- 01 September 2023 (4 messages)
-
hi, how can I debug hyperdbgkd while debugger mode? is it able to windbg and hyperdbg attach remote kernel at the same time ?
-
 Hi,
Hi,
You can use the command 'test breakpoint off', so HyperDbg won't intercept the breakpoints anymore, thus re-inject it for other debuggers like windbg or x64dbg. -
 I also see the issue, you mentioned before, but couldn't reproduce that. 🤔
I also see the issue, you mentioned before, but couldn't reproduce that. 🤔
Can you give me a simple example of a scenario (preferably kernel-mode only) so I can reproduce it? -
I'll dm you the sample later
- 02 September 2023 (10 messages)
-
Joined.
-
now I can use windbg to debug hyperdbgkd. I want to trace KdDispatchAndPerformCommandsFromDebugger, but the problem is that it takes too long for the commands like step-into in VS community .
-
-
 hey, how did you even manage to kernel debug in visual studio, I tried many many ways but all of them unsuccessful
hey, how did you even manage to kernel debug in visual studio, I tried many many ways but all of them unsuccessful -
both hyperdbg and windbg use pipename to attach
-
 It's basically the reason why WinDbg is not a good debugger for debugging HyperDbg. Only sometimes it works and you cannot perform multiple steppings because in most of the cases after 4, 5 or more instructions it will be halted and never returns again. The reason why is because WinDbg is not designed to debug VMX-root mode routines like this.
It's basically the reason why WinDbg is not a good debugger for debugging HyperDbg. Only sometimes it works and you cannot perform multiple steppings because in most of the cases after 4, 5 or more instructions it will be halted and never returns again. The reason why is because WinDbg is not designed to debug VMX-root mode routines like this. -
 I use serial device for debugging HyperDbg, you have functions like LogInfo() which you can use them like a printf debugging style kind of debugger.
I use serial device for debugging HyperDbg, you have functions like LogInfo() which you can use them like a printf debugging style kind of debugger. -
so do you suggest that only use LogInfo to debug while developing hyperdbgkd ?
-
 I used to debug it like this up until now, and it perfectly works in all cases. There might be better innovative ways but right now, the best way that I'm known of is this.
I used to debug it like this up until now, and it perfectly works in all cases. There might be better innovative ways but right now, the best way that I'm known of is this. -
 Joined.
Joined. - 03 September 2023 (68 messages)
-
-
-
can you explain the part event_inject
-
-
-
-
-
 I didn't get what you mean. 🤔
I didn't get what you mean. 🤔
Basically, we intercept interrupts by using the Exception Bitmap in VMCS in the target guest. And injecting event which is done by using the 'event_inject' function is also done by using hypervisor facilities. -
-
-
-
-
-
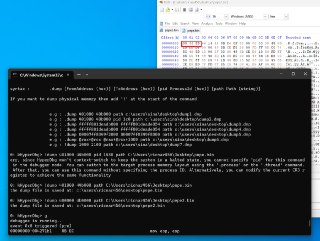
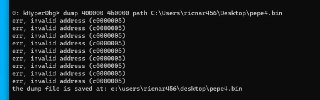
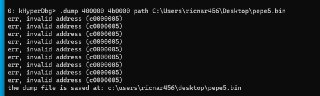
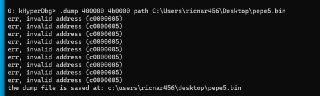
 No, you're using '!dump', the '!dump' creates the dump from physical memory
No, you're using '!dump', the '!dump' creates the dump from physical memory -
 not virtual memory
not virtual memory -
 Use the '.dump' or the 'dump' which is for virtual memory.
Use the '.dump' or the 'dump' which is for virtual memory. -
-
-
-
-
 🤨🤨
🤨🤨 -
-
-
-
-
-
-
-
-
-
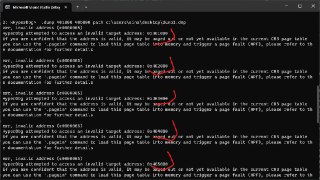
 yes, but all addresses should be available in the memory (not paged-out). (The exact limitation that we had, so we made the '.pagein' to solve it).
yes, but all addresses should be available in the memory (not paged-out). (The exact limitation that we had, so we made the '.pagein' to solve it). -
-
-
-
 🤔
🤔 -
 The problem here is, the 'CR2' for page-fault is only one register in Intel processors which mean we can only inject one page address for the page-fault.
The problem here is, the 'CR2' for page-fault is only one register in Intel processors which mean we can only inject one page address for the page-fault. -
-
-
-
-
-
 Yes, but it's a little bit complicated as in the current design the scripts are evaluated in the kernel-mode. Probably we need to re-write the script engine to support these kinds of scenarios.
Yes, but it's a little bit complicated as in the current design the scripts are evaluated in the kernel-mode. Probably we need to re-write the script engine to support these kinds of scenarios. -
-
-
-

