- 01 August 2024 (8 messages)
-
 [discord] <ohault> I wonder what could be the best way to monitor the filesystem access of a VM through HyperDbg?
[discord] <ohault> I wonder what could be the best way to monitor the filesystem access of a VM through HyperDbg? -
 You have plenty of options as long as you know the functions that are trying to communicate with the filesystem.
You have plenty of options as long as you know the functions that are trying to communicate with the filesystem.
Probably the easiest one is using a simple '!epthook' to monitor your target function.
Please see:
https://youtu.be/tjsFRBFGis4?si=llWvBcDxY8-31qMO
Or if you want to monitor the PCIe buffer accesses for the filesystem, you could use the '!monitor' command as well. -
 [discord] <ohault> Would it be possible to map the Windows semantics about well known topics like file, registry, process, network interface, …. towards whatever external monitor agents?
[discord] <ohault> Would it be possible to map the Windows semantics about well known topics like file, registry, process, network interface, …. towards whatever external monitor agents? -
Joined.
-
 We can add Windows stuff to HyperDbg, but we've tried to keep HyperDbg as OS-independent as possible so we can easily port it to other systems in the future. (Though we did end up using a lot of Windows semantics in it.) Right now, we're planning to move those OS-specific parts to the script engine and create standard libraries to handle different symbols and structures there. @xmaple555 is currently working on adding types to the script engine. Once that's done, we'll start making standard functions to analyze, view, or modify the Windows-specific stuff in the scriptsl libraries.
We can add Windows stuff to HyperDbg, but we've tried to keep HyperDbg as OS-independent as possible so we can easily port it to other systems in the future. (Though we did end up using a lot of Windows semantics in it.) Right now, we're planning to move those OS-specific parts to the script engine and create standard libraries to handle different symbols and structures there. @xmaple555 is currently working on adding types to the script engine. Once that's done, we'll start making standard functions to analyze, view, or modify the Windows-specific stuff in the scriptsl libraries. -
 [discord] <ohault> That’s really interesting. It is somehow similar to Nitro backends
[discord] <ohault> That’s really interesting. It is somehow similar to Nitro backends -
 Nitro? 🤨
Nitro? 🤨 -
 [discord] <ohault> [reply]: https://github.com/KVM-VMI/nitro/blob/master/doc/source/architecture.rstnitro/doc/source/architecture.rst at master · KVM-VMI/nitro
[discord] <ohault> [reply]: https://github.com/KVM-VMI/nitro/blob/master/doc/source/architecture.rstnitro/doc/source/architecture.rst at master · KVM-VMI/nitroContribute to KVM-VMI/nitro development by creating an account on GitHub.
- 02 August 2024 (7 messages)
-
 Joined.
Joined. -
 👍
👍 -
 hey hey, long time no see, sorry.
hey hey, long time no see, sorry.
@HughEverett is it possible to add showing some messages on debugee ? -
 like show message on debugee from script
like show message on debugee from script -
 Hi! 👋
Hi! 👋
There is debuggee operation code (bit), if you set this bit, instead of sending message to the debugger, it'll be delivered to the debugge. -
 great!
great! -
- 04 August 2024 (1 messages)
-
Joined.
- 05 August 2024 (8 messages)
-
 Hi guys!
Hi guys!
FYI, the #Discord server and #matrix group are added (and synchronized) to the HyperDbg groups. 🎉🥂
Telegram Group: https://t.me/HyperDbg
Discord Server: https://discord.gg/anSPsGUtzN
Matrix Group: https://matrix.to/#/#hyperdbg-discussion:matrix.org
Twitter: https://twitter.com/HyperDbg -
 None
None -

-

-

-
Joined.
-
 Joined.
Joined. -
- 06 August 2024 (19 messages)
-

-
 Joined.
Joined. -
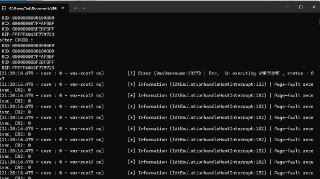
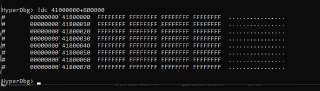
 [discord] <.wxg> Why, i can't read MMIO space
[discord] <.wxg> Why, i can't read MMIO space
https://cdn.discordapp.com/attachments/962350355839066130/1270210765051134086/image.png?ex=66b2df75&is=66b18df5&hm=576bc55650fa2e4608c0d6db0e4b0a3f28ab9aac56db29a73fdfd7b6fdabb82b& -
 Is it only for the MMIO space? Or do you see the same error for other physical addresses as well?
Is it only for the MMIO space? Or do you see the same error for other physical addresses as well? -
 [discord] <.wxg> [reply]: yep. only MMIO can't work
[discord] <.wxg> [reply]: yep. only MMIO can't work -
 Are you sure that this MMIO region is readable? Did you check the same with WinDbg? Does it read it?
Are you sure that this MMIO region is readable? Did you check the same with WinDbg? Does it read it? -
 As long as I remember (not sure) some MMIO regions that try transfer buffers to the target device (e.g., DMA regions) are not readable. Isn't it because of this? 🤨
As long as I remember (not sure) some MMIO regions that try transfer buffers to the target device (e.g., DMA regions) are not readable. Isn't it because of this? 🤨 -
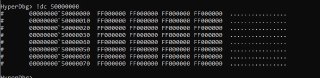
 [discord] <.wxg> [reply]: readable.
[discord] <.wxg> [reply]: readable.
from rweverything
https://cdn.discordapp.com/attachments/962350355839066130/1270228406906257408/image.png?ex=66b2efe3&is=66b19e63&hm=0e913626e26e5270ec1a3f61311bac6a4807952d066e3592c983721d96eca48d& -
Joined.
-
Joined.
-
 🤔
🤔 -
 Is it an open-source tool? Don't have any idea what's going wrong there.
Is it an open-source tool? Don't have any idea what's going wrong there. -
 Maybe cache policy?
Maybe cache policy? -
 [discord] <.wxg> [reply]: yep. I am using the the latest complied binaries
[discord] <.wxg> [reply]: yep. I am using the the latest complied binaries -
 [discord] <0xkylm> Hello
[discord] <0xkylm> Hello -
Joined.
-

