- 03 June 2023 (1 messages)
-
Joined.
- 04 June 2023 (1 messages)
-
Joined.
- 05 June 2023 (1 messages)
-
Joined.
- 06 June 2023 (18 messages)
-
 Starting from the next version of the HyperDbg, a new feature is added to the debugger called "event short-circuiting". By using this feature, you can ignore the execution of any events in the debugger.
Starting from the next version of the HyperDbg, a new feature is added to the debugger called "event short-circuiting". By using this feature, you can ignore the execution of any events in the debugger. -
 For example: Based on a special condition, you can ignore a SYSCALL instruction. Or for example, you can ignore an RDMSR or IN, OUT instructions. Another juicy scenario that this mechanism is also applied to is for the "!monitor" command. It's like you can ignore (or mask or change) the read and write to a specific address of the memory.
For example: Based on a special condition, you can ignore a SYSCALL instruction. Or for example, you can ignore an RDMSR or IN, OUT instructions. Another juicy scenario that this mechanism is also applied to is for the "!monitor" command. It's like you can ignore (or mask or change) the read and write to a specific address of the memory. -
 For example, assume the following C code:
For example, assume the following C code:
#include <iostream>
#include <Windows.h>
volatile int test = 0;
int main()
{
printf("Address of test variable: %llx | pid: %x\n", &test, GetCurrentProcessId());
for (;;)
{
test++;
printf("test value is : %d\n", test);
Sleep(2000);
}
} -
 It's possible to ignore this write (test++) by using the following script:
It's possible to ignore this write (test++) by using the following script:
!monitor w 7ff7a3198210 7ff7a3198210+4 pid 1178 script {
printf("writng into memory address: %llx is ignored\n", $context);
event_sc(1);
} -

-
 Here's the demo. You can also test it on your system by compiling the 'Dev' branch of HyperDbg. Let me know if you have any feedbacks regarding this new short-circuiting feature.
Here's the demo. You can also test it on your system by compiling the 'Dev' branch of HyperDbg. Let me know if you have any feedbacks regarding this new short-circuiting feature. -
-
 Yes; It's a 12-part long tutorial (around 18 hours). Lots of use cases, along with several RE techniques that are based on HyperDbg are there.
Yes; It's a 12-part long tutorial (around 18 hours). Lots of use cases, along with several RE techniques that are based on HyperDbg are there. -
-

-
 I never test it on KVM but there shouldn't be any problem. (I'm not sure)
I never test it on KVM but there shouldn't be any problem. (I'm not sure)
Currently, it works best on a physical machine and VMware Workstation and all other VMware products. Btw, the worst hypervisor that I've ever work on it is Hyper-v. We still have problem with Hyper-V. -

-

-
 I spent hundreds of hours on hyper-v and it still not working. 🫠
I spent hundreds of hours on hyper-v and it still not working. 🫠 -
Can I get it too?
-
 Sure, it's available for everyone. Currently, the video editors of Open Security Training are working on it, it's not yet completed but sure you can request to test (beta) it.
Sure, it's available for everyone. Currently, the video editors of Open Security Training are working on it, it's not yet completed but sure you can request to test (beta) it.
https://twitter.com/XenoKovah/status/1664583342572949506?s=20Link📣Call for #OST2 beta testers: “Debuggers 3001: Introductory HyperDbg” (a virtualization-based debugger)📣 Sign up here https://t.co/oLA9wNSxXx I was pleasantly surprised yesterday when @Intel80x86 sent all the videos for this class! Which means it’s time to start beta testing!
-
Thanks 🙏
-
I'll be taking the classes, hope I get to learn something cool
- 08 June 2023 (6 messages)
-
Joined.
-
 Here's another scenario which we can use the event-short circuiting by blocking network connection for port 443:
Here's another scenario which we can use the event-short circuiting by blocking network connection for port 443: -

-
 It generally blocks the connections to network from (syscall 0x7). Here's the actual script that is used in this video:
It generally blocks the connections to network from (syscall 0x7). Here's the actual script that is used in this video:
!syscall script {
if (@rax == 0x7) {
if (dw(@rsp + 30) == 0x12007) {
//
// Get the port address
//
port_num_high_bit = db(poi(@rsp + 38) + 1a);
port_num_low_bit = db(poi(@rsp + 38) + 1b);
port_num = 0;
port_num = port_num_high_bit << 8 | port_num_low_bit;
//
// Get the IP address
//
part0 = db(poi(@rsp + 38) + 1c);
part1 = db(poi(@rsp + 38) + 1d);
part2 = db(poi(@rsp + 38) + 1e);
part3 = db(poi(@rsp + 38) + 1f);
part0 = part0 << 0n24;
part1 = part1 << 0n16;
part2 = part2 << 0n8;
part3 = part3 << 0n0;
ip_addr = part0 | part1 | part2 | part3;
printf("Process Id: %x, name: %s connects to ====> Address: %d.%d.%d.%d:%d\n",
$pid,
$pname,
(ip_addr & 0xFF000000) >> 0n24,
(ip_addr & 0x00FF0000) >> 0n16,
(ip_addr & 0x0000FF00) >> 0n8,
ip_addr & 0x000000FF,
port_num);
if (port_num == 0n443) {
//
// Block the connection to port 443
//
printf("Connection to port 443 is blocked!\n");
event_sc(1);
}
}
}
} -
 And finally it's also documented: https://docs.hyperdbg.org/tips-and-tricks/misc/event-short-circuitingEvent short-circuiting
And finally it's also documented: https://docs.hyperdbg.org/tips-and-tricks/misc/event-short-circuitingEvent short-circuitingThe event short-circuiting and ignoring mechanism in HyperDbg
-
 Joined.
Joined. - 09 June 2023 (1 messages)
-

- 10 June 2023 (1 messages)
-
 Joined.
Joined. - 12 June 2023 (1 messages)
-
 Joined.
Joined. - 13 June 2023 (2 messages)
-
 Joined.
Joined. -
Joined.
- 16 June 2023 (6 messages)
-
 Joined.
Joined. -
 Joined.
Joined. -
Joined.
-
I can't see the hyperdbg course on my dashboard on ost2
-
 Hi, as long as I know, the editing of the 12th part is not yet finished and the video editor is still working on that. But, I'm not sure how Xeno wants to release it.
Hi, as long as I know, the editing of the 12th part is not yet finished and the video editor is still working on that. But, I'm not sure how Xeno wants to release it. -
ah, ok, I was worried that I skipped some instruction because today is the day the course starts
- 17 June 2023 (3 messages)
-
 Beta testers have access to the course in ost2-beta dashboard.
Beta testers have access to the course in ost2-beta dashboard. -
 Did you see the videos? All of them (12 part) are available there?
Did you see the videos? All of them (12 part) are available there? -
 Yes, each section has a video and it seems the videos are complete. Check your DM.
Yes, each section has a video and it seems the videos are complete. Check your DM. - 20 June 2023 (330 messages)
-
Joined.
-
 Joined.
Joined. -
-
-
-
-
-
-
-
-
-
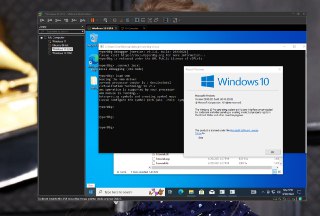
Microsoft (R) Windows Debugger Version 10.0.22000.194 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Using NET for debugging
Opened WinSock 2.0
Waiting to reconnect...
Connected to target 192.168.127.128 on port 50000 on local IP 192.168.127.1.
You can get the target MAC address by running .kdtargetmac command.
Connected to Windows 10 18362 x64 target at (Tue Jun 20 08:54:24.248 2023 (UTC - 3:00)), ptr64 TRUE
Kernel Debugger connection established.
************* Path validation summary **************
Response Time (ms) Location
Deferred SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Symbol search path is: SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 18362 MP (1 procs) Free x64
Edition build lab: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff803`72400000 PsLoadedModuleList = 0xfffff803`72845f30
System Uptime: 0 days 0:00:01.946
KDTARGET: Refreshing KD connectionSymbol informationProvides information about the Microsoft Symbol Server.
-
-
-
-
-
-
-
-
-
KDTARGET: Refreshing KD connection
*** Fatal System Error: 0x0000003b
(0x00000000C000001D,0xFFFFF80373778D52,0xFFFFF506EBAEC840,0x0000000000000000)
Break instruction exception - code 80000003 (first chance)
A fatal system error has occurred.
Debugger entered on first try; Bugcheck callbacks have not been invoked.
A fatal system error has occurred.
For analysis of this file, run !analyze -v
nt!DbgBreakPointWithStatus:
fffff803`725cbc90 cc int 3
0: kd> g -
-
-
-
-
-
-
 Hi,
Hi,
Can you provide the !analyze -v result of the WinDbg for this crash? -
-
-
: kd> g
Break instruction exception - code 80000003 (first chance)
hprdbghv+0x8cf9:
fffff801`24958cf9 cc int 3
2: kd> g
Break instruction exception - code 80000003 (first chance)
hprdbghv+0x8cf9:
fffff801`24958cf9 cc int 3
0: kd> g
KDTARGET: Refreshing KD connection
*** Fatal System Error: 0x0000003b
(0x00000000C000001D,0xFFFFF80124958D52,0xFFFFF9072196F840,0x0000000000000000)
Break instruction exception - code 80000003 (first chance)
A fatal system error has occurred.
Debugger entered on first try; Bugcheck callbacks have not been invoked.
A fatal system error has occurred.
nt!DbgBreakPointWithStatus:
fffff807`3d5cbc90 cc int 3
0: kd> g -
-
-
-
-
 So, there is problem with Hypervisor. Please send the result of !analyze -v.
So, there is problem with Hypervisor. Please send the result of !analyze -v. -
-
-
-
-
 Yeah, just load the HyperDbg (e.g., by connecting to serial port), and when the WinDbg crashes, run '!analyze -v' and send the output of WinDbg.
Yeah, just load the HyperDbg (e.g., by connecting to serial port), and when the WinDbg crashes, run '!analyze -v' and send the output of WinDbg. -
 And also, what's your processor model (generation)?
And also, what's your processor model (generation)? -
Connected to Windows 10 18362 x64 target at (Tue Jun 20 09:21:01.044 2023 (UTC - 3:00)), ptr64 TRUE
Loading Kernel Symbols
...................................................
Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.
Run !sym noisy before .reload to track down problems loading symbols.
............
................................................................
............................................................
Loading User Symbols
Loading unloaded module list
........Unable to enumerate user-mode unloaded modules, Win32 error 0n30
************* Symbol Loading Error Summary **************
Module name Error
hprdbghv The system cannot find the file specified
You can troubleshoot most symbol related issues by turning on symbol loading diagnostics (!sym noisy) and repeating the command that caused symbols to be loaded.
You should also verify that your symbol search path (.sympath) is correct.
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Unknown bugcheck code (0)
Unknown bugcheck description
Arguments:
Arg1: 0000000000000000
Arg2: 0000000000000000
Arg3: 0000000000000000
Arg4: 0000000000000000
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1562
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 6431
Key : Analysis.Init.CPU.mSec
Value: 5842
Key : Analysis.Init.Elapsed.mSec
Value: 1716818
Key : Analysis.Memory.CommitPeak.Mb
Value: 71
Key : WER.OS.Branch
Value: 19h1_release
Key : WER.OS.Timestamp
Value: 2019-03-18T12:02:00Z
Key : WER.OS.Version
Value: 10.0.18362.1
BUGCHECK_CODE: 0
BUGCHECK_P1: 0
BUGCHECK_P2: 0
BUGCHECK_P3: 0
BUGCHECK_P4: 0
PROCESS_NAME: System
ERROR_CODE: (NTSTATUS) 0x80000003 - {EXCEPTION} Breakpoint A breakpoint has been reached.
EXCEPTION_CODE_STR: 80000003
EXCEPTION_PARAMETER1: 0000000000000000 -
STACK_TEXT:
fffff184`b5429730 fffff184`b5429730 : ffffffff`ffffffff ffffc109`500e9010 00000000`270e2f0c 00000000`00000086 : hprdbghv+0x8cf9
fffff184`b5429738 ffffffff`ffffffff : ffffc109`500e9010 00000000`270e2f0c 00000000`00000086 fffff807`15d7597f : 0xfffff184`b5429730
fffff184`b5429740 ffffc109`500e9010 : 00000000`270e2f0c 00000000`00000086 fffff807`15d7597f 00000000`00000010 : 0xffffffff`ffffffff
fffff184`b5429748 00000000`270e2f0c : 00000000`00000086 fffff807`15d7597f 00000000`00000010 00000000`00000286 : 0xffffc109`500e9010
fffff184`b5429750 00000000`00000086 : fffff807`15d7597f 00000000`00000010 00000000`00000286 fffff184`b5429788 : 0x270e2f0c
fffff184`b5429758 fffff807`15d7597f : 00000000`00000010 00000000`00000286 fffff184`b5429788 00000000`00000018 : 0x86
fffff184`b5429760 00000000`00000010 : 00000000`00000286 fffff184`b5429788 00000000`00000018 ffffc109`500e9100 : hal!HalProcessorIdle+0xf
fffff184`b5429768 00000000`00000286 : fffff184`b5429788 00000000`00000018 ffffc109`500e9100 fffff807`15d5d95c : 0x10
fffff184`b5429770 fffff184`b5429788 : 00000000`00000018 ffffc109`500e9100 fffff807`15d5d95c ffffc109`500e9100 : 0x286
fffff184`b5429778 00000000`00000018 : ffffc109`500e9100 fffff807`15d5d95c ffffc109`500e9100 ffff8600`98700180 : 0xfffff184`b5429788
fffff184`b5429780 ffffc109`500e9100 : fffff807`15d5d95c ffffc109`500e9100 ffff8600`98700180 00000000`00000000 : 0x18
fffff184`b5429788 fffff807`15d5d95c : ffffc109`500e9100 ffff8600`98700180 00000000`00000000 00000000`00000000 : 0xffffc109`500e9100
fffff184`b5429790 fffff807`15e41fb9 : ffffc109`500e9328 00000000`270e2f0c 00000000`270e3503 ffff8600`98700180 : hal!KeQueryPerformanceCounter+0xec
fffff184`b54297c0 fffff807`15e4073a : 00000000`00000000 00000000`00000004 00000000`00000001 00000000`00000000 : nt!PpmIdleExecuteTransition+0x1719
fffff184`b5429b00 fffff807`15fc796e : 00000000`00000000 ffff8600`98700180 ffff8600`98711140 ffffc109`53722080 : nt!PoIdle+0x3aa
fffff184`b5429c60 00000000`00000000 : fffff184`b542a000 fffff184`b5424000 00000000`00000000 00000000`00000000 : nt!KiIdleLoop+0x7e
SYMBOL_NAME: hprdbghv+8cf9
MODULE_NAME: hprdbghv
IMAGE_NAME: hprdbghv.dll
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 8cf9
FAILURE_BUCKET_ID: 0x0_hprdbghv!unknown_function
OS_VERSION: 10.0.18362.1
BUILDLAB_STR: 19h1_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {804d1d0a-ae5c-2184-2ead-2dc122fdd9d7}
Followup: MachineOwner
--------- -
-
-
-
-
-
 HyperDbg package has symbol (.pdb) files. Would you please set a symbol server and load the symbols, so I'll know the name of the guilty function.
HyperDbg package has symbol (.pdb) files. Would you please set a symbol server and load the symbols, so I'll know the name of the guilty function. -
-
 And also, do you have the same problem in your physical machine?
And also, do you have the same problem in your physical machine? -
-
-
-
-
 The driver symbols are loaded on the (host) windbg. If it fails, you can reload the symbols. By reloading (.reload) command in WinDbg, the symbols for the failed driver will also be loaded.
The driver symbols are loaded on the (host) windbg. If it fails, you can reload the symbols. By reloading (.reload) command in WinDbg, the symbols for the failed driver will also be loaded. -
-
-
-
-
2: kd> !analyze -v
Connected to Windows 10 18362 x64 target at (Tue Jun 20 09:46:14.099 2023 (UTC - 3:00)), ptr64 TRUE
Loading Kernel Symbols
...............................................................
................................................................
............................................................
Loading User Symbols
Loading unloaded module list
.......Unable to enumerate user-mode unloaded modules, Win32 error 0n30
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
Unknown bugcheck code (0)
Unknown bugcheck description
Arguments:
Arg1: 0000000000000000
Arg2: 0000000000000000
Arg3: 0000000000000000
Arg4: 0000000000000000
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 1702
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 4113
Key : Analysis.Init.CPU.mSec
Value: 21405
Key : Analysis.Init.Elapsed.mSec
Value: 3211056
Key : Analysis.Memory.CommitPeak.Mb
Value: 210
Key : WER.OS.Branch
Value: 19h1_release
Key : WER.OS.Timestamp
Value: 2019-03-18T12:02:00Z
Key : WER.OS.Version
Value: 10.0.18362.1
BUGCHECK_CODE: 0
BUGCHECK_P1: 0
BUGCHECK_P2: 0
BUGCHECK_P3: 0
BUGCHECK_P4: 0
PROCESS_NAME: System
ERROR_CODE: (NTSTATUS) 0x80000003 - {EXCEPTION} Breakpoint A breakpoint has been reached.
EXCEPTION_CODE_STR: 80000003
EXCEPTION_PARAMETER1: 0000000000000000
STACK_TEXT:
ffffb50f`dc837730 ffffb50f`dc837730 : ffffffff`ffffffff ffff9802`7cc11010 00000000`3571ca8f 00000000`00000086 : hprdbghv!AsmVmxSaveState+0x29 [D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 39]
ffffb50f`dc837738 ffffffff`ffffffff : ffff9802`7cc11010 00000000`3571ca8f 00000000`00000086 fffff802`32ace97f : 0xffffb50f`dc837730
ffffb50f`dc837740 ffff9802`7cc11010 : 00000000`3571ca8f 00000000`00000086 fffff802`32ace97f 00000000`00000010 : 0xffffffff`ffffffff
ffffb50f`dc837748 00000000`3571ca8f : 00000000`00000086 fffff802`32ace97f 00000000`00000010 00000000`00000286 : 0xffff9802`7cc11010
ffffb50f`dc837750 00000000`00000086 : fffff802`32ace97f 00000000`00000010 00000000`00000286 ffffb50f`dc837788 : 0x3571ca8f
ffffb50f`dc837758 fffff802`32ace97f : 00000000`00000010 00000000`00000286 ffffb50f`dc837788 00000000`00000018 : 0x86
ffffb50f`dc837760 00000000`00000010 : 00000000`00000286 ffffb50f`dc837788 00000000`00000018 ffff9802`7cc11100 : hal!HalProcessorIdle+0xf
ffffb50f`dc837768 00000000`00000286 : ffffb50f`dc837788 00000000`00000018 ffff9802`7cc11100 fffff802`32ab695c : 0x10
ffffb50f`dc837770 ffffb50f`dc837788 : 00000000`00000018 ffff9802`7cc11100 fffff802`32ab695c ffff9802`7cc11100 : 0x286
ffffb50f`dc837778 00000000`00000018 : ffff9802`7cc11100 fffff802`32ab695c ffff9802`7cc11100 ffff8680`45680180 : 0xffffb50f`dc837788
ffffb50f`dc837780 ffff9802`7cc11100 : fffff802`32ab695c ffff9802`7cc11100 ffff8680`45680180 00000000`00000000 : 0x18
ffffb50f`dc837788 fffff802`32ab695c : ffff9802`7cc11100 ffff8680`45680180 00000000`00000000 00000000`00000000 : 0xffff9802`7cc11100
ffffb50f`dc837790 fffff802`32041fb9 : ffff9802`7cc11328 00000000`3571ca8f 00000000`3571cb30 ffff8680`45680180 : hal!KeQueryPerformanceCounter+0xec
ffffb50f`dc8377c0 fffff802`3204073a : 00000000`001cf198 00000000`00000002 00000000`00000001 00000000`00000000 : nt!PpmIdleExecuteTransition+0x1719
ffffb50f`dc837b00 fffff802`321c796e : 00000000`00000000 ffff8680`45680180 ffff8680`45691140 ffff9802`814c7080 : nt!PoIdle+0x3aa
ffffb50f`dc837c60 00000000`00000000 : ffffb50f`dc838000 ffffb50f`dc832000 00000000`00000000 00000000`00000000 : nt!KiIdleLoop+0x7e -
FAULTING_SOURCE_LINE: D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm
FAULTING_SOURCE_FILE: D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm
FAULTING_SOURCE_LINE_NUMBER: 39
SYMBOL_NAME: hprdbghv!AsmVmxSaveState+29
MODULE_NAME: hprdbghv
IMAGE_NAME: hprdbghv.dll
STACK_COMMAND: .thread ; .cxr ; kb
BUCKET_ID_FUNC_OFFSET: 29
FAILURE_BUCKET_ID: 0x0_hprdbghv!AsmVmxSaveState
OS_VERSION: 10.0.18362.1
BUILDLAB_STR: 19h1_release
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {30f42f4f-6e51-2575-2498-bb100f162777}
Followup: MachineOwner
--------- -
 Okay, it seems that something is preventing the execution of VMLAUNCH in your machine.
Okay, it seems that something is preventing the execution of VMLAUNCH in your machine. -