-

-

-
 @xmaple555 Here's the result. I couldn't reproduce the error that you mentioned.
@xmaple555 Here's the result. I couldn't reproduce the error that you mentioned. -
what will happen use t after eb ?
-

-
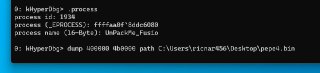
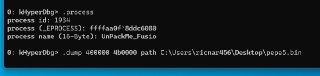
I'll make an issue later . the sample I have problem is packed by themida
-
 Okay 👍
Okay 👍 -
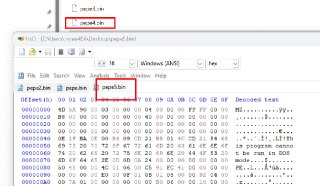
 @ricnar, one thing that I was thinking about it is why we need dumps from the PE modules? Is it because we want to reverse it based on extracted memory contents? or is it even possible to reconstruct the unpacked 'exe' file from this file? 🤔🧐
@ricnar, one thing that I was thinking about it is why we need dumps from the PE modules? Is it because we want to reverse it based on extracted memory contents? or is it even possible to reconstruct the unpacked 'exe' file from this file? 🤔🧐 -
-
-
-
-
-
 How do you reconstruct? Is there any special method that I'm not known of?
How do you reconstruct? Is there any special method that I'm not known of? -
 I try to find a solution to fix it.
I try to find a solution to fix it. -
-
-
-
 maybe we could write a custom assembly code that accesses the entire block, patch @RIP registers and once Windows brings the entire pages in the memory, we could use dump 🤔
maybe we could write a custom assembly code that accesses the entire block, patch @RIP registers and once Windows brings the entire pages in the memory, we could use dump 🤔 -
 Like what?
Like what? -
-
- 04 September 2023 (8 messages)
-
 🎉 Exciting news! The HyperDbg course is now available. 🚀
🎉 Exciting news! The HyperDbg course is now available. 🚀
This tutorial will guide you through the initial steps of using HyperDbg, covering essential concepts, principles, and debugging functionalities as well as numerous reverse engineering methods achievable by using HyperDbg, along with practical and real-world examples.
Check it out here: 🔗 https://ost2.fyi/Dbg3301Debuggers 3301: HyperDbgThis class teaches you how to use HyperDbg, a virtualization-based debugger.
-
 It's a ~16 hours course which shows the potential of using HyperDbg for reverse engineering alongside a lot of cool hypervisor-based reverse engineering tricks.
It's a ~16 hours course which shows the potential of using HyperDbg for reverse engineering alongside a lot of cool hypervisor-based reverse engineering tricks. -
-
hi, does anyone know how to show the message from LogInfo in hprdbgkd to the debuggee ? UseImmediateMessagingByDefaultOnEvents is true and the thread of ReadIrpBasedBuffer
is running. -
 Hi,
Hi,
What do you mean? 🤨
By default, once you connect HyperDbg to either the debugger mode or the VMI mode, the messages of LogInfo will be shown. -
 Like, you don't need to do anything for it, it shows the messages of this function automatically.
Like, you don't need to do anything for it, it shows the messages of this function automatically. -
my bad, I just realized that I always used the old sys file
-
Joined.
- 06 September 2023 (1 messages)
-
Joined.
- 07 September 2023 (12 messages)
-
 mkt The artifacts are now enabled in the 'dev' branch.
mkt The artifacts are now enabled in the 'dev' branch. -
@HughEverett Long time no see, can hyperdbg analyze vmprotect or themida, so as to deobfuscate and restore the original code.Very little information is available using vt-x analysis.
-

-

-

-

-
What are the now latest anti-obfuscation techniques.
-
deobfuscation
-
 vtil if you want to devirtualize
vtil if you want to devirtualize -
Someone said on reddit that vtil has many shortcomings and cannot perfectly solve some deobfuscation problems.
-
So it also is the reason why the author chooses not to update.
-
 hey with hyperdbg possible make read/write communication ?
hey with hyperdbg possible make read/write communication ? - 08 September 2023 (21 messages)
-
 what kind of communication? network communication?
what kind of communication? network communication? -
 Joined.
Joined. -
 He probably meant that he needs a virtual memory read/write primitives that he can call within the usermode part of his p2c
He probably meant that he needs a virtual memory read/write primitives that he can call within the usermode part of his p2c -

-
 BTW, whatever form he wants to communicate is possible. Either sharing a virtual memory (which can be done by using the '!monitor') or user/kernel communication (using the '!syscall'), PMIO or MMIO communication (using the '!ioin' and the '!ioout'), and even interrupt based communication using the '!interrupt'.
BTW, whatever form he wants to communicate is possible. Either sharing a virtual memory (which can be done by using the '!monitor') or user/kernel communication (using the '!syscall'), PMIO or MMIO communication (using the '!ioin' and the '!ioout'), and even interrupt based communication using the '!interrupt'. -
 I just wanted to know the exact form to conduct him to the corresponding examples. 😅
I just wanted to know the exact form to conduct him to the corresponding examples. 😅 -

