- 01 April 2024 (1 messages)
-

- 04 April 2024 (53 messages)
-

-
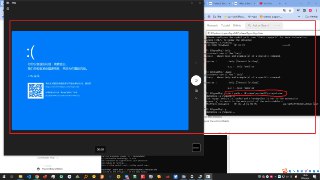
 hi, everyone, i fellow the instructions of the webpage(https://docs.hyperdbg.org/getting-started/attach-to-hyperdbg/start-process), but failed, why was that?Start a new process | HyperDbg Documentation
hi, everyone, i fellow the instructions of the webpage(https://docs.hyperdbg.org/getting-started/attach-to-hyperdbg/start-process), but failed, why was that?Start a new process | HyperDbg DocumentationStarting a process from entrypoint
-

-
 i used the efiguard to disable the vbs and the hvci was closed
i used the efiguard to disable the vbs and the hvci was closed -
 my processor is i7 6700, and the os is win10
my processor is i7 6700, and the os is win10 -
 i used the physical pc as the client
i used the physical pc as the client -

-

-
 Joined.
Joined. -
 Hi,
Hi,
Your processor is kinda old, it's a skylake processor, but there shouldn't be problem. As it caused bsod, WinDbg will grab the error. If you can get the result of the '!analyze -v', then we could investigate the error. -
 This is so general view of the error, further information is needed to find the bug that caused this error.
This is so general view of the error, further information is needed to find the bug that caused this error. -
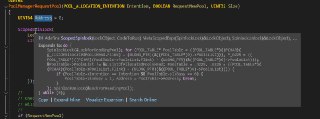
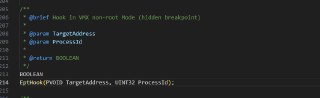
@HughEverett hi, I'm learning to try to use HOOK and then I find that it consistently fails, I debug and find that the Address in the PoolManagerRequestPool is always 0, am I missing something?
-
&PoolTable->PoolsList ! = &g_ListOfAllocatedPoolsHead is always equal resulting in not going inside the loop to set address
-
 Can you tell me how can I reproduce the error?
Can you tell me how can I reproduce the error? -
 Are you using the latest version?
Are you using the latest version? -
yes
-
I am using v0.8.2 version and then I will call EptHookInlineHook and this error occurs within its internal trigger
-
I referenced this use case https://github.com/HyperDbg/HyperDbg/blob/master/hyperdbg/hprdbghv/code/hooks/syscall-hook/SsdtHook.cHyperDbg/hyperdbg/hprdbghv/code/hooks/syscall-hook/SsdtHook.c at master · HyperDbg/HyperDbg
State-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 Are you using HyperDbg as library (dll)?
Are you using HyperDbg as library (dll)? -
 Call the routines directly?
Call the routines directly? -
No, I created a test driver project using hprdbghv, then manually loaded and initialized hv (it returned success), then called EptHookInlineHook.
-
I called them from driverentry.
-
 The reason why you got those errors is because you didn't pre-allocate (initialized) the pool manager, as HyperDbg automatically manages it.
The reason why you got those errors is because you didn't pre-allocate (initialized) the pool manager, as HyperDbg automatically manages it. -
 You can use this function to reserve pre-allocated pools:
You can use this function to reserve pre-allocated pools:
https://github.com/HyperDbg/HyperDbg/blob/103874d777d681324ac61948c8eae06a237ae812/hyperdbg/hprdbghv/code/hooks/ept-hook/EptHook.c#L70HyperDbg/hyperdbg/hprdbghv/code/hooks/ept-hook/EptHook.c at 103874d777d681324ac61948c8eae06a237ae812 · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 Make sure to run this function only in PASSIVE_LEVEL. Don't call it from VMX root mode.
Make sure to run this function only in PASSIVE_LEVEL. Don't call it from VMX root mode. -
Aha, I thought hv initialization would automatically get everything ready and I saw that PoolManagerRequestPool internal PoolManagerRequestAllocation would request it again (I called hook multiple times without success), so that's why 😂. I'll try again.
-
 Other than that, it's better not to use this exmple as a reference. There is another usage from the debugger, which is the valid call to this function. The link you sent is not tested/maintained for years. I should remove that.
Other than that, it's better not to use this exmple as a reference. There is another usage from the debugger, which is the valid call to this function. The link you sent is not tested/maintained for years. I should remove that. -
Where to find another example of usage
-
 EPT hook is fundamentally an event which is categorized as a KD task, not a HV task. So, it's the responsibility of the debugger to take care of its pools.
EPT hook is fundamentally an event which is categorized as a KD task, not a HV task. So, it's the responsibility of the debugger to take care of its pools. -
 Let me find it.
Let me find it. -
 HyperDbg/hyperdbg/hprdbghv/code/interface/Configuration.c at 103874d777d681324ac61948c8eae06a237ae812 · HyperDbg/HyperDbg
HyperDbg/hyperdbg/hprdbghv/code/interface/Configuration.c at 103874d777d681324ac61948c8eae06a237ae812 · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
It looks like the two seem to be the same (in terms of passing parameters) and I don't see any difference 😅
-
 That could be the case. As it that piece of code is not used, I wasn't sure whether it's working or not.
That could be the case. As it that piece of code is not used, I wasn't sure whether it's working or not. -
 Anyway, you have plenty of limitations on inline EPT hooks (or !epthook2). It's always better to use the classic EPT hook (!epthook).
