eventsevents | HyperDbg DocumentationFunctions related to events
-
 You can use them along with the $event_id pseudo-register.
You can use them along with the $event_id pseudo-register. -
 no.. sample from my script:
no.. sample from my script:
n = check_address(edx+c);
k = 0;
if (n == 1){
printf("%s %s DYN CALL TO %x\n",$date, $time, dd(edx+c));
k = 1;
} else {
printf("%s %s DYN CALL, BUT FAILED TO DECODE %x\n",$date, $time, edx+c);
return here as memory is invalid, so no longer processing needed
}
if (k == 1){.... -
 it would improve scripting a lot i think, no additional if branches
it would improve scripting a lot i think, no additional if branches -
 Like a function return? 🤨
Like a function return? 🤨 -
 yup
yup -
 i understand, but pause will loose context in this case..
i understand, but pause will loose context in this case.. -
 @xmaple555 implemented the functions logic, you can use it like a function.
@xmaple555 implemented the functions logic, you can use it like a function. -
 Constants & Functions | HyperDbg Documentation
Constants & Functions | HyperDbg DocumentationDescription of constants and functions
-
 No, pause will pause the debugger immediately. Context is preserved.
No, pause will pause the debugger immediately. Context is preserved. -
 hm. in main script it told me there is error when i put return;
hm. in main script it told me there is error when i put return; -
 You need to ask @xmaple555 to fix it, I don't know that much about the script engine parser. 🙂🙃
You need to ask @xmaple555 to fix it, I don't know that much about the script engine parser. 🙂🙃 -
 this is good to know.. bad thing those dynamic calls are calculated within one page :(
this is good to know.. bad thing those dynamic calls are calculated within one page :( -
 ok, i will create issue
ok, i will create issue -
 What do you mean by dynamic calls calculation? 🤨
What do you mean by dynamic calls calculation? 🤨 -
 something like
something like
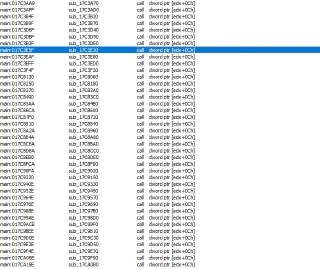
main:017C9D0E call dword ptr [edx+0Ch]
and
main:017C9BEE call dword ptr [edx+0Ch]
those are different subs, but stays within one page, so i cant put !monitors on both calls -
 edx will point to different offsets
edx will point to different offsets -
 so the chain actually is : call dword ptr [eax+8] -> ( main:017C9D0E call dword ptr [edx+0Ch] OR main:017C9BEE call dword ptr [edx+0Ch])
so the chain actually is : call dword ptr [eax+8] -> ( main:017C9D0E call dword ptr [edx+0Ch] OR main:017C9BEE call dword ptr [edx+0Ch]) -
 so i need to calculate the target function at the very end of this
so i need to calculate the target function at the very end of this -
 so far i know call dword ptr [eax+8] location, that is executed always
so far i know call dword ptr [eax+8] location, that is executed always -
 Wait, you cannot put two !monitors in one page?
Wait, you cannot put two !monitors in one page? -
 I thought it's possible. 🤔
I thought it's possible. 🤔 -
 lemme prepare sample
lemme prepare sample -
 Not sure if I understand what you mean but !monitor receives (to/from) parameters from the script expressions:
Not sure if I understand what you mean but !monitor receives (to/from) parameters from the script expressions:
https://github.com/HyperDbg/HyperDbg/blob/a691c1df3be48660907fcf93840302a8c4650ff4/hyperdbg/libhyperdbg/code/debugger/commands/extension-commands/monitor.cpp#L204HyperDbg/hyperdbg/libhyperdbg/code/debugger/commands/extension-commands/monitor.cpp at a691c1df3be48660907fcf93840302a8c4650ff4 · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 if i put monitor on whole page, it will flood with calls...
if i put monitor on whole page, it will flood with calls... -
 Which means you can calculate your addresses in global variables and use them as parameters to the !monitor.
Which means you can calculate your addresses in global variables and use them as parameters to the !monitor. -
 ok, let me explain a bit
ok, let me explain a bit -
 E.g., !monitor .FromGlobalVar .FromGlobalVar+0x85 script { ... }
E.g., !monitor .FromGlobalVar .FromGlobalVar+0x85 script { ... } -
 Wait couldn't you put multiple !monitor hooks in one page? As long as I remember it was possible. 🤔🤔🤔
Wait couldn't you put multiple !monitor hooks in one page? As long as I remember it was possible. 🤔🤔🤔
Not a big deal BTW, you can handle it through the script.
E.g., check for your ranges within if conditions. $context pseudo-register contains the address of accessed memory address. However, I'm pretty sure we support multiple !monitor(s) on same page at some point. 🤔 -
 first i put monitor here main:017CA56B call dword ptr [eax+8] ; then inside script i want to do something like put monitor x eax+8 l 4 so it will follow function call, for example main:017C9D00, i know offest where dword ptr [edx+0Ch] will be called, let say 017C9D00+58, so i will put new monitor again on 017C9D00+58 and then, when im in desired function - print disasembly
first i put monitor here main:017CA56B call dword ptr [eax+8] ; then inside script i want to do something like put monitor x eax+8 l 4 so it will follow function call, for example main:017C9D00, i know offest where dword ptr [edx+0Ch] will be called, let say 017C9D00+58, so i will put new monitor again on 017C9D00+58 and then, when im in desired function - print disasembly -
 0: kHyperDbg> !monitor x 760658a0 l 4 script {
0: kHyperDbg> !monitor x 760658a0 l 4 script {
>
> printf("monitor");
> }
0: kHyperDbg> !monitor x 760658f0 l 4 script {
>
> printf("monitor");
> }
err, the page modification is not applied, make sure that you don't put multiple EPT Hooks or Monitors on a single page (c0000026)
0: kHyperDbg> -
 i will try to play with from/to params, but im afraid it will spam me with events though :(
i will try to play with from/to params, but im afraid it will spam me with events though :( -
 Why don't you check ranges within if conditions?
Why don't you check ranges within if conditions? -
 yea, going to do that
yea, going to do that -
 Like put a !monitor on an entire page, and check for the $context.
Like put a !monitor on an entire page, and check for the $context. -
 yup, thats my idea for now :)
yup, thats my idea for now :) -
 thanks for advice
thanks for advice -
 This one again could be handled from the by the method I told you earlier (pause())
This one again could be handled from the by the method I told you earlier (pause()) -
 i want to do it automatically (e.g. all possible "end" calls)
i want to do it automatically (e.g. all possible "end" calls) -
 You can use global variables to check your $context with dynamic ranges.
You can use global variables to check your $context with dynamic ranges. -
 there are bunch of them, like 30
there are bunch of them, like 30 -
 yes, will see how it helps
yes, will see how it helps -
 Maybe a combination of loops could help.
Maybe a combination of loops could help. -
 if i was allowed to use monitors on same page, it would help a lot :)
if i was allowed to use monitors on same page, it would help a lot :) -
 and a bit more below
and a bit more below -
 as you see those subs are pretty close to each other, so probably global variables might do the trick
as you see those subs are pretty close to each other, so probably global variables might do the trick -
 @HughEverett one more bug about monitors - when i remove monitors and .debug close, vm restarts, i think its related to that bug where cant set monitor on same adderss
@HughEverett one more bug about monitors - when i remove monitors and .debug close, vm restarts, i think its related to that bug where cant set monitor on same adderss - 04 July 2024 (7 messages)
-
-
 It's just the matter of handling complex logic of hooks in different pages. I'm so lazy to think about it since the algorithm of handling multiple hooks and events could become complex. 😅
It's just the matter of handling complex logic of hooks in different pages. I'm so lazy to think about it since the algorithm of handling multiple hooks and events could become complex. 😅 -
 But sure, I'll add it to the future todo list.
But sure, I'll add it to the future todo list. -
 Thanks for reporting it, I'll check it.
