- 01 April 2025 (15 messages)
-
 Joined.
Joined. -
 Yeah, the current implementation is also not perfect, but it just works. At the time when I implemented this, we didn't have Zydis in our kernel codes. Now that we also have Zydis in the kernel, we could reimplement it even better.
Yeah, the current implementation is also not perfect, but it just works. At the time when I implemented this, we didn't have Zydis in our kernel codes. Now that we also have Zydis in the kernel, we could reimplement it even better. -
 Fun fact about windows virtual unwinding machine btw: they do have virtual opcodes for function prolog reconstruction. But they don’t have such opcodes for epilogue, so they literally disassemble function epilogue if they need to unwind the stack on rip located in the function epilogue. This also defies the whole purpose of this virtual unwinding machine which was supposed to be machine independent.
Fun fact about windows virtual unwinding machine btw: they do have virtual opcodes for function prolog reconstruction. But they don’t have such opcodes for epilogue, so they literally disassemble function epilogue if they need to unwind the stack on rip located in the function epilogue. This also defies the whole purpose of this virtual unwinding machine which was supposed to be machine independent. -
 😅😅
😅😅 -
well it looks like stack walk is a headache really but i will need it in my project
-
most edr
-
now use the call stack analysis to catch malicious patterns (example : direct syscalls etc)
-
Btw procmon really implement a very good stack dump analysis example but it's not open slurce😢😂
-
Thanks for this good example I will try to get an idea from it
-
 Well it just uses dbghelp library
Well it just uses dbghelp library -
 StackWalk function (dbghelp.h) - Win32 apps
StackWalk function (dbghelp.h) - Win32 appsObtains a stack trace. (StackWalk)
-
Unfortunately we cannot take advantage of this library .. since from what I have read in hyperdvg doc.. the parsing of the stack frames happened in vmx root mode
-
 I was just pointing out it is not implemented in procmon itself
I was just pointing out it is not implemented in procmon itself -
Yes bro got your idea ^^
-
Let's see what we can do with this nightmare xd
- 02 April 2025 (2 messages)
-
@HughEverett bro
-
Have you test before the effect of excessive I/O operation on the behavior of hyperdbg
- 03 April 2025 (22 messages)
-
@HughEverett brother i was reading intel manuel
-
i think this will solve the issue of extensive vm-exit due to Access/dirty bits access by the CPU
-
The Intel 64 architecture supports accessed and dirty flags in ordinary paging-structure entries (see Section
4.8). Some processors also support corresponding flags in EPT paging-structure entries. Software should read the
VMX capability MSR IA32_VMX_EPT_VPID_CAP (see Appendix A.10) to determine whether the processor supports
this feature.
Software can enable accessed and dirty flags for EPT using bit 6 of the extended-page-table pointer (EPTP), a VM execution control field (see Table 25-9 in Section 25.6.11). If this bit is 1, the processor will set the accessed and
dirty flags for EPT as described below. In addition, setting this flag causes processor accesses to guest paging structure entries to be treated as writes (see below and Section 29.3.3.2). -
i will modify this bit number 6 in the EPTP pointer tomorrow and see what will happen , i will share the results
-