-
-
 Don't worry, we could fix together.
Don't worry, we could fix together. -
 Basically, one of these checks and loads are failed :
Basically, one of these checks and loads are failed : -

-
 We have to trace this function and find where is the problem. Do you have a Visual Studio+WDK?
We have to trace this function and find where is the problem. Do you have a Visual Studio+WDK? -
 Build & Install
Build & InstallThis document helps you to build and install HyperDbg
-
-
-
-
-
-
-
 No, we don't need VS on target but I'm not sure if we could build HyperDbg with a VS2019. We use VS2022. As the newest version of Windows SDK broke the compatibility with the previous SDK and we were forced to make everything compatible with the newest SDK.
No, we don't need VS on target but I'm not sure if we could build HyperDbg with a VS2019. We use VS2022. As the newest version of Windows SDK broke the compatibility with the previous SDK and we were forced to make everything compatible with the newest SDK. -
-
 But, you could try it. If it's not built successfully on your VS2019, you need to update it to VS2022 + newest version of SDK
But, you could try it. If it's not built successfully on your VS2019, you need to update it to VS2022 + newest version of SDK -
 That's great 👍
That's great 👍 -
-
 Thank you for putting time helping us fixing these problems. 🙏
Thank you for putting time helping us fixing these problems. 🙏 -
-
-
-
-
-
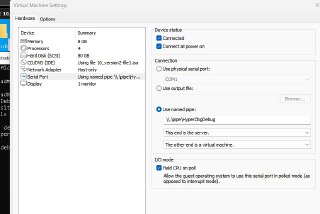
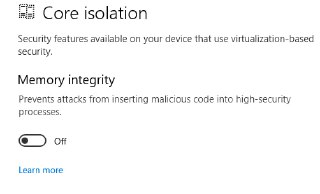
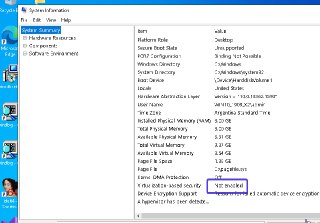
 Just to double check with you. Are you sure that the VBS/HVCI is disabled in the target VM?
Just to double check with you. Are you sure that the VBS/HVCI is disabled in the target VM?
https://docs.hyperdbg.org/getting-started/build-and-install#disable-vbs-hvci-and-device-guardBuild & InstallThis document helps you to build and install HyperDbg
-
-
-
 No, you should disable it in the guest.
No, you should disable it in the guest. -
-
-
-
-
 HyperDbg won't load anything (like drivers, hypervisor) in the host. When you run hyperdbg in the host, it works as a simple user-mode application that connects to the serial port and control the debugee.
HyperDbg won't load anything (like drivers, hypervisor) in the host. When you run hyperdbg in the host, it works as a simple user-mode application that connects to the serial port and control the debugee. -
-
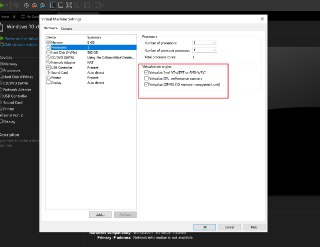
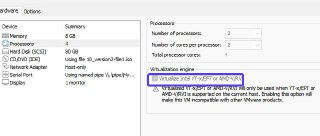
 And also, are you sure that the nested-virtualization is properly enabled?
And also, are you sure that the nested-virtualization is properly enabled? -