Thanks for reporting it, I'll check it. -
 I think it's shared between all drivers. I see caaes where it's not shared but if I remember it correctly, it's generally shared between different processes (but not sure). 🤔
I think it's shared between all drivers. I see caaes where it's not shared but if I remember it correctly, it's generally shared between different processes (but not sure). 🤔 -
 ok, no worries, but pls try to solve that monitor mystery :) actually after putting one monitor i shall restart vm (it restarts itself) and then put another one
ok, no worries, but pls try to solve that monitor mystery :) actually after putting one monitor i shall restart vm (it restarts itself) and then put another one -
 Sure
Sure - 05 July 2024 (24 messages)
-
 I was able to reproduce this error.
I was able to reproduce this error.
https://github.com/HyperDbg/HyperDbg/issues/409 -
 It seems that it's because HyperDbg doesn't remove the !monitor hooks correctly when the address is not available in HyperDbg's address space. 🤔
It seems that it's because HyperDbg doesn't remove the !monitor hooks correctly when the address is not available in HyperDbg's address space. 🤔 -
 Since this address is only valid in the target process memory, not HyperDbg's view of memory (cr3).
Since this address is only valid in the target process memory, not HyperDbg's view of memory (cr3). -
 Eduard Please switch to this branch and test it again:
Eduard Please switch to this branch and test it again:
https://github.com/HyperDbg/HyperDbg/tree/fix-monitor-removeGitHub - HyperDbg/HyperDbg at fix-monitor-removeState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 Test this one and ...
Test this one and ... -
 this one.
this one. -
 Both of them should be fixed.
Both of them should be fixed. -
 I changed the logic of clearing !monitor events.
I changed the logic of clearing !monitor events. -
 Also please try to test it with different conditions and different ways if you can. At the moment it passed all of my tests but since the logic of clearing these kinds of events is changed, I might break it in some other ways, so performing a complete test would help a lot.
Also please try to test it with different conditions and different ways if you can. At the moment it passed all of my tests but since the logic of clearing these kinds of events is changed, I might break it in some other ways, so performing a complete test would help a lot. -
 Once you've done testing it, please let me know so I'll merge it to the 'dev' branch.
Once you've done testing it, please let me know so I'll merge it to the 'dev' branch. -
 Ok, will test today
Ok, will test today -
 good! i can set monitor on same address again :)
good! i can set monitor on same address again :) -
 VM also does not restart on .debug close when monitor removed
VM also does not restart on .debug close when monitor removed -
 That's great. I merged it to the 'dev' branch now.
That's great. I merged it to the 'dev' branch now. -
 thanks
thanks -
 one thing, i have to run process for some while to get monitor completely removed, i cant remove and set new within one break
one thing, i have to run process for some while to get monitor completely removed, i cant remove and set new within one break -
 Yep, this is what I told here:
Yep, this is what I told here: -
 .
. -
 ah.. i see, but its minor thing anyway :)
ah.. i see, but its minor thing anyway :) -
 But generally you have tons of options, you could disable/enable events instead of clearing them. Or use a nop+jmp infinite loop at the @RIP register.
But generally you have tons of options, you could disable/enable events instead of clearing them. Or use a nop+jmp infinite loop at the @RIP register. -
 This one is really hard to solve. 😅
This one is really hard to solve. 😅
In HyperDbg we use NMIs for halting cores. This mechanism should be changed to IPIs instead of NMIs.
The reason why it doesn't support immediately clearing of events is because we might halt the core in the middle of handling an event and conclude to remove them. In that case, the event will trigger BSOD since its structures are freed. But, using IPIs will make sure that handling one event will be finished, and then another VM-exit happens which will halt the core. -
 Using IPIs by itself is okay but since HyperDbg is highly dependent on NMIs, changing it to IPIs will probably break lots of its functionalities. That's why I didn't dare to change it to IPIs yet. 😅
Using IPIs by itself is okay but since HyperDbg is highly dependent on NMIs, changing it to IPIs will probably break lots of its functionalities. That's why I didn't dare to change it to IPIs yet. 😅 -
 ah.. i know only in general what are those interrupts :D not details, so i have to believe You :D
ah.. i know only in general what are those interrupts :D not details, so i have to believe You :D -
 one more issue in github :)
one more issue in github :) - 06 July 2024 (8 messages)
-
 Anyone tried hyperdbg gui?
Anyone tried hyperdbg gui? -
 It's not ready yet. These days I'm working on it together with another team member. I'll let you guys know once it's finished.
It's not ready yet. These days I'm working on it together with another team member. I'll let you guys know once it's finished. -
 @HughEverett
@HughEverett
0: kHyperDbg> !monitor x 8ef7b0 l 1 script {
> printf("trigger\n");
> }
err, invalid address (c0000005)
address may be paged-out or unavailable on the page table due to 'demand paging'
please refer to https://docs.hyperdbg.org/tips-and-tricks/considerations/accessing-invalid-address for further information
0: kHyperDbg>
0: kHyperDbg> u2 8ef7b0
00000000`008ef7b0 83 EC 18 sub esp, 0x18
00000000`008ef7b3 8B 44 24 1C mov eax, dword ptr ss:[esp+0x1C]
00000000`008ef7b7 53 push ebx
00000000`008ef7b8 55 push ebp
00000000`008ef7b9 56 push esi
00000000`008ef7ba 8B 30 mov esi, dword ptr ds:[eax]
...
0: kHyperDbg> bp 8ef7b0
what im doing wrong ?Accessing Invalid Address | HyperDbg DocumentationConsiderations for accessing memory in different modes
-
 (switched to process before)
(switched to process before) -
 ok.. looks like its working with l 4
ok.. looks like its working with l 4 -
 ah... so:
ah... so:
if i put monitor on !monitor x 017CA56B l 3 script {....
and then run for some while and put monitor
!monitor x 8ef7b0 l 1 script {
results to:
trigger
(22:36:23.619 - core : 0 - vmx-root? yes) [+] Information (IdtEmulationhandleHostInterrupt:182) | Page-fault received, CR2: 8ef7b0
(22:36:23.619 - core : 0 - vmx-root? yes) [+] Information (IdtEmulationhandleHostInterrupt:182) | Page-fault received, CR2: 8ef7b0
(22:36:23.619 - core : 0 - vmx-root? yes) [+] Information (IdtEmulationhandleHostInterrupt:182) | Page-fault received, CR2: 8ef7b0
(22:36:23.619 - core : 0 - vmx-root? yes) [+] Information (IdtEmulationhandleHostInterrupt:182) | Page-fault rece
loop.
any ideas ? -
 !monitor x 017CA56B l 3 script { is just reading some registers
!monitor x 017CA56B l 3 script { is just reading some registers -
 so i need to remove 017CA56B monitor first. i definetly know that 017CA56B is calling 8ef7b0
so i need to remove 017CA56B monitor first. i definetly know that 017CA56B is calling 8ef7b0 - 07 July 2024 (19 messages)
-
 Didn't get it 🤔
Didn't get it 🤔
It doesn't work with 1 in the '!monitor'? -
 Could you please make a GitHub issue with the sequence of commands I could reproduce the error?
Could you please make a GitHub issue with the sequence of commands I could reproduce the error?
If there are multiple ways of reproducing error (e.g., it crashes with both 1 and 3 length) make sure to include all sequences separately so all of them will be fixed. -
 Hello guys, I need some help here
Hello guys, I need some help here
I'm trying to install EfiGaurd to disable PatchGaurd in my local machine,
But I cannot find the option to add a boot option, or enter the boot setup.
I disabled the secure boot and make it legacy, but the problem still the same. -

-
 @Mattiwatti The original author is in the group but not sure if he still checks his Telegram since he rarely uses this app.
@Mattiwatti The original author is in the group but not sure if he still checks his Telegram since he rarely uses this app. -

-

-
 As long as I remember, you could boot EfiGuard from a USB.
As long as I remember, you could boot EfiGuard from a USB. -
 BTW, why do you need to disable PatchGuard? The only command that is not PatchGuard compatible in HyperDbg is the '!syscall'. Are you going to intercepts system-calls?