-
@HughEverett Is this possible for binary deobfuscator using hyperdbg? Or there is no idea.
-
 ^
^ -
Can it be used as a tracker?
-
 As @invlpg mentioned, HyperDbg makes you able to debug. You might use HyperDbg's functionalities to perform your deobfuscation logic but it's not designed to directly deobfuscate anything.
As @invlpg mentioned, HyperDbg makes you able to debug. You might use HyperDbg's functionalities to perform your deobfuscation logic but it's not designed to directly deobfuscate anything. -
 If you mean tracker of (let say) memory, yes. It can be used for tracking it.
If you mean tracker of (let say) memory, yes. It can be used for tracking it. -
☺️
-
 But obviously, only tracking the memory is not enough for deobfuscating binaries 😵💫
But obviously, only tracking the memory is not enough for deobfuscating binaries 😵💫 -
If it is possible to record the instructions that are executing rip of the current process
-
i also need to what knowledge?
-
If can record each specified instruction, then it is feasible.
-
 I don't have expertise in this area, maybe other members here can help.
I don't have expertise in this area, maybe other members here can help. -
 You can record the instructions by using the "!monitor"'s 'x' attribute, but it's not practical (slow) if you want to do it for millions of instructions.
You can record the instructions by using the "!monitor"'s 'x' attribute, but it's not practical (slow) if you want to do it for millions of instructions. -
But it's fine. Thank you very much. ^ . ^
-
- 09 September 2023 (16 messages)
-
-
-
-
-
-
-
-
-
 Sure. I will add it tonight.
Sure. I will add it tonight. -
-
 Done! Please check the latest commit in the 'dev' branch.
Done! Please check the latest commit in the 'dev' branch. -

-
-
 The documentation is updated and following functions are now added:
The documentation is updated and following functions are now added:
- event_inject (https://docs.hyperdbg.org/commands/scripting-language/functions/events/event_inject)
- event_inject_error_code (https://docs.hyperdbg.org/commands/scripting-language/functions/events/event_inject_error_code)
and this the documentation for the '.dump' and the '!dump' commands:
- .dump (https://docs.hyperdbg.org/commands/meta-commands/.dump)
- !dump (https://docs.hyperdbg.org/commands/extension-commands/dump)
cc @ricnarevent_injectDescription of 'event_inject' function in HyperDbg Scripts
-
 and this is the document for the 'gu' command:
and this is the document for the 'gu' command:
https://docs.hyperdbg.org/commands/debugging-commands/gu
cc @xmaple555gu (step-out or go up)Description of the 'gu' command in HyperDbg.
-
- 10 September 2023 (1 messages)
-
Joined.
- 11 September 2023 (4 messages)
-
 Joined.
Joined. -
 Joined.
Joined. -
 Joined.
Joined. -