Anyway, you have plenty of limitations on inline EPT hooks (or !epthook2). It's always better to use the classic EPT hook (!epthook).
Some of these limitations are explained here (the "Remarks" section):
https://docs.hyperdbg.org/commands/extension-commands/epthook2!epthook2 (hidden hook with EPT - detours) | HyperDbg DocumentationDescription of the '!epthook2' command in HyperDbg.
-
but epthook does not provide the HookFunction parameter
-
so I don't know how to make it jump to my code
-
 All of HyperDbg events eventually call a callback function named 'DebuggerTriggerEvent'. You can put your codes there.
All of HyperDbg events eventually call a callback function named 'DebuggerTriggerEvent'. You can put your codes there. -
 HyperDbg/hyperdbg/hprdbghv/code/interface/Dispatch.c at 103874d777d681324ac61948c8eae06a237ae812 · HyperDbg/HyperDbg
HyperDbg/hyperdbg/hprdbghv/code/interface/Dispatch.c at 103874d777d681324ac61948c8eae06a237ae812 · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
i found it. I'll try it later.
-
 This one, put your hook/code here.
This one, put your hook/code here. -
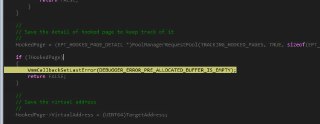
I called ConfigureEptHookReservePreallocatedPoolsForEptHooks before calling the hook but it still returns null!
-
I thought it was DebuggerTriggerEvents 😅.
-
 Ah, forgot to tell you, once you called this function, then call 'PoolManagerCheckAndPerformAllocationAndDeallocation()' to perform the actual allocation.
Ah, forgot to tell you, once you called this function, then call 'PoolManagerCheckAndPerformAllocationAndDeallocation()' to perform the actual allocation. -
 DebuggerTriggerEvent is a function in hprdbgkd, not hprdbghv. So, if you just wanted to use hypervisor and not debugger, then that couldn't be used.
DebuggerTriggerEvent is a function in hprdbgkd, not hprdbghv. So, if you just wanted to use hypervisor and not debugger, then that couldn't be used. -
This seems to require me to manually write the code to the internals of the hv, I don't want to break the internals, is there a callback provided.
-
 Not yet, but you can use hprdbgkd. This driver uses the hv with all needed initializations and considerations.
Not yet, but you can use hprdbgkd. This driver uses the hv with all needed initializations and considerations. -
okay, I'll see how it works.
-
 I think the handler has to do some necessary things. This function was not supposed to be used this way, it probably needs lots of modification.
I think the handler has to do some necessary things. This function was not supposed to be used this way, it probably needs lots of modification.
Why don't you use hprdbgkd directly? You can add your code to hprdbgkd and develop your driver along with that driver in the same code base solution. -
Because I want to add functions step by step to learn, if I use hprdbgkd then I have to look at the code content in this project now. I want to put it on the back burner🙈
-
I‘m now trying to learn to use the whole project
-
 That's okay. 👍
That's okay. 👍 -
 Actually, I should improve the SDK and document its functions.
Actually, I should improve the SDK and document its functions. -
It took me some more time to realize that I probably understood some of the logic. I used the wrong method before
- 05 April 2024 (8 messages)
-
 Is your problem fixed now? Did you successfully call the EPT function in your custom module?
Is your problem fixed now? Did you successfully call the EPT function in your custom module? -
Not yet, I mean I might (should) have read part of the hook handling logic
-
@HughEverett I was reading about the !epthook related handler function, and how I can modify the rip internally in order to make it jump to my function, and I don't see the code to modify the rip. It seems that the original function is still executed even after debugger processing.
-
 In case of !epthook (not !epthook2), you can change the RIP from VMCS using VMWRITE instruction on GUEST_RIP.
In case of !epthook (not !epthook2), you can change the RIP from VMCS using VMWRITE instruction on GUEST_RIP. -
 Just curious to know, is what you trying to do with HyperDbg is also possible by writing scripts?
Just curious to know, is what you trying to do with HyperDbg is also possible by writing scripts?
https://docs.hyperdbg.org/commands/scripting-language -
 Generally, the recommended way of using HyperDbg is to use the script engine as there are tens of technical difficulties and considerations that are all checked once you use an script.
Generally, the recommended way of using HyperDbg is to use the script engine as there are tens of technical difficulties and considerations that are all checked once you use an script. -
Why isn't https://github.com/HyperDbg/RedDbg in the same project as hyperdbg, theoretically it's reusable except for the different hv implementation.GitHub - HyperDbg/RedDbg: Hypervisor-based debugger for AMD processors
Hypervisor-based debugger for AMD processors. Contribute to HyperDbg/RedDbg development by creating an account on GitHub.
-
 It will join HyperDbg in the future, currently it's on R&D phase.
It will join HyperDbg in the future, currently it's on R&D phase. - 06 April 2024 (17 messages)
-