BTW, why do you need to disable PatchGuard? The only command that is not PatchGuard compatible in HyperDbg is the '!syscall'. Are you going to intercepts system-calls? -
 Other commands are perfectly fine with PatchGuard.
Other commands are perfectly fine with PatchGuard. -

-

-
 Not sure if I understand it correctly. Are you going to hook system-call handler using the '!epthook' command? 🤨
Not sure if I understand it correctly. Are you going to hook system-call handler using the '!epthook' command? 🤨 -
 Oh, I feel very stupid right now 😶.
Oh, I feel very stupid right now 😶.
It's just I was going to apply your example that you did in this video about the epthook (that I'm mentioning) but in VMI mode. I thought that it would be ok 😶. -
 As I understand, the epthook will remove the execute permission on that page that holds the code for hooked API, so whenever the caller calls it, it will cause a vm-exit, then the Hypervisor will take control then execute my script then cause vm-continue and continue the execution normally to the guest. I don't know if I understand it right 😶.
As I understand, the epthook will remove the execute permission on that page that holds the code for hooked API, so whenever the caller calls it, it will cause a vm-exit, then the Hypervisor will take control then execute my script then cause vm-continue and continue the execution normally to the guest. I don't know if I understand it right 😶. -
 This example doesn't need patchguard to be disabled. It's works even if PatchGuard is running in both the 'Debugger Mode' and the 'VMI Mode'.
This example doesn't need patchguard to be disabled. It's works even if PatchGuard is running in both the 'Debugger Mode' and the 'VMI Mode'. -
 No, actually this behavior is not for the '!epthook'. The one you mentioned is the scenario where you use the '!monitor x' command. For the '!epthook', the execution bit is in effect while the 'read/write' bits are cleared. There is a hidden breakpoint there (int3 or 0xCC) which will be triggered and handled in the hypervisor whenever the target function is executed. Please take a look at these document pages for more information:
No, actually this behavior is not for the '!epthook'. The one you mentioned is the scenario where you use the '!monitor x' command. For the '!epthook', the execution bit is in effect while the 'read/write' bits are cleared. There is a hidden breakpoint there (int3 or 0xCC) which will be triggered and handled in the hypervisor whenever the target function is executed. Please take a look at these document pages for more information:
- https://docs.hyperdbg.org/design/features/vmm-module/design-of-epthook
- https://docs.hyperdbg.org/design/features/vmm-module/design-of-monitorDesign of !epthook | HyperDbg DocumentationDesign of !epthook command
-
 @HughEverett https://github.com/HyperDbg/HyperDbg/issues/415 i cant clearly reproduce length issue, but reproducing subsequent call monitor is easyCan't set monitors on subsequent calls. · Issue #415 · HyperDbg/HyperDbg
@HughEverett https://github.com/HyperDbg/HyperDbg/issues/415 i cant clearly reproduce length issue, but reproducing subsequent call monitor is easyCan't set monitors on subsequent calls. · Issue #415 · HyperDbg/HyperDbg0: kHyperDbg> x ws2_32!send 00000000`75c658a0 ws2_32!send 0: kHyperDbg> bp 75c658a0 0: kHyperDbg> g debuggee is running... breakpoint 0x1 hit ws2_32!send: 00000000`75c658a0 8B FF mov edi, ...
-
 Thanks, I'll fix it.
Thanks, I'll fix it. - 08 July 2024 (13 messages)
-
 HyperDbg (@HyperDbg) on X
HyperDbg (@HyperDbg) on X🔥 Summer's heating up, and so is the learning! VMware Workstation is now free, making it the perfect time to dive into hypervisor-based reverse engineering. Check out the free HyperDbg tutorial at @OpenSecTraining: https://t.co/I1n3ggYlU9 (preferred) https://t.co/119iZNhSsA
-
 None
None -
 I was not able to reproduce the error using your scripts in the GitHub, but it was reproduced once using this script:
I was not able to reproduce the error using your scripts in the GitHub, but it was reproduced once using this script:
.sym reload pid 3024
.process pid 3024
g
.process
!monitor x ws2_32!send l 3 script {
printf("pre triggered\n");
}
--------------------------------------
g
event c all
g
.process pid 3024
g
.process
--------------------------------------
bp ws2_32!send
!monitor x ws2_32!send l 3 script {
printf("pre triggered\n");
}
.process -
Joined.
-
 But, only one time! Couldn't reproduce it again. It seems to be race condition but in order to investigate it, it needs to be deterministically reproduced.
But, only one time! Couldn't reproduce it again. It seems to be race condition but in order to investigate it, it needs to be deterministically reproduced. -
 I'll keep testing the same scripts to find a way for reproducing it, meanwhile if you find a reproduceable sequence of command, pls send it here.
I'll keep testing the same scripts to find a way for reproducing it, meanwhile if you find a reproduceable sequence of command, pls send it here. -
 Okay, I found a sequence that reproduces the error:
Okay, I found a sequence that reproduces the error:
.sym reload pid 3024
.process pid 3024
g
.process
!monitor x ws2_32!send l 3 script {
printf("pre triggered\n");
}
!monitor x 00354b67 l 3 script {
printf("pre triggered\n");
} -
 Maybe setting vm to use one core might help..
Maybe setting vm to use one core might help.. -
 Fixed. Check the latest 'dev' branch.
Fixed. Check the latest 'dev' branch. -
 Will check later today
Will check later today -
Joined.
-
 all good
all good -
Joined.
- 10 July 2024 (5 messages)
-
 Eduard I fixed this issue, but I'm not sure if I correctly fixed it and it didn't break anything. Once you have free time, please update your 'dev' branch and make a comprehensive test on both the step-over 'p' and the step-in 't', and let me know if you find any problems.
Eduard I fixed this issue, but I'm not sure if I correctly fixed it and it didn't break anything. Once you have free time, please update your 'dev' branch and make a comprehensive test on both the step-over 'p' and the step-in 't', and let me know if you find any problems.
https://github.com/HyperDbg/HyperDbg/issues/406Step over hangs, if process terminates/excepts within call instruction. · Issue #406 · HyperDbg/HyperDbgStepOverTst.zip Steps to reproduce: .start path C:\dbg\StepOverTst.exe 2: kHyperDbg> bp 00007ff7`54c3156c 2: kHyperDbg> g debuggee is running... breakpoint 0x3 hit 00007ff7`54c3156c E8 37 03 ...
-
 You did a great job.
You did a great job. -
 @HughEverett no good :( it solved the issue i mentioned, i can quit waiting with ctrl+c, but introduced another - if i put bp on call instruction and when bp is trapped, when i press p it just continues execution
@HughEverett no good :( it solved the issue i mentioned, i can quit waiting with ctrl+c, but introduced another - if i put bp on call instruction and when bp is trapped, when i press p it just continues execution -
 will prepare another test
will prepare another test -
 sorry.. cant reproduce stable, but i hope in real debug i will understand something
sorry.. cant reproduce stable, but i hope in real debug i will understand something - 11 July 2024 (11 messages)
-
Joined.
-
这个调试器怎么用
-
有没有使用教程
-
-
视频了
-
 You mean the patch (last commit) should be reverted? 🤨
You mean the patch (last commit) should be reverted? 🤨 -
 Or it just sometimes cause errors?
Or it just sometimes cause errors? -

-
 maybe put it to another branch for a while... something has changed, but i dont know exactly what
maybe put it to another branch for a while... something has changed, but i dont know exactly what -
 try, for example, put bp on any call, and when its trapped, execute p
try, for example, put bp on any call, and when its trapped, execute p -
 its like sometimes it steps overs, sometimes it waits for a long time for no reason
its like sometimes it steps overs, sometimes it waits for a long time for no reason - 12 July 2024 (9 messages)
-
Joined.
-
 It's on the 'dev' branch now. Sure we won't release (merge it to the master) if the problem is not yet fixed.
It's on the 'dev' branch now. Sure we won't release (merge it to the master) if the problem is not yet fixed. -
 I'll create a GitHub issue to further investigate it. Meanwhile, if you find a deterministic way of reproducing it, pls let me know.