-
-
-
-
-
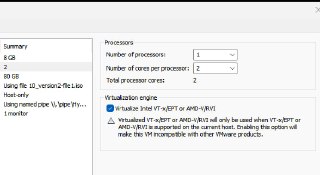
 And also please set the number of processors (not number of cores) to 1. Generally, it shouldn't be a problem but as we gonna debug it, it's better to debug it in a single processor (with many cores).
And also please set the number of processors (not number of cores) to 1. Generally, it shouldn't be a problem but as we gonna debug it, it's better to debug it in a single processor (with many cores). -
-
 Great.
Great. -
-
 Yes.
Yes. -
-
-
-
 Okay, now clone the 'master' branch with --recursive flag and compile it. Compiling it is as easy as pressing the build button in VS.
Okay, now clone the 'master' branch with --recursive flag and compile it. Compiling it is as easy as pressing the build button in VS. -
-
 git clone --recursive https://github.com/HyperDbg/HyperDbg.gitGitHub - HyperDbg/HyperDbg: State-of-the-art native debugging tool
git clone --recursive https://github.com/HyperDbg/HyperDbg.gitGitHub - HyperDbg/HyperDbg: State-of-the-art native debugging toolState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
-
-
-
-
-
 Did you build it successfully?
Did you build it successfully? -
-
-
 Build it in VS2022.
Build it in VS2022. -
-
-
 Yes
Yes -
-
-
 Debug
Debug -
-
-
-
11>Successfully signed: C:\Users\ricnar\Desktop\aca\HyperDbg\hyperdbg\build\bin\debug\hprdbgkd.sys
11>
11>Driver is 'Universal'.
11>Inf2Cat task was skipped as there were no inf files to process
11>Done building project "hprdbgkd.vcxproj".
========== Rebuild All: 12 succeeded, 0 failed, 0 skipped ==========
========== Rebuild started at 10:54 AM and took 34.991 seconds ========== -
-
-
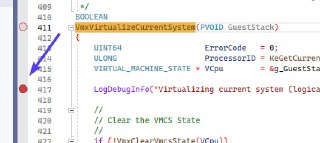
 Okay, now please find this function and put a 'DbgBreakPoint();' on the top of function.
Okay, now please find this function and put a 'DbgBreakPoint();' on the top of function. -
-
 Yes.
Yes. -
-
-
-
 After that, move the newly built files to the VM. Run HyperDbg and wait until the breakpoint is triggered in HyperDbg.
After that, move the newly built files to the VM. Run HyperDbg and wait until the breakpoint is triggered in HyperDbg. -
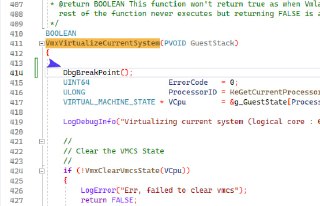
 Where is the breakpoint? 🤔
Where is the breakpoint? 🤔 -
-
-
 I couldn't see it in this picture.
I couldn't see it in this picture. -
 This.
This. -
-
 No, this is not how it will be triggered. As I mentioned, please add 'DbgBreakPoint();' one the very first line of function.
No, this is not how it will be triggered. As I mentioned, please add 'DbgBreakPoint();' one the very first line of function. -
-
 Yes, it's correct. Now, rebuild it and move the binary files to the VM. Once you load HyperDbg, the breakpoint will be triggered and you can trace the code line by line in WinDbg.
Yes, it's correct. Now, rebuild it and move the binary files to the VM. Once you load HyperDbg, the breakpoint will be triggered and you can trace the code line by line in WinDbg. -
-
 No, you can load it in whatever form you want.
No, you can load it in whatever form you want. -
-
-
-
-
-
-
 Actually, not important here. In whatever form that it triggers the breakpoint is okay
Actually, not important here. In whatever form that it triggers the breakpoint is okay -
-
-
 Is the breakpoint triggered?
Is the breakpoint triggered? -
-
 Yes 😇☺️
Yes 😇☺️ -
 Are you sure you run the newly compiled code?
Are you sure you run the newly compiled code? -
-
-
 Give me a minute to double check with source code.
Give me a minute to double check with source code. -
-
-
 Would you please double check it.
Would you please double check it.
The breakpoint that we expected to be executed should be triggered before this breakpoint. Please rebuild HyperDbg and make sure you're currently rebuilding the correct solution 'debug' in this case. -
-
-
-
-
 That's also correct, I usually prefer to debug it like this. In any case, all of them are correct.
That's also correct, I usually prefer to debug it like this. In any case, all of them are correct. -
-
-
-
-
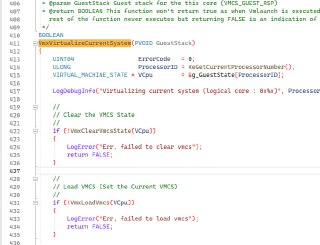
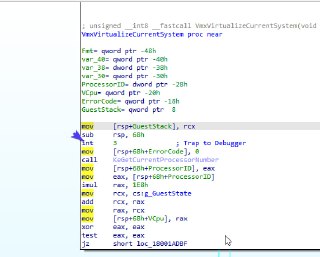
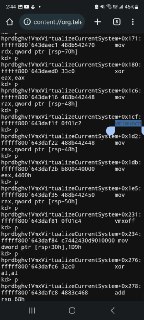
0: kd> x *!VmxVirtualizeCurrentSystem
fffff805`8198abb0 hprdbghv!VmxVirtualizeCurrentSystem (void *)
0: kd> u fffff805`8198abb0
hprdbghv!VmxVirtualizeCurrentSystem [D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\vmm\vmx\Vmx.c @ 412]:
fffff805`8198abb0 48894c2408 mov qword ptr [rsp+8],rcx
fffff805`8198abb5 4883ec68 sub rsp,68h
fffff805`8198abb9 48c744245000000000 mov qword ptr [rsp+50h],0
fffff805`8198abc2 e8292dffff call hprdbghv!KeGetCurrentProcessorNumber (fffff805`8197d8f0)
fffff805`8198abc7 89442440 mov dword ptr [rsp+40h],eax
fffff805`8198abcb 8b442440 mov eax,dword ptr [rsp+40h]
fffff805`8198abcf 4869c0e8010000 imul rax,rax,1E8h
fffff805`8198abd6 488b0d9b360600 mov rcx,qword ptr [hprdbghv!g_GuestState (fffff805`819ee278)] -
 Would you please step one instruction "p" in WinDbg.
Would you please step one instruction "p" in WinDbg. -
-
 Okay, Still, something is going wrong here. We shouldn't trigger this breakpoint before our target breakpoint. Maybe one core is raising other core, but in any case we have an alternative solution.
Okay, Still, something is going wrong here. We shouldn't trigger this breakpoint before our target breakpoint. Maybe one core is raising other core, but in any case we have an alternative solution. -
-
-
 Yes that's okay. We could even solve it tomorrow. No worries.
Yes that's okay. We could even solve it tomorrow. No worries. -
-
 Let me know when you return, if I was not available we could fix it tomorrow.
Let me know when you return, if I was not available we could fix it tomorrow. -
-
-
 Thanks to you for putting time on this.
Thanks to you for putting time on this. -
-
-
-
 Hi again,
Hi again,
Let's continue our debugging step by step. We have to get the execution before VmxVirtualizeCurrentSystem is made. -
-
hprdbghv!VmxVirtualizeCurrentSystem [D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\vmm\vmx\Vmx.c @ 412]:
fffff805`8198abb0 48894c2408 mov qword ptr [rsp+8],rcx
fffff805`8198abb5 4883ec68 sub rsp,68h
fffff805`8198abb9 48c744245000000000 mov qword ptr [rsp+50h],0
fffff805`8198abc2 e8292dffff call hprdbghv!KeGetCurrentProcessorNumber (fffff805`8197d8f0)
fffff805`8198abc7 89442440 mov dword ptr [rsp+40h],eax
fffff805`8198abcb 8b442440 mov eax,dword ptr [rsp+40h]
fffff805`8198abcf 4869c0e8010000 imul rax,rax,1E8h
fffff805`8198abd6 488b0d9b360600 mov rcx,qword ptr [hprdbghv!g_GuestState (fffff805`819ee278)] -
 It's weird why our 'int 3' is not called.
It's weird why our 'int 3' is not called. -
-
-
-
 Yes, but why the int 3 is not called in the newly compiled driver?
Yes, but why the int 3 is not called in the newly compiled driver? -
-
-
-
-
 You mean the running dll is different from the compiled driver DLL? Maybe the previous driver is not removed?
You mean the running dll is different from the compiled driver DLL? Maybe the previous driver is not removed? -
-
 By the way, we have another option here. We could also modify the code here, and add int3 assembly code
By the way, we have another option here. We could also modify the code here, and add int3 assembly code -
 But you have to find a way to load the newly compiled driver. Maybe an snapshot to the previous VM state?
But you have to find a way to load the newly compiled driver. Maybe an snapshot to the previous VM state? -
-
 Yes, 'int3' without space is also better but no difference here. But, this only works if the newly compiled driver is loaded in the guest.
Yes, 'int3' without space is also better but no difference here. But, this only works if the newly compiled driver is loaded in the guest. -
Microsoft Windows [Version 10.0.18363.1621]
(c) 2019 Microsoft Corporation. All rights reserved.
C:\Users\admin>driverq uery
'driverq' is not recognized as an internal or external command,
operable program or batch file.
C:\Users\admin>driverquery
Module Name Display Name Driver Type Link Date
============ ====================== ============= ======================
1394ohci 1394 OHCI Compliant Ho Kernel
3ware 3ware Kernel 5/18/2015 7:28:03 PM
ACPI Microsoft ACPI Driver Kernel
AcpiDev ACPI Devices driver Kernel
acpiex Microsoft ACPIEx Drive Kernel
acpipagr ACPI Processor Aggrega Kernel
AcpiPmi ACPI Power Meter Drive Kernel
acpitime ACPI Wake Alarm Driver Kernel
Acx01000 Acx01000 Kernel
ADP80XX ADP80XX Kernel 4/9/2015 5:49:48 PM
AFD Ancillary Function Dri Kernel
afunix afunix Kernel
ahcache Application Compatibil Kernel
amdgpio2 AMD GPIO Client Driver Kernel 2/7/2019 6:32:20 AM
amdi2c AMD I2C Controller Ser Kernel 6/13/2018 2:25:43 AM
AmdK8 AMD K8 Processor Drive Kernel
AmdPPM AMD Processor Driver Kernel
amdsata amdsata Kernel 5/14/2015 9:14:52 AM
amdsbs amdsbs Kernel 12/11/2012 6:21:44 PM
amdxata amdxata Kernel 4/30/2015 9:55:35 PM
AppID AppID Driver Kernel
applockerflt Smartlocker Filter Dri Kernel
AppvStrm AppvStrm File System
AppvVemgr AppvVemgr File System
AppvVfs AppvVfs File System
arcsas Adaptec SAS/SATA-II RA Kernel 4/9/2015 4:12:07 PM
AsyncMac RAS Asynchronous Media Kernel
atapi IDE Channel Kernel
b06bdrv QLogic Network Adapter Kernel 5/25/2016 4:03:08 AM
bam Background Activity Mo Kernel
BasicDisplay BasicDisplay Kernel
BasicRender BasicRender Kernel
bcmfn2 bcmfn2 Service Kernel 10/31/2016 11:09:15 PM
Beep Beep Kernel
bindflt Windows Bind Filter Dr File System
bowser Browser File System
BthA2dp Microsoft Bluetooth A2 Kernel
BthEnum Bluetooth Enumerator S Kernel
BthHFEnum Microsoft Bluetooth Ha Kernel
BthLEEnum Bluetooth Low Energy D Kernel
BthMini Bluetooth Radio Driver Kernel
BTHMODEM Bluetooth Modem Commun Kernel
BTHPORT Bluetooth Port Driver Kernel
BTHUSB Bluetooth Radio USB Dr Kernel
bttflt Microsoft Hyper-V VHDP Kernel
buttonconver Service for Portable D Kernel
CAD Charge Arbitration Dri Kernel
cdfs CD/DVD File System Rea File System
cdrom CD-ROM Driver Kernel
cht4iscsi cht4iscsi Kernel 5/8/2018 10:27:04 AM
cht4vbd Chelsio Virtual Bus Dr Kernel 5/8/2018 10:23:38 AM
circlass Consumer IR Devices Kernel
CldFlt Windows Cloud Files Fi File System
CLFS Common Log (CLFS) Kernel
CmBatt Microsoft ACPI Control Kernel
CNG CNG Kernel
cnghwassist CNG Hardware Assist al Kernel
CompositeBus Composite Bus Enumerat Kernel
condrv Console Driver Kernel
CSC Offline Files Driver Kernel
dam Desktop Activity Moder Kernel
Dfsc DFS Namespace Client D File System
disk Disk Driver Kernel
dmvsc dmvsc Kernel
drmkaud Microsoft Trusted Audi Kernel
DXGKrnl LDDM Graphics Subsyste Kernel
E1G60 Intel(R) PRO/1000 NDIS Kernel 3/23/2010 6:08:16 PM
ebdrv QLogic 10 Gigabit Ethe Kernel 5/25/2016 4:01:05 AM
EhStorClass Enhanced Storage Filte Kernel
EhStorTcgDrv Microsoft driver for s Kernel
ErrDev Microsoft Hardware Err Kernel
exfat exFAT File System Driv File System
fastfat FAT12/16/32 File Syste File System
fdc Floppy Disk Controller Kernel
FileCrypt FileCrypt File System -
FileInfo File Information FS Mi File System
Filetrace Filetrace File System
flpydisk Floppy Disk Driver Kernel
FltMgr FltMgr File System
FsDepends File System Dependency File System
fvevol BitLocker Drive Encryp Kernel
gencounter Microsoft Hyper-V Gene Kernel
genericusbfn Generic USB Function C Kernel
GPIOClx0101 Microsoft GPIO Class E Kernel
GpuEnergyDrv GPU Energy Driver Kernel
HdAudAddServ Microsoft 1.1 UAA Func Kernel
HDAudBus Microsoft UAA Bus Driv Kernel
HidBatt HID UPS Battery Driver Kernel
HidBth Microsoft Bluetooth HI Kernel
hidi2c Microsoft I2C HID Mini Kernel
hidinterrupt Common Driver for HID Kernel
HidIr Microsoft Infrared HID Kernel
hidspi Microsoft SPI HID Mini Kernel
HidUsb Microsoft HID Class Dr Kernel
HpSAMD HpSAMD Kernel 3/26/2013 6:36:54 PM
HTTP HTTP Service Kernel
hvcrash hvcrash Kernel
hvservice Hypervisor/Virtual Mac Kernel
HwNClx0101 Microsoft Hardware Not Kernel
hwpolicy Hardware Policy Driver Kernel
hyperkbd hyperkbd Kernel
HyperVideo HyperVideo Kernel
i8042prt PS/2 Keyboard and Mous Kernel
iagpio Intel Serial IO GPIO C Kernel 7/23/2018 6:04:46 AM
iai2c Intel(R) Serial IO I2C Kernel 7/23/2018 6:04:39 AM
iaLPSS2i_GPI Intel(R) Serial IO GPI Kernel 4/19/2018 4:53:24 AM
iaLPSS2i_GPI Intel(R) Serial IO GPI Kernel 4/17/2018 6:25:15 AM
iaLPSS2i_GPI Intel(R) Serial IO GPI Kernel 4/17/2018 4:07:03 AM
iaLPSS2i_GPI Intel(R) Serial IO GPI Kernel 5/16/2018 2:46:36 AM
iaLPSS2i_I2C Intel(R) Serial IO I2C Kernel 4/19/2018 4:52:58 AM
iaLPSS2i_I2C Intel(R) Serial IO I2C Kernel 4/17/2018 6:24:40 AM
iaLPSS2i_I2C Intel(R) Serial IO I2C Kernel 4/17/2018 4:06:22 AM
iaLPSS2i_I2C Intel(R) Serial IO I2C Kernel 5/16/2018 2:46:02 AM
iaLPSSi_GPIO Intel(R) Serial IO GPI Kernel 2/2/2015 6:00:09 AM
iaLPSSi_I2C Intel(R) Serial IO I2C Kernel 2/24/2015 12:52:07 PM
iaStorAVC Intel Chipset SATA RAI Kernel 2/7/2018 8:53:36 AM
iaStorV Intel RAID Controller Kernel 4/11/2011 3:48:16 PM
ibbus Mellanox InfiniBand Bu Kernel 4/25/2018 1:29:09 PM
IndirectKmd Indirect Displays Kern Kernel
intelide intelide Kernel
intelpep Intel(R) Power Engine Kernel