-

-

-

-
 Yes, HyperDbg has been tested under heavy I/O operations, but the answer to this question is relative. Technically, it can generate a large number of events within seconds, so the impact depends on the specific number of events being used.
Yes, HyperDbg has been tested under heavy I/O operations, but the answer to this question is relative. Technically, it can generate a large number of events within seconds, so the impact depends on the specific number of events being used. -
 Yes, but isn't it just for EPT page-tables?
Yes, but isn't it just for EPT page-tables? -
 I mean to me, from the description of what you sent, it seems that it's only for EPT page tables, not for the regular OS page tables. 🤔
I mean to me, from the description of what you sent, it seems that it's only for EPT page tables, not for the regular OS page tables. 🤔 -
 You need to use it in the VMI mode, currently HyperDbg over two physical machines is not supported but it's in a priority list that we will implement Intel E1000 NIC drivers for HyperDbg so it could connect to the network over ethernet (at least for Intel consumer NICs).
You need to use it in the VMI mode, currently HyperDbg over two physical machines is not supported but it's in a priority list that we will implement Intel E1000 NIC drivers for HyperDbg so it could connect to the network over ethernet (at least for Intel consumer NICs). -
 But, it's on the todo list right now, not yet implemented. I'll notify it in the Twitter and different social platform accounts of HyperDbg once it's available.
But, it's on the todo list right now, not yet implemented. I'll notify it in the Twitter and different social platform accounts of HyperDbg once it's available. -
 Right now, you might also want to try pulsedbg, I think it supports debugging over two different physical machines. @honorary_bot could provide more information.
Right now, you might also want to try pulsedbg, I think it supports debugging over two different physical machines. @honorary_bot could provide more information. -
The doc of intel didn't explain this feature well... here is what I found
-
When you set the 6 bit of EPTP pointer to 1 , access from the cpu to "guest page tables entries" will be cause an ept violation with "write access"
-
So when I tried to search for the addresses code that cause the vm exit in this scenario most of it were "read access" like cmp [rax+4], 0xfe
-
Even if you want to monitor "write access" only on guest page table entries
-
That sounds crazy right😂
-
And this freez the vm because of the large number of vm exit
.. -
So when I unset that bit 6, I didn't catch this kind of vm exits..
-
So yeah it's related to Access/dirty bits of ept entries but also it influence somehow ept violation related to guest page table entries
- 04 April 2025 (11 messages)
-
@HughEverett bro hyperhv.dll , hyperlog.dll and hyperdbg_driver are loaded successfully to the kernel however I don't know how to communicate with these components to display outputs and the results of my tests .. I'm trying to build hyperdbg_driver to be like a small edr based on hyperhv
-
But it's not really documented how we can do that😅😢
-
 Hyperlog.dll is responsible for transferring buffers to user mode.
Hyperlog.dll is responsible for transferring buffers to user mode. -
 It works by sending a couple of functions (callbacks) to the hyperhv.dll (and of course hyperkd.sys).
It works by sending a couple of functions (callbacks) to the hyperhv.dll (and of course hyperkd.sys). -
 You need to make sure to call the initialization functions of hyperlog.dll.
You need to make sure to call the initialization functions of hyperlog.dll. -
Okay bro
-
But my question
-
Is it possible to not interfere with hyperjd.sys code
-
😂😂
-
I mean logically hyperkd.sys was built on the top of hyperhv as backbone
-
Why I cannot do the same 😒😢😂 I mean I'm more comfortable with hypehv.sys code and like I don't want to destroy the logic of my code
- 05 April 2025 (5 messages)
-
-
 Yes of course. You just need to initialize it from the hyperhv project or if you have a top-level project, you could initialize it from the top-level project
Yes of course. You just need to initialize it from the hyperhv project or if you have a top-level project, you could initialize it from the top-level project -
 The exact initialization routines can be used (called) from hyperhv.
The exact initialization routines can be used (called) from hyperhv. -
Great bro thanks very much
-
Joined.
- 06 April 2025 (5 messages)
-
 [discord] <spliii> Hello hello
[discord] <spliii> Hello hello -
 [discord] <spliii> i dont know if this is the right place but im about to start working on implementing AMD support for HyperDbg ^^
[discord] <spliii> i dont know if this is the right place but im about to start working on implementing AMD support for HyperDbg ^^ -
 [discord] <spliii> And wanted to ask for permission to do so and to let everyone know i am about to go do this 😄
[discord] <spliii> And wanted to ask for permission to do so and to let everyone know i am about to go do this 😄 -
 [discord] <spliii> will open a discussion on github as well 🙂
[discord] <spliii> will open a discussion on github as well 🙂 -
 It would be great. Looking forward to see how it works. You can also consider merging it to the HyperDbg repo. 👌👍
It would be great. Looking forward to see how it works. You can also consider merging it to the HyperDbg repo. 👌👍 - 09 April 2025 (44 messages)
-
@honorary_bot people of intel cpu ... why it seems that there is a tons of academic papers with graphs /algorithms/schema 📊 etc about cpu side channel attacks but it seems that the only one with a real proof of concept is the famous specter/meltdown vulnerability?
-
 are you asking why there are no PoCs?
are you asking why there are no PoCs? -
 I'm kinda sure there public PoCs for ridl and l1tf
I'm kinda sure there public PoCs for ridl and l1tf -
 They just require a more complex setup
They just require a more complex setup -
 But the idea is always the same - you just use prime and probe and look for stale data
But the idea is always the same - you just use prime and probe and look for stale data -
Ridley and l1tf?names for other side channel vulnerabilities?
-
 The "popular" ones so to say
The "popular" ones so to say -