-
-
 [discord] <.wxg> [reply]: What is that
[discord] <.wxg> [reply]: What is that - 07 August 2024 (9 messages)
-
 Could you send me a link to its github or source code?
Could you send me a link to its github or source code? -
 The cache policy of how to read the memory using different caching methods.
The cache policy of how to read the memory using different caching methods.
Windbg has this feature, though HyperDbg does not support caching policy yet:
https://learn.microsoft.com/en-us/windows-hardware/drivers/debuggercmds/-db---dc---dd---dp---dq---du---dw -
 But I think the problem shouldn't be because of this caching policies. 🤔
But I think the problem shouldn't be because of this caching policies. 🤔 -
 [discord] <.wxg> [reply]: https://github.com/HyperDbg/HyperDbg/releases/tag/v0.10Release v0.10 · HyperDbg/HyperDbg
[discord] <.wxg> [reply]: https://github.com/HyperDbg/HyperDbg/releases/tag/v0.10Release v0.10 · HyperDbg/HyperDbgHyperDbg v0.10 is released! If you’re enjoying HyperDbg, don’t forget to give a star 🌟 on GitHub! Please visit Build & Install to configure the environment for running HyperDbg. Check out the Q...
-
 This is why you should always consider using HyperDbg's script engine to avoid what we refer to as "unsafe behavior".
This is why you should always consider using HyperDbg's script engine to avoid what we refer to as "unsafe behavior".
Read more:
https://docs.hyperdbg.org/tips-and-tricks/considerations/the-unsafe-behavior -
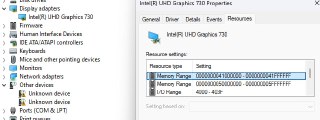
 [discord] <.wxg> [reply]: Intel Network Adapter MMIO/Space
[discord] <.wxg> [reply]: Intel Network Adapter MMIO/Space -
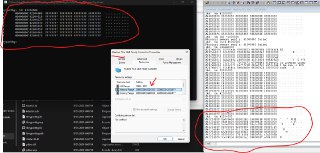
 [discord] <.wxg> [reply]: The MMIO address shown in my image is an example and not real, as depicted in the sample picture.
[discord] <.wxg> [reply]: The MMIO address shown in my image is an example and not real, as depicted in the sample picture.
Using MmMapIoSpace access the MMIO space (0x84600000) that hyperDBG cannot access.
PVOID address = MmMapIoSpaceEx(PhysicalAddress = 0x84600000, 0x100000, PAGE_READWRITE);
// Access the address;
https://cdn.discordapp.com/attachments/962350355839066130/1270609529675059251/Windows-cannot-identify-all-the-resources-Code-16.png?ex=66b452d6&is=66b30156&hm=246900c3f925aebc79098106c0949d8fb263eb053564bb3a5b3ef94e161f0b93& -
 [discord] <.wxg> [reply]: You can select a device with MMIO space from WDM, such as a network adapter or a graphics card, to check its MMIO space range and attempt to access it.
[discord] <.wxg> [reply]: You can select a device with MMIO space from WDM, such as a network adapter or a graphics card, to check its MMIO space range and attempt to access it.
Currently, HyperDBG cannot access any MMIO space.
My system version is Windows 11 23H2 22631.3880. -

- 08 August 2024 (7 messages)
-
Joined.
-

-
 The target machine (the one you want to debug) has to have native serial port. The reason for that is you need drivers for the transport. While writing a driver for serial connection is simple, it is not simple to write one and maintain it coherent with the target OS for USB.
The target machine (the one you want to debug) has to have native serial port. The reason for that is you need drivers for the transport. While writing a driver for serial connection is simple, it is not simple to write one and maintain it coherent with the target OS for USB. -
 Simply put, USB to COM converter will only work with the host machine, the target one has to have a netive serial port.
Simply put, USB to COM converter will only work with the host machine, the target one has to have a netive serial port. -
 I know a hypervisor level debugger that can debug physical machines with different transports, but I'm not sure if @HughEverett will appreciate unauthorized ad :)
I know a hypervisor level debugger that can debug physical machines with different transports, but I'm not sure if @HughEverett will appreciate unauthorized ad :) -

-

- 09 August 2024 (5 messages)
-
-
 Of course, feel free to advertise whatever you want.
Of course, feel free to advertise whatever you want. -
 I'm pretty sure he's talking about PulseDbg, which is great debugger. 👌
I'm pretty sure he's talking about PulseDbg, which is great debugger. 👌 -
 Doesn't run in VMware workstation? 🤨
Doesn't run in VMware workstation? 🤨 -
 You can start learning about hypervisors by reading Hypervisor From Scratch series:
You can start learning about hypervisors by reading Hypervisor From Scratch series:
https://rayanfam.com/tutorials/TutorialsWe write about Windows Internals, Hypervisors, Linux, and Networks.
- 10 August 2024 (21 messages)
-

-
 hello , is possible debug host exception handle? I found my vm stuck if used host nmi
hello , is possible debug host exception handle? I found my vm stuck if used host nmi -
 If you comment those lines, all exceptions are passed to the Windows IDT handler, except NMIs that are handled by HyperDbg.
If you comment those lines, all exceptions are passed to the Windows IDT handler, except NMIs that are handled by HyperDbg. -
 Guest NMIs won't be handled like this, NMIs in guest are handled through a VM-exit.
Guest NMIs won't be handled like this, NMIs in guest are handled through a VM-exit. -
 But, generally I think when an NMI is triggered, all other exceptions/faults/interrupts are masked until next execution of 'iret'.
But, generally I think when an NMI is triggered, all other exceptions/faults/interrupts are masked until next execution of 'iret'. -
 But it's kinda weird, why are you trying to do that? 🤔
But it's kinda weird, why are you trying to do that? 🤔 -

-
 Did you try to change this pragma?
Did you try to change this pragma?
https://github.com/HyperDbg/HyperDbg/blob/ceca0ae762b09ec9a8d55c94fcd62332e3657e04/hyperdbg/hyperhv/code/vmm/vmx/VmxBroadcast.c#L31HyperDbg/hyperdbg/hyperhv/code/vmm/vmx/VmxBroadcast.c at ceca0ae762b09ec9a8d55c94fcd62332e3657e04 · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
-
 Probably, the only currently maintained VT debugger is HyperDbg. I'm not aware of any other virtualization-based debugger that is currently maintained (working with the latest Windows versions).
Probably, the only currently maintained VT debugger is HyperDbg. I'm not aware of any other virtualization-based debugger that is currently maintained (working with the latest Windows versions). -
-
 HyperDbg, by its very design, is not intended for debugging games. Unlike traditional debuggers, it is more stealthy because it doesn't use any Windows debugging APIs. Debugging games are really complicated due to the anti-hypervisor and anti-debugging mechanisms they often use. This requires a deep understanding and advanced techniques to bypass these protections, which go beyond HyperDbg's intended use.
HyperDbg, by its very design, is not intended for debugging games. Unlike traditional debuggers, it is more stealthy because it doesn't use any Windows debugging APIs. Debugging games are really complicated due to the anti-hypervisor and anti-debugging mechanisms they often use. This requires a deep understanding and advanced techniques to bypass these protections, which go beyond HyperDbg's intended use.
I see some individuals do modify HyperDbg for such purposes and keep those modifications private for their personal use, but please consider that HyperDbg's philosophy is to offer a powerful VT-based debugger with unique features that are not available in classic debuggers and it's not about facilitating game cheating. -
-
 it seems have connection with debugpoint and DbgPrintEx in vmm root when uses hostidt on nmi.
it seems have connection with debugpoint and DbgPrintEx in vmm root when uses hostidt on nmi. -
 HyperDbg doesn't use DbgPrint and it's variants in the vmx root mode.
HyperDbg doesn't use DbgPrint and it's variants in the vmx root mode. -
 How did you run HyperDbg? Is there a way I can reproduce your error?
How did you run HyperDbg? Is there a way I can reproduce your error? -
 I add some log in hyperhv and it get this problem. If u want to reproduce this problem, you can try adding a breakpoint in vmm code.
I add some log in hyperhv and it get this problem. If u want to reproduce this problem, you can try adding a breakpoint in vmm code. -
 You shouldn't use DbgPrint in hyperhv. You need to use the 'LogInfo' and its variants to use custom hyperdbg's logging component instead of DbgPrint.
You shouldn't use DbgPrint in hyperhv. You need to use the 'LogInfo' and its variants to use custom hyperdbg's logging component instead of DbgPrint. -