- 12 September 2023 (63 messages)
-
@HughEverett Hello, last week, I asked a question about deobfuscation in the group,One of my friends in the group answered my question and gave his solution, also using vt-x technology for de-obfuscation. Later I saw his open source project and gave his advice.All the debuggers on the market today (e.g. ida pro x64dbg, etc.) have sdk capabilities. I think hyperdbg should also have sdk capabilities.It is more convenient for them to prevent repeated manufacturing of wheels.Similar projects cannot be compared to hyperdbg because hyperdbg is superior.
-
 HyperDbg already has a SDK (from v0.2).
HyperDbg already has a SDK (from v0.2).
Here is a link to examples:
https://github.com/HyperDbg/HyperDbg/tree/rev-machine/hyperdbg/include/SDK/ExamplesHyperDbg/hyperdbg/include/SDK/Examples at rev-machine · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 It's not yet well-documented but as it's open-source, it's easy to understand.
It's not yet well-documented but as it's open-source, it's easy to understand. -
 I try to document everything once I find free time.
I try to document everything once I find free time. -
Thank you, today I find a warehouse, https://github.com/tklengyel/drakvuf, look at their ideas very well, can draw lessons from?GitHub - tklengyel/drakvuf: DRAKVUF Black-box Binary Analysis
DRAKVUF Black-box Binary Analysis. Contribute to tklengyel/drakvuf development by creating an account on GitHub.
-
They have a video demo on their website that you can check out
-
 Yes, drakvuf is great project. There are so many cool ideas we'd love to bring to life with HyperDbg. The only catch is that we're a bit short on time and developers. We're really hoping to see more folks from the community jump in and help us design and implement these features for HyperDbg.
Yes, drakvuf is great project. There are so many cool ideas we'd love to bring to life with HyperDbg. The only catch is that we're a bit short on time and developers. We're really hoping to see more folks from the community jump in and help us design and implement these features for HyperDbg. -
If the project is perfect and meets the needs of the majority of developers, some people will not reinvent the wheel, and the project will be kept active and more people will be involved.
-
 bro sina is currently one man army, he’s doing his higher education while developing hyperdbg and some other projects. So show some respect. He wants to make it perfect, he just doesn’t have the time, he works until 4,5 am each day as I know
bro sina is currently one man army, he’s doing his higher education while developing hyperdbg and some other projects. So show some respect. He wants to make it perfect, he just doesn’t have the time, he works until 4,5 am each day as I know -
I have a look and it doesn't seem possible to add this project to hyperdbg because they are using open source projects xen and qemu which don't follow the same principles as hyperdbg implementation.hyperdbg is placed in the guest system, drakvuf is outside the guest system, and drakvuf has higher concealment for malicious programs.So, the idea is right for hyperdbg, but the hyperdbg implementation is wrong.
-
Therefore, in order to avoid overworking yourself, we should think about how we can reduce the task and make the project better.
-
And staying up late for a long time is not good for your body, the symptoms will have spleen and stomach disorders, hypertension and other symptoms. So you need to pay attention.
-
 Yeah no worries, Tony is a little bit exaggerating 😅
Yeah no worries, Tony is a little bit exaggerating 😅 -
 Of course there are plenty of people here helping in the development of HyperDbg, I'm not the only developer.
Of course there are plenty of people here helping in the development of HyperDbg, I'm not the only developer. -
 But sure, new developers are always welcome to join.
But sure, new developers are always welcome to join. -
These are chronic diseases, long-term will indeed have an impact on the body, look at their tongue, tongue coating white is sick, on the contrary, the body is healthy
-
I didn't mean anything other than to make the project better, and I've committed code before. Are there any good ideas to change that.
-
 Do you need some ideas to implement in HyperDbg?
Do you need some ideas to implement in HyperDbg? -
Yes, but not at the moment
-
I didn't come up with good ideas
-
 There are plenty of ideas.
There are plenty of ideas.
But, one of the things that are really needed right now is supporting 'kdnet'. The source code for 'kdnet' is available in Windows SDK and the license allows us to use it. Maybe if you can take a look at it and use it on a sample project and send/receive data using it, we could add it to HyperDbg. This will be a huge contribution at the moment. -
I need to complete my deobfuscation task, but this is also a big pit.
-
From my point of view, I need some time to complete this task, I really sorry about hyperdbg.
-
At some point I will think about how to incorporate qemu functionality into hyperdbg, current I have no good idea.
-
 This one is also a nice idea. Using qemu or any other emulator we could enhance HyperDbg core.
This one is also a nice idea. Using qemu or any other emulator we could enhance HyperDbg core. -
yeah
-
If hyperdbg can replace xen hypervisor, I believe we can.
-
 For example, the current implementation of the '!monitor' command uses Monitor Trap Flag (MTF) to restore the state to the previous state. If we have an emulator there we could eliminate the MTF and by this we can gain 2x speed up as we only one VM-exit happens and the second VM-exit is eliminated.
For example, the current implementation of the '!monitor' command uses Monitor Trap Flag (MTF) to restore the state to the previous state. If we have an emulator there we could eliminate the MTF and by this we can gain 2x speed up as we only one VM-exit happens and the second VM-exit is eliminated. -
I think we should think about it carefully.
-
It also brings in more developers.
-
 yeah, in case of the emulator it should be VMX-mode Compatible (or simply written in C) without any special API call or weird memory allocations.
yeah, in case of the emulator it should be VMX-mode Compatible (or simply written in C) without any special API call or weird memory allocations. -