-

-
 there are more and more
there are more and more -
 Pretty googlable
Pretty googlable -
Well that looks delicious 😋 😍
-
Must read..
-
Btw , how the researchers managed to know
-
That the cpu behave exactly while doing some
-
Brunch prediction
-
I mean is it a public info in sole Manuel Intel or they had to make some serious hare reverse
-
Engineering
-
 Wikipedia has the history here https://en.wikipedia.org/wiki/Meltdown_(security_vulnerability). But in essence around 2016 Ander Fogh and Daniel Gruss made and attempt to read the kernel data with prime and probe techinque. Thier result was negative but it got people thinking and trying out different stuff and eventually opening a pandora's boxMeltdown (security vulnerability)
Wikipedia has the history here https://en.wikipedia.org/wiki/Meltdown_(security_vulnerability). But in essence around 2016 Ander Fogh and Daniel Gruss made and attempt to read the kernel data with prime and probe techinque. Thier result was negative but it got people thinking and trying out different stuff and eventually opening a pandora's boxMeltdown (security vulnerability)vulnerability in modern microprocessors which permits unauthorized memory reads
-
 Anders' thinking originally was based on CPU pipeline model thought experiment
Anders' thinking originally was based on CPU pipeline model thought experiment -
 Of course, external researchers don't have clue on how the pipeline is designed, but they can make thier guesses
Of course, external researchers don't have clue on how the pipeline is designed, but they can make thier guesses -
Okay so it's all about hard work and analyzing the behavior of cpu.. well that's not easy xd
-
 But again, cpu pipelines are not a mystery, you can learn how to build those from books like "computer architecture: a quantative approach"
But again, cpu pipelines are not a mystery, you can learn how to build those from books like "computer architecture: a quantative approach" -
I don't remember a friend send me a research about some guys managed to find some hidden intel instructions... they can be enabled just by some weird wqys
-
 And then it boils down to the implementation details
And then it boils down to the implementation details -
They discover these instructions by a power analysis..
-
 yeah, guys from positive technologies
yeah, guys from positive technologies -
 there are some instructions that can only be enabled after red unlock, right
there are some instructions that can only be enabled after red unlock, right -
 those are for internal testing and debugging
those are for internal testing and debugging -
@HughEverett sorry 😞 bro for flooding the group with cpu channels stuffs I'm just taking a break from hypervisor bugs now xd
-
@HughEverett well that sounds some really interesting subjects...
-
 speaking of meltdown, lunar lake cpus introduced a final hw mitigation against it,,, finally
speaking of meltdown, lunar lake cpus introduced a final hw mitigation against it,,, finally -
 it's alreay described in sdm
it's alreay described in sdm -
 called LASS - linear address space separation
called LASS - linear address space separation -
 in short - addresses with highest bits set are considered as kernel addresses
in short - addresses with highest bits set are considered as kernel addresses -
 so the cpu doesnt have to consult ptes anymore and check if they are u or s
so the cpu doesnt have to consult ptes anymore and check if they are u or s -
 because of that there is no sidechannel while cpu is doing a page walk
because of that there is no sidechannel while cpu is doing a page walk -
Okay so when cpu see ffffff
-
No need to check the privilege but
-
Bit* in pte
-
 exactly
exactly -
 there will be no speculative fetch for this address, since you have your current cpl immediately
there will be no speculative fetch for this address, since you have your current cpl immediately -
 hehe, lunar lake also fixed ridl and alike
hehe, lunar lake also fixed ridl and alike -
 by removing hyperthreading
by removing hyperthreading - 11 April 2025 (2 messages)
-
 Joined.
Joined. -
 Joined.
Joined. - 13 April 2025 (3 messages)
-
 HyperDbg v0.13.1 has been released. 💫
HyperDbg v0.13.1 has been released. 💫
This version includes improved mitigations against anti-hypervisor techniques used to detect nested virtualization environments, along with various bug fixes.
Check it out:
https://github.com/HyperDbg/HyperDbg/releasesReleases · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
-
 Joined.
Joined. - 14 April 2025 (1 messages)
-
- 17 April 2025 (1 messages)
-
- 19 April 2025 (9 messages)
-
-
-
 Hey 👋
Hey 👋
You need to use the debugger either in the VMI Mode (local debugging) or the Debugger Mode (full-featured debugging). If you are debugging in VMI mode, you cannot pause (halt) the debugger or step through instructions but in the debugger mode, everything is supported. HyperDbg works best in VMware Workstation's nested virtualization (note that VMware workstation is now free). -