-

-

-
 No, that's not possible as Intel prevents it. But, if you specify such a configuration in the '!monitor' command, HyperDbg will silently set this attribute bit, but won't trigger an event once such an event happens in the system. It works as expected, except that some of the events are ignored in the debugger side.
No, that's not possible as Intel prevents it. But, if you specify such a configuration in the '!monitor' command, HyperDbg will silently set this attribute bit, but won't trigger an event once such an event happens in the system. It works as expected, except that some of the events are ignored in the debugger side. -

-
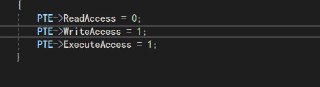
 Sorry man, but that's not true. Execute-only is a totaly valid setting for EPT PTE (Unlike regular MMU PTE)
Sorry man, but that's not true. Execute-only is a totaly valid setting for EPT PTE (Unlike regular MMU PTE) -
 Of course, some of the platforms don't support that combination, but those are really old
Of course, some of the platforms don't support that combination, but those are really old -

-
 "Execute-only allowed in EPT"
"Execute-only allowed in EPT" -
 *UPD* I misread the config that was requested. I thought it was "execute only".
*UPD* I misread the config that was requested. I thought it was "execute only". -
 If you want "W" without "R", it's a EPT misconfig
If you want "W" without "R", it's a EPT misconfig -