-
 @yxxyz take a look at this reply too. It might help if you trying to debug HyperDbg.
@yxxyz take a look at this reply too. It might help if you trying to debug HyperDbg. -
- 11 August 2024 (7 messages)
-
Has anyone encountered this error before? It is triggered when exiting debugging on a real machine (the computer was in sleep for more than 12 hours without being used before).
1: kd> k
# Child-SP RetAddr Call Site
00 ffffab00`d17eb158 fffff806`608fbe2e nt!KeBugCheckEx
01 ffffab00`d17eb160 fffff806`6080891f nt!HvlpVtlCallExceptionHandler+0x22
02 ffffab00`d17eb1a0 fffff806`6075f917 nt!RtlpExecuteHandlerForException+0xf
03 ffffab00`d17eb1d0 fffff806`6075d846 nt!RtlDispatchException+0x297
04 ffffab00`d17eb8f0 fffff806`607fef42 nt!KiDispatchException+0x186
05 ffffab00`d17ebfb0 fffff806`607fef10 nt!KxExceptionDispatchOnExceptionStack+0x12
06 ffffa789`48c2f388 fffff806`608126e5 nt!KiExceptionDispatchOnExceptionStackContinue
07 ffffa789`48c2f390 fffff806`6080c178 nt!KiExceptionDispatch+0x125
08 ffffa789`48c2f570 fffff806`860a3fe2 nt!KiInvalidOpcodeFault+0x338
09 ffffa789`48c2f708 00000dcc`8167789f hprdbghv!AsmVmxVmcall+0x22 [f:\HyperDbg\hyperdbg\hprdbghv\code\assembly\AsmVmxOperation.asm @ 32]
0a ffffa789`48c2f710 00000000`00000000 0x00000dcc`8167789f -
 I think a similar issue was discussed previously in the group. At that time, we conclude that there are some situations maybe with ACPI that is not handled correctly in HyperDbg.
I think a similar issue was discussed previously in the group. At that time, we conclude that there are some situations maybe with ACPI that is not handled correctly in HyperDbg. -
 But, unfortunately it's really hard to reproduce and find the root cause.
But, unfortunately it's really hard to reproduce and find the root cause. -
 Though, you're callstack is really interesting to me, since it seems that a VMCALL vm-exit happens there which usually happens in the case of Hyper-V. As far as I know, VMware workstation won't use VMCALL instruction within the guest. So, just curious to know, is hyper-v active in your target system? 🤔
Though, you're callstack is really interesting to me, since it seems that a VMCALL vm-exit happens there which usually happens in the case of Hyper-V. As far as I know, VMware workstation won't use VMCALL instruction within the guest. So, just curious to know, is hyper-v active in your target system? 🤔 -
-
-
 [discord] <.wxg> [reply]: Did you reproduce it?
[discord] <.wxg> [reply]: Did you reproduce it? - 12 August 2024 (1 messages)
-
 Joined.
Joined. - 13 August 2024 (4 messages)
-
 Got it thank you.
Got it thank you. -
 Not yet, though I'll check it this week.
Not yet, though I'll check it this week. -
https://rayanfam.com/topics/defeating-malware-anti-vm-techniques-cpuid-based-instructions/ @HughEverett Is this bypass feature built into hyerdbg? How to enable it?Defeating malware’s Anti-VM techniques (CPUID-Based Instructions)
We write about Windows Internals, Hypervisors, Linux, and Networks.
-
 Nope it's not on HyperDbg but you can write a simple script to achieve the same functionality. Take a look at this video, you'll get an idea how to write it:
Nope it's not on HyperDbg but you can write a simple script to achieve the same functionality. Take a look at this video, you'll get an idea how to write it:
https://youtu.be/H4lrb5x64Ws?si=PKawMAypbHH2gyMdDbg3301: HyperDbg 08 03 CPUID HookingView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
- 14 August 2024 (16 messages)
-
-
After waking up the machine I send the exit command triggering this error
-
 is it the process of VMware tools?
is it the process of VMware tools? -
I'm running on a real machine
-
 Is it a Windows process? or an anti-hypervisor technique?
Is it a Windows process? or an anti-hypervisor technique? -
The triggered address is invalid, and no other related anti-hypervisor programs are running
-
Debugger saved IRQL for processor 0x1 -- 2 (DISPATCH_LEVEL)
-
Process space in system
-
If you are debugging in a virtual machine, this is the case: manually triggering sleep and then the virtual machine appears to restart immediately. Am I the only one who encounters this situation?
test NtOpenProcess
test NtOpenProcess
the remote connection is closed
ffffffff: kHyperDbg> -
 [discord] <hongjunli> Hi guys How do I use it on xdbg64?
[discord] <hongjunli> Hi guys How do I use it on xdbg64? -
Joined.
-
 There are a couple of ways for passing debugging events (e.g., #bp and #db) to the ring 0 or the ring 3 debuggers like using these commands:
There are a couple of ways for passing debugging events (e.g., #bp and #db) to the ring 0 or the ring 3 debuggers like using these commands:
test breakpoint off
test trap off
You can use the above commands to pass events to x64dbg or WinDbg. -
 Is it about executing VMCALL or triggering the bug for sleep? Not sure if we're in the same page. 🤔
Is it about executing VMCALL or triggering the bug for sleep? Not sure if we're in the same page. 🤔 -
 [discord] <rayanfam> [reply]: Also here is a video of debugging WinDbg by using HyperDbg, you might find it helpful:
[discord] <rayanfam> [reply]: Also here is a video of debugging WinDbg by using HyperDbg, you might find it helpful:
https://youtu.be/wL7qDdzq5gA?si=-r8T8aM7guyrr7SdDbg3301: HyperDbg 11 02 Debugging WinDbgView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
I am discussing two issues:
The first is to install hyperdbg on a real machine (using epthook), sleep and wake up the machine, and then send the exit command to exit and trigger a blue screen.
The second is to install hyperdbg in vmware (using epthook) and then manually trigger sleep to immediately trigger a restart (no blue screen) -
Joined.
- 15 August 2024 (4 messages)
-
 I just tested it on VMware and it just closes the connection.
I just tested it on VMware and it just closes the connection. -
 Which is expected, I didn't see a VMCALL or anything like that. 🤔
Which is expected, I didn't see a VMCALL or anything like that. 🤔 -
 Maybe it only happens on a physical machine?
Maybe it only happens on a physical machine? -
 [discord] <rayanfam> [reply]: I tested it with a sample MMIO address and it works. I don't have an nvidia GPU right now to test it with MMIO address space of a GPU but it seems to work on regular MMIOs.
[discord] <rayanfam> [reply]: I tested it with a sample MMIO address and it works. I don't have an nvidia GPU right now to test it with MMIO address space of a GPU but it seems to work on regular MMIOs.
https://cdn.discordapp.com/attachments/962350355839066130/1273599714725728337/image.png?ex=66bf33aa&is=66bde22a&hm=50dcc26b2c8bba643660a5fc24fefb43d00aabdd646f6a364fcc4bc47190eaa4& - 16 August 2024 (5 messages)
-
 [discord] <.wxg> [reply]: None of the MMIO accesses work in my case. I am using VMI; could that be related?
[discord] <.wxg> [reply]: None of the MMIO accesses work in my case. I am using VMI; could that be related? -
 [discord] <.wxg> [reply]: Physical and virtual addresses are working, except for MMIO.
[discord] <.wxg> [reply]: Physical and virtual addresses are working, except for MMIO. -
-
 That's weird. Maybe it's because of specific IO device (GPU in this case). 🤔
That's weird. Maybe it's because of specific IO device (GPU in this case). 🤔 -
 [discord] <.wxg> [reply]: I suspect that the MMIO address of the graphics card in the virtual machine is physical memory space, so it works because this device is a virtual graphics card.
[discord] <.wxg> [reply]: I suspect that the MMIO address of the graphics card in the virtual machine is physical memory space, so it works because this device is a virtual graphics card.
Have you tried accessing real MMIO addresses? - 18 August 2024 (46 messages)