The key point is how can qemu be combined with hyperdbg to make both of them more useful.
-
Some concepts seem to be different between qemu and vt-x
-
 Yeah, I see some of the code in KVM that uses Qemu-based emulators to enhance and accelerate the execution IOMMU instructions.
Yeah, I see some of the code in KVM that uses Qemu-based emulators to enhance and accelerate the execution IOMMU instructions.
https://android.googlesource.com/kernel/msm/+/android-wear-5.1.1_r0.6/arch/x86/kvm/emulate.c?autodive=0%2F%2F%2F%2F%2F%2F%2F%2F%2F#4567 -
So, do you have any good ideas for hyperdbg and qemu?
-
 Yes, as I said we can enhance many feature if we have the capability of emulating instruction in VMX-root mode.
Yes, as I said we can enhance many feature if we have the capability of emulating instruction in VMX-root mode. -
 One improvement idea would be this.
One improvement idea would be this. -
 It also makes us able to do a lot of other improvements in PMIO and MMIO emulations making endless possibilities.
It also makes us able to do a lot of other improvements in PMIO and MMIO emulations making endless possibilities. -
qemu might not be very compatible with windows,What I mean is that if you change either side, it will affect the code, and if great modification hyperdbg, it will require your consent.
-
intel/haxm is required to run qemu on windows.
-
 I think what we need right now is the codes of qemu that perform emulation for certain instructions. Maybe the bochs project can help us too.
I think what we need right now is the codes of qemu that perform emulation for certain instructions. Maybe the bochs project can help us too.
https://github.com/bochs-emu/Bochs
The way that they used Qemu in KVM is for implementing certain Intel instructions in C. It doesn't need to be compatible with Windows, we only need their Instructions implementations which is an Intel (more specifically x86) dependent.GitHub - bochs-emu/Bochs: Bochs - Cross Platform x86 Emulator ProjectBochs - Cross Platform x86 Emulator Project. Contribute to bochs-emu/Bochs development by creating an account on GitHub.
-
 This is the way that I can think of using Qemu in HyperDbg. Maybe other usages can be also applied that I'm not yet known of.
This is the way that I can think of using Qemu in HyperDbg. Maybe other usages can be also applied that I'm not yet known of. -
 KVM is truly a masterpiece. 👌
KVM is truly a masterpiece. 👌 -
Yes,kvm is more mature, now it is mainly to understand the project structure of qemu,kvm or xen and drakvuf, analyze the code. How to do the docking is more appropriate
-
Less important features for now, can we put them on hold.
-
For vt-x, some programs do have the ability to check that vt-x is on, so we're going to avoid those.
-
 you mean anti-hypervisor methods?
you mean anti-hypervisor methods? -
I mean for example drakvuf with the idea that any program should not detect anomalous vt-x drivers
-
 yes, we also made some efforts for hiding HyperDbg but sure that's not enough. You can read about some of them here: https://research.hyperdbg.org/debugger/transparency.html
yes, we also made some efforts for hiding HyperDbg but sure that's not enough. You can read about some of them here: https://research.hyperdbg.org/debugger/transparency.html -
Even if turned on,They can't be hidden. Some detect these
-
 Yes, there are plenty of ways that reveal the presence of a hypervisor.
Yes, there are plenty of ways that reveal the presence of a hypervisor. -
 But most of them can be mitigated in HyperDbg.
But most of them can be mitigated in HyperDbg. -
 Which would be an enhancement for the future versions.
Which would be an enhancement for the future versions. -
 like how? 🤔
like how? 🤔 -
I think hiding works better if you handle this at the qemu level, not at the guest os, which is why the reverse engineer uses qemu.
-
 I don't have any idea how handling things in qemu-level can be helpful mitigating these caveats. Do you know any special use case for it? 🤔
I don't have any idea how handling things in qemu-level can be helpful mitigating these caveats. Do you know any special use case for it? 🤔 -
Because if a driver is loaded inside the system, it is already exposed, and a malicious program can always obtain the program in various ways to reverse analyze it anyway.
-
 I think the solution to these kind of problems is better to be handled at EPT-level leveraging a Type1-like hypervisor memory in which the VMM codes (drivers) are hidden behind the EPT.
I think the solution to these kind of problems is better to be handled at EPT-level leveraging a Type1-like hypervisor memory in which the VMM codes (drivers) are hidden behind the EPT. -
Yes, but in some developing countries, r3 can also detect r-1.
-
 Yes, but detecting a hypervisor is not a big deal these days. Mainly because Hyper-V's VBS and HVCI are now enabled by default in Win 11.
Yes, but detecting a hypervisor is not a big deal these days. Mainly because Hyper-V's VBS and HVCI are now enabled by default in Win 11. -
What you said is only a small part, for other malicious programs, when detected, the consequences can be imagined.
-
This is where projects like drakvuf cause for emergence.
-
 Joined.
Joined. - 13 September 2023 (1 messages)
-
 Joined.
Joined. - 14 September 2023 (5 messages)
-
Hi,I have a question about VPID and TLB. When VPID is enabled, when there is an instruction to modify cr3, we manually flush guest TLB entries in the HvHandleControlRegisterAccess function. But by default we do not intercept access to cr3 because of IA32_VMX_BASIC. Does this mean that a Mov to CR3 instruction will automatically flush the TLB, but when we intercept an instruction to modify cr3, we put cr3 into VMCS and then execute VMRESUME, which will not automatically flush the TLB and we must manually execute INVVPID to flush TLB?
-
 Hi,
Hi,
Yes, you're right. By default MOV to CR3 flushes the TLB but once you activate VPIDs, you have to manually invalidate it. -
ok thanks
-
 Joined.
Joined. -
 @Sina (don't want to actually tag u) i love you, thanks for this amazing project.
@Sina (don't want to actually tag u) i love you, thanks for this amazing project. - 15 September 2023 (5 messages)
-