-

-
 Execute-only is valid but he sets the write access without setting a read access which HyperDbg will set the read bit in these cases.
Execute-only is valid but he sets the write access without setting a read access which HyperDbg will set the read bit in these cases. -
 Yes, I mean this one.
Yes, I mean this one. -
 Yeah, sorry, I misread that
Yeah, sorry, I misread that -
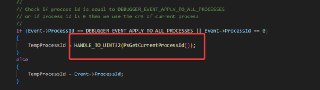
@HughEverett I have a question: if you get the id of the current process here, why does it enable the hook for all processes?
- 07 April 2024 (2 messages)
-
 If you apply it to the kernel or shared user libraries (DLLs), then it will be triggered for all processes.
If you apply it to the kernel or shared user libraries (DLLs), then it will be triggered for all processes. -
 EPT hooks are mainly based on physical addresses. So, if someone puts a hook somewhere that is shared between different processes, then all of them will trigger the hook.
EPT hooks are mainly based on physical addresses. So, if someone puts a hook somewhere that is shared between different processes, then all of them will trigger the hook. - 08 April 2024 (21 messages)
-
 Thank you for your reply, i will try it later. thank you again.
Thank you for your reply, i will try it later. thank you again. -
 My consideration is that it may be due to prolonged thread blocking. As in my test, if the blocking time of the thread is relatively short, it will not blue screen; if the time is relatively long, it will.
My consideration is that it may be due to prolonged thread blocking. As in my test, if the blocking time of the thread is relatively short, it will not blue screen; if the time is relatively long, it will. -
 I want to debug user processes. Which mode should I choose??
I want to debug user processes. Which mode should I choose?? -
 Just like before, I use a physical machine as the client
Just like before, I use a physical machine as the client -
 and connect the server and client via the serial port.
and connect the server and client via the serial port. -

-
 The best way to use HyperDbg at this stage is using either a VMware Workstation or VMware Player (free) in the debugger mode. However, you can also use your machine in the VMI Mode which is like Local Debugging in WinDbg. You cannot step through instructions or put a break or breakpoint anywhere in your machine once you're in the VMI mode. Other functionalities are perfectly okay to be used.
The best way to use HyperDbg at this stage is using either a VMware Workstation or VMware Player (free) in the debugger mode. However, you can also use your machine in the VMI Mode which is like Local Debugging in WinDbg. You cannot step through instructions or put a break or breakpoint anywhere in your machine once you're in the VMI mode. Other functionalities are perfectly okay to be used. -
 I usually use HyperDbg along with printf scripts to debug user-mode processes in the VMI mode.
I usually use HyperDbg along with printf scripts to debug user-mode processes in the VMI mode. -
 Well, honestly I didn't test or document this feature yet. But as you noticed, one of our contributors implement it. You can test it as the '!crwrite' command but I'm not sure if it currently works (and it's not yet released/documented). I will get into it in the future but if you could use and debug (which is probably not that problematic), please let me know, or if anything is fixed, you could open a PR in GitHub.
Well, honestly I didn't test or document this feature yet. But as you noticed, one of our contributors implement it. You can test it as the '!crwrite' command but I'm not sure if it currently works (and it's not yet released/documented). I will get into it in the future but if you could use and debug (which is probably not that problematic), please let me know, or if anything is fixed, you could open a PR in GitHub. -

-

-
 Not sure if I correctly understand, do you mean that you don't know how Intel makes it possible to monitor CR0-CR4?
Not sure if I correctly understand, do you mean that you don't know how Intel makes it possible to monitor CR0-CR4? -