-
 Yeah, it seems you're right.
Yeah, it seems you're right. -
 HyperDbg cannot show MMIO addresses in the physical machine. I'll try to investigate that. 🤔
HyperDbg cannot show MMIO addresses in the physical machine. I'll try to investigate that. 🤔 -
 How do you implement physical memory access? mapiospace?
How do you implement physical memory access? mapiospace? -
 No, I think I mapped it to a reserved virtual address directly from PTE.
No, I think I mapped it to a reserved virtual address directly from PTE. -
 Is it wrong? 🤨
Is it wrong? 🤨 -
 Sorry, don’t quite got what you mean. What is a reserved virtual address?
Sorry, don’t quite got what you mean. What is a reserved virtual address? -
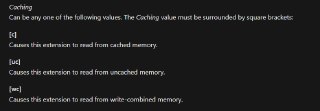
 Two points to consider when working with MMIO: EPT entry for that physical (system) address should be uncached. There are some devices that allow write-combined caching, but in general it is uncached. Second: it should be accessed as dwords (4 bytes)
Two points to consider when working with MMIO: EPT entry for that physical (system) address should be uncached. There are some devices that allow write-combined caching, but in general it is uncached. Second: it should be accessed as dwords (4 bytes) -
 This function reserves a virtual address without actually allocating physical memory. Then, we could safely modify the PTE entry corresponding to this address and change the PFN of this address and access the physical memory using the same virtual address.
This function reserves a virtual address without actually allocating physical memory. Then, we could safely modify the PTE entry corresponding to this address and change the PFN of this address and access the physical memory using the same virtual address.
https://github.com/HyperDbg/HyperDbg/blob/ceca0ae762b09ec9a8d55c94fcd62332e3657e04/hyperdbg/hyperhv/code/memory/MemoryMapper.c#L573HyperDbg/hyperdbg/hyperhv/code/memory/MemoryMapper.c at ceca0ae762b09ec9a8d55c94fcd62332e3657e04 · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 Ok understood your implementation, make sure it is mapped as uncached then
Ok understood your implementation, make sure it is mapped as uncached then -
 So it could be a caching problem?
So it could be a caching problem? -
 And accessed as 4 bytes. memcpy doesn’t work by default
And accessed as 4 bytes. memcpy doesn’t work by default -
 Most likely one of those two things
Most likely one of those two things -
 I observed a similar behaviour when I was using 64 bit implementation of memcpy
I observed a similar behaviour when I was using 64 bit implementation of memcpy -
 Intel devices allow that
Intel devices allow that -
 But non Intel - mostly not
But non Intel - mostly not -
 4 bytes? You mean reading 8 bytes from the MMIO space doesn't work? 🤨
4 bytes? You mean reading 8 bytes from the MMIO space doesn't work? 🤨 -
 I see it’s Realtek
I see it’s Realtek -
 No, it should not by the PCI spec actually
No, it should not by the PCI spec actually -
 It’s just Intel devices on bus 0 (root complex) are not real pci devices :)
It’s just Intel devices on bus 0 (root complex) are not real pci devices :) -
 So they allow random width access
So they allow random width access -
 Once it’s random Realtek or something else, it will likely fail
Once it’s random Realtek or something else, it will likely fail -
 Your [memcpy] should only operate in aligned 4 bytes chunks there
Your [memcpy] should only operate in aligned 4 bytes chunks there -
 Not sure if I get it correctly. Reading 8 bytes at a time is not allowed?
Not sure if I get it correctly. Reading 8 bytes at a time is not allowed? -
 No, just 4 bytes. It’s by the PCI spec
No, just 4 bytes. It’s by the PCI spec -
 The mmio from the screenshot is a BAR address
The mmio from the screenshot is a BAR address -
 So, pci
So, pci -
 One more question, is there any way to know whether and address is a RAM physical or an MMIO address?
One more question, is there any way to know whether and address is a RAM physical or an MMIO address? -
 That also means not 1 or 2 bytes. Only mov dword ptr
That also means not 1 or 2 bytes. Only mov dword ptr -
 Yes, two ways
Yes, two ways -
 As long as I remember, the arrangement of MMIO physical addresses only passes to Windows at startup (from UEFI).
As long as I remember, the arrangement of MMIO physical addresses only passes to Windows at startup (from UEFI). -
 I created this issue for further investigation: https://github.com/HyperDbg/HyperDbg/issues/457Problem with reading physical addresses of MMIO devices in the VMI Mode · Issue #457 · HyperDbg/HyperDbg
I created this issue for further investigation: https://github.com/HyperDbg/HyperDbg/issues/457Problem with reading physical addresses of MMIO devices in the VMI Mode · Issue #457 · HyperDbg/HyperDbgBased on the discussion, in the HyperDbg group. It seems that HyperDbg cannot read MMIO physical addresses in the VMI Mode. ref: https://t.me/HyperDbg/7557
-
 First way is to follow UEFI memory map. UEFI does everything for you
First way is to follow UEFI memory map. UEFI does everything for you -
 Is it still available once Windows is fully loaded?
Is it still available once Windows is fully loaded? -
 Second - sort of simplistic root complex driver, you can learn reserved memory regions TOLUD, TOLUUD and stuff like that from pci device 0.0.0
Second - sort of simplistic root complex driver, you can learn reserved memory regions TOLUD, TOLUUD and stuff like that from pci device 0.0.0 -
 On client systems, doesn’t work for servers!
On client systems, doesn’t work for servers! -
 No, it’s in the boot services only
No, it’s in the boot services only -
 And since you work on windows, there might be a 3rd way - parse pfn database.
And since you work on windows, there might be a 3rd way - parse pfn database. -
 Some reserved memory address ranges are in ram, but you need to treat those as mmios as well
Some reserved memory address ranges are in ram, but you need to treat those as mmios as well -
 Like gfx dsm and gsm for instance
Like gfx dsm and gsm for instance -
 Do you have any sample codes for this? e.g., any open source project that did the similar thing?
Do you have any sample codes for this? e.g., any open source project that did the similar thing? -
 Ah, kinda complex 🫠
Ah, kinda complex 🫠 -
 That I’m not sure, but I can share my pseudo code
That I’m not sure, but I can share my pseudo code -
 Once I’m at my computer though, I’m travelling atm :)
Once I’m at my computer though, I’m travelling atm :) -
 Great. Thank you. Pls share it with us once you have access to it. 🙏
Great. Thank you. Pls share it with us once you have access to it. 🙏 -
 [discord] <.wxg> [reply]: 🫡
[discord] <.wxg> [reply]: 🫡 -
Joined.
- 19 August 2024 (3 messages)
-
 hey hey, any news about using asm in script body ?
hey hey, any news about using asm in script body ? -
Joined.
-
 some useful script - how to get current time as integers:
some useful script - how to get current time as integers:
? {
void printTime() {
printf("process pid %d \n",$pid);
timePtr = $time;
printf("TIME PTR %x\n", timePtr);
yearPtr = timePtr - 10;
year = (db(yearPtr+1) << 8) | db(yearPtr);
monthPtr = timePtr - E;
month = (db(monthPtr+1) << 8) | db(monthPtr);
dayPtr = timePtr - C;
day = (db(dayPtr+1) << 8) | db(dayPtr);
hourPtr = timePtr - A;
hour = (db(hourPtr+1) << 8) | db(hourPtr);
minPtr = timePtr - 8;
min = (db(minPtr+1) << 8) | db(minPtr);
secPtr = timePtr - 6;
sec = (db(secPtr+1) << 8) | db(secPtr);
msecPtr = timePtr - 4;
msec = (db(msecPtr+1) << 8) | db(msecPtr);
printf("FULL TIME : %d %d %d %d %d %d %d\n", year, month, day, hour, min, sec, msec);