intelpmax Intel Power Limit Driv Kernel
intelppm Intel Processor Driver Kernel
iorate Disk I/O Rate Filter D Kernel
IpFilterDriv IP Traffic Filter Driv Kernel
IPMIDRV IPMIDRV Kernel
IPNAT IP Network Address Tra Kernel
IPT IPT Kernel
isapnp isapnp Kernel
iScsiPrt iScsiPort Driver Kernel
ItSas35i ItSas35i Kernel 5/3/2018 6:57:21 AM
kbdclass Keyboard Class Driver Kernel
kbdhid Keyboard HID Driver Kernel
kbldfltr kbldfltr Kernel
kdnic Microsoft Kernel Debug Kernel
KSecDD KSecDD Kernel
KSecPkg KSecPkg Kernel
ksthunk Kernel Streaming Thunk Kernel
lltdio Link-Layer Topology Di Kernel
LSI_SAS LSI_SAS Kernel 3/25/2015 4:36:48 PM
LSI_SAS2i LSI_SAS2i Kernel 8/2/2017 10:29:59 AM
LSI_SAS3i LSI_SAS3i Kernel 5/2/2018 6:40:30 AM
LSI_SSS LSI_SSS Kernel 3/15/2013 8:39:38 PM
luafv UAC File Virtualizatio File System
mausbhost MA-USB Host Controller Kernel
mausbip MA-USB IP Filter Drive Kernel
MbbCx MBB Network Adapter Cl Kernel
megasas megasas Kernel 3/4/2015 11:36:29 PM
megasas2i megasas2i Kernel 7/24/2017 6:46:09 AM
megasas35i megasas35i Kernel 12/6/2018 2:45:11 PM
megasr megasr Kernel 6/3/2013 7:02:39 PM
Microsoft_Bl Microsoft Bluetooth Av Kernel -
mlx4_bus Mellanox ConnectX Bus Kernel 4/25/2018 1:29:43 PM
MMCSS Multimedia Class Sched Kernel
Modem Modem Kernel
monitor Microsoft Monitor Clas Kernel
mouclass Mouse Class Driver Kernel
mouhid Mouse HID Driver Kernel
mountmgr Mount Point Manager Kernel
mpsdrv Windows Defender Firew Kernel
MRxDAV WebDav Client Redirect File System
mrxsmb SMB MiniRedirector Wra File System
mrxsmb10 SMB 1.x MiniRedirector File System
mrxsmb20 SMB 2.0 MiniRedirector File System
MsBridge Microsoft MAC Bridge Kernel
Msfs Msfs File System
msgpiowin32 Common Driver for Butt Kernel
mshidkmdf Pass-through HID to KM Kernel
mshidumdf Pass-through HID to UM Kernel
msisadrv msisadrv Kernel
MSKSSRV Microsoft Streaming Se Kernel
MsLldp Microsoft Link-Layer D Kernel
MSPCLOCK Microsoft Streaming Cl Kernel
MSPQM Microsoft Streaming Qu Kernel
MsRPC MsRPC Kernel
MsSecFlt Microsoft Security Eve Kernel
mssmbios Microsoft System Manag Kernel
MSTEE Microsoft Streaming Te Kernel
MTConfig Microsoft Input Config Kernel
Mup Mup File System
mvumis mvumis Kernel 5/23/2014 5:39:04 PM
NativeWifiP NativeWiFi Filter Kernel
ndfltr NetworkDirect Service Kernel 4/25/2018 1:28:08 PM
NDIS NDIS System Driver Kernel
NdisCap Microsoft NDIS Capture Kernel
NdisImPlatfo Microsoft Network Adap Kernel
NdisTapi Remote Access NDIS TAP Kernel
Ndisuio NDIS Usermode I/O Prot Kernel
NdisVirtualB Microsoft Virtual Netw Kernel
NdisWan Remote Access NDIS WAN Kernel
ndiswanlegac Remote Access LEGACY N Kernel
NDKPing NDKPing Driver Kernel
ndproxy NDIS Proxy Driver Kernel
Ndu Windows Network Data U Kernel
NetAdapterCx Network Adapter Wdf Cl Kernel
NetBIOS NetBIOS Interface File System
NetBT NetBT Kernel
netvsc netvsc Kernel
Npfs Npfs File System
npsvctrig Named pipe service tri Kernel
nsiproxy NSI Proxy Service Driv Kernel
Ntfs Ntfs File System
Null Null Kernel
nvdimm Microsoft NVDIMM devic Kernel
nvraid nvraid Kernel 4/21/2014 3:28:42 PM
nvstor nvstor Kernel 4/21/2014 3:34:03 PM
Parport Parallel port driver Kernel
partmgr Partition driver Kernel
pci PCI Bus Driver Kernel
pciide pciide Kernel
pcmcia pcmcia Kernel
pcw Performance Counters f Kernel
pdc pdc Kernel
PEAUTH PEAUTH Kernel
percsas2i percsas2i Kernel 3/14/2016 9:50:11 PM
percsas3i percsas3i Kernel 6/1/2018 6:47:02 PM
PktMon Packet Monitor Driver Kernel
pmem Microsoft persistent m Kernel
PNPMEM Microsoft Memory Modul Kernel
portcfg portcfg Kernel
PptpMiniport WAN Miniport (PPTP) Kernel
Processor Processor Driver Kernel
Psched QoS Packet Scheduler Kernel
QWAVEdrv QWAVE driver Kernel
Ramdisk Windows RAM Disk Drive Kernel
RasAcd Remote Access Auto Con Kernel
RasAgileVpn WAN Miniport (IKEv2) Kernel
Rasl2tp WAN Miniport (L2TP) Kernel
RasPppoe Remote Access PPPOE Dr Kernel
RasSstp WAN Miniport (SSTP) Kernel
rdbss Redirected Buffering S File System
rdpbus Remote Desktop Device Kernel
RDPDR Remote Desktop Device Kernel
RdpVideoMini Remote Desktop Video M Kernel
rdyboost ReadyBoost Kernel
ReFS ReFS File System
ReFSv1 ReFSv1 File System
RFCOMM Bluetooth Device (RFCO Kernel
rhproxy Resource Hub proxy dri Kernel
rspndr Link-Layer Topology Di Kernel
s3cap s3cap Kernel -
sbp2port SBP-2 Transport/Protoc Kernel
scfilter Smart card PnP Class F Kernel
scmbus Microsoft Storage Clas Kernel
sdbus sdbus Kernel
SDFRd SDF Reflector Kernel
sdstor SD Storage Port Driver Kernel
SerCx Serial UART Support Li Kernel
SerCx2 Serial UART Support Li Kernel
Serenum Serenum Filter Driver Kernel
Serial Serial port driver Kernel
sermouse Serial Mouse Driver Kernel
sfloppy High-Capacity Floppy D Kernel
SgrmAgent System Guard Runtime M Kernel
SiSRaid2 SiSRaid2 Kernel 9/24/2008 3:28:20 PM
SiSRaid4 SiSRaid4 Kernel 10/1/2008 6:56:04 PM
SmartSAMD SmartSAMD Kernel 4/17/2018 12:29:21 PM
smbdirect smbdirect File System
spaceport Storage Spaces Driver Kernel
SpatialGraph Holographic Spatial Gr Kernel
SpbCx Simple Peripheral Bus Kernel
srv Server SMB 1.xxx Drive File System
srv2 Server SMB 2.xxx Drive File System
srvnet srvnet File System
stexstor stexstor Kernel 11/26/2012 9:02:51 PM
storahci Microsoft Standard SAT Kernel
storflt Microsoft Hyper-V Stor Kernel
stornvme Microsoft Standard NVM Kernel
storqosflt Storage QoS Filter Dri File System
storufs Microsoft Universal Fl Kernel
storvsc storvsc Kernel
swenum Software Bus Driver Kernel
Synth3dVsc Synth3dVsc Kernel
Tcpip TCP/IP Protocol Driver Kernel
Tcpip6 @todo.dll,-100;Microso Kernel
tcpipreg TCP/IP Registry Compat Kernel
tdx NetIO Legacy TDI Suppo Kernel
terminpt Microsoft Remote Deskt Kernel
TPM TPM Kernel
TsUsbFlt Remote Desktop USB Hub Kernel
TsUsbGD Remote Desktop Generic Kernel
tsusbhub Remote Desktop USB Hub Kernel
tunnel Microsoft Tunnel Minip Kernel
UASPStor USB Attached SCSI (UAS Kernel
UcmCx0101 USB Connector Manager Kernel
UcmTcpciCx01 UCM-TCPCI KMDF Class E Kernel
UcmUcsiAcpiC UCM-UCSI ACPI Client Kernel
UcmUcsiCx010 UCM-UCSI KMDF Class Ex Kernel
Ucx01000 USB Host Support Libra Kernel
UdeCx USB Device Emulation S Kernel
udfs udfs File System
UEFI Microsoft UEFI Driver Kernel
UevAgentDriv UevAgentDriver File System
Ufx01000 USB Function Class Ext Kernel
UfxChipidea USB Chipidea Controlle Kernel
ufxsynopsys USB Synopsys Controlle Kernel
umbus UMBus Enumerator Drive Kernel
UmPass Microsoft UMPass Drive Kernel
UrsChipidea Chipidea USB Role-Swit Kernel
UrsCx01000 USB Role-Switch Suppor Kernel
UrsSynopsys Synopsys USB Role-Swit Kernel
usbaudio USB Audio Driver (WDM) Kernel
usbaudio2 USB Audio 2.0 Service Kernel
usbccgp Microsoft USB Generic Kernel
usbcir eHome Infrared Receive Kernel
usbehci Microsoft USB 2.0 Enha Kernel
usbhub Microsoft USB Standard Kernel
USBHUB3 SuperSpeed Hub Kernel
usbohci Microsoft USB Open Hos Kernel
usbprint Microsoft USB PRINTER Kernel
usbser Microsoft USB Serial D Kernel
USBSTOR USB Mass Storage Drive Kernel
usbuhci Microsoft USB Universa Kernel
USBXHCI USB xHCI Compliant Hos Kernel
vdrvroot Microsoft Virtual Driv Kernel
VerifierExt Driver Verifier Extens Kernel
vhdmp vhdmp Kernel
vhf Virtual HID Framework Kernel
Vid Vid Kernel
vm3dmp vm3dmp Kernel 7/15/2022 12:35:55 PM
vm3dmp-debug vm3dmp-debug Kernel 7/15/2022 12:36:14 PM
vm3dmp-stats vm3dmp-stats Kernel 7/15/2022 12:36:31 PM
vm3dmp_loade vm3dmp_loader Kernel 7/15/2022 12:35:47 PM
vmbus Virtual Machine Bus Kernel
VMBusHID VMBusHID Kernel
vmci VMware VMCI Bus Driver Kernel 11/21/2021 11:21:56 PM
vmgid Microsoft Hyper-V Gues Kernel
vmhgfs VMware Host Guest Clie File System 11/17/2021 1:32:25 AM -
VMMemCtl Memory Control Driver Kernel 11/17/2021 1:40:06 AM
vmmouse VMware Pointing Device Kernel 11/24/2021 2:03:02 AM
VMRawDsk VMware Physical Disk H Kernel 11/17/2021 1:40:19 AM
volmgr Volume Manager Driver Kernel
volmgrx Dynamic Volume Manager Kernel
volsnap Volume Shadow Copy dri Kernel
volume Volume driver Kernel
vpci Microsoft Hyper-V Virt Kernel
vsmraid vsmraid Kernel 4/22/2014 4:21:41 PM
vsock vSockets Virtual Machi Kernel 11/21/2021 11:22:26 PM
VSTXRAID VIA StorX Storage RAID Kernel 1/21/2013 4:00:28 PM
vwifibus Virtual Wireless Bus D Kernel
vwififlt Virtual WiFi Filter Dr Kernel
WacomPen Wacom Serial Pen HID D Kernel
wanarp Remote Access IP ARP D Kernel
wanarpv6 Remote Access IPv6 ARP Kernel
wcifs Windows Container Isol File System
wcnfs Windows Container Name File System
WdBoot Windows Defender Antiv Kernel
Wdf01000 Kernel Mode Driver Fra Kernel
WdFilter Windows Defender Antiv File System
wdiwifi WDI Driver Framework Kernel
WdmCompanion WdmCompanionFilter Kernel
WdNisDrv Windows Defender Antiv Kernel
WFPLWFS Microsoft Windows Filt Kernel
WIMMount WIMMount File System
WindowsTrust Windows Trusted Execut Kernel
WindowsTrust Microsoft Windows Trus Kernel
WinMad WinMad Service Kernel 4/25/2018 1:27:32 PM
WinNat Windows NAT Driver Kernel
WinQuic WinQuic Kernel
WINUSB WinUsb Driver Kernel
WinVerbs WinVerbs Service Kernel 4/25/2018 1:28:00 PM
WmiAcpi Microsoft Windows Mana Kernel
Wof Windows Overlay File S File System
WpdUpFltr WPD Upper Class Filter Kernel
ws2ifsl Windows Socket 2.0 Non Kernel
WudfPf User Mode Driver Frame Kernel
WUDFRd Windows Driver Foundat Kernel
xboxgip Xbox Game Input Protoc Kernel
xinputhid XINPUT HID Filter Driv Kernel
C:\Users\admin> -
-
-
 HyperDbg has a command for unloading and removing its driver "unload remove vmm", but it only works if the driver is loaded in the current instance which may not work in this case.
HyperDbg has a command for unloading and removing its driver "unload remove vmm", but it only works if the driver is loaded in the current instance which may not work in this case. -
 We have to manually unload these drivers. It's possible by using OSR driver loader but there should be some 'sc' command for that as well. Let me search.
We have to manually unload these drivers. It's possible by using OSR driver loader but there should be some 'sc' command for that as well. Let me search. -
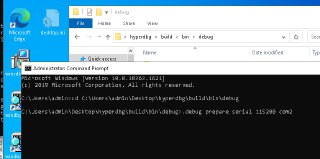
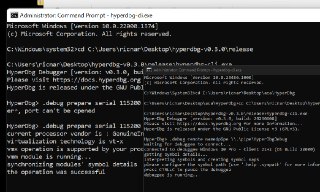
HyperDbg> .debug prepare serial 115200 com2
err, path to the driver not found, or the access to the driver file is limited
most of the time, it's because anti-virus software is not finished scanning the drivers, so, if you try to load the driver again (re-enter the previous command), the problem will be solved
unable to install VMM driver
failed to install or load the driver -
-
hprdbghv!AsmVmxSaveState+0x24:
fffff807`76d28d04 cc int 3
0: kd> u rip
hprdbghv!AsmVmxSaveState+0x24 [C:\Users\ricnar\Desktop\aca\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 38]:
fffff807`76d28d04 cc int 3
fffff807`76d28d05 e846200100 call hprdbghv!VmxVirtualizeCurrentSystem (fffff807`76d3ad50)
fffff807`76d28d0a cc int 3
fffff807`76d28d0b eb00 jmp hprdbghv!AsmVmxRestoreState (fffff807`76d28d0d)
hprdbghv!AsmVmxRestoreState [C:\Users\ricnar\Desktop\aca\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 51]:
fffff807`76d28d0d 4881c400010000 add rsp,100h
fffff807`76d28d14 415f pop r15
fffff807`76d28d16 415e pop r14
fffff807`76d28d18 415d pop r13 -
-
 Oh, yes.
Oh, yes. -
-
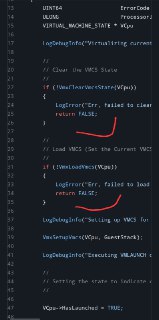
 Now, please step through the source code, change windbg mode from binary mode to source code and go through the VmxVirtualizeCurrentSystem function and see what stops it from running (what returns false).
Now, please step through the source code, change windbg mode from binary mode to source code and go through the VmxVirtualizeCurrentSystem function and see what stops it from running (what returns false). -
 Please also note that as you have two cores, probably two cores hit the breakpoint simultaneously. But that's not a problem just step through the source code.
Please also note that as you have two cores, probably two cores hit the breakpoint simultaneously. But that's not a problem just step through the source code. -
-
-
-
-
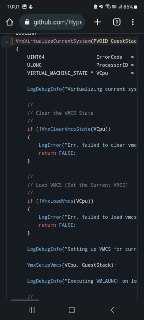
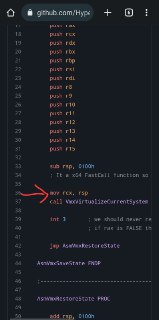
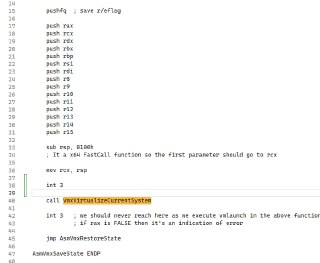
 That's okay, you can also understand what was wrong by only using disassembly. Just go to the VmxVirtualizeCurrentSystem function and step "p" though the instructions to see what was the guilty check.
That's okay, you can also understand what was wrong by only using disassembly. Just go to the VmxVirtualizeCurrentSystem function and step "p" though the instructions to see what was the guilty check.
This is source code of this function:
https://github.com/HyperDbg/HyperDbg/blob/a571781e8651998b982a9f53edf8f3d3501a6b2e/hyperdbg/hprdbghv/code/vmm/vmx/Vmx.c#L411HyperDbg/hyperdbg/hprdbghv/code/vmm/vmx/Vmx.c at a571781e8651998b982a9f53edf8f3d3501a6b2e · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
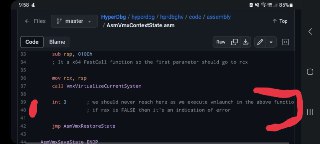
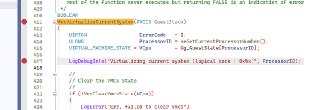
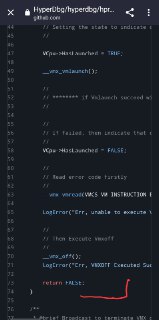
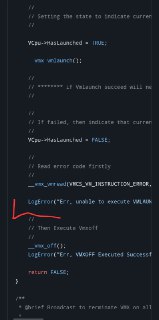
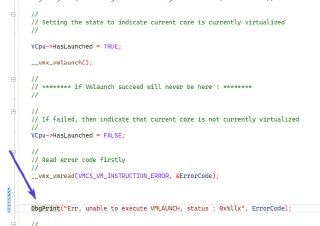
 Which of these functions return FALSE?
Which of these functions return FALSE? -