 Not sure if I understand the question, but there are tons of examples available in the HyperDbg's course that you can see:
Not sure if I understand the question, but there are tons of examples available in the HyperDbg's course that you can see:
https://ost2.fyi/Dbg3301
Or YouTube:
https://www.youtube.com/watch?v=RDlp0PCFgxI&list=PLUFkSN0XLZ-kF1f143wlw8ujlH2A45nZYDebuggers 3301: HyperDbgThis class teaches you how to use HyperDbg, a virtualization-based debugger.
-
-
-
 Do not use the user-mode debugger in VMI Mode for now. HyperDbg in the Debugger Mode fully supports user-mode and kernel-mode debugging.
Do not use the user-mode debugger in VMI Mode for now. HyperDbg in the Debugger Mode fully supports user-mode and kernel-mode debugging. -
 Did you follow the steps mentioned in this video?
Did you follow the steps mentioned in this video?
https://youtu.be/MDZ9zYfqo50Dbg3301: HyperDbg 02 04 HyperDbg Lab SetupView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
 If yes, then what is the exact error that is happening for you?
If yes, then what is the exact error that is happening for you? - 20 April 2025 (9 messages)
-
How should I change how to make this tester run in a virtual machine, I've changed the name of the named pipe why can't connect
-
You are running hyperdbg_app.exe
-
I think u should run
-
Hyperdbg-client.ewe
-
Exe*
-
-
-
 Yes, as Poikourditchy78 mentioned, you are running the wrong file. In the VM (guest), there is no named pipe, but instead, it's either COM1 or COM2.
Yes, as Poikourditchy78 mentioned, you are running the wrong file. In the VM (guest), there is no named pipe, but instead, it's either COM1 or COM2. -
 I recommend running HyperDbg's main client (hyperdbg-cli.exe), and then once you find the correct parameters on each side (host and guest), then try again. Note that, you also need to run the client in the host (not just guest).
I recommend running HyperDbg's main client (hyperdbg-cli.exe), and then once you find the correct parameters on each side (host and guest), then try again. Note that, you also need to run the client in the host (not just guest). - 21 April 2025 (1 messages)
-
@HughEverett in your opinion how much time it will take to create hyperdbg for linux?
- 22 April 2025 (59 messages)
-
 Hi
Hi
I estimate it to be done within 6 months to one year depending on the skill and knowledge of the person who wants to implement it (I mean the Linux kernel knowledge, I don't have that much information about Linux and how it works). -
Joined.
-
hi
-
Does anyone have an example of RW?
-
-
-
Anyone know what I'm missing?
-
Who knows that although I used my signature, I still can't load the driver?
-
I'm going to set hyperdbg to a process that belongs to me.
-
I think u didn't clone correctly the repos
-
Ia32 and some other dependencies will be downloaded automatically with git clone --recursive
-
Yes, I solved this mistake. But I don't understand why my signature can't be loaded on the driver.
-
It can only be loaded in test mode. Does it only support test mode?
-
 This is how self signed drivers work
This is how self signed drivers work -
 Only in test mode
Only in test mode -
I have my own ev driver signature, but even though I have signed it, it still doesn't work.
-
 Does it work with any other driver? I doubt it has anything to do with hyperdbg
Does it work with any other driver? I doubt it has anything to do with hyperdbg -
It seems that there is something wrong with the function entry.
-
You must sign sys.
-
 With function entry of HyperDbg? Have you tried to disable DSE instead of test signing mode?
With function entry of HyperDbg? Have you tried to disable DSE instead of test signing mode? -
 Because I think HyperDbg just comes without signing, not with test sign.
Because I think HyperDbg just comes without signing, not with test sign. -
 So, probably that's why test signing does not work, but there are plenty of options for disabling DSE. First, you can press shift and restart and then there is a start up menu that lets you disable DSE. Second option would be connecting Kdnet for disabling DSE and if you don't want to use kdnet, then you can use EfiGuard for disabling patchguard and dse.
So, probably that's why test signing does not work, but there are plenty of options for disabling DSE. First, you can press shift and restart and then there is a start up menu that lets you disable DSE. Second option would be connecting Kdnet for disabling DSE and if you don't want to use kdnet, then you can use EfiGuard for disabling patchguard and dse. -
 There are examples for all of the above mentioned methods here:
There are examples for all of the above mentioned methods here:
https://docs.hyperdbg.org/getting-started/build-and-installBuild & Install | HyperDbg DocumentationThis document helps you to build and install HyperDbg
-
 Also, you can see the video, that shows you all of these methods step by step.