-
 Thank you ☺️
Thank you ☺️
As I said before, it's not just me, plenty of my friends and community members helped in this project. -
 @ricnar
@ricnar
My friend @mammadataei is redesigning the website of HyperDbg. Are you okay that he put a link (a reference) to your videos on the main website?
It would be like this:
https://hyperdbg-48pxfwan3-hyperdbg.vercel.app/tutorials -
-
- 16 September 2023 (9 messages)
-

-

-
 @xmaple555
@xmaple555
We automatically change the grammar file (for adding "strcmp").
First, you should add the function into this file:
https://github.com/HyperDbg/HyperDbg/blob/master/hyperdbg/script-engine/python/Grammar.txt
And after that, you should run this python script:
https://github.com/HyperDbg/HyperDbg/blob/master/hyperdbg/script-engine/python/generator.py
It will automatically create the constant values needed for the script engine.
BTW, I fixed it now, and pushed it into the 'dev' branch but please consider this for the future. 🙏HyperDbg/hyperdbg/script-engine/python/Grammar.txt at master · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 Now, that you added this function, once you have free time, please add the "wcscmp" too. As most of the strings in the Windows kernel are in wide char string format, it would be best if HyperDbg supported it too. @xmaple555
Now, that you added this function, once you have free time, please add the "wcscmp" too. As most of the strings in the Windows kernel are in wide char string format, it would be best if HyperDbg supported it too. @xmaple555 -
 and even the 'memcmp' and other possible cstring functions might be helpful as well.
and even the 'memcmp' and other possible cstring functions might be helpful as well.
https://cplusplus.com/reference/cstring/memcmp/ -
thank for the information, I will consider it next time
-
 Hy , i was running codespell on hyperdbg source and got tons of typo , will you accept such pr's to correct them?
Hy , i was running codespell on hyperdbg source and got tons of typo , will you accept such pr's to correct them? -
 Sure. It would be best if you can push it into the 'dev' branch (not 'master' branch) to avoid possible git conflicts. 🙏
Sure. It would be best if you can push it into the 'dev' branch (not 'master' branch) to avoid possible git conflicts. 🙏 -

- 19 September 2023 (44 messages)
-
-
I got the problem since the commit https://github.com/HyperDbg/HyperDbg/commit/bab42a6623fa6370c0449dad89d2888c74da059dfix conflicts of rev branch · HyperDbg/HyperDbg@bab42a6
State-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
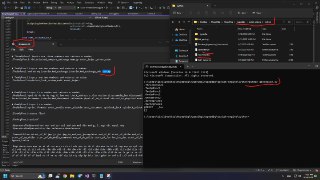
 Are "hprdbghv.sys" and "hprdbgkd.sys" correctly build?
Are "hprdbghv.sys" and "hprdbgkd.sys" correctly build? -
 Can 'git pull' to the latest commit in the 'dev' branch?
Can 'git pull' to the latest commit in the 'dev' branch? -
this is the latest dev.
-
 ؟
؟ -
 Are these files there?
Are these files there? -
yes
-
 🤨🤔
🤨🤔 -

-
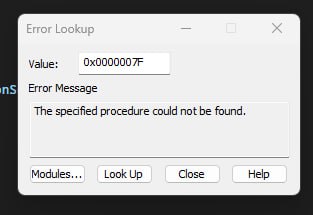
this failed to start the service hprdbgkd
-
 Doesn't make sense, I didn't do anything special since the previous commit.
Doesn't make sense, I didn't do anything special since the previous commit. -
yes I know the error, and I have tried to google it
-
-
I guess the problem is from the two commits
-
 I don't think so, because the later commits fixed these problems
I don't think so, because the later commits fixed these problems -