I'll create a GitHub issue to further investigate it. Meanwhile, if you find a deterministic way of reproducing it, pls let me know. -
 sure, no prob
sure, no prob -
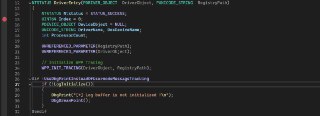
hi guys, I'm trying to use visual studio kernel debug. But there is no current line shown (yellow arrow) in source code when hitting breakpoint
-
only show yellow arrow to the current line in asm
-
any solution ? 😢
-
-
- 13 July 2024 (6 messages)
-
I use Debug mode to compile . I guess the optimization is off
-
the rsp pointing to mov dword ptr [rsp +40h],0 (UINT Index = 0)
-
-
 @HughEverett sorry, i have no time currently, i think i can implement some deterministic test in asm, but it need me to remember asm :) i studied it almost 15 yrs ago, lot of thing have changed, chatgpt also not helping much, but i got some ideas already
@HughEverett sorry, i have no time currently, i think i can implement some deterministic test in asm, but it need me to remember asm :) i studied it almost 15 yrs ago, lot of thing have changed, chatgpt also not helping much, but i got some ideas already -
 in general, it seems, that p bug is related to threading
in general, it seems, that p bug is related to threading -
 e.g. if new thread is spawn within call, then p cant detect ret properly, maybe some cpu optimizations, so thread is started and control flow now belongs to thread, so it wont return until thread is complete (if ever), but thats just assumptions
e.g. if new thread is spawn within call, then p cant detect ret properly, maybe some cpu optimizations, so thread is started and control flow now belongs to thread, so it wont return until thread is complete (if ever), but thats just assumptions - 14 July 2024 (4 messages)
-
 Ok, got it. I'll check it with these new details. Thanks 👍
Ok, got it. I'll check it with these new details. Thanks 👍 -
 @HughEverett im back to debugging and need some advice:
@HughEverett im back to debugging and need some advice:
main:00D6A4BD push [ebp+arg_4]
main:00D6A4C0 push [ebp+arg_0]
main:00D6A4C3 mov eax, [ebp+var_8]
main:00D6A4C6 movzx eax, word ptr [eax]
main:00D6A4C9 push eax
main:00D6A4CA mov eax, [ebp+var_8]
main:00D6A4CD inc eax
main:00D6A4CE inc eax
main:00D6A4CF push eax
main:00D6A4D0 mov ecx, [ebp+var_8]
main:00D6A4D0
main:00D6A4D3 call sub_D6A5E0 ; add c3
main:00D6A4D8 mov esp, ebp
main:00D6A4DA pop ebp
main:00D6A4DB retn 8
main:00D6A4DE
i want to main:00D6A4D3 call sub_D6A5E0 ; add c3 call 5 times instead of one with some interval, now i have:
!monitor x 0D6A4D0 l 2 core 0 stage post script {
if ($context == 0D6A4D0){
for (i = 0; i < 5; i++){
@eip = 00D6A4D3;
}
printf("NOW WILL CALL %x\n",eip);
}
}
but it fails even on first time, when parameters are adequate (instant crash)
i tried to use code {....} but it fails with page fault, any ideas how to do this? -
 This doesn't work as expected. You're trying to change @eip 5 times in one single execution. Doesn't make sense. 🤔
This doesn't work as expected. You're trying to change @eip 5 times in one single execution. Doesn't make sense. 🤔
So, it probably needs to be changed to:
!monitor x 0D6A4D0 l 2 core 0 stage post script {
if ($context == 0D6A4D0){
@eip = 00D6A4D3;
printf("NOW WILL CALL %x\n",eip);
}
} -
 But, that's definitely not a reason for the crash. Is it a crash of HyperDbg (BSOD)? or the target program crashes through SEH?
But, that's definitely not a reason for the crash. Is it a crash of HyperDbg (BSOD)? or the target program crashes through SEH? - 15 July 2024 (34 messages)
-
-
 App crash, hyberdbg is just fine. Yea, just got it that changing eip within one execution is pointless. Is there another way to call some code from script? Like xdbg script .asm sections?
App crash, hyberdbg is just fine. Yea, just got it that changing eip within one execution is pointless. Is there another way to call some code from script? Like xdbg script .asm sections? -
 It's 32 bit app I'm trying to reverse )
It's 32 bit app I'm trying to reverse ) -
 Starting from v0.10 (the next version), HyperDbg uses @keystone_engine as its assembler. ❤️
Starting from v0.10 (the next version), HyperDbg uses @keystone_engine as its assembler. ❤️
Thanks to our new team member @Reverser69 for adding it.
The following commands are added to assemble virtual and physical memory:
- https://docs.hyperdbg.org/commands/debugging-commands/a
- https://docs.hyperdbg.org/commands/extension-commands/aa (assemble virtual address) | HyperDbg DocumentationDescription of the 'a' command in HyperDbg.
-
 None
None -
 No, actually if you wanna call something within an event, it'll be called from VMX root-mode. Though, not sure if it's because you're using it in the post stage or not.
No, actually if you wanna call something within an event, it'll be called from VMX root-mode. Though, not sure if it's because you're using it in the post stage or not.
Can you put the '!monitor' check into the next address (the address after the current @eip) and use it in the regular 'pre' stage? -
 I actually want to call next instruction after monitored address.. I used stage post, because on monitored instruction parameter for call was set, so it will be set up properly..
I actually want to call next instruction after monitored address.. I used stage post, because on monitored instruction parameter for call was set, so it will be set up properly.. -
 I was thinking about it. The thing is, after executing a call (pre stage), an MTF is set to bring the results back (post stage).
I was thinking about it. The thing is, after executing a call (pre stage), an MTF is set to bring the results back (post stage). -
 This MTF will be executed exactly after one instruction. It doesn't work like a step-over, it's like a step-in.
This MTF will be executed exactly after one instruction. It doesn't work like a step-over, it's like a step-in. -
 So, I don't have any idea what's going on inside HyperDbg with a post stage !monitor to a CALL instruction. 🤔
So, I don't have any idea what's going on inside HyperDbg with a post stage !monitor to a CALL instruction. 🤔 -
 The thing that you wanna do, seems more reasonable to be done by using an !epthook. But as probably you're dealing with an executable with lots of anti debugging methods, maybe modifying the stack and putting the return address of a CALL gadget works for this case?
The thing that you wanna do, seems more reasonable to be done by using an !epthook. But as probably you're dealing with an executable with lots of anti debugging methods, maybe modifying the stack and putting the return address of a CALL gadget works for this case? -
 yes, thinking about playing with stack, its a pity, that code {} execution is in vmx-root...
yes, thinking about playing with stack, its a pity, that code {} execution is in vmx-root... -
 epthooks are always detected.. not instantly, but after some time
epthooks are always detected.. not instantly, but after some time -
 FYI, @Reverser69 is now working on bringing the support for assembly codes (keystone) within code {} statements, along with its classic hex format.
FYI, @Reverser69 is now working on bringing the support for assembly codes (keystone) within code {} statements, along with its classic hex format. -
 thats good, but seems wont fix my situation :)
thats good, but seems wont fix my situation :) -
 i will give a try to call eb within script, maybe antidebug wont detect it instantly, so i will manage o put code back :) but there are aligment problems for sure
i will give a try to call eb within script, maybe antidebug wont detect it instantly, so i will manage o put code back :) but there are aligment problems for sure -
 @HughEverett i also wanted to ask - is it possible to implement sleep(x) in script, so it pauses execution for x miliseconds?