}
printTime();
} - 20 August 2024 (31 messages)
-
 Joined.
Joined. -
-
 Will be ready in future versions. @xmaple555 will notify us once he finds time to implement it.
Will be ready in future versions. @xmaple555 will notify us once he finds time to implement it. -
 Great. Can you consider creating a PR and add it here? https://github.com/HyperDbg/scripts/tree/master/basicsscripts/basics at master · HyperDbg/scripts
Great. Can you consider creating a PR and add it here? https://github.com/HyperDbg/scripts/tree/master/basicsscripts/basics at master · HyperDbg/scriptsA collection of useful HyperDbg scripts. Contribute to HyperDbg/scripts development by creating an account on GitHub.
-
 It's handled from this function:
It's handled from this function:
https://github.com/HyperDbg/HyperDbg/blob/ceca0ae762b09ec9a8d55c94fcd62332e3657e04/hyperdbg/hyperhv/code/vmm/vmx/Vmexit.c#L168HyperDbg/hyperdbg/hyperhv/code/vmm/vmx/Vmexit.c at ceca0ae762b09ec9a8d55c94fcd62332e3657e04 · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 @HughEverett how do i stop breaking on popfq call ?
@HughEverett how do i stop breaking on popfq call ? -
 Stop on execution of popfq?
Stop on execution of popfq? -
 i mean it automatically stops, i want prevent it
i mean it automatically stops, i want prevent it -
 Does it enable a trap flag from the stack?
Does it enable a trap flag from the stack? -
 PR created
PR created -
 mm i dont know,
mm i dont know,
i even dont have any monitor, but vm stops all of sudden:
3: kHyperDbg> g
debuggee is running...
ffff8104`0971da4c 9D popfq
3: kHyperDbg> g
debuggee is running...
ffff8104`0971da4d C3 ret
3: kHyperDbg> g
debuggee is running...
ffff8104`0b81daff F1 int1
4: kHyperDbg> g
debuggee is running...
ffff8104`0b81db01 81 24 24 FF FE FF FF and dword ptr ss:[rsp], 0xFFFFFEFF
4: kHyperDbg> g
debuggee is running...
ffff8104`0b81db08 9D popfq
4: kHyperDbg> g
debuggee is running...
ffff8104`0b81db09 C3 ret
4: kHyperDbg> g
debuggee is running...
ffff8104`096926ff F1 int1
5: kHyperDbg> g -
 Check the trap flag before continuing the debuggee.
Check the trap flag before continuing the debuggee. -
 like:
like:
r @tf -
 ok.. will wait until next stop and check
ok.. will wait until next stop and check -
 It seems to be an anti-debugging method.
It seems to be an anti-debugging method. -
 If it's because of a trap flag, then you have plenty of options for masking it.
If it's because of a trap flag, then you have plenty of options for masking it. -
 i noticed, that it appears when im connecting to vm by RDP
i noticed, that it appears when im connecting to vm by RDP -
 🤨🤨
🤨🤨 -
 i will let you know, when it stops again, its not so easy to reproduce
i will let you know, when it stops again, its not so easy to reproduce -
__vmx_vmwrite(GUEST_RIP, (ULONG64)g_VirtualGuestMemoryAddress) - g_VirtualGuestMemoryAddress - addres starting guest code?
-
 @HughEverett got it again:
@HughEverett got it again:
0: kHyperDbg> r @tf
tf=0000000000000001
0: kHyperDbg> g
debuggee is running...
ntkrnlmp!KiSystemCall64+0x3:
fffff803`6e811d03 65 48 89 24 25 10 00 00 00 mov qword ptr gs:[0x0000000000000010], rsp
0: kHyperDbg> r @tf
tf=0000000000000001
0: kHyperDbg> -
 😘
😘 -
 yes
yes -
 Ah, as I told you, it seems to be a anti-debugging method. You have plenty of options here. You can completely disable trap flags (#DBs) and later activate it by using 'test trap off'
Ah, as I told you, it seems to be a anti-debugging method. You have plenty of options here. You can completely disable trap flags (#DBs) and later activate it by using 'test trap off' -
 or you can write a simple '!epthook' that either masks the trap flag '@tf = 0;' in a script or change the stack value that will be poped later and mask the trap flag.
or you can write a simple '!epthook' that either masks the trap flag '@tf = 0;' in a script or change the stack value that will be poped later and mask the trap flag. -
 can you help with epthook? on which action hook shall execute ?
can you help with epthook? on which action hook shall execute ? -
 I think it needs to be executed after 'popfq'. 🤔
I think it needs to be executed after 'popfq'. 🤔 -
 Or if you want to modify stack (since the 'popfq' instruction pops the rflags value from stack) then it should be on the 'popfq' instruction itself. or the instruction before the 'popfq'.
Or if you want to modify stack (since the 'popfq' instruction pops the rflags value from stack) then it should be on the 'popfq' instruction itself. or the instruction before the 'popfq'. -
 im not sure whether popfq comes from debuggable process
im not sure whether popfq comes from debuggable process -
 debuggable process? HyperDbg doesn't care which process you gonna debug, you can put hooks on whatever system component that you want.
debuggable process? HyperDbg doesn't care which process you gonna debug, you can put hooks on whatever system component that you want. -
 ok.. looks like more info needed, i didnt note address which calls popfq
ok.. looks like more info needed, i didnt note address which calls popfq - 21 August 2024 (75 messages)
-
and in the new version, there is a trap(rflag.tf) processing when executing cpuid?
-
Joined.
-
 We didn't discover a good solution for it yet!
We didn't discover a good solution for it yet! -
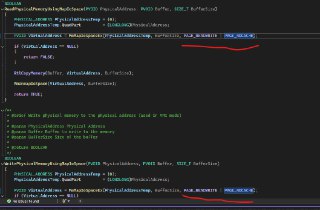
 Regarding this one, I changed the implementation to use 'MmMapIoSpaceEx'. Though, there seem to be a problem in the current implementation as the resulting memory is not equal to WinDbg's memory.
Regarding this one, I changed the implementation to use 'MmMapIoSpaceEx'. Though, there seem to be a problem in the current implementation as the resulting memory is not equal to WinDbg's memory. -
as far as I remember, it is necessary to check for the trap flag in vmexit (cpuid), handle the exception, and then the cpuid
-
 But last time that we implemented it, it didn't work, if I remember correctly? 🤔
But last time that we implemented it, it didn't work, if I remember correctly? 🤔 -
 This is the new implementation of physical memory reading. Though, the above problem exists.
This is the new implementation of physical memory reading. Though, the above problem exists.
https://github.com/HyperDbg/HyperDbg/blob/4b41b42d6c356820803322ad0ed30f63384260e0/hyperdbg/hyperhv/code/memory/MemoryManager.c#L174HyperDbg/hyperdbg/hyperhv/code/memory/MemoryManager.c at 4b41b42d6c356820803322ad0ed30f63384260e0 · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 @honorary_bot do you have any idea regarding this? Is it correctly implemented?
@honorary_bot do you have any idea regarding this? Is it correctly implemented? -
 The result of reading physical memory is different from WinDbg's MMIO space.
The result of reading physical memory is different from WinDbg's MMIO space. -
it worked, but periodically the hypervisor began to crash
-
 It works fine with the regular (non-MMIO memory) but for MMIO, the result is invalid.
It works fine with the regular (non-MMIO memory) but for MMIO, the result is invalid. -
 What was the crash error?
What was the crash error? -
-
 Did you find its patch? Where did we change last time to detect it?
Did you find its patch? Where did we change last time to detect it? -
there is no source code left ;((( I thought the branch would exist on github
-
 PAGE_NOCACHE needed for uncached mappings
PAGE_NOCACHE needed for uncached mappings -
 PVOID VirtualAddress = MmMapIoSpaceEx(PhysicalAddressTemp, BufferSize, PAGE_READWRITE);
PVOID VirtualAddress = MmMapIoSpaceEx(PhysicalAddressTemp, BufferSize, PAGE_READWRITE); -
 Try PAGE_READWRITE | PAGE_NOCACHE
Try PAGE_READWRITE | PAGE_NOCACHE -
 Same result:
Same result: -