Also, you can see the video, that shows you all of these methods step by step. -
I don't mean the test signature, I have a whql certified ev signature.
-
I mean, after I sign with ev, the sys file can't be loaded, and it can only be loaded when I turn on the system test mode.
-
But my ev signature is expired. But it does work, and I can load it normally in other sys files.
-
I have closed dse, so it has nothing to do with dse, but the source code.
-
 WHQL needs Microsoft approval from their website, you need to upload driver for them. Ev signing does not work anymore (I think it was Windows 10 22h2 that they start checking the drivers)
WHQL needs Microsoft approval from their website, you need to upload driver for them. Ev signing does not work anymore (I think it was Windows 10 22h2 that they start checking the drivers) -
I adjusted hyperkekd Function entry of, delete the iotco, and it can be loaded.
-
 Are you test HyperDbg on old versions of Windows?
Are you test HyperDbg on old versions of Windows? -
But you can sign with the previous ev.
-
I'm in the latest win10
-
Wqhl authentication is only for new signatures.
-
If you have an old signature. Then you can not use whql.
-
 But it won't load in Windows 11, and newer versions of Windows 10 as far as I remember (I might be wrong). Are you sure that it works? Did you also do the same with other WDK drivers? 🤔
But it won't load in Windows 11, and newer versions of Windows 10 as far as I remember (I might be wrong). Are you sure that it works? Did you also do the same with other WDK drivers? 🤔 -
Yes, I can use another hyper drivers normally.
-
Only hyperdbg can't be used in my ev signature.
-
Test mode must be used.
-
 Okay, let me give a list of drivers that you need to sign.
Okay, let me give a list of drivers that you need to sign. -
So I want to know, do you all load drivers in test mode?
-
You can send it to me for a try. The driver I compiled with wdk10 can be loaded normally.
-
 hyperhv.dll
hyperhv.dll
hyperkd.sys
hyperlog.dll
kdserial.dll -
dll
-
 You need to sign all of these drivers.
You need to sign all of these drivers. -
Dll files also need to be signed? I don't understand.
-
 Yes, a DLL could be a driver (kernel mode DLL).
Yes, a DLL could be a driver (kernel mode DLL). -
Maybe I missed this question.
-
 Of course, if you just not sign one of them, it won't work.
Of course, if you just not sign one of them, it won't work. -
But is the mode it wants to sign kernel mode or application mode?
-
I only signed the sys file.
-
 DLLs can be also signed.
DLLs can be also signed. -
 I remember years ago I signed HyperDbg and all of the DLLs are also needed to be signed. I mean kernel-mode (driver) DLLs, not user-mode DLLs.
I remember years ago I signed HyperDbg and all of the DLLs are also needed to be signed. I mean kernel-mode (driver) DLLs, not user-mode DLLs. -
Maybe that's why I'll test it tomorrow. thank you
-
I want to use it in a game.
-
😂
-
 Also, make sure to keep your signed drivers for your own use only. If Microsoft finds your signed drivers, they will blacklist your signature.
Also, make sure to keep your signed drivers for your own use only. If Microsoft finds your signed drivers, they will blacklist your signature. -
Use ept hook to bypass integrity check.
-
 Bypassing game anti-cheat systems is illegal in many countries. Tools like HyperDbg should be used responsibly for legitimate purposes such as security research and malware analysis. Put them to good use.
Bypassing game anti-cheat systems is illegal in many countries. Tools like HyperDbg should be used responsibly for legitimate purposes such as security research and malware analysis. Put them to good use. - 23 April 2025 (3 messages)
-
 Well... 😂
Well... 😂 -
Can it be used to monitor processes on X86?
-
 Yes, there is no difference between debugging a x86 process and a x64 process in HyperDbg. Both of them are supported.
Yes, there is no difference between debugging a x86 process and a x64 process in HyperDbg. Both of them are supported. - 24 April 2025 (1 messages)
-
 [discord] <t0int> when will hyperdbg support usermode stuff?
[discord] <t0int> when will hyperdbg support usermode stuff? - 25 April 2025 (3 messages)
-
 Do you mean supporting user mode debugging in the VMI mode? Right now, HyperDbg fully supports user mode debugging in the Debugger mode.
Do you mean supporting user mode debugging in the VMI mode? Right now, HyperDbg fully supports user mode debugging in the Debugger mode. -
 [discord] <t0int> docs are saying its unstable
[discord] <t0int> docs are saying its unstable -
 Docs talk about user mode debugging in the VMI mode. In the debugger mode, everything is fine.
Docs talk about user mode debugging in the VMI mode. In the debugger mode, everything is fine. - 27 April 2025 (94 messages)
-
 @HughEverett hi bro, I have a problem.
@HughEverett hi bro, I have a problem.
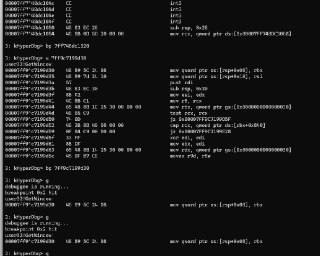
I set up three eph hooks, but it seems that only the third one is working. -