@HughEverett i also wanted to ask - is it possible to implement sleep(x) in script, so it pauses execution for x miliseconds? -
 like pause() wait some time and resume
like pause() wait some time and resume -
 Don't have any idea how it's implemented in the OS-level functions or how we can implement it in VMX root-mode. 🤔
Don't have any idea how it's implemented in the OS-level functions or how we can implement it in VMX root-mode. 🤔
Does it need a timer configuration? 🤨 -
 ah... but i need it only for one process, so it wont stop execution of whole vm
ah... but i need it only for one process, so it wont stop execution of whole vm -
 about timer - kernel32!GetTickCount might help
about timer - kernel32!GetTickCount might help -
 (i dont know 64bit windows call)
(i dont know 64bit windows call) -
 in assembly its quite simple to do :D
in assembly its quite simple to do :D -
 call kernel32!SleepEx(time,0). it will break current process for time milis
call kernel32!SleepEx(time,0). it will break current process for time milis -
 HyperDbg is in VMX root-mode, not user-mode 😕
HyperDbg is in VMX root-mode, not user-mode 😕 -
 i mean use sleep implementation as reference
i mean use sleep implementation as reference -
 There are tons of way to do this. Let me find an example from OST2 videos
There are tons of way to do this. Let me find an example from OST2 videos -
 yes, maybe i missed something when watched
yes, maybe i missed something when watched -
 Dbg3301: HyperDbg 10 08 Ignoring Events
Dbg3301: HyperDbg 10 08 Ignoring EventsView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
 This one. You can use the short-circuiting mechanisom along with the !monitor's X attribute to pause the target process.
This one. You can use the short-circuiting mechanisom along with the !monitor's X attribute to pause the target process. -
 i just thought about sc :)
i just thought about sc :) -
 Another option is using the newly added !mode command+event_sc:
Another option is using the newly added !mode command+event_sc:
https://docs.hyperdbg.org/commands/extension-commands/mode!mode (detect kernel-to-user and user-to-kernel transitions) | HyperDbg DocumentationDescription of the '!mode' command in HyperDbg.
-
 ah.. i thought its related to timer somehow, of course i used monitors for pid with sc :)
ah.. i thought its related to timer somehow, of course i used monitors for pid with sc :) -
 @HughEverett looks like i found solution about timer - can you pls add $timeD that returns time as milis, but not string, then by using global vars i can manage timing easily
@HughEverett looks like i found solution about timer - can you pls add $timeD that returns time as milis, but not string, then by using global vars i can manage timing easily - 16 July 2024 (8 messages)
-
 Only time in milis doesn't make sense since it will change each time you try to get it and it takes a long time to be ready (like some functions needed to be called) which makes it not a suitable case.
Only time in milis doesn't make sense since it will change each time you try to get it and it takes a long time to be ready (like some functions needed to be called) which makes it not a suitable case. -
 What about a function for RDTSC/P? 🤨
What about a function for RDTSC/P? 🤨 -
 i understand, my solutions would be something like:
i understand, my solutions would be something like:
if ($time - .oldTime > 200){
.oldTime = $time;
} else {eventsc(1)) -
 i dont need high precision in my case
i dont need high precision in my case -
 looks interesting, i can execute it from code{} part, right ?
looks interesting, i can execute it from code{} part, right ? -
 @HughEverett for now, my goal is achieved :) thanks once again for this great tool. i will continue to explore this app so i can find even more exploits
@HughEverett for now, my goal is achieved :) thanks once again for this great tool. i will continue to explore this app so i can find even more exploits -
 ? .count = 0;
? .count = 0;
? ._ecx = 0;
? ._eax = 0;
? ._ebp = 0;
? ._esp = 0;
? .run = 0;
!monitor x D6A5E0 00D6A7AD script {
if ($context == D6A5E0){
ptr = dd(esp+4);
v0 = db(ptr);
v2 = db(ptr+2);
if ((v0 == c1) && (v2 == b7)) {
printf("process pid %x ctx %x \n",$pid,$context );
._esp = esp;
._ecx = ecx;
if (.count < 5){
printf("count less than 5, duplicating \n");
.run = 1;
} else {
printf("count is 5, stop duplicating \n");
.run = 0;
.count = 0;
}
}
}
if ($context == 00D6A7AD && .run == 1){
printf("process pid %x %x TURBO\n",$pid, .count);
//eax = ._eax;
ecx = ._ecx;
//ebp = ._ebp;
//esp = ._esp;
eip = D6A5E0;
.count = .count + 1;
event_sc(1);
}
} -
 it recursively calls same sub 00D6A7AD in this case 5 times, and then exits
it recursively calls same sub 00D6A7AD in this case 5 times, and then exits - 17 July 2024 (7 messages)
-
 No, I mean a function in the script engine.
No, I mean a function in the script engine. -
 Oh, the problem is solved now?
Oh, the problem is solved now? -
 Timer problem not, but recursive call is
Timer problem not, but recursive call is -
 No problem, I could implement that, but just to confirm it with you, do you expect to sleep() and halt the entire core for a couple of seconds or do you want to make sleep() only the target thread?
No problem, I could implement that, but just to confirm it with you, do you expect to sleep() and halt the entire core for a couple of seconds or do you want to make sleep() only the target thread? -
 mm depends whats simplier :)
mm depends whats simplier :) -
 im fine with both variants
im fine with both variants -
 maybe for single thread will be more useful
maybe for single thread will be more useful - 18 July 2024 (41 messages)
-
Joined.
-
 I think for the thread variant it's better to patch the execution flow (e.g. some assembly codes at @rip or somewhere else), but for the VMX-root variant, I'll try to see what's the best method of adding such a function.
I think for the thread variant it's better to patch the execution flow (e.g. some assembly codes at @rip or somewhere else), but for the VMX-root variant, I'll try to see what's the best method of adding such a function. -
 ? {
? {
void Sleep(int milliseconds) {
.count = 0;
.delay = milliseconds * 1000; // Convert milliseconds to microseconds
while (.delay != 0) {
.delay--;
.count = 1000; // This constant can be adjusted based on the clock speed
while (.count != 0) {
.count--;
// Do nothing, just busy-wait
}
}
}
Sleep(10);
} -
 Eduard What about this one? I test it an it works perfectly. You can adjust waiting time too.
Eduard What about this one? I test it an it works perfectly. You can adjust waiting time too. -
 Wow..looks interesting, already in git?
Wow..looks interesting, already in git? -
 Ah. It's script
Ah. It's script -
 Will test later today
Will test later today -
 ? .count = 0;
? .count = 0;
? ._ecx = 0;
? ._eax = 0;
? ._ebp = 0;
? ._esp = 0;
? .run = 0;
!monitor x D6A5E0 00D6A7AD script {
void Sleep(int milliseconds) {
.count = 0;
.delay = milliseconds * 1000; // Convert milliseconds to microseconds
while (.delay != 0) {
.delay--;
.count = 1000; // This constant can be adjusted based on the clock speed
while (.count != 0) {
.count--;
// Do nothing, just busy-wait
}
}
}
if ($context == D6A5E0){
ptr = dd(esp+4);
v0 = db(ptr);
v2 = db(ptr+2);
if ((v0 == c1) && (v2 == b7)) {
printf("process pid %x ctx %x \n",$pid,$context );
._esp = esp;
._ecx = ecx;
if (.count < 10){
//printf("count less than 16, duplicating \n");
.run = 1;
} else {
printf("count is 16, stop duplicating \n");
.run = 0;
.count = 0;
}
}
}
if ($context == 00D6A7AD && .run == 1){
//printf("process pid %x %x TURBO\n",$pid, .count);
//eax = ._eax;
ecx = ._ecx;
//ebp = ._ebp;
//esp = ._esp;
Sleep(150);
printf("%s",$time);
eip = D6A5E0;
.count = .count + 1;
event_sc(1);
}
}
freezes vm :( -
well, I guess the problem is from the stack buffer in vmx-root
-
@HughEverett is there one more core that run script in vmx-root ?
-
each core should have its own stack buffer to run script
-
so I guess that one core's stack buffer is accessed or modified by other cores at the same time
-
 Each core can run its script independently. Each core has its own stack and could run script simultaneously.
Each core can run its script independently. Each core has its own stack and could run script simultaneously. -
 He uses global variables. Variables start with a '.' means global variables.
He uses global variables. Variables start with a '.' means global variables. -
 If you don't use '.' before name of each variable, it's considered as a local variable (local to each core).
If you don't use '.' before name of each variable, it's considered as a local variable (local to each core). -
 So, I agree with @xmaple555, if your code is supposed to run simultaneously on multiple cores, you need to use local variables instead.