-
 Or maybe this:
Or maybe this: -

-
 Which one?
Which one? -
-
-
-
Microsoft (R) Windows Debugger Version 10.0.22621.1778 AMD64
Copyright (c) Microsoft Corporation. All rights reserved.
Using NET for debugging
Opened WinSock 2.0
Waiting to reconnect...
Connected to target 192.168.127.128 on port 50000 on local IP 192.168.127.1.
You can get the target MAC address by running .kdtargetmac command.
Connected to Windows 10 18362 x64 target at (Tue Jun 20 10:31:00.210 2023 (UTC - 3:00)), ptr64 TRUE
Kernel Debugger connection established.
************* Path validation summary **************
Response Time (ms) Location
Deferred SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Symbol search path is: SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 18362 MP (1 procs) Free x64
Edition build lab: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff804`4ac00000 PsLoadedModuleList = 0xfffff804`4b045f30
System Uptime: 0 days 0:00:01.983
KDTARGET: Refreshing KD connection
KDNET received an out of sequence ping packet.
The target machine restarted without notifying the debugger.
Forcing a debugger reconnect...
Shutdown occurred at (Tue Jun 20 10:40:22.551 2023 (UTC - 3:00))...unloading all symbol tables.
Using NET for debugging
Opened WinSock 2.0
Connected to target 192.168.127.128 on port 50000 on local IP 192.168.127.1.
You can get the target MAC address by running .kdtargetmac command.
Connected to Windows 10 18362 x64 target at (Tue Jun 20 10:40:22.673 2023 (UTC - 3:00)), ptr64 TRUE
Kernel Debugger connection established.
************* Path validation summary **************
Response Time (ms) Location
Deferred SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Symbol search path is: SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 18362 MP (1 procs) Free x64
Edition build lab: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff803`5ce00000 PsLoadedModuleList = 0xfffff803`5d245f30
System Uptime: 0 days 0:00:01.851
KDTARGET: Refreshing KD connection
Break instruction exception - code 80000003 (first chance)
hprdbghv!AsmVmxSaveState+0x29:
fffff808`7bb28cf9 cc int 3
1: kd> g
Break instruction exception - code 80000003 (first chance)
hprdbghv!AsmVmxSaveState+0x29:
fffff808`7bb28cf9 cc int 3
0: kd> g
KDTARGET: Refreshing KD connection
*** Fatal System Error: 0x0000003b
(0x00000000C000001D,0xFFFFF8087BB28D52,0xFFFFC907DEC1A840,0x0000000000000000)
Break instruction exception - code 80000003 (first chance)
A fatal system error has occurred.
Debugger entered on first try; Bugcheck callbacks have not been invoked.
A fatal system error has occurred.
For analysis of this file, run !analyze -v
nt!DbgBreakPointWithStatus:
fffff803`5cfcbc90 cc int 3
0: kd> g
KDNET received an out of sequence ping packet.
The target machine restarted without notifying the debugger.
Forcing a debugger reconnect...
Shutdown occurred at (Tue Jun 20 11:21:12.389 2023 (UTC - 3:00))...unloading all symbol tables.
Using NET for debugging
Opened WinSock 2.0
Connected to target 192.168.127.128 on port 50000 on local IP 192.168.127.1.
You can get the target MAC address by running .kdtargetmac command.
Connected to Windows 10 18362 x64 target at (Tue Jun 20 11:21:12.534 2023 (UTC - 3:00)), ptr64 TRUE
Kernel Debugger connection established.Symbol informationProvides information about the Microsoft Symbol Server.
-
************* Path validation summary **************
Response Time (ms) Location
Deferred SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Symbol search path is: SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 18362 MP (1 procs) Free x64
Edition build lab: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff807`13000000 PsLoadedModuleList = 0xfffff807`13445f30
System Uptime: 0 days 0:00:01.046
KDTARGET: Refreshing KD connection
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
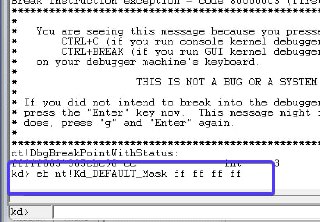
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`131cbc90 cc int 3
0: kd> g
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`131cbc90 cc int 3
1: kd> g
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *Symbol informationProvides information about the Microsoft Symbol Server.
-
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`131cbc90 cc int 3
0: kd> g
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`131cbc90 cc int 3
1: kd> g
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`131cbc90 cc int 3
0: kd> g
Break instruction exception - code 80000003 (first chance)
hprdbghv!AsmVmxSaveState+0x29:
fffff805`81978cf9 cc int 3
0: kd> k
# Child-SP RetAddr Call Site
00 ffff8283`1fbbee90 ffff8283`1fbbee90 hprdbghv!AsmVmxSaveState+0x29 [D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 39]
01 ffff8283`1fbbee98 00000000`00000002 0xffff8283`1fbbee90
02 ffff8283`1fbbeea0 00000000`00000000 0x2
0: kd> .reload
Connected to Windows 10 18362 x64 target at (Tue Jun 20 11:28:41.673 2023 (UTC - 3:00)), ptr64 TRUE
Loading Kernel Symbols
.................................................
Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.
Run !sym noisy before .reload to track down problems loading symbols. -
..............
................................................................
...........................................................
Loading User Symbols
......................................
Loading unloaded module list
.......
0: kd> lm
start end module name
00007ff6`895c0000 00007ff6`89876000 hyperdbg_cli (deferred)
00007ffa`a0ab0000 00007ffa`a0f1d000 pdbex (deferred)
00007ffa`a0f20000 00007ffa`a11f8000 symbol_parser (deferred)
00007ffa`a1200000 00007ffa`a13a0000 hprdbgrev (deferred)
00007ffa`a13a0000 00007ffa`a1589000 script_engine (deferred)
00007ffa`a1590000 00007ffa`a1a6d000 HPRDBGCTRL (deferred)
00007ffa`b84a0000 00007ffa`b8694000 dbghelp (deferred)
00007ffa`bc2d0000 00007ffa`bc4a5000 urlmon (deferred)
00007ffa`bdb60000 00007ffa`bde07000 iertutil (deferred)
00007ffa`c36e0000 00007ffa`c376f000 apphelp (deferred)
00007ffa`c4e40000 00007ffa`c4e4c000 CRYPTBASE (deferred)
00007ffa`c5490000 00007ffa`c54a0000 UMPDC (deferred)
00007ffa`c54a0000 00007ffa`c54b1000 kernel_appcore (deferred)
00007ffa`c54c0000 00007ffa`c550a000 powrprof (deferred)
00007ffa`c5530000 00007ffa`c554e000 profapi (deferred)
00007ffa`c5740000 00007ffa`c57de000 msvcp_win (deferred)
00007ffa`c57e0000 00007ffa`c5801000 win32u (deferred)
00007ffa`c58c0000 00007ffa`c59ba000 ucrtbase (deferred)
00007ffa`c59e0000 00007ffa`c5c85000 KERNELBASE (deferred)
00007ffa`c5c90000 00007ffa`c5d14000 bcryptPrimitives (deferred)
00007ffa`c5d70000 00007ffa`c64eb000 windows_storage (deferred)
00007ffa`c64f0000 00007ffa`c6688000 gdi32full (deferred)
00007ffa`c6690000 00007ffa`c672e000 msvcrt (deferred)
00007ffa`c6730000 00007ffa`c67d9000 shcore (deferred)
00007ffa`c67e0000 00007ffa`c6806000 GDI32 (deferred)
00007ffa`c6810000 00007ffa`c6862000 SHLWAPI (deferred)
00007ffa`c6870000 00007ffa`c6922000 KERNEL32 (deferred)
00007ffa`c6930000 00007ffa`c6ac4000 USER32 (deferred)
00007ffa`c6ad0000 00007ffa`c6b67000 sechost (deferred)
00007ffa`c6fc0000 00007ffa`c702f000 WS2_32 (deferred)
00007ffa`c7030000 00007ffa`c7366000 combase (deferred)
00007ffa`c7420000 00007ffa`c744e000 IMM32 (deferred)
00007ffa`c78c0000 00007ffa`c78c8000 PSAPI (deferred)
00007ffa`c7930000 00007ffa`c79d3000 ADVAPI32 (deferred)
00007ffa`c7a00000 00007ffa`c7b57000 ole32 (deferred)
00007ffa`c7bf0000 00007ffa`c7cb5000 OLEAUT32 (deferred)
00007ffa`c7cc0000 00007ffa`c7ddf000 RPCRT4 (deferred)
00007ffa`c85e0000 00007ffa`c87d0000 ntdll (pdb symbols) c:\symbols\ntdll.pdb\BF51864800EAAA852CE7A7AF426B3F011\ntdll.pdb
ffffac9f`b9c00000 ffffac9f`b9fa2000 win32kfull (deferred)
ffffac9f`b9fb0000 ffffac9f`ba252000 win32kbase (deferred)
ffffac9f`ba260000 ffffac9f`ba2a8000 cdd (deferred)
ffffac9f`baa00000 ffffac9f`baa8c000 win32k (deferred)
fffff805`80020000 fffff805`8003f000 dump_lsi_sas (deferred)
fffff805`80060000 fffff805`8007d000 dump_dumpfve (deferred)
fffff805`80090000 fffff805`800c0000 cdrom (deferred)
fffff805`800d0000 fffff805`800e5000 filecrypt (deferred)
fffff805`800f0000 fffff805`800fe000 tbs (deferred)
fffff805`80100000 fffff805`8010a000 Null (deferred)
fffff805`80110000 fffff805`8011a000 Beep (deferred)
fffff805`80120000 fffff805`80131000 vmrawdsk (deferred) -
fffff805`80140000 fffff805`804b1000 dxgkrnl (deferred)
fffff805`804c0000 fffff805`804d6000 watchdog (deferred)
fffff805`804e0000 fffff805`804f6000 BasicDisplay (deferred)
fffff805`80500000 fffff805`80511000 BasicRender (deferred)
fffff805`80520000 fffff805`8053c000 Npfs (deferred)
fffff805`80540000 fffff805`80551000 Msfs (deferred)
fffff805`80560000 fffff805`80586000 tdx (deferred)
fffff805`80590000 fffff805`805a0000 TDI (deferred)
fffff805`805b0000 fffff805`805be000 ws2ifsl (deferred)
fffff805`805c0000 fffff805`80619000 netbt (deferred)
fffff805`80620000 fffff805`80633000 afunix (deferred)
fffff805`80640000 fffff805`806e7000 afd (deferred)
fffff805`806f0000 fffff805`8070a000 vwififlt (deferred)
fffff805`80710000 fffff805`8073b000 pacer (deferred)
fffff805`80740000 fffff805`80754000 netbios (deferred)
fffff805`80760000 fffff805`807db000 rdbss (deferred)
fffff805`807e0000 fffff805`80874000 csc (deferred)
fffff805`80880000 fffff805`80892000 nsiproxy (deferred)
fffff805`808a0000 fffff805`808ad000 npsvctrig (deferred)
fffff805`808b0000 fffff805`808c0000 mssmbios (deferred)
fffff805`808d0000 fffff805`808da000 gpuenergydrv (deferred)
fffff805`808e0000 fffff805`8090c000 dfsc (deferred)
fffff805`80910000 fffff805`80928000 monitor (deferred)
fffff805`80930000 fffff805`80946000 bam (deferred)
fffff805`80950000 fffff805`8099f000 ahcache (deferred)
fffff805`809a0000 fffff805`80a2d000 Vid (deferred)
fffff805`80a30000 fffff805`80a4f000 winhvr (deferred)
fffff805`80a50000 fffff805`80a61000 CompositeBus (deferred)
fffff805`80a70000 fffff805`80a7d000 kdnic (deferred)
fffff805`80a80000 fffff805`80a95000 umbus (deferred)
fffff805`80aa0000 fffff805`80ac3000 i8042prt (deferred)
fffff805`80ad0000 fffff805`80ae4000 kbdclass (deferred)
fffff805`80af0000 fffff805`80af9000 vmmouse (deferred)
fffff805`80b00000 fffff805`80b13000 mouclass (deferred)
fffff805`80b20000 fffff805`80b3f000 parport (deferred)
fffff805`80b40000 fffff805`80b5c000 serial (deferred)
fffff805`80b60000 fffff805`80b6f000 serenum (deferred)
fffff805`80b70000 fffff805`80b7f000 fdc (deferred)
fffff805`80b80000 fffff805`80b8a000 vm3dmp_loader (deferred)
fffff805`80b90000 fffff805`80be2000 vm3dmp (deferred)
fffff805`80bf0000 fffff805`80bff000 CmBatt (deferred)
fffff805`80c00000 fffff805`80c10000 BATTC (deferred)
fffff805`80c20000 fffff805`80c5e000 intelppm (deferred)
fffff805`80c60000 fffff805`80c6d000 NdisVirtualBus (deferred)
fffff805`80c70000 fffff805`80c7c000 swenum (deferred)
fffff805`80c80000 fffff805`80cf8000 ks (deferred)
fffff805`80d00000 fffff805`80d0e000 rdpbus (deferred)
fffff805`80d10000 fffff805`80d6b000 udfs (deferred)
fffff805`80d70000 fffff805`80d83000 HIDPARSE (deferred)
fffff805`80da0000 fffff805`80dae000 dump_diskdump (deferred)
fffff805`80dd0000 fffff805`80ded000 crashdmp (deferred)
fffff805`80e00000 fffff805`80e8f000 mrxsmb (deferred)
fffff805`80e90000 fffff805`80ed5000 mrxsmb20 (deferred)
fffff805`80ee0000 fffff805`80ef8000 lltdio (deferred)
fffff805`80f00000 fffff805`80f19000 mslldp (deferred) -
fffff805`80f20000 fffff805`80f3b000 rspndr (deferred)
fffff805`80f40000 fffff805`80f5d000 wanarp (deferred)
fffff805`80f60000 fffff805`810a4000 HTTP (deferred)
fffff805`810b0000 fffff805`810ca000 mpsdrv (deferred)
fffff805`810d0000 fffff805`81123000 srvnet (deferred)
fffff805`81130000 fffff805`811f5000 srv2 (deferred)
fffff805`81200000 fffff805`8120a000 vmmemctl (deferred)
fffff805`81210000 fffff805`81224000 mmcss (deferred)
fffff805`81230000 fffff805`81282000 mrxsmb10 (deferred)
fffff805`81290000 fffff805`812b7000 Ndu (deferred)
fffff805`81330000 fffff805`8140a000 dxgmms2 (deferred)
fffff805`81410000 fffff805`8141d000 rdpvideominiport (deferred)
fffff805`81450000 fffff805`81487000 wcifs (deferred)
fffff805`81490000 fffff805`81507000 cldflt (deferred)
fffff805`81510000 fffff805`8153f000 rdpdr (deferred)
fffff805`81540000 fffff805`8155a000 storqosflt (deferred)
fffff805`81560000 fffff805`81587000 tsusbhub (deferred)
fffff805`81590000 fffff805`815b5000 bowser (deferred)
fffff805`815c0000 fffff805`815f8000 winquic (deferred)
fffff805`81800000 fffff805`8182c000 vmhgfs (deferred)
fffff805`81830000 fffff805`81852000 rasl2tp (deferred)
fffff805`81860000 fffff805`81880000 raspptp (deferred)
fffff805`81890000 fffff805`818a3000 condrv (deferred)
fffff805`818b0000 fffff805`818cc000 raspppoe (deferred)
fffff805`818d0000 fffff805`818df000 ndistapi (deferred)
fffff805`818e0000 fffff805`8191a000 ndiswan (deferred)
fffff805`81920000 fffff805`8193c000 WdNisDrv (deferred)
fffff805`81940000 fffff805`81957000 hprdbgkd (deferred)
fffff805`81960000 fffff805`8196b000 hyperlog (deferred)
fffff805`81970000 fffff805`819f6000 hprdbghv (private pdb symbols) c:\symbols\hprdbghv.pdb\CD299968B52442318710EFF6CE521E681\hprdbghv.pdb
fffff805`81a00000 fffff805`81a0e000 kdserial (deferred)
fffff805`823c0000 fffff805`82496000 peauth (deferred)
fffff805`824a0000 fffff805`82535000 srv (deferred)
fffff805`82540000 fffff805`82554000 tcpipreg (deferred)
fffff805`82560000 fffff805`8257d000 rassstp (deferred)
fffff805`82580000 fffff805`825c1000 NDProxy (deferred)
fffff805`825d0000 fffff805`825f7000 AgileVpn (deferred)
fffff807`12f5c000 fffff807`13000000 hal (deferred)
fffff807`13000000 fffff807`13ab5000 nt (pdb symbols) c:\symbols\ntkrnlmp.pdb\2146E84F70B609E577618A477DC70B541\ntkrnlmp.pdb
fffff807`16200000 fffff807`16247000 kd_02_8086 (deferred)
fffff807`16250000 fffff807`16299000 kdcom (deferred)
fffff807`162a0000 fffff807`164a1000 mcupdate_GenuineIntel (deferred)
fffff807`164b0000 fffff807`164c1000 werkernel (deferred)
fffff807`164d0000 fffff807`164f9000 ksecdd (deferred)
fffff807`16500000 fffff807`16561000 msrpc (deferred)
fffff807`16570000 fffff807`16597000 tm (deferred)
fffff807`165a0000 fffff807`165ba000 PSHED (deferred)
fffff807`165c0000 fffff807`165cb000 BOOTVID (deferred)
fffff807`165d0000 fffff807`165de000 cmimcext (deferred)
fffff807`165e0000 fffff807`165ec000 ntosext (deferred)
fffff807`165f0000 fffff807`165ff000 SleepStudyHelper (deferred)
fffff807`16690000 fffff807`166f8000 CLFS (deferred)
fffff807`16700000 fffff807`16805000 clipsp (deferred) -
fffff807`16810000 fffff807`16881000 FLTMGR (deferred)
fffff807`16890000 fffff807`1696f000 CI (deferred)
fffff807`16970000 fffff807`16a2f000 cng (deferred)
fffff807`16a30000 fffff807`16b05000 Wdf01000 (deferred)
fffff807`16b10000 fffff807`16b23000 WDFLDR (deferred)
fffff807`16b30000 fffff807`16b40000 WppRecorder (deferred)
fffff807`16b50000 fffff807`16b75000 acpiex (deferred)
fffff807`16b80000 fffff807`16bc9000 mssecflt (deferred)
fffff807`16bd0000 fffff807`16bea000 SgrmAgent (deferred)
fffff807`16bf0000 fffff807`16cbc000 ACPI (deferred)
fffff807`16cc0000 fffff807`16ccc000 WMILIB (deferred)
fffff807`16cf0000 fffff807`16d4b000 intelpep (deferred)
fffff807`16d50000 fffff807`16d67000 WindowsTrustedRT (deferred)
fffff807`16d70000 fffff807`16d7b000 WindowsTrustedRTProxy (deferred)
fffff807`16d80000 fffff807`16d95000 pcw (deferred)
fffff807`16da0000 fffff807`16dab000 msisadrv (deferred)
fffff807`16db0000 fffff807`16e1e000 pci (deferred)
fffff807`16e20000 fffff807`16e33000 vdrvroot (deferred)
fffff807`16e40000 fffff807`16e81000 ucx01000 (deferred)
fffff807`16e90000 fffff807`16ec3000 pdc (deferred)
fffff807`16ed0000 fffff807`16ee9000 CEA (deferred)
fffff807`16ef0000 fffff807`16f20000 partmgr (deferred)
fffff807`16f30000 fffff807`16fd5000 spaceport (deferred)
fffff807`16fe0000 fffff807`16feb000 intelide (deferred)
fffff807`16ff0000 fffff807`17003000 PCIIDEX (deferred)
fffff807`17010000 fffff807`1702a000 volmgr (deferred)
fffff807`17030000 fffff807`1707e000 sdbus (deferred)
fffff807`17080000 fffff807`170e3000 volmgrx (deferred)
fffff807`170f0000 fffff807`17108000 vsock (deferred)
fffff807`17110000 fffff807`1712c000 vmci (deferred)
fffff807`17130000 fffff807`17148000 urscx01000 (deferred)
fffff807`17150000 fffff807`1716f000 mountmgr (deferred)
fffff807`17170000 fffff807`1718f000 lsi_sas (deferred)
fffff807`17190000 fffff807`17234000 storport (deferred)
fffff807`17240000 fffff807`1724d000 atapi (deferred)
fffff807`17250000 fffff807`1728b000 ataport (deferred)
fffff807`17290000 fffff807`172ab000 EhStorClass (deferred)
fffff807`172b0000 fffff807`172ca000 fileinfo (deferred)
fffff807`172d0000 fffff807`1730d000 Wof (deferred)
fffff807`17310000 fffff807`1738e000 WdFilter (deferred)
fffff807`17390000 fffff807`1762c000 Ntfs (deferred)
fffff807`17630000 fffff807`17663000 usbccgp (deferred)
fffff807`17670000 fffff807`1767e000 USBD (deferred)
fffff807`17680000 fffff807`1768d000 urschipidea (deferred)
fffff807`17690000 fffff807`176ad000 usbehci (deferred)