-

-
For the first two hooks It looks like they two addressed belongs to the same page which means u cannot put two hooks on them if I'm not wrong but @HughEverett need to confirm that
-
 If I only set test1, it won't work too
If I only set test1, it won't work too -

-
 I only set test1, and I can see the code of test1.
I only set test1, and I can see the code of test1. -
 it not work😢
it not work😢 -
 No, this limitation is only for the !monitor command. The !epthook does not have such a limitation.
No, this limitation is only for the !monitor command. The !epthook does not have such a limitation. -
 Are you sure you're putting hooks in instructions boundaries? I mean into valid RIP addresses? Can you send a disassembly of this addresses (using the 'u' command).
Are you sure you're putting hooks in instructions boundaries? I mean into valid RIP addresses? Can you send a disassembly of this addresses (using the 'u' command). -
 And is it a notmal code? Or a self modifying code?
And is it a notmal code? Or a self modifying code? -

-
 just like this
just like this -
 this is the code of demo
this is the code of demo -
 So, what are those addresses? Are you using VMWare?
So, what are those addresses? Are you using VMWare? -
 yes, vmware 17
yes, vmware 17 -
 And are you sure those memory addresses are called? You can test it by using the 'bp' command. Double check if the breakpoint is hit.
And are you sure those memory addresses are called? You can test it by using the 'bp' command. Double check if the breakpoint is hit. -
 e... this is .connect local
e... this is .connect local -
 can bp work under .connect local ?
can bp work under .connect local ? -

-
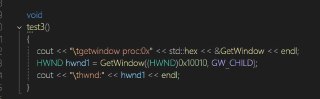
 I can see the code for both of them
I can see the code for both of them -
 but only can epthook the GetWindow, windows API
but only can epthook the GetWindow, windows API -
 No, connect to it from host using the '.debug' command.
No, connect to it from host using the '.debug' command. -
 sry, I have never used '.debug' before.
sry, I have never used '.debug' before. -
 😞
😞 -
 Use this instructions:
Use this instructions:
https://docs.hyperdbg.org/getting-started/attach-to-hyperdbg/debugAttach to a remote machine | HyperDbg DocumentationRemote debugging in VMI Mode and Debugger Mode
-
 ok, let me see
ok, let me see -
 I have tried many times, but I am unable to input anything
I have tried many times, but I am unable to input anything -

-

-
 Yes, this is correct.
Yes, this is correct. -
 Now you need to press CTRL+C in the host.
Now you need to press CTRL+C in the host. -
 It will pause the debuggee.
It will pause the debuggee. -
 Oh, I understand now. So that's how it works
Oh, I understand now. So that's how it works -
 The working style is like windbg
The working style is like windbg -
 Yes, but using HyperDbg is more complicated compared to other debuggers mainly because it operates on VMX root mode which you need to know lots of different concepts, use it based on different system-level considerations and hypervisor-based techniques. It's not like opening and working with it without prior knowledge. I highly recommend going through HyperDbg course in open security trainings or YouTube before using it:
Yes, but using HyperDbg is more complicated compared to other debuggers mainly because it operates on VMX root mode which you need to know lots of different concepts, use it based on different system-level considerations and hypervisor-based techniques. It's not like opening and working with it without prior knowledge. I highly recommend going through HyperDbg course in open security trainings or YouTube before using it:
https://ost2.fyi/Dbg3301
Or,
https://www.youtube.com/watch?v=RDlp0PCFgxI&list=PLUFkSN0XLZ-kF1f143wlw8ujlH2A45nZYDebuggers 3301: HyperDbgThis class teaches you how to use HyperDbg, a virtualization-based debugger.
-
 😳Yes, I feel it. Is there a written version of the instructions for use?
😳Yes, I feel it. Is there a written version of the instructions for use? -
 There are examples in the docs.hyperdbg.org but the videos are better to start with.
There are examples in the docs.hyperdbg.org but the videos are better to start with. -
 unfortunately, my English is not good.😱
unfortunately, my English is not good.😱 -
 I will try, at least let me use bp
I will try, at least let me use bp -