-
 I'll try to rewrite it for you today.
I'll try to rewrite it for you today. -
 FFFFFFFF is a correct result for an unmapped mmio space
FFFFFFFF is a correct result for an unmapped mmio space -
 Where did you get this addres from?
Where did you get this addres from? -
That's great.
-

-
 So, you mean the WinDbg's result is incorrect in this case?
So, you mean the WinDbg's result is incorrect in this case? -
 Oh, it's a GFX device, MMIO BAR
Oh, it's a GFX device, MMIO BAR -
 No, windbg is right then
No, windbg is right then -
 Can you read 41000000 + 800000 just to make sure?
Can you read 41000000 + 800000 just to make sure? -
 I don't remember if this BAR starts with GTT or MMIO space
I don't remember if this BAR starts with GTT or MMIO space -
 Oh wait, wait
Oh wait, wait -
 I think I know what's happening
I think I know what's happening -

-
 I'm confusing the GFX BARs
I'm confusing the GFX BARs -
 Can you read 500000000 instead? The other BAR?
Can you read 500000000 instead? The other BAR? -
 50000000
50000000 -

-
 So! It works
So! It works -
 It should be a framebuffer
It should be a framebuffer -
 Unless the OS driver is loaded
Unless the OS driver is loaded -
 Then why WinDbg is different in that case?
Then why WinDbg is different in that case? -
 🤔
🤔 -
 I would suggest you to test BARs from a different device
I would suggest you to test BARs from a different device -
 I'm very well awware of GFX devices (it's my job, hehe)
I'm very well awware of GFX devices (it's my job, hehe) -
 It would take a lot of time to explain why GFX MMIO is a bad target for testing
It would take a lot of time to explain why GFX MMIO is a bad target for testing -
 50000000?
50000000? -
 Ah, got it
Ah, got it -
 It behaves very different depending on a platform state
It behaves very different depending on a platform state -
 okay, I'll test it with another MMIO physical address and will let you know.
okay, I'll test it with another MMIO physical address and will let you know. -
 Try one of network adapters (preferrably not the root complex one)
Try one of network adapters (preferrably not the root complex one) -
 Not on bus 0
Not on bus 0 -

-
 Still FFFFFFF.
Still FFFFFFF. -
 It's on PCIe bus 2
It's on PCIe bus 2 -
 Well, MmCopyMemory(UserBuffer, CopyAddress, Size, MM_COPY_MEMORY_PHYSICAL, ReturnSize) will succeed, right? Try removing it
Well, MmCopyMemory(UserBuffer, CopyAddress, Size, MM_COPY_MEMORY_PHYSICAL, ReturnSize) will succeed, right? Try removing it -
 Also, can't find what CheckAddressPhysical does
Also, can't find what CheckAddressPhysical does -