So, I agree with @xmaple555, if your code is supposed to run simultaneously on multiple cores, you need to use local variables instead. -
@sina well, I mean, this script works for one single core
? {
int my_func(int var1) {
if (var1 == 0) {
return 0;
}
if (var1 == 1) {
return 1;
}
return my_func(var1 - 1) + my_func(var1 - 2);
}
var = my_func(9);
printf("%d\n", var);
}
but , there is problem for multi-core
!epthook ntopenprocess script {
int my_func(int var1) {
if (var1 == 0) {
return 0;
}
if (var1 == 1) {
return 1;
}
return my_func(var1 - 1) + my_func(var1 - 2);
}
var = my_func(9);
printf("%d, %s, %d\n", var, $pname, $core);
} -
is the page faulted caused by accessing invalid memory ?
-
 It should work on multi-core unless there is a error.
It should work on multi-core unless there is a error. -
 It needs to be investigated, if you have Windbg attached, you could comment this line:
It needs to be investigated, if you have Windbg attached, you could comment this line: -

-
can we use windbg to debug hypervisor now ?
-
 Once you comment #pf line, all page-faults in the VMX root-mode will be passed to the Windows handler (which is WinDbg) and you could see the exact location of the crash.
Once you comment #pf line, all page-faults in the VMX root-mode will be passed to the Windows handler (which is WinDbg) and you could see the exact location of the crash. -
 Yes, the main debugger we used to debug HyperDbg is windbg+serial handler of HyperDbg itself. It works on all cases.
Yes, the main debugger we used to debug HyperDbg is windbg+serial handler of HyperDbg itself. It works on all cases. -
 Just make sure to comment this line and !analyze -v in windbg will tell you where page-fault happens.
Just make sure to comment this line and !analyze -v in windbg will tell you where page-fault happens. -
@HughEverett nice, it helps a lot for developing the hypervisor
-
well, it seems like not able to use t or p to debug each code line
-
but now I did it for dump crash analysis
-
 Yes, it's not that straightforward. You can do single stepping but it takes a lot of time to get the execution cobtext again and sometimes it doesn't work (like after 4 or 5 single steppings).
Yes, it's not that straightforward. You can do single stepping but it takes a lot of time to get the execution cobtext again and sometimes it doesn't work (like after 4 or 5 single steppings). -
 I usually use our magical 'LogInfo' function which immediately sends the results over serial and it effectively works as the main printf-debugging function of the VMX root-mode.
I usually use our magical 'LogInfo' function which immediately sends the results over serial and it effectively works as the main printf-debugging function of the VMX root-mode. -
 'LogInfo' is guaranteed to send the results immediately without buffering them in the Debugger Mode. But, in the VMI Mode, it first buffers the logs and then sends them to the user-mode whenever it's possible.
'LogInfo' is guaranteed to send the results immediately without buffering them in the Debugger Mode. But, in the VMI Mode, it first buffers the logs and then sends them to the user-mode whenever it's possible. -
@HughEverett well, is there any tip to debug something that executes in multi-core? for now, the script engine function can work in one single core, but not really sure what happen in multi-core
-
 You could run scripts within an event with a high rate of execution.
You could run scripts within an event with a high rate of execution.
E.g.:
!epthook nt!ExAllocatePoolWithTag script { blah blah }
All cores definitely run your scripts simultaneously in this special case. -
 Because the execution rate of 'nt!ExAllocatePoolWithTag' is high enough to make them run simultaneously.
Because the execution rate of 'nt!ExAllocatePoolWithTag' is high enough to make them run simultaneously. -
 its not, process is single threaded, but i'll give a try in hour or so
its not, process is single threaded, but i'll give a try in hour or so -
 nop...
nop...
? .count = 0;
? ._ecx = 0;
? ._eax = 0;
? ._ebp = 0;
? ._esp = 0;
? .run = 0;
!monitor x D6A5E0 00D6A7AD script {
void Sleep(int milliseconds) {
cntr = 0;
int delay = milliseconds * 1000; // Convert milliseconds to microseconds
while (delay != 0) {
delay--;
cntr = 1000; // This constant can be adjusted based on the clock speed
while (cntr != 0) {
cntr--;
// Do nothing, just busy-wait
}
}
}
if ($context == D6A5E0){
ptr = dd(esp+4);
v0 = db(ptr);
v2 = db(ptr+2);
if ((v0 == c1) && (v2 == b7)) {
printf("process pid %x ctx %x \n",$pid,$context );
._esp = esp;
._ecx = ecx;
if (.count < 10){
//printf("count less than 16, duplicating \n");
.run = 1;
} else {
printf("count is 16, stop duplicating \n");
.run = 0;
.count = 0;
}
}
}
if ($context == 00D6A7AD && .run == 1){
//printf("process pid %x %x TURBO\n",$pid, .count);
//eax = ._eax;
ecx = ._ecx;
//ebp = ._ebp;
//esp = ._esp;
printf("%s",$time);
Sleep(150);
eip = D6A5E0;
.count = .count + 1;
event_sc(1);
}
}
this also fails -
 vm freeze
vm freeze -
 output:
output:
process pid 1fa0 ctx d6a5e0
23:54:48.793
freeze -
 ok... looks like counter and delay shall be adjusted, with original provided values it froze, when i put int delay = milliseconds * 10; it more less ok
ok... looks like counter and delay shall be adjusted, with original provided values it froze, when i put int delay = milliseconds * 10; it more less ok -
 so, on my pc its not stable:
so, on my pc its not stable:
? {
void Sleep(int milliseconds) {
.count = 0;
.delay = milliseconds; // Convert milliseconds to microseconds
printf("before\n");
while (.delay != 0) {
.delay--;
.count = 10; // This constant can be adjusted based on the clock speed
while (.count != 0) {
.count--;
// Do nothing, just busy-wait
}
}
printf("after\n");
}
Sleep(1);
}
sometimes it runs instantly, sometimes not -
 i think its related to cpu clock speed - as i have dynamic frequency
i think its related to cpu clock speed - as i have dynamic frequency - 19 July 2024 (17 messages)
-
 Yes, the CPU clock speed is an important factor in this case.
Yes, the CPU clock speed is an important factor in this case. -
 Is the problem solved? Or it still freezes the debuggee? 🤨
Is the problem solved? Or it still freezes the debuggee? 🤨 -
I'm rewriting the parser and code execution. I think the problem will be fixed soon
-
 Are you working on rewriting the parser of the script engine? Or the main parser of commands?
Are you working on rewriting the parser of the script engine? Or the main parser of commands? -
 @Reverser69 finished rewriting the parser of commands yesterday.
@Reverser69 finished rewriting the parser of commands yesterday. -
Merge pull request #434 from HyperDbg/Abbas-MG-parser · HyperDbg/HyperDbg@98ebfae
parser and "0n" prefix
-
 Yes
Yes -
-
 But it's for command (libhyperdbg.dll), not the script engine.
But it's for command (libhyperdbg.dll), not the script engine. -
I'm current rewrite the code generation of lr parser
-
 Oh, okay, you're working on parser of script engine
Oh, okay, you're working on parser of script engine -
and code execution (ScriptEngineExecute)
-
yes
-
 It's okay, he was working on something else.
It's okay, he was working on something else. -
 No collision
No collision -
 👍
👍 -
 its not freezing, but works unstable, even with same values, interval is different
its not freezing, but works unstable, even with same values, interval is different - 20 July 2024 (10 messages)
-
 So I assume that, this is not a problem with HyperDbg?
So I assume that, this is not a problem with HyperDbg? -
 Since the interval depends on CPU clock speed
Since the interval depends on CPU clock speed -
 Also, we need to have a discussion about this one.
Also, we need to have a discussion about this one. -
 It's a new change proposed by @xmaple555.
It's a new change proposed by @xmaple555.
I'm not sure if it's a good idea of having a limitation for the number of IRs that could be executed. -
 What do you guys think ? Does anybody have any idea regarding this one?