-
 I only called it once, why does the breakpoint keep hitting ?
I only called it once, why does the breakpoint keep hitting ? -
 😂
😂 -
 Because this is how breakpoints work?
Because this is how breakpoints work? -
 maby not?
maby not? -
 when I click on the vmware, the breakpoint will be hit
when I click on the vmware, the breakpoint will be hit -
 How do you expect them to work?
How do you expect them to work? -
 I hope hit once
I hope hit once -
 Have you used a debugger before? Like windbg or something?
Have you used a debugger before? Like windbg or something? -

-
 Oh, that's what you mean
Oh, that's what you mean -
 You're expecting to catch one breakpoint inside your application, right?
You're expecting to catch one breakpoint inside your application, right? -
 Got it
Got it -
 yes, I have used windbg before
yes, I have used windbg before -
 yes
yes -
 With hypervisors breakpoints work in a different way, because the hypervisor sets a breakpoint to the guest physical address
With hypervisors breakpoints work in a different way, because the hypervisor sets a breakpoint to the guest physical address -
 And since it is a usermode module, it is shared among several processes
And since it is a usermode module, it is shared among several processes -
 That's why the breakpoint may be hit
That's why the breakpoint may be hit -
 I mean it might be hit in a different process as well
I mean it might be hit in a different process as well -
 o , you are right
o , you are right -
 So it makes sense when you click vmware windows, it also calls your bp'ed function
So it makes sense when you click vmware windows, it also calls your bp'ed function -
 Thank you, I understand now
Thank you, I understand now -
 So yeah, this thing is different compared to what we are used to in windbg
So yeah, this thing is different compared to what we are used to in windbg -
 Sorry, I misunderstood your question at first
Sorry, I misunderstood your question at first -
 I thought you were expecting one-time only breakpoints :)
I thought you were expecting one-time only breakpoints :) -
 @HughEverett do you filter breakpoint hits by context?
@HughEverett do you filter breakpoint hits by context? -
 What I do in this case is compare the target cr3 with bp cr3 and skip the bp if they don't match
What I do in this case is compare the target cr3 with bp cr3 and skip the bp if they don't match -
 cr3 is unique to a process, so you can filter out only the needed ones
cr3 is unique to a process, so you can filter out only the needed ones -
 I don't think that judgment was made😂
I don't think that judgment was made😂 -
 I'm not sure how it's implemented in hyperdbg, maybe we just don't know something
I'm not sure how it's implemented in hyperdbg, maybe we just don't know something -
 It's strange why the breakpoint of test1 wasn't hit
It's strange why the breakpoint of test1 wasn't hit -
 How do you know if it wasnt?
How do you know if it wasnt? -
 I set a breakpoint by bp
I set a breakpoint by bp -
 You had several hits, right? One of those might be from your app
You had several hits, right? One of those might be from your app -
 When I run test1(), the breakpoint was not hit
When I run test1(), the breakpoint was not hit -
 The Successful one is GetWindow, it not test1()
The Successful one is GetWindow, it not test1() -
 How do you set it? Before running the app?
How do you set it? Before running the app? -
 DO you pause the app and then set the bp?
DO you pause the app and then set the bp? -
 CTRL+C / .process pid xxx / g / bp addr
CTRL+C / .process pid xxx / g / bp addr -
 Is test running before this? Is it on pause or something? It's not clear from the source code
Is test running before this? Is it on pause or something? It's not clear from the source code -
 Maybe I did something wrong, or maybe it's a console app
Maybe I did something wrong, or maybe it's a console app -
Oh right sorry I didn't read about epthool how it was designed I focused more on !monitor .. and obviously the hook operate on a page level of 4kb so u cannot put two different config for two addresses of the same page
-
No, this limitation is only for the !monitor command. The !epthook does not have such a limitation.
-
 Try the MFC exe tomorrow 😂
Try the MFC exe tomorrow 😂 -
 It should not be the problem
It should not be the problem -
 Thank you, I will try my idea tomorrow
Thank you, I will try my idea tomorrow -