-

-

-
 Joined.
Joined. -
 Great resource, thanks
Great resource, thanks -
 I was about to ask if somebody did use hyperdbg on Intel sandybridge. I saw recommendations about gen 4th as minimum but wanted to confirm why specifically
I was about to ask if somebody did use hyperdbg on Intel sandybridge. I saw recommendations about gen 4th as minimum but wanted to confirm why specifically -
 When I load vmm I get "vmx is supported" but then the kernel crash(win10/win11 same on both), tried all different ways of disabling DSE/patchguard but the behaviour is the same
When I load vmm I get "vmx is supported" but then the kernel crash(win10/win11 same on both), tried all different ways of disabling DSE/patchguard but the behaviour is the same -
 Using windbg I can at least avoid the crash as I get a breakpoint over hyperdbghv, the internal error code is ERROR_GEN_FAILURE , apparently it can't init the handlers but not sure if this is specific to some missing extensions on sandy bridge CPUs . thanks x)
Using windbg I can at least avoid the crash as I get a breakpoint over hyperdbghv, the internal error code is ERROR_GEN_FAILURE , apparently it can't init the handlers but not sure if this is specific to some missing extensions on sandy bridge CPUs . thanks x) -
 This is over latest VMWare Workstation Pro of course.
This is over latest VMWare Workstation Pro of course. - 09 April 2024 (19 messages)
-