-
 I suspect maybe you previously loaded a driver which is not yet unloaded correctly
I suspect maybe you previously loaded a driver which is not yet unloaded correctly -
 and that might be problematic? Did you load anything manually? like using OSR Driver Loader?
and that might be problematic? Did you load anything manually? like using OSR Driver Loader? -
 🤔
🤔 -
but It works fine for me on the commit add strcmp into the grammar file
-
 I am in the latest 'dev' branch.
I am in the latest 'dev' branch. -
 Can you remove your local files and clone the project again?
Can you remove your local files and clone the project again? -
I have tried it
-
 It's weird. 🧐🤔
It's weird. 🧐🤔 -
 Let me try github artifacts: https://github.com/HyperDbg/HyperDbg/actions/runs/6221482653add mode command · HyperDbg/HyperDbg@78ca118
Let me try github artifacts: https://github.com/HyperDbg/HyperDbg/actions/runs/6221482653add mode command · HyperDbg/HyperDbg@78ca118State-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
maybe hyperdbg.sln changed ?
-
 GitHub artifact works fine.
GitHub artifact works fine. -
 It might be changed by file changes but I didn't change anything special since that commit.
It might be changed by file changes but I didn't change anything special since that commit. -
 And if you got the latest commit, it should be fine.
And if you got the latest commit, it should be fine. -
-
maybe the differential OS ?
-
 I don't think so. Let me check it on Win 10.
I don't think so. Let me check it on Win 10. -
-
 Did you get the same error on both the "debug" and the "release" version?
Did you get the same error on both the "debug" and the "release" version? -
-
yes
-
 @xmaple555 I test it on a Win 10 VM and it worked perfectly fine. Are you sure that you didn't made any special changes in your VM? (e.g., like disabling Nested-virtualization)
@xmaple555 I test it on a Win 10 VM and it worked perfectly fine. Are you sure that you didn't made any special changes in your VM? (e.g., like disabling Nested-virtualization) -
 Can you also test it with github-built artifacts?
Can you also test it with github-built artifacts?
https://github.com/HyperDbg/HyperDbg/actions/runs/6221482653add mode command · HyperDbg/HyperDbg@78ca118State-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
Joined.
-
it looks like you didn't turn off driver signature verification or The hyperdbg project was not compiled correctly.
-
@HughEverett it works fine on WIN 11
-
not really sure what I had done on WIN 10 🤔
-
- 20 September 2023 (2 messages)
-
 Joined.
Joined. -
 Joined.
Joined. - 22 September 2023 (1 messages)
-

- 23 September 2023 (6 messages)
-

-

-
 Do you mean the page-table attributes?
Do you mean the page-table attributes? -
 yes
yes -
 You can use the '!pte' command:
You can use the '!pte' command:
https://docs.hyperdbg.org/commands/extension-commands/pte!pte (display page-level address and entries)Description of the '!pte' command in HyperDbg.
-
 ah i remember this command.
ah i remember this command.
i'm just now seeing that it also gives you the attributes. thanks! - 24 September 2023 (17 messages)
-
Joined.
-
@HughEverett Observing drakvuf for a few days found that the idea is very good, but the underlying infrastructure is very bad, not recommended to use, or concentrate on vt-x related projects
-
For malicious programs to find vt-x drivers, it should be possible to find the key points through static or dynamic combination.
-
Joined.
-
 What else do you suggest other than vt-x? Direct hooking?
What else do you suggest other than vt-x? Direct hooking? -
At present, direct hook, there is not much manpower and material resources to repair.
-
The vt-x seems like a time - and labor-saving solution,However, they have all the versions fixed and it is difficult to update iterations,They try to keep the same version, so it's hard to iterate,
-
The underlying libvmi is very low active and poorly compatible
-
For now, the best practice is to do static analysis first and then hook with vt-x
-
@HughEverett Hi,I noticed that the implementation principle of !epthook is to allocate a new page, then unsets the Read and Write bits of that page but sets the Execute bit, and change the physical address of that entry to the new location.Then if someone tries to Read or Write on that virtual address, we bring the original physical address back to the page entry and set both Read and Write bits of that page but unset the Execute bit.
But when the page we want to hook has an instruction to read its own page, For example, mov rcx, [rip], can !epthook work well? -
 Hi,
Hi,
Nice catch. I never thought about it though it never happens to HyperDbg as this sentence doesn't imply how !epthook is implemented. I mean this sentence:
> we bring the original physical address back to the page entry and set both Read and Write bits of that page but unset the Execute bit.
The entry that will be restored has the full permission (Read/Write/Exec) + plus we set MTF to restore everything after executing one instruction. -
Yes, I noticed that the entry that will be restored to OriginalEntry, and OriginalEntry has full permissions, which solves the problem of the instruction reading itself. But it seems to introduce another problem. We give a page complete permissions, and then we set MTF to execute one instruction in this Core. However, because all Cores use the same EptPageTable, another Core may execute in the page without hook at this time.
-
 This problem is also solved. 🙂
This problem is also solved. 🙂 -
 Each core uses its own EPTP instead of a single memory layout design.
Each core uses its own EPTP instead of a single memory layout design. -
 Check the latest commits in the 'dev' branch.
Check the latest commits in the 'dev' branch. -
That's great
-