What do you guys think ? Does anybody have any idea regarding this one? -
 🤔
🤔 -
 Mm I would say it is.. as sometimes with minimal interval it returns instantly, sometimes waits up to 10 seconds, in the sample you provided, it never waited for 10 milliseconds, but much longer
Mm I would say it is.. as sometimes with minimal interval it returns instantly, sometimes waits up to 10 seconds, in the sample you provided, it never waited for 10 milliseconds, but much longer -
 Maybe not with hyperdbg but scripting engine
Maybe not with hyperdbg but scripting engine -
 i will try to apply interlocked exchange later, and see if it helps
i will try to apply interlocked exchange later, and see if it helps -
 but as i said, i just ran example, and wait time is different :(
but as i said, i just ran example, and wait time is different :( - 21 July 2024 (26 messages)
-
 I've looked into the sleep implementation in the OS, and it seems quite complex because it uses an external device timer. ☹️
I've looked into the sleep implementation in the OS, and it seems quite complex because it uses an external device timer. ☹️ -
 That's no good... maybe some vmware stuff(like drivers) can help?
That's no good... maybe some vmware stuff(like drivers) can help? -
 https://learn.microsoft.com/en-us/windows-hardware/drivers/ddi/wdm/nf-wdm-kedelayexecutionthread @HughEverett might this help?KeDelayExecutionThread function (wdm.h) - Windows drivers
https://learn.microsoft.com/en-us/windows-hardware/drivers/ddi/wdm/nf-wdm-kedelayexecutionthread @HughEverett might this help?KeDelayExecutionThread function (wdm.h) - Windows driversThe KeDelayExecutionThread routine puts the current thread into an alertable or nonalertable wait state for a specified interval.
-
it requires IRQL level
-
 https://learn.microsoft.com/en-us/windows-hardware/drivers/ddi/wdm/nf-wdm-kequerysystemtime-r1 this? If we have system time, implementation of sleep shall not be complexKeQuerySystemTime function (wdm.h) - Windows drivers
https://learn.microsoft.com/en-us/windows-hardware/drivers/ddi/wdm/nf-wdm-kequerysystemtime-r1 this? If we have system time, implementation of sleep shall not be complexKeQuerySystemTime function (wdm.h) - Windows driversThe KeQuerySystemTime routine obtains the current system time.
-
 VMware? 🤨
VMware? 🤨 -
 Exactly. In the VMX root-mode, interrupts are masked (RFLAG.IF is cleared).
Exactly. In the VMX root-mode, interrupts are masked (RFLAG.IF is cleared). -
 This is exactly same as the function we used for the $time pseudo-register.
This is exactly same as the function we used for the $time pseudo-register. -
 ok.. but I asked for $time register to return time as milis :) then by using global vars i can implement smth looking as sleep
ok.. but I asked for $time register to return time as milis :) then by using global vars i can implement smth looking as sleep -
 i thought maybe there is some vmware API, didnt studied that question deep
i thought maybe there is some vmware API, didnt studied that question deep -
 I think you can use this $time for this purpose too. By default, it returns a pointer to a string.
I think you can use this $time for this purpose too. By default, it returns a pointer to a string. -
 Also, dslang supports dereferencing (memory access) through & operator.
Also, dslang supports dereferencing (memory access) through & operator. -
 i also thought about another idea:
i also thought about another idea:
is it possible to write some value inside memory and then read it from script, lets say:
!monitor .... code {
push rdx;
push rax;
rdtsc;
mov [vmx_root_offset_any], rax ;lo bits
mov [vmx_root_offset_any+8], rdx ;hi bits
ret
}
script {
n = dq(vmx_root_offset_any);
k = dq(vmx_root_offset_any+8);
rsp = rsp + 16; //move esp back
// do something
} -
I think I can include the inline asm to script-engine
-
 it would be perfect actually :)
it would be perfect actually :) -
 but $time returns pointer to string.. of course i can modify hyperdbg source code as well
but $time returns pointer to string.. of course i can modify hyperdbg source code as well -
 just thinking how to deal with this situation
just thinking how to deal with this situation
!monitor .... code {
this i executed in vm root, with kernel addressspace
push rdx;
push rax;
rdtsc;
mov [vmx_root_offset_any], rax ;lo bits
mov [vmx_root_offset_any+8], rdx ;hi bits
ret
}
script {
this executed in process address space
n = dq(vmx_root_offset_any);
k = dq(vmx_root_offset_any+8);
rsp = rsp + 16; //move esp back
// do something
}
correct me if im using bad terminology :) -
 It would be great if we can have such a feature. You can use the Keystone disassembler that is recently added to the project.
It would be great if we can have such a feature. You can use the Keystone disassembler that is recently added to the project. -
 You can add (+x) number to the time and read it using db, or dd. Like db($time+123)
You can add (+x) number to the time and read it using db, or dd. Like db($time+123) -
not a problem. BTW I plan the next update will be variable type, array, pointer, deference, and followed by struct
-
Joined.
-
Hey! Junior Vulnerability Researcher and Reverse Engineer here who's been really liking HyperDbg! Any way I could help contribute!
-
 Hi and welcome to the group. 🤗
Hi and welcome to the group. 🤗
Tomorrow, we'll release HyperDbg v0.10.
Along with that, I'll create a list of potential tasks that you (and anyone else) could add to the HyperDbg. I'll notify you when the list is ready (hopefully tomorrow). -
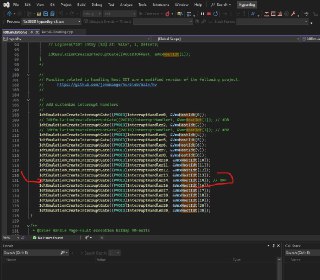
 Eduard please don't forget to check this as well.
Eduard please don't forget to check this as well.
https://github.com/HyperDbg/HyperDbg/issues/417
If it's solved, please close this issue.Script with functions going crazy · Issue #417 · HyperDbg/HyperDbg!monitor x 00D6A712 l 2 script { void printMemDD(int addr){ dlen = 20; for (i = 0; i < dlen; i = i + 4){ printf("%x ", dd(addr + i)); } printf("\n"); return; } void printMemB...
-
Thanks! Good timing on my part lol!
-
 sure
sure - 22 July 2024 (24 messages)
-
 Happy to announce @HyperDbg v0.10! 🎉🎊✨
Happy to announce @HyperDbg v0.10! 🎉🎊✨
This version comes with numerous bug fixes and stability improvements, plus new features like running assembly code directly in the events (VMX root-mode) and two new commands.
Check out the latest version: https://github.com/HyperDbg/HyperDbg/releases
For more information,
Assembly codes in conditions:
- https://docs.hyperdbg.org/using-hyperdbg/prerequisites/how-to-create-a-condition
Assembly codes in code sections:
- https://docs.hyperdbg.org/using-hyperdbg/prerequisites/how-to-create-an-action
Assemble virtual address:
- https://docs.hyperdbg.org/commands/debugging-commands/a
Assemble physical address:
- https://docs.hyperdbg.org/commands/extension-commands/aReleases · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 # Changelog
# Changelog
## Added
- Support using assembly conditions and codes in all events
- Added the assembler command 'a' for virtual memory
- Added the assembler command '!a' for physical memory
- Providing a unified SDK API for reading memory in the VMI Mode and the Debugger Mode
- Export SDK APIs for reading/writing into registers in the Debugger Mode
- Export SDK API for writing memory in the VMI Mode and the Debugger Mode
- Export SDK API for getting kernel base address
- Export SDK API for connecting to the debugger and from debuggee in the Debugger Mode
- Export SDK API for starting a new process
- Add and export SDK API for unsetting message callback
- Event commands are coming with more examples regarding scripts and assembly codes
- Add message callback using shared memory
- Add maximum execution limitation to the script IRs (#435)
## Changed
- Fix clearing '!monitor' hooks on a different process or if the process is closed (#409)
- Fix triggering multiple '!monitor' hooks with different contexts (#415)
- Fix the problem of repeating commands once kHyperDbg is disconnected
- Fix step-over hangs if the process terminates/excepts within call instruction (#406)
- Fix crash on editing invalid physical addresses (#424)
- Fix exporting VMM module load and install it in the SDK
- Fix function interpretation issues and update the parser and the code execution (#435) -
 Thanks to @xmaple555 and @Reverser69 for their great contributions in this release. ❤️
Thanks to @xmaple555 and @Reverser69 for their great contributions in this release. ❤️ -
 Right on
Right on -
 None
None -
 Here is an updated list of tasks that needs contributions from the community members:
Here is an updated list of tasks that needs contributions from the community members:
https://github.com/HyperDbg/HyperDbg/blob/dev/CONTRIBUTING.mdHyperDbg/CONTRIBUTING.md at dev · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 cc @supermanfranky
cc @supermanfranky -
Thanks!