-
Has anyone experienced an automatic reboot (no bsod) after using !epthook? It only occurs occasionally
-
The following exception occurs when i use !epthook MmGetPhysicalAddress
0: kd> K
# Child-SP RetAddr Call Site
00 fffff806`152a3128 01000000`00100000 nt!KiDispatchInterruptContinue+0x1b
01 fffff806`152a3130 00000000`00000103 0x01000000`00100000
02 fffff806`152a3138 00000000`00000000 0x103 -
 Please check this link:
Please check this link:
https://github.com/HyperDbg/HyperDbg/blob/7710b92be4998e68c187cf4698ee585d827fdfee/hyperdbg/hprdbgkd/code/debugger/events/ApplyEvents.c#L891HyperDbg/hyperdbg/hprdbgkd/code/debugger/events/ApplyEvents.c at 7710b92be4998e68c187cf4698ee585d827fdfee · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 It's how we implement it on HyperDbg.
It's how we implement it on HyperDbg. -
 Starting from the recent versions of HyperDbg, the MBEC (mode-based execution controls) is used for functionalities which are only available on gen 7 or newer. (E.g. even skylake processors won't support it).
Starting from the recent versions of HyperDbg, the MBEC (mode-based execution controls) is used for functionalities which are only available on gen 7 or newer. (E.g. even skylake processors won't support it). -
 Because these processors are problematic in some cases that are really hard to investigate. For example I remember some features like SYSCALL hooks doesn't work on these generations.
Because these processors are problematic in some cases that are really hard to investigate. For example I remember some features like SYSCALL hooks doesn't work on these generations. -
 If you could put me to the exact line that leads to error, I can further investigate it.
If you could put me to the exact line that leads to error, I can further investigate it. -
 Yeah, I found some of these behaviors in the past, but I fixed most of them. Usually, these types of bugs happens when a driver tries to access a not existed physical address.
Yeah, I found some of these behaviors in the past, but I fixed most of them. Usually, these types of bugs happens when a driver tries to access a not existed physical address.
These types of bugs are easy to investigate if we could find a way to deterministically re-produce them. -
 Ah, we call this function several times when we want to apply EPT Hooks. 😄
Ah, we call this function several times when we want to apply EPT Hooks. 😄 -
 It's probably a stack overflow because of recursive function calls to this function. I didn't consider these cases on the implementation.
It's probably a stack overflow because of recursive function calls to this function. I didn't consider these cases on the implementation. -
 Would you please create a GitHub issue (if it's possible), for this? This seems to be an interesting problem that needs to be solved.
Would you please create a GitHub issue (if it's possible), for this? This seems to be an interesting problem that needs to be solved. -
When I use !epthook MmGetPhysicalAddress I can reproduce it a lot more often
-
windbg log
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> g
Access violation - code c0000005 (!!! second chance !!!)
nt!KiDispatchInterruptContinue+0x1b:
fffff806`137c5cab c3 ret
0: kd> .crash
Access violation - code c0000005 (!!! second chance !!!)
nt!HvlpGetRegister64+0xd6:
fffff806`13885ece 48c1e220 shl rdx,20h
0: kd> k
# Child-SP RetAddr Call Site
00 fffff806`152a1b00 fffff806`1387e54d nt!HvlpGetRegister64+0xd6
01 fffff806`152a1b30 fffff806`1389eb6f nt!HvlLogGuestCrashInformation+0x39
02 fffff806`152a1b70 fffff806`137bf147 nt!KeBugCheck2+0x7cf
03 fffff806`152a2290 fffff806`13ea7907 nt!KeBugCheckEx+0x107
04 fffff806`152a22d0 fffff806`13ea69ef nt!KdpSendWaitContinue+0x807
05 fffff806`152a24d0 fffff806`13899ef4 nt!KdpReportExceptionStateChange+0x9b
06 fffff806`152a2630 fffff806`13ea9665 nt!KdpReport+0xb4
07 fffff806`152a2670 fffff806`13716138 nt!KdpTrap+0x14d
08 fffff806`152a26c0 fffff806`138426d1 nt!KdTrap+0x2c
09 fffff806`152a2700 fffff806`137d0942 nt!KiDispatchException+0x12ca61
0a fffff806`152a2db0 fffff806`137cc805 nt!KiExceptionDispatch+0xc2
0b fffff806`152a2f90 fffff806`137c5cab nt!KiGeneralProtectionFault+0x305
0c fffff806`152a3128 01000000`00100000 nt!KiDispatchInterruptContinue+0x1b
0d fffff806`152a3130 00000000`00000103 0x01000000`00100000
0e fffff806`152a3138 00000000`00000000 0x103 -
 Yes, it's because of the recursive calls and the fact that we use this function once HyperDbg wants to apply an EPT hook.
Yes, it's because of the recursive calls and the fact that we use this function once HyperDbg wants to apply an EPT hook. -
I had thought it was due to hv's internal call to
MmGetPhysicalAddress with !epthook
MmGetPhysicalAddress conflict. -
Access violation - code c0000005 · Issue #356 · HyperDbg/HyperDbg
Describe the bug Sometimes using the !epthook MmGetPhysicalAddress triggers an exception. To Reproduce Use !epthook MmGetPhysicalAddress (note: this is an occasional 0: kd> g Access violation - ...
-
 Great! Thanks
Great! Thanks -
- 10 April 2024 (2 messages)
-
Joined.
-
 Joined.
Joined. - 11 April 2024 (1 messages)
-
 Joined.
Joined. - 13 April 2024 (1 messages)
-
- 14 April 2024 (5 messages)
-
-
-
https://rayanfam.com/topics/hypervisor-from-scratch-part-4/
第四部分源码在我的win1903系统上面,一加载驱动就蓝屏,前面三部分正常Hypervisor From Scratch – Part 4: Address Translation Using Extended Page Table (EPT)We write about Windows Internals, Hypervisors, Linux, and Networks.
-
-