fffff807`176b0000 fffff807`1772a000 USBPORT (deferred)
fffff807`17730000 fffff807`177ba000 usbhub (deferred)
fffff807`177c0000 fffff807`17860000 UsbHub3 (deferred)
fffff807`17870000 fffff807`1787d000 Fs_Rec (deferred)
fffff807`17880000 fffff807`179f1000 ndis (deferred)
fffff807`17a00000 fffff807`17a94000 NETIO (deferred)
fffff807`17aa0000 fffff807`17ad2000 ksecpkg (deferred)
fffff807`17ae0000 fffff807`17dcc000 tcpip (deferred)
fffff807`17dd0000 fffff807`17e4a000 fwpkclnt (deferred)
fffff807`17e50000 fffff807`17e80000 wfplwfs (deferred) -
fffff807`17e90000 fffff807`17f59000 fvevol (deferred)
fffff807`17f60000 fffff807`17f6b000 volume (deferred)
fffff807`17f70000 fffff807`17fdd000 volsnap (deferred)
fffff807`17fe0000 fffff807`18069000 USBXHCI (deferred)
fffff807`18070000 fffff807`18095000 USBSTOR (deferred)
fffff807`180a0000 fffff807`180b8000 uaspstor (deferred)
fffff807`180c0000 fffff807`180de000 sdstor (deferred)
fffff807`180e0000 fffff807`1812e000 rdyboost (deferred)
fffff807`18130000 fffff807`18156000 mup (deferred)
fffff807`18160000 fffff807`18172000 iorate (deferred)
fffff807`181a0000 fffff807`181bc000 disk (deferred)
fffff807`181c0000 fffff807`1822c000 CLASSPNP (deferred)
Unloaded modules:
fffff805`81420000 fffff805`8144b000 luafv.sys
fffff805`80000000 fffff805`8000f000 dump_storport.sys
fffff805`80030000 fffff805`80050000 dump_lsi_sas.sys
fffff805`80070000 fffff805`8008e000 dump_dumpfve.sys
fffff805`80910000 fffff805`8092e000 dam.sys
fffff807`16cd0000 fffff807`16ce1000 WdBoot.sys
fffff807`18180000 fffff807`18191000 hwpolicy.sys
0: kd> .reload /f
Connected to Windows 10 18362 x64 target at (Tue Jun 20 11:29:29.829 2023 (UTC - 3:00)), ptr64 TRUE
Loading Kernel Symbols
...............................................................
...........................................................
Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.
Run !sym noisy before .reload to track down problems loading symbols.
.....
...........................................................
Loading User Symbols
.*** WARNING: Unable to verify checksum for hyperdbg-cli.exe
.....*** WARNING: Unable to verify checksum for HPRDBGCTRL.dll
................*** WARNING: Unable to verify checksum for script-engine.dll
.*** WARNING: Unable to verify checksum for hprdbgrev.dll
.*** WARNING: Unable to verify checksum for symbol-parser.dll
..........*** WARNING: Unable to verify checksum for pdbex.dll
Press ctrl-c (cdb, kd, ntsd) or ctrl-break (windbg) to abort symbol loads that take too long.
Run !sym noisy before .reload to track down problems loading symbols.
....
Loading unloaded module list
.......
************* Symbol Loading Error Summary **************
Module name Error
clipsp The system cannot find the file specified
vsock The system cannot find the file specified
vmci The system cannot find the file specified
WdFilter The system cannot find the file specified
vmrawdsk The system cannot find the file specified
vmmouse The system cannot find the file specified
vm3dmp_loader The system cannot find the file specified
vm3dmp The system cannot find the file specified
vmmemctl The system cannot find the file specified
peauth The system cannot find the file specified
vmhgfs The system cannot find the file specified
WdNisDrv The system cannot find the file specified
hprdbgkd The system cannot find the file specified
hyperlog The system cannot find the file specified
kdserial The system cannot find the file specified -
You can troubleshoot most symbol related issues by turning on symbol loading diagnostics (!sym noisy) and repeating the command that caused symbols to be loaded.
You should also verify that your symbol search path (.sympath) is correct.
0: kd> k
# Child-SP RetAddr Call Site
00 ffff8283`1fbbee90 ffff8283`1fbbee90 hprdbghv!AsmVmxSaveState+0x29 [D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 39]
01 ffff8283`1fbbee98 00000000`00000002 0xffff8283`1fbbee90
02 ffff8283`1fbbeea0 00000000`00000000 0x2
0: kd> x *!VmxVirtualizeCurrentSystem
fffff805`8198abb0 hprdbghv!VmxVirtualizeCurrentSystem (void *)
0: kd> u fffff805`8198abb0
hprdbghv!VmxVirtualizeCurrentSystem [D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\vmm\vmx\Vmx.c @ 412]:
fffff805`8198abb0 48894c2408 mov qword ptr [rsp+8],rcx
fffff805`8198abb5 4883ec68 sub rsp,68h
fffff805`8198abb9 48c744245000000000 mov qword ptr [rsp+50h],0
fffff805`8198abc2 e8292dffff call hprdbghv!KeGetCurrentProcessorNumber (fffff805`8197d8f0)
fffff805`8198abc7 89442440 mov dword ptr [rsp+40h],eax
fffff805`8198abcb 8b442440 mov eax,dword ptr [rsp+40h]
fffff805`8198abcf 4869c0e8010000 imul rax,rax,1E8h
fffff805`8198abd6 488b0d9b360600 mov rcx,qword ptr [hprdbghv!g_GuestState (fffff805`819ee278)]
windbg> .open -a fffff8058198abb0
0: kd> p
hprdbghv!AsmVmxSaveState+0x2a:
fffff805`81978cfa eb00 jmp hprdbghv!AsmVmxRestoreState (fffff805`81978cfc)
0: kd> ub rip
hprdbghv!AsmVmxSaveState+0x12 [D:\a\HyperDbg\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 28]:
fffff805`81978ce2 4154 push r12
fffff805`81978ce4 4155 push r13
fffff805`81978ce6 4156 push r14
fffff805`81978ce8 4157 push r15
fffff805`81978cea 4881ec00010000 sub rsp,100h
fffff805`81978cf1 488bcc mov rcx,rsp
fffff805`81978cf4 e8b71e0100 call hprdbghv!VmxVirtualizeCurrentSystem (fffff805`8198abb0)
fffff805`81978cf9 cc int 3
0: kd> g
KDNET received an out of sequence ping packet.
The target machine restarted without notifying the debugger.
Forcing a debugger reconnect...
KDNET received an out of sequence ping packet.
The target machine restarted without notifying the debugger.
Forcing a debugger reconnect...
Shutdown occurred at (Tue Jun 20 13:54:32.830 2023 (UTC - 3:00))...unloading all symbol tables.
Using NET for debugging
Opened WinSock 2.0
Connected to target 192.168.127.128 on port 50000 on local IP 192.168.127.1.
You can get the target MAC address by running .kdtargetmac command.
KDTARGET: Refreshing KD connection
Connected to Windows 10 18362 x64 target at (Tue Jun 20 13:54:43.349 2023 (UTC - 3:00)), ptr64 TRUE
Kernel Debugger connection established. -
************* Path validation summary **************
Response Time (ms) Location
Deferred SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Symbol search path is: SRV*c:\Symbols*http://msdl.microsoft.com/download/symbols
Executable search path is:
Windows 10 Kernel Version 18362 MP (2 procs) Free x64
Product: WinNt, suite: TerminalServer SingleUserTS
Edition build lab: 18362.1.amd64fre.19h1_release.190318-1202
Machine Name:
Kernel base = 0xfffff807`7a000000 PsLoadedModuleList = 0xfffff807`7a445f30
Debug session time: Tue Jun 20 13:54:44.002 2023 (UTC - 3:00)
System Uptime: 0 days 0:00:28.722
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`7a1cbc90 cc int 3
1: kd> lm
start end module name
fffff807`7a000000 fffff807`7aab5000 nt (pdb symbols) c:\symbols\ntkrnlmp.pdb\2146E84F70B609E577618A477DC70B541\ntkrnlmp.pdb
fffff808`ec8d0000 fffff808`ec8e6000 BasicDisplay (deferred)
fffff808`ec8f0000 fffff808`ec901000 BasicRender (deferred)
fffff808`ec910000 fffff808`ec92c000 Npfs (deferred)
fffff808`ec930000 fffff808`ec941000 Msfs (deferred)
fffff808`ec950000 fffff808`ec976000 tdx (deferred)
fffff808`ec980000 fffff808`ec990000 TDI (deferred)
fffff808`ec9a0000 fffff808`ec9ae000 ws2ifsl (deferred)
fffff808`ec9b0000 fffff808`eca09000 netbt (deferred)
fffff808`eca10000 fffff808`eca23000 afunix (deferred)
fffff808`eca30000 fffff808`ecad7000 afd (deferred)
fffff808`ecae0000 fffff808`ecafa000 vwififlt (deferred)
fffff808`ecb00000 fffff808`ecb2b000 pacer (deferred)
fffff808`ecb30000 fffff808`ecb44000 netbios (deferred)
fffff808`ecb50000 fffff808`ecbcb000 rdbss (deferred)
fffff808`ecbd0000 fffff808`ecc64000 csc (deferred)
fffff808`ecc70000 fffff808`ecc82000 nsiproxy (deferred)
fffff808`ecc90000 fffff808`ecc9d000 npsvctrig (deferred)
fffff808`ecca0000 fffff808`eccb0000 mssmbios (deferred)
fffff808`eccc0000 fffff808`eccca000 gpuenergydrv (deferred)
fffff808`eccd0000 fffff808`eccfc000 dfsc (deferred)
fffff808`ecd20000 fffff808`ecd36000 bam (deferred)
fffff808`ecd40000 fffff808`ecd8f000 ahcache (deferred)
fffff808`ed380000 fffff808`ed40d000 Vid (deferred)
fffff808`ed410000 fffff808`ed42f000 winhvr (deferred)
fffff808`ed430000 fffff808`ed441000 CompositeBus (deferred)
fffff808`ed450000 fffff808`ed45d000 kdnic (deferred)Symbol informationProvides information about the Microsoft Symbol Server.
-
-
Unloaded modules:
fffff808`ecd00000 fffff808`ecd1e000 dam.sys
fffff807`7cad0000 fffff807`7cae1000 WdBoot.sys
fffff807`7df80000 fffff807`7df91000 hwpolicy.sys
1: kd> g
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`7a1cbc90 cc int 3
1: kd> g
Break instruction exception - code 80000003 (first chance)
hprdbghv!AsmVmxSaveState+0x24:
fffff807`76d28d04 cc int 3
0: kd> u rip
hprdbghv!AsmVmxSaveState+0x24 [C:\Users\ricnar\Desktop\aca\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 38]:
fffff807`76d28d04 cc int 3
fffff807`76d28d05 e846200100 call hprdbghv!VmxVirtualizeCurrentSystem (fffff807`76d3ad50)
fffff807`76d28d0a cc int 3
fffff807`76d28d0b eb00 jmp hprdbghv!AsmVmxRestoreState (fffff807`76d28d0d)
hprdbghv!AsmVmxRestoreState [C:\Users\ricnar\Desktop\aca\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxContextState.asm @ 51]:
fffff807`76d28d0d 4881c400010000 add rsp,100h
fffff807`76d28d14 415f pop r15
fffff807`76d28d16 415e pop r14
fffff807`76d28d18 415d pop r13
0: kd> t
hprdbghv!AsmVmxSaveState+0x25:
fffff807`76d28d05 e846200100 call hprdbghv!VmxVirtualizeCurrentSystem (fffff807`76d3ad50)
0: kd> t
hprdbghv!AsmVmxSaveState+0x24:
fffff807`76d28d04 cc int 3
1: kd> t
hprdbghv!AsmVmxSaveState+0x25:
fffff807`76d28d05 e846200100 call hprdbghv!VmxVirtualizeCurrentSystem (fffff807`76d3ad50)
1: kd> t
hprdbghv!VmxVirtualizeCurrentSystem:
fffff807`76d3ad50 48894c2408 mov qword ptr [rsp+8],rcx
1: kd> t
hprdbghv!VmxVirtualizeCurrentSystem+0x9:
fffff807`76d3ad59 cc int 3
1: kd> t
hprdbghv!VmxVirtualizeCurrentSystem+0xa:
fffff807`76d3ad5a 48c744245000000000 mov qword ptr [rsp+50h],0
1: kd> t
hprdbghv!VmxVirtualizeCurrentSystem+0x13:
fffff807`76d3ad63 e8882cffff call hprdbghv!KeGetCurrentProcessorNumber (fffff807`76d2d9f0)
1: kd> t
hprdbghv!KeGetCurrentProcessorNumber:
fffff807`76d2d9f0 658a042584010000 mov al,byte ptr gs:[184h]
1: kd> t
hprdbghv!KeGetCurrentProcessorNumber+0x8:
fffff807`76d2d9f8 0fb6c0 movzx eax,al
1: kd> t
hprdbghv!KeGetCurrentProcessorNumber+0xb:
fffff807`76d2d9fb c3 ret
1: kd> t
hprdbghv!VmxVirtualizeCurrentSystem+0x18:
fffff807`76d3ad68 89442440 mov dword ptr [rsp+40h],eax
1: kd> p
hprdbghv!VmxVirtualizeCurrentSystem+0x1c:
fffff807`76d3ad6c 8b442440 mov eax,dword ptr [rsp+40h]
1: kd> t
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), * -
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`7a1cbc90 cc int 3
1: kd> t
nt!DbgBreakPointWithStatus+0x1:
fffff807`7a1cbc91 c3 ret
1: kd> t
nt!KdCheckForDebugBreak+0x86b28:
fffff807`7a1e6a0c 90 nop
1: kd> t
nt!KdCheckForDebugBreak+0x86b29:
fffff807`7a1e6a0d e9f094f7ff jmp nt!KdCheckForDebugBreak+0x1e (fffff807`7a15ff02)
1: kd> t
nt!KdCheckForDebugBreak+0x1e:
fffff807`7a15ff02 4883c428 add rsp,28h
1: kd> t
nt!KdCheckForDebugBreak+0x22:
fffff807`7a15ff06 c3 ret
1: kd> t
nt!KeAccumulateTicks+0x1b80d3:
fffff807`7a1fa7a3 90 nop
1: kd> t
nt!KeAccumulateTicks+0x1b80d4:
fffff807`7a1fa7a4 e9787fe4ff jmp nt!KeAccumulateTicks+0x51 (fffff807`7a042721)
1: kd> u rip
nt!KeAccumulateTicks+0x1b80d4:
fffff807`7a1fa7a4 e9787fe4ff jmp nt!KeAccumulateTicks+0x51 (fffff807`7a042721)
fffff807`7a1fa7a9 cc int 3
fffff807`7a1fa7aa a801 test al,1
fffff807`7a1fa7ac 0f848d84e4ff je nt!KiCheckForTimerExpiration+0x18f (fffff807`7a042c3f)
fffff807`7a1fa7b2 4180fe02 cmp r14b,2
fffff807`7a1fa7b6 0f838384e4ff jae nt!KiCheckForTimerExpiration+0x18f (fffff807`7a042c3f)
fffff807`7a1fa7bc 65488b042520000000 mov rax,qword ptr gs:[20h]
fffff807`7a1fa7c5 488b90b8610000 mov rdx,qword ptr [rax+61B8h]
1: kd> gu
nt!KeClockInterruptNotify+0xc07:
fffff807`7a044477 488b7308 mov rsi,qword ptr [rbx+8]
1: kd> gu
fffff807`79f5f28c 0f1f440000 nop dword ptr [rax+rax]
1: kd> gu
Single step exception - code 80000004 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
hprdbghv!VmxVirtualizeCurrentSystem+0x2e:
fffff807`76d3ad7e 4803c8 add rcx,rax
1: kd> p
hprdbghv!VmxVirtualizeCurrentSystem+0x39:
fffff807`76d3ad89 33c0 xor eax,eax
1: kd> p
hprdbghv!VmxVirtualizeCurrentSystem+0x7f:
fffff807`76d3adcf 488b4c2448 mov rcx,qword ptr [rsp+48h]
1: kd> p
hprdbghv!VmxVirtualizeCurrentSystem+0xd9:
fffff807`76d3ae29 488b4c2448 mov rcx,qword ptr [rsp+48h]
1: kd> p
hprdbghv!VmxVirtualizeCurrentSystem+0xe8:
fffff807`76d3ae38 7549 jne hprdbghv!VmxVirtualizeCurrentSystem+0x133 (fffff807`76d3ae83)
1: kd> p
hprdbghv!VmxVirtualizeCurrentSystem+0x133:
fffff807`76d3ae83 33c0 xor eax,eax
1: kd> r
rax=0000000000000001 rbx=ffff9c800a302f80 rcx=ffffc787fcf84200
rdx=0000000000000000 rsi=ffff9c800a305a20 rdi=ffff9c800a300180
rip=fffff80776d3ae83 rsp=ffffac8a01e30a10 rbp=ffffac8a01e30d40
r8=ffffac8a02909090 r9=ffffac8a02909098 r10=fffff80776d29d30
r11=0000000000000000 r12=0000000000000000 r13=0000000000000000
r14=ffffac8a01e30e70 r15=0000000000000001
iopl=0 nv up ei pl nz na pe nc
cs=0010 ss=0018 ds=002b es=002b fs=0053 gs=002b efl=00000202
hprdbghv!VmxVirtualizeCurrentSystem+0x133:
fffff807`76d3ae83 33c0 xor eax,eax
1: kd> t
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), * -
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`7a1cbc90 cc int 3
0: kd> t
nt!DbgBreakPointWithStatus+0x1:
fffff807`7a1cbc91 c3 ret
0: kd> t
hprdbghv!VmxVirtualizeCurrentSystem+0x171:
fffff807`76d3aec1 488b542470 mov rdx,qword ptr [rsp+70h]
1: kd> t
hprdbghv!VmxSetupVmcs:
fffff807`76d3a520 4889542410 mov qword ptr [rsp+10h],rdx
1: kd> t
nt!KdCheckForDebugBreak+0x86b28:
fffff807`7a1e6a0c 90 nop
0: kd> t
hprdbghv!VmxSetupVmcs+0xa:
fffff807`76d3a52a 57 push rdi
1: kd> gu
Single step exception - code 80000004 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
nt!KdCheckForDebugBreak+0x86b29:
fffff807`7a1e6a0d e9f094f7ff jmp nt!KdCheckForDebugBreak+0x1e (fffff807`7a15ff02)
0: kd> t
nt!KdCheckForDebugBreak+0x1e:
fffff807`7a15ff02 4883c428 add rsp,28h
0: kd> gu
nt!KeAccumulateTicks+0x1b80d3:
fffff807`7a1fa7a3 90 nop
0: kd> gu
nt!KeClockInterruptNotify+0x98c:
fffff807`7a0441fc 488b7308 mov rsi,qword ptr [rbx+8]
0: kd> gu
fffff807`79f5d562 0f1f440000 nop dword ptr [rax+rax]
0: kd> gu
Break instruction exception - code 80000003 (first chance)
hprdbghv!AsmVmxSaveState+0x2a:
fffff807`76d28d0a cc int 3
1: kd> g
Break instruction exception - code 80000003 (first chance)
*******************************************************************************
* *
* You are seeing this message because you pressed either *
* CTRL+C (if you run console kernel debugger) or, *
* CTRL+BREAK (if you run GUI kernel debugger), *
* on your debugger machine's keyboard. *
* *
* THIS IS NOT A BUG OR A SYSTEM CRASH *
* *
* If you did not intend to break into the debugger, press the "g" key, then *
* press the "Enter" key now. This message might immediately reappear. If it *
* does, press "g" and "Enter" again. *
* *
*******************************************************************************
nt!DbgBreakPointWithStatus:
fffff807`7a1cbc90 cc int 3
1: kd> g
Single step exception - code 80000004 (first chance)
First chance exceptions are reported before any exception handling.
This exception may be expected and handled.
hprdbghv!VmxVirtualizeCurrentSystem:
fffff807`76d3ad50 48894c2408 mov qword ptr [rsp+8],rcx
0: kd> g
Break instruction exception - code 80000003 (first chance)
hprdbghv!VmxVirtualizeCurrentSystem+0x9:
fffff807`76d3ad59 cc int 3
0: kd> g
Break instruction exception - code 80000003 (first chance)
hprdbghv!AsmVmxSaveState+0x2a:
fffff807`76d28d0a cc int 3
0: kd> g
KDTARGET: Refreshing KD connection
*** Fatal System Error: 0x0000003b
(0x00000000C000001D,0xFFFFF80776D28D72,0xFFFFAC8A02908820,0x0000000000000000) -
Break instruction exception - code 80000003 (first chance)
A fatal system error has occurred.
Debugger entered on first try; Bugcheck callbacks have not been invoked.
A fatal system error has occurred.
nt!DbgBreakPointWithStatus:
fffff807`7a1cbc90 cc int 3
0: kd> g -
 I think the other core hit the breakpoint. Maybe if it's complicated to debug two cores simultaneously, you can configure your VM to have only one core.
I think the other core hit the breakpoint. Maybe if it's complicated to debug two cores simultaneously, you can configure your VM to have only one core. -
-
 Can you send the above WinDbg tracing in a txt file format? It's a little bit hard to follow it from the text message.
Can you send the above WinDbg tracing in a txt file format? It's a little bit hard to follow it from the text message. -
-
-
-
-
-
 Okay, I'll get it, the VMLAUNCH is failed.
Okay, I'll get it, the VMLAUNCH is failed. -