-

-
 The same.
The same. -
 Is your underlying EPT PTE is also non-cached?
Is your underlying EPT PTE is also non-cached? -
 Coz I don't see any obvious mistake here
Coz I don't see any obvious mistake here -
 Other than EPT discrepancy
Other than EPT discrepancy -
 Not sure. So, you mean I need to read it through a VMCALL in VMX-root mode to bypass EPT?
Not sure. So, you mean I need to read it through a VMCALL in VMX-root mode to bypass EPT? -
 FFFFFFFF is usually an invalid MMIO space
FFFFFFFF is usually an invalid MMIO space -
 I'm not sure about your implementation details, but yeah, sounds like worth trying
I'm not sure about your implementation details, but yeah, sounds like worth trying -
 @instw0 check this new branch: https://github.com/HyperDbg/HyperDbg/tree/cpuid-trapGitHub - HyperDbg/HyperDbg at cpuid-trap
@instw0 check this new branch: https://github.com/HyperDbg/HyperDbg/tree/cpuid-trapGitHub - HyperDbg/HyperDbg at cpuid-trapState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 I tried VMCALL, still the same result. But, it's kinda expected since even WinDbg is under the hypervisor, so if the problem was because of EPT caching policies, it should produce the same result for WinDbg too.
I tried VMCALL, still the same result. But, it's kinda expected since even WinDbg is under the hypervisor, so if the problem was because of EPT caching policies, it should produce the same result for WinDbg too. -
 I see, then I'm not quite sure what's going on
I see, then I'm not quite sure what's going on -
 sorry
sorry -
 No worries, if I find the problem, I'll let you know.
No worries, if I find the problem, I'll let you know. -
-
ia32-doc/out/ia32.h: No such file or directory
-
-
 You forgot '--recursive' in the git clone.
You forgot '--recursive' in the git clone. -
what could be the reason for this error?
- 22 August 2024 (8 messages)
-
 reclone it like:
reclone it like:
git clone -b cpuid-trap --recursive https://github.com/HyperDbg/HyperDbg.git -
recent commits deleted the submodule in the branch dev. https://github.com/HyperDbg/HyperDbg/commit/27359df8faced23b40ac4cc05a57d891fa9b78d4Fix script-engine-test submodule bug · HyperDbg/HyperDbg@27359df
Remove the script-engine-test from incorrect path
-
 It's actually not removed, still available here:
It's actually not removed, still available here:
https://github.com/HyperDbg/HyperDbg/tree/dev/hyperdbg/testsHyperDbg/hyperdbg/tests at dev · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 But there was an error, since I moved it from another folder to this directory, it was not correctly modified. That's why Behrooz manually fixed it to avoid errors in the CI/CD.
But there was an error, since I moved it from another folder to this directory, it was not correctly modified. That's why Behrooz manually fixed it to avoid errors in the CI/CD. -
 @HughEverett 20:55:24.297 - core : 3 - vmx-root? yes) [+] Information (DebuggerPerformRunScript:1740) | err, exceeding the max execution count - where i can find this error in code ?i dont see DebuggerPerformRunScript class...
@HughEverett 20:55:24.297 - core : 3 - vmx-root? yes) [+] Information (DebuggerPerformRunScript:1740) | err, exceeding the max execution count - where i can find this error in code ?i dont see DebuggerPerformRunScript class... -
 @xmaple555 maybe you know the answer ^^^^ ? :)
@xmaple555 maybe you know the answer ^^^^ ? :) -
HyperDbg/hyperdbg/include/SDK/Headers/Constants.h at ceca0ae762b09ec9a8d55c94fcd62332e3657e04 · HyperDbg/HyperDbg
State-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
- 24 August 2024 (3 messages)
-
!epthook kernel32!BaseThreadInitThunk script{
if (strcmp("notepad.exe", $pname)==0){
pause();
}
} -
// Injects interruption to a guest
VOID EventInjectInterruption(INTERRUPT_TYPE InterruptionType, EXCEPTION_VECTORS Vector, BOOLEAN DeliverErrorCode, ULONG32 ErrorCode)
{
INTERRUPT_INFO Inject = { 0 };
Inject.Valid = TRUE;
Inject.InterruptType = InterruptionType;
Inject.Vector = Vector;
Inject.DeliverCode = DeliverErrorCode;
__vmx_vmwrite(VM_ENTRY_INTR_INFO, Inject.Flags);
if (DeliverErrorCode) {
__vmx_vmwrite(VM_ENTRY_EXCEPTION_ERROR_CODE, ErrorCode);
}
}
there is such an interrupt handling function... what should be written to __vmx_vm write so that processing is forwarded to the operating system? -
 can you pls explain in short how that counter works? does it just gets increased when event is triggered or there is some more complex logic underneath ?
can you pls explain in short how that counter works? does it just gets increased when event is triggered or there is some more complex logic underneath ? - 25 August 2024 (5 messages)
-
 There are a couple of functions for injecting different interrupts/exceptions/faults in this file, you can use it:
There are a couple of functions for injecting different interrupts/exceptions/faults in this file, you can use it:
https://github.com/HyperDbg/HyperDbg/blob/master/hyperdbg/hyperhv/code/vmm/vmx/Events.cHyperDbg/hyperdbg/hyperhv/code/vmm/vmx/Events.c at master · HyperDbg/HyperDbgState-of-the-art native debugging tools. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 It will be injected immediately after the processor resumes in the vmx non-root mode.
It will be injected immediately after the processor resumes in the vmx non-root mode.
Other than that, the ability to inject is also exported in the script engine as functions with/without error code, you can use these function:
https://docs.hyperdbg.org/commands/scripting-language/functions/events/event_inject
and
https://docs.hyperdbg.org/commands/scripting-language/functions/events/event_inject_error_codeevent_inject | HyperDbg DocumentationDescription of the 'event_inject' function in HyperDbg Scripts
-
Thanks for the answer! This is your example of hypervisor from scratch 8. Does it send interrupt handling to the operating system by default?
-
 It will be injected by processor to the target guest. And it's handled by the operating system.
It will be injected by processor to the target guest. And it's handled by the operating system. -
so the parameters in the project are set correctly and nothing needs to be changed? analog operation in hyperdbg "trap flag off"
- 26 August 2024 (1 messages)
-
 [discord] <kanrab> Hey. I’d like to contribute but I’m a bit of a newbie when it comes to contributing to large projects. I hope you don’t mind some newbie questions and I’m happy to be here :)!
[discord] <kanrab> Hey. I’d like to contribute but I’m a bit of a newbie when it comes to contributing to large projects. I hope you don’t mind some newbie questions and I’m happy to be here :)! - 27 August 2024 (3 messages)
-
 Ah, sorry for the very late response. That's really cool. You can start with Hypervisor From Scratch to know about the starting points and internals:
Ah, sorry for the very late response. That's really cool. You can start with Hypervisor From Scratch to know about the starting points and internals:
https://rayanfam.com/tutorials/TutorialsWe write about Windows Internals, Hypervisors, Linux, and Networks.
-
 Yes. The parameters in the HyperDbg's VMX event handler are correctly configured.
Yes. The parameters in the HyperDbg's VMX event handler are correctly configured. -
Joined.
- 28 August 2024 (3 messages)
-
-
 [discord] <.wxg> Dear HyperDbg Team,
[discord] <.wxg> Dear HyperDbg Team,
I have two questions regarding the !monitor command:
How can I set two different Debug Scripts (DS) with !monitor, one for write and one for read operations? When I try to use !monitor r and !monitor w to set two different scripts, I receive an error indicating that the same address cannot be set twice.
How can I unhook an address that is being monitored by !monitor?
Thank you for your assistance. -
 [discord] <.wxg> [reply]: When using the !monitor command, I found that it incorrectly identifies the correct MMIO address as invalid.
[discord] <.wxg> [reply]: When using the !monitor command, I found that it incorrectly identifies the correct MMIO address as invalid.
https://cdn.discordapp.com/attachments/962350355839066130/1278419624672628756/image.png?ex=66d0bc8e&is=66cf6b0e&hm=2fb65cf2d3cfd3139427d8e3d292b2c2bd79aabb7ab9e0c990c2656bf3b91f0a& - 29 August 2024 (8 messages)
-
-