-
 Good night then :)
Good night then :) -
 It's too late, I'm already confused
It's too late, I'm already confused -
 Good night
Good night -
 No, by default HyperDbg won't filter anything unless you explicitly mention it using the 'pid xx' or 'tid xx' or 'core xx' parameters:
No, by default HyperDbg won't filter anything unless you explicitly mention it using the 'pid xx' or 'tid xx' or 'core xx' parameters:
https://docs.hyperdbg.org/commands/debugging-commands/bpbp (set breakpoint) | HyperDbg DocumentationDescription of the 'bp' command in HyperDbg.
-
 But you're certainly right. The reason why he/she sees this error is because the breakpoint in set system-wide.
But you're certainly right. The reason why he/she sees this error is because the breakpoint in set system-wide. -
 Other than that, there are many options for setting a conditional breakpoint using the script engine (combining the 'pause' function with the '!epthook' command).
Other than that, there are many options for setting a conditional breakpoint using the script engine (combining the 'pause' function with the '!epthook' command).
https://docs.hyperdbg.org/commands/scripting-language/functions/debugger/pausepause | HyperDbg DocumentationDescription of the 'pause' function in HyperDbg Scripts
-
 You need to use the '.start' command, so HyperDbg will intercept the first instructions (original entry point) for you. After that, you're in the context (memory space) of the process:
You need to use the '.start' command, so HyperDbg will intercept the first instructions (original entry point) for you. After that, you're in the context (memory space) of the process:
https://docs.hyperdbg.org/commands/meta-commands/.start
Please keep in mind that whenever you continue the debuggee using the 'g' command, you're no longer in the address space of the target process when you pause it again. There are options like using the '.process', '.process2', '.thread', or '.thread2' commands each of which is implemented differently and suitable for a different use case. These commands let you switch to the memory space of your process..start (start a new process) | HyperDbg DocumentationDescription of the '.start' command in HyperDbg.
- 28 April 2025 (6 messages)
-
 @HughEverett I changed my MFC program and epthook is working now
@HughEverett I changed my MFC program and epthook is working now -
 😂
😂 -
 The console program may have been optimized
The console program may have been optimized -
 I can't hit breakpoints even with x64dbg in console program
I can't hit breakpoints even with x64dbg in console program -
 👍
👍 -

- 29 April 2025 (2 messages)
-
-
 Hi,
Hi,
You can use the '.listen' command along with the '.connect' command to connect over Ethernet. But, Ethernet debugging is only supported in the VMI mode (not the debugger mode).
https://docs.hyperdbg.org/commands/meta-commands/.listen.listen (listen on a port and wait for the debugger to connect) | HyperDbg DocumentationDescription of the '.listen' command in HyperDbg.
- 30 April 2025 (5 messages)
-
I have some problem. It is possible that the debugger is frozen and does not respond to key presses. Include Ctrl-C
-
so now you can connect via a physical ethernet cable, but only in vmi mode while it's working?
-
 If you're breaking the guest (doing something wrong that guest crashes), the kernel of the guest will BSOD the system and obviously HyperDbg couldn't pause (CTRL+C) the guest again.
If you're breaking the guest (doing something wrong that guest crashes), the kernel of the guest will BSOD the system and obviously HyperDbg couldn't pause (CTRL+C) the guest again. -
 HyperDbg is highly privileged (hypervisor level), so it means you have control over the user mode applications and the OS kernel. Changing a register or a memory without knowing the consequences will definitely BSOD the guest kernel. You should know what you are trying to do.
HyperDbg is highly privileged (hypervisor level), so it means you have control over the user mode applications and the OS kernel. Changing a register or a memory without knowing the consequences will definitely BSOD the guest kernel. You should know what you are trying to do. -
 Yes
Yes
- 01 Apr 2025 (15)
- 02 Apr 2025 (2)
- 03 Apr 2025 (22)
- 04 Apr 2025 (11)
- 05 Apr 2025 (5)
- 06 Apr 2025 (5)
- 09 Apr 2025 (44)
- 11 Apr 2025 (2)
- 13 Apr 2025 (3)
- 14 Apr 2025 (1)
- 17 Apr 2025 (1)
- 19 Apr 2025 (9)
- 20 Apr 2025 (9)
- 21 Apr 2025 (1)
- 22 Apr 2025 (59)
- 23 Apr 2025 (3)
- 24 Apr 2025 (1)
- 25 Apr 2025 (3)
- 27 Apr 2025 (94)
- 28 Apr 2025 (6)
- 29 Apr 2025 (2)
- 30 Apr 2025 (5)