-
 As VMLAUNCH is failed, the entire virtualization routine will be failed.
As VMLAUNCH is failed, the entire virtualization routine will be failed. -
 Now, the question is why this VMLAUNCH is failed? After running it gives an error code. Which CPU-ish error code.
Now, the question is why this VMLAUNCH is failed? After running it gives an error code. Which CPU-ish error code. -
 The next step is putting removing all the currently breakpoint that we insert into the HyperDbg and put a breakpoint right after running the VMLAUNCH intrinsic function to read the CPU error code
The next step is putting removing all the currently breakpoint that we insert into the HyperDbg and put a breakpoint right after running the VMLAUNCH intrinsic function to read the CPU error code -
 I hope we won't conclude error code 7. 😄
I hope we won't conclude error code 7. 😄
Because it's the worst CPU error code. -
-
-
-
 Here:
Here: -
VCpu->HasLaunched = TRUE;
__vmx_vmlaunch();
//
// ******** if Vmlaunch succeed will never be here ! ********
//
//
// If failed, then indicate that current core is not currently virtualized
//
VCpu->HasLaunched = FALSE;
//
// Read error code firstly
//
__vmx_vmread(VMCS_VM_INSTRUCTION_ERROR, &ErrorCode);
LogError("Err, unable to execute VMLAUNCH, status : 0x%llx", ErrorCode); -

-
 We need to read the result of this:
We need to read the result of this:
LogError("Err, unable to execute VMLAUNCH, status : 0x%llx", ErrorCode); -
 Use DbgPrint instead of LogError. And before running hyperdbg, run the following command in windbg:
Use DbgPrint instead of LogError. And before running hyperdbg, run the following command in windbg:
eb nt!Kd_DEFAULT_Mask ff ff ff ff -
-
-
-
 🤦♂
🤦♂ -
-
 I hate this error. It generally means one or more field of hypervisor is configured incorrectly. But it won't say, what component is configured incorrectly. Which kinda weird. Because some hypervisor layout that work on older systems and newer systems shouldn't behave differently.
I hate this error. It generally means one or more field of hypervisor is configured incorrectly. But it won't say, what component is configured incorrectly. Which kinda weird. Because some hypervisor layout that work on older systems and newer systems shouldn't behave differently. -
 I didn't expect that to happen after it works in one computer. 😕
I didn't expect that to happen after it works in one computer. 😕 -
-
-
 Disabled hypervisor in host machine? How it's even possible? 🤨
Disabled hypervisor in host machine? How it's even possible? 🤨 -
 Do you mean you disabled hyper-v?
Do you mean you disabled hyper-v? -
-
 In the host machine?
In the host machine? -
-
 No, it shouldn't be because of that.
No, it shouldn't be because of that. -

-
-
-
-
-
 No, it's an Intel-ish issue with the layout of hypervisor.
No, it's an Intel-ish issue with the layout of hypervisor.
https://rayanfam.com/topics/hypervisor-from-scratch-part-5/#checking-vmcs-layoutHypervisor From Scratch – Part 5: Setting up VMCS & Running Guest CodeWe write about Windows Internals, Hypervisors, Linux, and Networks.
-
-
 These problems are really hard to find/solve. Because generally once a hypervisor works on an older/newer machine, it should also work on mid-range generations of Intel processors too. Which is kinda weird.
These problems are really hard to find/solve. Because generally once a hypervisor works on an older/newer machine, it should also work on mid-range generations of Intel processors too. Which is kinda weird. -
-
 I'll try to read the Intel manual again, to see if anything comes to my mind and will reach you again if I find anything. Meanwhile, you can try testing it on other machines.
I'll try to read the Intel manual again, to see if anything comes to my mind and will reach you again if I find anything. Meanwhile, you can try testing it on other machines. -
-
-
-
-
-
-
 Okay, let me know how it goes and sorry for that 🙏
Okay, let me know how it goes and sorry for that 🙏 -
-
-
 Hi just out of curiosity, are you the Ricardo Narvaja from crack-latinos?
Hi just out of curiosity, are you the Ricardo Narvaja from crack-latinos? -
-

-
-
-

-
-
-
-
-
 Yeah i saw that but difficult to translate.
Yeah i saw that but difficult to translate. -
-