-
 What do you mean by 'debugging interrupts'? 🤔
What do you mean by 'debugging interrupts'? 🤔 -
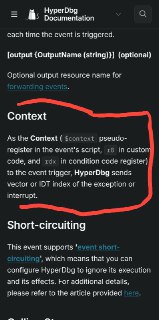
 You can have as many !monitor hooks as you want but only one hook within a 4 KB boundary of a page. For example, if you put a hook 0x12345678, you cannot put any more hooks on 0x12345000 to 0x12345fff (within a page boundary). For using multiple hooks you can hook an entire range and then manage the occurrence of each hook using its script (by checking with the $context pseudo-register).
You can have as many !monitor hooks as you want but only one hook within a 4 KB boundary of a page. For example, if you put a hook 0x12345678, you cannot put any more hooks on 0x12345000 to 0x12345fff (within a page boundary). For using multiple hooks you can hook an entire range and then manage the occurrence of each hook using its script (by checking with the $context pseudo-register).
> How can I unhook an address that is being monitored by !monitor?
The !monitor hook as well as almost all of the features of HyperDbg are exported as events. Events can be disabled/removed using the 'events' command.
https://docs.hyperdbg.org/commands/debugging-commands/eventsevents (show and modify active/disabled events) | HyperDbg DocumentationDescription of the 'event' command in HyperDbg.
-
 It's probably because the way that we check for the validity of the address is not working for MMIOs. Could you please open an issue on GitHub? So, it will be fixed.
It's probably because the way that we check for the validity of the address is not working for MMIOs. Could you please open an issue on GitHub? So, it will be fixed. -
 For more information regarding the first question, you can take a look at this video:
For more information regarding the first question, you can take a look at this video:
https://www.youtube.com/watch?v=PX38N5F3SL8&list=PLUFkSN0XLZ-kF1f143wlw8ujlH2A45nZY&index=34Dbg3301: HyperDbg 05 03 Memory MonitorView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
int1, int3.... is it possible to disable them somehow like "trap flag off"
-
- 30 August 2024 (7 messages)
-
 [discord] <.wxg> [reply]: I use separate write and read scripts because I don't know how to distinguish between read and write operations in DS. For MMIO, it would be very unreasonable to use a 4K page as the basic unit for EPTHOOK2. Of course, it would be best if DS could distinguish between write and read operations.
[discord] <.wxg> [reply]: I use separate write and read scripts because I don't know how to distinguish between read and write operations in DS. For MMIO, it would be very unreasonable to use a 4K page as the basic unit for EPTHOOK2. Of course, it would be best if DS could distinguish between write and read operations.
In my scenario, most of what I want to achieve is similar to the mmiotrace provided by the Linux kernel. -
 [discord] <.wxg> [reply]: ok
[discord] <.wxg> [reply]: ok -

-
 Joined.
Joined. -
 Hello, going through the opensecurity2 training right now , and really want to use usermode for debugger instead of just kernel. I know I have to build the hyperdbg and I am getting errors , I have tried building on release and debug. I have VS 2022 , C++ package and windows 11 SDK installed .. I then installed the latest 10.026 SDK and WDK. I am using windows 10 for both host and VM , VM using vmware workstation 17
Hello, going through the opensecurity2 training right now , and really want to use usermode for debugger instead of just kernel. I know I have to build the hyperdbg and I am getting errors , I have tried building on release and debug. I have VS 2022 , C++ package and windows 11 SDK installed .. I then installed the latest 10.026 SDK and WDK. I am using windows 10 for both host and VM , VM using vmware workstation 17 -
 Also using the same build for hyperDbg-cli on host and guest but get failed to load driver on guest
Also using the same build for hyperDbg-cli on host and guest but get failed to load driver on guest -
 Do I have to build it on guest too ?
Do I have to build it on guest too ? - 31 August 2024 (17 messages)
-
 INT1 is #DB which you can disable or enable it by using:
INT1 is #DB which you can disable or enable it by using:
test trap off
test trap on -
 For INT3 which is #BP, you can use
For INT3 which is #BP, you can use
test breakpoint off
test breakpoint on -
 If you're using the script engine the '$context' shows the vector number.
If you're using the script engine the '$context' shows the vector number. -

-
 Right now, the !monitor command cannot distinguish between read/write/execute but that's a really good feature to be added to it. I'll add it to the todo list.
Right now, the !monitor command cannot distinguish between read/write/execute but that's a really good feature to be added to it. I'll add it to the todo list. -
 Some solution that came to my mind about distinguishing between read/write is checking it with the target instruction (current @rip). Basically, you need read the @rip using memcpy in the script engine and make a basic instruction disassembler for MOV commands.
Some solution that came to my mind about distinguishing between read/write is checking it with the target instruction (current @rip). Basically, you need read the @rip using memcpy in the script engine and make a basic instruction disassembler for MOV commands. -
 It's not just kernel, HyperDbg support both user mode and kernel mode in the Debugger Mode:
It's not just kernel, HyperDbg support both user mode and kernel mode in the Debugger Mode:
https://docs.hyperdbg.org/using-hyperdbg/prerequisites/operation-modesOperation Modes | HyperDbg DocumentationDifferent Modes of Operation in HyperDbg
-
 What's the error? Didn't fully understand what's going wrong there 🤔
What's the error? Didn't fully understand what's going wrong there 🤔 -
thank you! Very match
-
 [discord] <.wxg> [reply]: Using 8B 89 to distinguish between read and write is indeed a solution, but since the source data comes from different registers, it seems a bit tricky.
[discord] <.wxg> [reply]: Using 8B 89 to distinguish between read and write is indeed a solution, but since the source data comes from different registers, it seems a bit tricky. -
 [discord] <.wxg> [reply]: It would be very beneficial to provide additional context, such as Read/Write flags, Address, and Value.
[discord] <.wxg> [reply]: It would be very beneficial to provide additional context, such as Read/Write flags, Address, and Value. -
 Do you want to see what's modified (the modification result)?
Do you want to see what's modified (the modification result)? -
 Yes, agree. It would be added to the future versions.
Yes, agree. It would be added to the future versions. -
 [discord] <.wxg> [reply]: read value
[discord] <.wxg> [reply]: read value
write newValue -
 You can use event calling stages for it. Check the first example of the !monitor command here:
You can use event calling stages for it. Check the first example of the !monitor command here:
https://docs.hyperdbg.org/tips-and-tricks/misc/event-calling-stageEvent calling stage | HyperDbg DocumentationThe event calling stage in HyperDbg
-
 Also check this video: https://youtu.be/rlNALkSacbs?si=WfM_abZzpk5kqSVFDbg3301: HyperDbg 10 10 Event Calling Stages
Also check this video: https://youtu.be/rlNALkSacbs?si=WfM_abZzpk5kqSVFDbg3301: HyperDbg 10 10 Event Calling StagesView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
 Joined.
Joined.
- 01 Aug 2024 (8)
- 02 Aug 2024 (7)
- 04 Aug 2024 (1)
- 05 Aug 2024 (8)
- 06 Aug 2024 (19)
- 07 Aug 2024 (9)
- 08 Aug 2024 (7)
- 09 Aug 2024 (5)
- 10 Aug 2024 (21)
- 11 Aug 2024 (7)
- 12 Aug 2024 (1)
- 13 Aug 2024 (4)
- 14 Aug 2024 (16)
- 15 Aug 2024 (4)
- 16 Aug 2024 (5)
- 18 Aug 2024 (46)
- 19 Aug 2024 (3)
- 20 Aug 2024 (31)
- 21 Aug 2024 (75)
- 22 Aug 2024 (8)
- 24 Aug 2024 (3)
- 25 Aug 2024 (5)
- 26 Aug 2024 (1)
- 27 Aug 2024 (3)
- 28 Aug 2024 (3)
- 29 Aug 2024 (8)
- 30 Aug 2024 (7)
- 31 Aug 2024 (17)