-
Congrats on the release!
-
-
 I just wonder whether there is any plan for adding something like import or #include to the dslang scripts?
I just wonder whether there is any plan for adding something like import or #include to the dslang scripts? -
 This one is really something if it could be added! @xmaple555 🤔
This one is really something if it could be added! @xmaple555 🤔 -
 My first idea is passing a pointer to a buffer where links for the buffers of scripts are stored.
My first idea is passing a pointer to a buffer where links for the buffers of scripts are stored. -
 This way, we could even pre-load a bunch of standard scripts.
This way, we could even pre-load a bunch of standard scripts. -
if you mean include the C file to the script-engine, that must be really difficult to do it
-
 No, I think he means include of .ds files.
No, I think he means include of .ds files. -
 C files needs compiler which is really hard to do.
C files needs compiler which is really hard to do. -
 But, .ds files might be good if we could implement functions in it and import it to other .ds files.
But, .ds files might be good if we could implement functions in it and import it to other .ds files. -
 Not sure if it's possible 🤔
Not sure if it's possible 🤔 -
 We could start implementing standard script functions.
We could start implementing standard script functions. -
😅, the current grammar of the script-engine is free ambiguous, so it is not difficult like C to implement it
-
 I think some functionalities like Windows-specific routines (and in the future other functions) that needs interaction with symbols (structure offsets and function addresses) are better to be implemented in the script-engine.
I think some functionalities like Windows-specific routines (and in the future other functions) that needs interaction with symbols (structure offsets and function addresses) are better to be implemented in the script-engine. -
 This way, we could add lots of cool functions for modifying Windows as a standard library (say Windows.ds), and then import it and use it in the scripts.
This way, we could add lots of cool functions for modifying Windows as a standard library (say Windows.ds), and then import it and use it in the scripts. -
 This would be super cool! 👌🤔
This would be super cool! 👌🤔 - 23 July 2024 (6 messages)
-
Joined.
-
Joined.
-
 Joined.
Joined. -
 Joined.
Joined. -
 Joined.
Joined. -
 Joined.
Joined. - 24 July 2024 (8 messages)
-
 Joined.
Joined. -
-
 Joined.
Joined. -
 Joined.
Joined. -
Joined.
-
 Joined.
Joined. -
Joined.
-
 Joined.
Joined. - 25 July 2024 (2 messages)
-
 Joined.
Joined. -
Joined.
- 26 July 2024 (17 messages)
-
-
 If you mean v0.10, then unfortunately no! ☹️
If you mean v0.10, then unfortunately no! ☹️ -
 I spent time on finding the issue but it seems that it needs more investigation, I added it to the contributing list (to-do) list.
I spent time on finding the issue but it seems that it needs more investigation, I added it to the contributing list (to-do) list. -
-
 Is it deleted? 🤨
Is it deleted? 🤨 -
 Forgot to say that #HyperDbg v0.10 also supports event forwarding to external binary (DLLs) modules.
Forgot to say that #HyperDbg v0.10 also supports event forwarding to external binary (DLLs) modules.
- If you want to use HyperDbg events in your function, check out the guide:
https://docs.hyperdbg.org/tips-and-tricks/misc/event-forwarding
- Rust/C++ implementations are available here:
https://github.com/HyperDbg/event-forwarding-examplesEvent forwarding | HyperDbg DocumentationBrief explanation about Event Forwarding Mechanism
-
-
-
Joined.
-
-
 Ah, it seems to be deleted. 😔
Ah, it seems to be deleted. 😔 -
 What do you mean by return trap flag from cpuid? 🤨
What do you mean by return trap flag from cpuid? 🤨 -
Joined.
-
emote project
-
-
 In the Debugger Mode, if the debugee is paused, you could view/modify the trap flag using the 'r' command.
In the Debugger Mode, if the debugee is paused, you could view/modify the trap flag using the 'r' command. -
 It's also accessible through the script engine using @rflag register.
It's also accessible through the script engine using @rflag register. - 27 July 2024 (2 messages)
-

-

- 28 July 2024 (4 messages)
-

-
there was a solution to this problem in the cpuid_flags_tf branch https://howtohypervise .blogspot.com/2019/01/a-common-missight-in-most-hypervisors.html . Is it possible to return this branch?
-
 It seems that it's deleted.
It seems that it's deleted.
https://stackoverflow.com/questions/2613903/does-deleting-a-branch-in-git-remove-it-from-the-historyDoes deleting a branch in git remove it from the history?Coming from svn, just starting to become familiar with git. When a branch is deleted in git, is it removed from the history? In svn, you can easily recover a branch by reverting the delete opera...
-
 I don't remember what I did on that branch, did you clone it somewhere in your computer?
I don't remember what I did on that branch, did you clone it somewhere in your computer? - 29 July 2024 (10 messages)
-
 Hi everyone!
Hi everyone!
We've updated the list of things for which we need contributions from the community in HyperDbg!
If you have some free time, you're more than welcome to join and contribute to the HyperDbg debugger. 😊✨
Check it out:
https://github.com/HyperDbg/HyperDbg/blob/dev/CONTRIBUTING.md -
 None
None -
there is no copy of the source code left(((
-
Is there any desire to detect and inspect undocumented windows kerbel structures.
Such as these: https://www.vergiliusproject.com/kernels/x64Vergilius ProjectTake a look into the depths of Windows kernels and reveal more than 60000 undocumented structures.
-
Also, is there desire to be able to print the dump the page table for a process?
-
 [discord] <oi_its_me> Test
[discord] <oi_its_me> Test -
 What do you mean by inspecting kernel structures?
What do you mean by inspecting kernel structures?
Is it anything other than the 'struct' command?
https://docs.hyperdbg.org/commands/debugging-commands/structstruct (make structures, enums, data types from symbols) | HyperDbg DocumentationDescription of the 'struct' command in HyperDbg.
-
 Dump of all page tables?
Dump of all page tables?
HyperDbg already shows the page table entries, but won't dump them. You could use a combination of the '!pte' command + the '.dump' command to perform that.
https://docs.hyperdbg.org/commands/extension-commands/pte
https://docs.hyperdbg.org/commands/meta-commands/.dump!pte (display page-level address and entries) | HyperDbg DocumentationDescription of the '!pte' command in HyperDbg.
-
Joined.
-

- 30 July 2024 (1 messages)
-

- 01 Jul 2024 (9)
- 02 Jul 2024 (11)
- 03 Jul 2024 (60)
- 04 Jul 2024 (7)
- 05 Jul 2024 (24)
- 06 Jul 2024 (8)
- 07 Jul 2024 (19)
- 08 Jul 2024 (13)
- 10 Jul 2024 (5)
- 11 Jul 2024 (11)
- 12 Jul 2024 (9)
- 13 Jul 2024 (6)
- 14 Jul 2024 (4)
- 15 Jul 2024 (34)
- 16 Jul 2024 (8)
- 17 Jul 2024 (7)
- 18 Jul 2024 (41)
- 19 Jul 2024 (17)
- 20 Jul 2024 (10)
- 21 Jul 2024 (26)
- 22 Jul 2024 (24)
- 23 Jul 2024 (6)
- 24 Jul 2024 (8)
- 25 Jul 2024 (2)
- 26 Jul 2024 (17)
- 27 Jul 2024 (2)
- 28 Jul 2024 (4)
- 29 Jul 2024 (10)
- 30 Jul 2024 (1)