- 25 September 2023 (3 messages)
-
Joined.
-
-
 HyperDbg v0.6-beta is released!
HyperDbg v0.6-beta is released!
Check out: https://github.com/HyperDbg/HyperDbg/releases/tag/v0.6.0-beta
HyperDbg's memory model has undergone a significant change, transitioning to a multiple-EPTP model. This change has effectively resolved potential raised conditions. Because this was a fundamental design change, we decided to release a 'beta' version, which is mainly released for testing purposes, if you've ever occurred to have an error, please report it on GitHub issues.
Added
event_inject(InterruptionType, Vector) function in script engine
event_inject_error_code(InterruptionType, Vector, ErrorCode) function in script engine
.dump - command is added to the debugger to dump the virtual memory into a file
!dump - command is added to the debugger to dump the physical memory into a file
gu - command is added to the debugger to step-out or go up instructions thanks to @xmaple555
Changed
HyperDbg now switched to a multiple EPTP memory model, and each core has its own EPT table
Building mtrr map by adding smrr, fixed ranges, and default memory type is fixed (#255) thanks to @Air14
The problem of removing multiple EPT hooks on a single address is fixed
The problem of not intercepting the step-over command 'p' when executed in different cores is fixed
HyperDbg now checks for the validity of physical addresses based on CPUID.80000008H:EAX[7:0]'s physical address widthRelease v0.6.0-beta · HyperDbg/HyperDbgHyperDbg v0.6-beta is released! If you’re enjoying HyperDbg, don’t forget to give a star 🌟 on GitHub! Please visit Build & Install to configure the environment for running HyperDbg. Check out t...
- 27 September 2023 (1 messages)
-

- 28 September 2023 (7 messages)
-
Joined.
-
hi everybody,how to use it with x64dbg?
-
 Hi,
Hi,
The full support of x64dbg (and possibly other debuggers) is not yet added to the HyperDbg, though it's on top of the to-do list and will be added hopefully in v0.7 or v0.8 but right now you can use some feature and it more or less make it possible to support other debuggers, e.g., by default HyperDbg intercepts all breakpoints as it's a hypervisor-level debugger, thus, other debuggers won't get a chance to handle the breakpoints but using the 'test breakpoint off' you can tell HyperDbg not to handle breakpoints and re-inject #BPs to the Windows (and thus x64dbg).
https://docs.hyperdbg.org/commands/debugging-commands/test#parameterstest (test functionalities)Description of the 'test' command in HyperDbg.
-
 Other than that, HyperDbg v0.6 supports event (interrupts/exceptions/faults) injection which brings thousands of possible scenarios in which you can pass or not pass events to the kernel-mode or user-mode debugger. But it's a little bit tricky to use.
Other than that, HyperDbg v0.6 supports event (interrupts/exceptions/faults) injection which brings thousands of possible scenarios in which you can pass or not pass events to the kernel-mode or user-mode debugger. But it's a little bit tricky to use.
Please check,
https://docs.hyperdbg.org/commands/scripting-language/functions/events/event_injectevent_injectDescription of 'event_inject' function in HyperDbg Scripts
-
If you need help, I can help you for free. I hope that the dbg plug-in will appear soon.
-
 Do you want to help in adding the support to x64dbg? or generally helping in the development?
Do you want to help in adding the support to x64dbg? or generally helping in the development? -
 I think I have to add support for x64dbg myself because it's likely a one-minute task to re-inject #DBs (along with #BPs) into the user-mode or kernel-mode debugger. However, the challenge is that it may potentially disrupt other features of HyperDbg that rely on these events. Therefore, I need to have a comprehensive test to ensure that passing #DBs to the guest doesn't break anything. For example, commands like !epthook also utilize #BPs. If we re-inject everything without considering these internal usages, we might break other HyperDbg commands.
I think I have to add support for x64dbg myself because it's likely a one-minute task to re-inject #DBs (along with #BPs) into the user-mode or kernel-mode debugger. However, the challenge is that it may potentially disrupt other features of HyperDbg that rely on these events. Therefore, I need to have a comprehensive test to ensure that passing #DBs to the guest doesn't break anything. For example, commands like !epthook also utilize #BPs. If we re-inject everything without considering these internal usages, we might break other HyperDbg commands. - 29 September 2023 (2 messages)
-
 new bee
new bee -
 hyperdbg yyds
hyperdbg yyds - 30 September 2023 (4 messages)
-
Joined.
-

-
 Joined.
Joined. -
 Joined.
Joined.
- 01 Sep 2023 (4)
- 02 Sep 2023 (10)
- 03 Sep 2023 (68)
- 04 Sep 2023 (8)
- 06 Sep 2023 (1)
- 07 Sep 2023 (12)
- 08 Sep 2023 (21)
- 09 Sep 2023 (16)
- 10 Sep 2023 (1)
- 11 Sep 2023 (4)
- 12 Sep 2023 (63)
- 13 Sep 2023 (1)
- 14 Sep 2023 (5)
- 15 Sep 2023 (5)
- 16 Sep 2023 (9)
- 19 Sep 2023 (44)
- 20 Sep 2023 (2)
- 22 Sep 2023 (1)
- 23 Sep 2023 (6)
- 24 Sep 2023 (17)
- 25 Sep 2023 (3)
- 27 Sep 2023 (1)
- 28 Sep 2023 (7)
- 29 Sep 2023 (2)
- 30 Sep 2023 (4)