- 15 April 2024 (2 messages)
-
Joined.
-
 Joined.
Joined. - 16 April 2024 (1 messages)
-
被be检测到了
- 17 April 2024 (1 messages)
-
- 18 April 2024 (1 messages)
-
- 19 April 2024 (3 messages)
-
 Soon we'll say welcome to our new family member, hwdbg. 🛠️⚙️🔲
Soon we'll say welcome to our new family member, hwdbg. 🛠️⚙️🔲
Hardware Debugger, or #hwdbg, is a new class of event-driven chip debuggers that allows precise signal control down to the period of a single clock cycle.
https://github.com/HyperDbg/hwdbgGitHub - HyperDbg/hwdbg: HyperDbg's chip-level hardware debuggerHyperDbg's chip-level hardware debugger. Contribute to HyperDbg/hwdbg development by creating an account on GitHub.
-
 None
None -
 If you've ever worked with HyperDbg, you probably know that everything in HyperDbg is treated as an event.
If you've ever worked with HyperDbg, you probably know that everything in HyperDbg is treated as an event.
This new debugger is designed to allow us to control the smallest unit in computers which is a clock cycle, so we can execute custom actions for each event (clock). - 20 April 2024 (10 messages)
-
Is there anyways to debug when a process with a specific name is created? I am not very experience with windows internal so maybe there is a way to hook a function when it is created?
-
 You can hook NtCreateProcess (or NtCreateUserProcess) using the '!epthook' command and once you find the name of the process in the process exe path, pause the debugger before its creation. The script engine support strings comparison:
You can hook NtCreateProcess (or NtCreateUserProcess) using the '!epthook' command and once you find the name of the process in the process exe path, pause the debugger before its creation. The script engine support strings comparison:
https://docs.hyperdbg.org/commands/scripting-language/assumptions-and-evaluationsAssumptions & Evaluations | HyperDbg DocumentationDescription of keywords, operators, pseudo-registers, number prefixes, and pre-defined functions
-
 Another option is using the '!interrupt' command and monitor for each Crock interrupt. If HyperDbg finds a clock interrupt on your target process (you can use $pname pseudo-register to read and compare the process name) then it'll pause the debugger.
Another option is using the '!interrupt' command and monitor for each Crock interrupt. If HyperDbg finds a clock interrupt on your target process (you can use $pname pseudo-register to read and compare the process name) then it'll pause the debugger. -
what is crock interrupt? do you have any document or reference so I can read about it?
-
 Yes, please take a look at this video:
Yes, please take a look at this video:
https://youtu.be/UFLZC3bZ9eU?si=ctdbnEYMn0IL3DUF&t=331Dbg3301: HyperDbg 08 01 Faults Exceptions InterruptsView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
thanks
-
 For more information, it uses this command:
For more information, it uses this command:
https://docs.hyperdbg.org/commands/extension-commands/interrupt!interrupt (hook external device interrupts) | HyperDbg DocumentationDescription of the '!interrupt' command in HyperDbg.
-
Joined.
-
-
Joined.
- 22 April 2024 (4 messages)
-
I have a question: should hwdbg require the purchase of additional responsive hardware devices, if so it seems to be more costly relative to cpu-based virtualization debugging.
-
 of course, what's the question?
of course, what's the question? -
 hwdbg is for debugging hardware microchips, not Windows or Linux so it's completely different. It needs at least a ~1000$ worth of Xilinx FPGA.
hwdbg is for debugging hardware microchips, not Windows or Linux so it's completely different. It needs at least a ~1000$ worth of Xilinx FPGA. -
 If you don't have an FPGA, usually universities have a bunch of FPGA boards for digital design courses. You could borrow one from the university or ask a friend to do so on your behalf.
If you don't have an FPGA, usually universities have a bunch of FPGA boards for digital design courses. You could borrow one from the university or ask a friend to do so on your behalf. - 24 April 2024 (1 messages)
-

- 25 April 2024 (2 messages)
-
-
 Joined.
Joined. - 27 April 2024 (1 messages)
-
Joined.
- 01 Apr 2024 (1)
- 04 Apr 2024 (53)
- 05 Apr 2024 (8)
- 06 Apr 2024 (17)
- 07 Apr 2024 (2)
- 08 Apr 2024 (21)
- 09 Apr 2024 (19)
- 10 Apr 2024 (2)
- 11 Apr 2024 (1)
- 13 Apr 2024 (1)
- 14 Apr 2024 (5)
- 15 Apr 2024 (2)
- 16 Apr 2024 (1)
- 17 Apr 2024 (1)
- 18 Apr 2024 (1)
- 19 Apr 2024 (3)
- 20 Apr 2024 (10)
- 22 Apr 2024 (4)
- 24 Apr 2024 (1)
- 25 Apr 2024 (2)
- 27 Apr 2024 (1)