-
- 21 June 2023 (47 messages)
-
 @ricnar The persian community is much less familiar with you and your tutorials / activities . I'm glad to see you here Ricardo.
@ricnar The persian community is much less familiar with you and your tutorials / activities . I'm glad to see you here Ricardo.
Enjoy HyperDbg. -
 As I didn't test the current version of HyperDbg (v0.3), on a Win 10 machine and everything was tested only on Win 11, I thought maybe I made some wrong configurations that leads to this error. I couldn't find a Win 10 19h1 iso (like in your case @ricnar) but HyperDbg was pretty okay on a VMware Win 10 22h2 on my 12 Gen i5-12400 machine.
As I didn't test the current version of HyperDbg (v0.3), on a Win 10 machine and everything was tested only on Win 11, I thought maybe I made some wrong configurations that leads to this error. I couldn't find a Win 10 19h1 iso (like in your case @ricnar) but HyperDbg was pretty okay on a VMware Win 10 22h2 on my 12 Gen i5-12400 machine. -
Thanks glad to see you too
-
thanks for investigating
-
Microsoft Windows and Office ISO Download Tool
https://www.heidoc.net/joomla/technology-science/microsoft/67-microsoft-windows-and-office-iso-download-toolMicrosoft Windows and Office ISO Download ToolThis new tool allows an easy and comfortable way to download genuine Microsoft Windows 7, 8.1 and 10, as well as Office 2007, 2010, 2013 and 2016 disk images (ISO) directly from Microsoft's servers.
-
-
-
-
-
 Doesn't seem to work for me.
Doesn't seem to work for me. -
 That's great, let me know what's the result when your tests finished.
That's great, let me know what's the result when your tests finished. -
-
Rufus - Create bootable USB drives the easy way
Rufus: Create bootable USB drives the easy way
-
-
-
 Joined.
Joined. -
-
-
-
-
 I test it before, it only contains the newest 22h2.
I test it before, it only contains the newest 22h2. -
 It doesn't work either
It doesn't work either -
-
-

-
-
-
-
-
 This one is okay.
This one is okay. -
 I try to download it now.
I try to download it now. -
-
You should go back to your roots, Try soft98 :D
-
Joined.
-
 Hi everyone,
Hi everyone,
Considering that this is a public group, we have taken the initiative to create an online version of the group at tg-archive.hyperdbg.org. This will ensure that the valuable contributions made by the community are preserved and easily accessible online.
If any of you have privacy concerns regarding this online archive, please kindly inform me so that we can address them appropriately.
Thank you -
 None
None -
 @ricnar I tested HyperDbg on Win 10 1909 at it works perfectly.
@ricnar I tested HyperDbg on Win 10 1909 at it works perfectly. -
-
 Seems that the issue might be related to 9 gen processors, but it's kinda weird why you encountered error.
Seems that the issue might be related to 9 gen processors, but it's kinda weird why you encountered error. -
-
-
 Did you test it in any other systems?
Did you test it in any other systems? -
-
-
-
-
 Joined.
Joined. - 22 June 2023 (1 messages)
-
 Joined.
Joined. - 24 June 2023 (55 messages)
-
 Joined.
Joined. -
 @HughEverett Hey, would you mind if I shared a the signed kernel driver here?
@HughEverett Hey, would you mind if I shared a the signed kernel driver here? -
 Signed it with my EV cert and perhaps could be of use to some people
Signed it with my EV cert and perhaps could be of use to some people -
 I'm pretty okay with sharing anything but I think it would be problematic for you. Because, as long as I know Microsoft is not interested in modifying its kernel memory by a thrid party driver and as a debugger, HyperDbg has the ability to do this. So, they will blacklist your signature and probably next time, they won't let you sign anything again.
I'm pretty okay with sharing anything but I think it would be problematic for you. Because, as long as I know Microsoft is not interested in modifying its kernel memory by a thrid party driver and as a debugger, HyperDbg has the ability to do this. So, they will blacklist your signature and probably next time, they won't let you sign anything again. -
 ah, that's a fair point
ah, that's a fair point -
 I know some people who signed HyperDbg but they use their signed version of HyperDbg privately.
I know some people who signed HyperDbg but they use their signed version of HyperDbg privately. -
 Also, while looking through hyperdbg's documentation, I've stumbled upon one area that kind of interests me, although executed in a different manner. https://docs.hyperdbg.org/using-hyperdbg/kernel-mode-debugging/examples/events/monitoring-accesses-to-structures
Also, while looking through hyperdbg's documentation, I've stumbled upon one area that kind of interests me, although executed in a different manner. https://docs.hyperdbg.org/using-hyperdbg/kernel-mode-debugging/examples/events/monitoring-accesses-to-structures
I'm analyzing a kernel-mode driver that does a lot of changes within the operating system, and I'd like to try and see what kind of memory accesses and writes to, be it in ntoskrnl or other system drivers. What would be the best way to go about this? I've considered placed an EPT-Hook on some specific functions, but it's virtualized to a certain degree. They abuse a couple stuff for hijacking exception handling of the system, etc, and wanted to see if there's perhaps more things they touch that I'm not aware ofMonitoring Accesses To StructuresFinding the writers and reader of memory
-
 The only viable idea that came to mind would be hooking the entire driver, and checking registers for a specific list of address ranges..
The only viable idea that came to mind would be hooking the entire driver, and checking registers for a specific list of address ranges.. -
 considering disabling r/w protections on system drivers would not be such a good idea..
considering disabling r/w protections on system drivers would not be such a good idea.. -
 This is exactly the topic of a new feature we're working on right now. We want to add a lot of memory-controlling events to the HyperDbg. But, it's not in a working state yet and probably takes several months to finish. But, one idea is to memory allocation of the target driver maybe that would be helpful.
This is exactly the topic of a new feature we're working on right now. We want to add a lot of memory-controlling events to the HyperDbg. But, it's not in a working state yet and probably takes several months to finish. But, one idea is to memory allocation of the target driver maybe that would be helpful. -
 When running in VMI mode, do you think the consequences of disabling r/w protection on a large .data section chunk of a driver would be a huge hinder on performance?
When running in VMI mode, do you think the consequences of disabling r/w protection on a large .data section chunk of a driver would be a huge hinder on performance? -
 I understand the overhead is already huge..
I understand the overhead is already huge.. -
 You can disable it directly by modifying the source code using this function:
You can disable it directly by modifying the source code using this function:
https://github.com/HyperDbg/HyperDbg/blob/a571781e8651998b982a9f53edf8f3d3501a6b2e/hyperdbg/hprdbghv/code/vmm/ept/Ept.c#L299
But, keep in mind that you need to handle #EPT Violations by your own as HyperDbg doesn't expect these EPT Violations.HyperDbg/hyperdbg/hprdbghv/code/vmm/ept/Ept.c at a571781e8651998b982a9f53edf8f3d3501a6b2e · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 I don't think so,
I don't think so,
I did the exact same thing in this branch by using MBEC for user-mode codes, but as I said, it's not in a working state yet but the code might be helpful:
https://github.com/HyperDbg/HyperDbg/tree/memory-introspectionGitHub - HyperDbg/HyperDbg at memory-introspectionState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 Thanks! I'll take a look once I get a bit more comfy with the tool :)
Thanks! I'll take a look once I get a bit more comfy with the tool :) -
 Hopefully HyperDbg won't start crashing my system randomly like Hyper-V (literally a bsod in every 3 minutes, not using VMs, just having the feature enabled)
Hopefully HyperDbg won't start crashing my system randomly like Hyper-V (literally a bsod in every 3 minutes, not using VMs, just having the feature enabled) -
 If you want to develop anything in HyperDbg, it's better to test HyperDbg in a VMware Workstation machine with nested-virtualization.
If you want to develop anything in HyperDbg, it's better to test HyperDbg in a VMware Workstation machine with nested-virtualization. -
 After that, you can use it in your physical machine.
After that, you can use it in your physical machine. -
 At the moment just trying to observe its capabilities, I followed some of the development throughout the years but never actually got to using it (since I only recently switched to latest Intel from AMD)
At the moment just trying to observe its capabilities, I followed some of the development throughout the years but never actually got to using it (since I only recently switched to latest Intel from AMD) -
 Also mainly for research purposes, been lurking around some virtualization related resources in the past weeks, to see how everything actually works
Also mainly for research purposes, been lurking around some virtualization related resources in the past weeks, to see how everything actually works -
 The articles on rayanfam were really great :)
The articles on rayanfam were really great :) -
 Saw the last one on hyperdbg and thought i'd take a look
Saw the last one on hyperdbg and thought i'd take a look -
 Interesting, Windows doesn't want to load it even though I just signed it..
Interesting, Windows doesn't want to load it even though I just signed it.. -

-
 Are you sure that you signed it correctly? I mean as long as I know the process of signing drivers for Windows 11 and probably Windows 10 22H2 is changed. After signing it, you have to upload it to the Microsoft portal, so they'll sign it and give a signed version of it for download. Did you upload it there?
Are you sure that you signed it correctly? I mean as long as I know the process of signing drivers for Windows 11 and probably Windows 10 22H2 is changed. After signing it, you have to upload it to the Microsoft portal, so they'll sign it and give a signed version of it for download. Did you upload it there? -
 Yep, otherwise it'd show my certificate instead of microsoft's.
Yep, otherwise it'd show my certificate instead of microsoft's. -
 It's odd, my other driver works fine.
It's odd, my other driver works fine. -
 I'll try resubmitting it I guess.
I'll try resubmitting it I guess. -
 You have to submit three drivers. One for Serial Kd, one for hyperdbg HV, and one for HyperDbg Kd.
You have to submit three drivers. One for Serial Kd, one for hyperdbg HV, and one for HyperDbg Kd. -
 + One for Hyperlog and hprdbgrev.
+ One for Hyperlog and hprdbgrev. -

-
 All of them are DLLs and drivers imported by hyperdbg.
All of them are DLLs and drivers imported by hyperdbg. -
 Oh.
Oh. -
 I only submitted the kd driver
I only submitted the kd driver -
 That's probably why, thanks.
That's probably why, thanks. -
 👍
👍 -
 Signed all of them and still the issue persists.. weird
Signed all of them and still the issue persists.. weird -
 oh.. forgot to sign the last one
oh.. forgot to sign the last one -
 😂
😂 -
 However I'm still pretty conflicted about this, sure, it's a hyper-visor assisted debugging tool, but that's not inherently bad. WinDbg runs in kernel-mode, but I assume it's because they expect the user to have test-signing and disabled PG as to not be potentially abused by malware...?
However I'm still pretty conflicted about this, sure, it's a hyper-visor assisted debugging tool, but that's not inherently bad. WinDbg runs in kernel-mode, but I assume it's because they expect the user to have test-signing and disabled PG as to not be potentially abused by malware...? -
 Probably, yes. BTW, this is the main reason of a conflict on Twitter.
Probably, yes. BTW, this is the main reason of a conflict on Twitter.
They even blacklist the Driver signature for ProcessHacker which doesn't have an arbitrary READ/WRITE. Now, you expect they let HyperDbg which has several arbitrary READ/WRITE to be signed? 😅😁
https://twitter.com/processhacker/status/1442439527235153920?s=20 -
 True enough..
True enough.. -
 Not like they sign drivers that expose arbitrary r/w and sometimes even kernel execute functionality (from um request) daily..
Not like they sign drivers that expose arbitrary r/w and sometimes even kernel execute functionality (from um request) daily.. -
 signed every image, now it works fine :)
signed every image, now it works fine :) -
 thanks for the help, Sina
thanks for the help, Sina -
 🤝
🤝 -
 Are there any scripting functions for retrieving a module base from lm?
Are there any scripting functions for retrieving a module base from lm? -
 i.e. I want to retrieve a driver's base address in a script
i.e. I want to retrieve a driver's base address in a script -
 Also, can we combine code & script actions?
Also, can we combine code & script actions? -
 What is the reason VMI mode is incompatible with !vmcall (etc) on script/custom code modes?
What is the reason VMI mode is incompatible with !vmcall (etc) on script/custom code modes? -
 Under debugger mode, is there support for Transparency towards kernel-mode drivers?
Under debugger mode, is there support for Transparency towards kernel-mode drivers? -
I'm copying a w11 machine to this pc
-
 Are there any alternatives at all for Debugger mode to use anything but COM? My motherboard literally doesn't have any serial ports.. (for remote debugging)
Are there any alternatives at all for Debugger mode to use anything but COM? My motherboard literally doesn't have any serial ports.. (for remote debugging) -
 apparently COM via pcie won't work
apparently COM via pcie won't work -
 nevermind, ordered a motherboard with one.. (and a laptop to use as the debugger)
nevermind, ordered a motherboard with one.. (and a laptop to use as the debugger) - 25 June 2023 (57 messages)
-
i tried in w11 as target and it woks
-
-
-
 for anyone not working with legacy hardware and interested in remote debugging:
for anyone not working with legacy hardware and interested in remote debugging: -
 No, 'lm' is a command, not the script function. But, if there is some Windows functions (that are HIGH_IRQL compatible), can be used as a new script function.
No, 'lm' is a command, not the script function. But, if there is some Windows functions (that are HIGH_IRQL compatible), can be used as a new script function. -
 Yes. It can be combined. You can also create several events with same conditions.
Yes. It can be combined. You can also create several events with same conditions. -
 No, it's compatible. Where did you see that? 🤨
No, it's compatible. Where did you see that? 🤨 -
 Unfortunately, no.
Unfortunately, no. -
 Can't you use a VMware nested virtualization?
Can't you use a VMware nested virtualization?
It's been a long time that I didn't test the physical COM capability of the HyperDbg, there might be some problems but sure, should be easily solvable once you have the facility to debug it. -
 Wow, that's great. 👍
Wow, that's great. 👍 -
-
-
-
 Yes, the breakpoint on READ/WRITE is done by using the '!monitor' command.
Yes, the breakpoint on READ/WRITE is done by using the '!monitor' command.
The documentation:
https://docs.hyperdbg.org/commands/extension-commands/monitor
Example:
https://docs.hyperdbg.org/using-hyperdbg/kernel-mode-debugging/examples/events/monitoring-accesses-to-structures!monitor (monitor read/write/execute to a range of memory)Description of the '!monitor' command in HyperDbg.
-
 The exact address is available at $context pseudo-register in script and in debugger:
The exact address is available at $context pseudo-register in script and in debugger:
https://docs.hyperdbg.org/commands/extension-commands/monitor#context!monitor (monitor read/write/execute to a range of memory)Description of the '!monitor' command in HyperDbg.
-
-
-
-
 The difference here with WinDbg is that break on READ/WRITE is implemented in EPT level; thus, we won't use Hardware Debug Registers for this purpose and as the result, there is no limitation on quantity or size. You can set as many monitors as you want with unlimited size.
The difference here with WinDbg is that break on READ/WRITE is implemented in EPT level; thus, we won't use Hardware Debug Registers for this purpose and as the result, there is no limitation on quantity or size. You can set as many monitors as you want with unlimited size. -
-
 Not yet. We didn't write it, but that should be hard as we released HyperDbg SDK.
Not yet. We didn't write it, but that should be hard as we released HyperDbg SDK. -
-
-
 Agree. That should be added to the to-do list.
Agree. That should be added to the to-do list. -
-
 Yes, of course.
Yes, of course.
- 03 Jun 2023 (1)
- 04 Jun 2023 (1)
- 05 Jun 2023 (1)
- 06 Jun 2023 (18)
- 08 Jun 2023 (6)
- 09 Jun 2023 (1)
- 10 Jun 2023 (1)
- 12 Jun 2023 (1)
- 13 Jun 2023 (2)
- 16 Jun 2023 (6)
- 17 Jun 2023 (3)
- 20 Jun 2023 (330)
- 21 Jun 2023 (47)
- 22 Jun 2023 (1)
- 24 Jun 2023 (55)
- 25 Jun 2023 (57)
- 26 Jun 2023 (42)
- 27 Jun 2023 (131)
- 28 Jun 2023 (70)
- 29 Jun 2023 (1)
- 30 Jun 2023 (3)