- 04 May 2023 (103 messages)
-
Joined.
-
Joined.
-
-
Joined.
-

-
 Joined.
Joined. -

-
 Joined.
Joined. -
 Joined.
Joined. -
 Joined.
Joined. -

-
 Joined.
Joined. -
-
 Joined.
Joined. -

-
Joined.
-
 Joined.
Joined. -

-
 Joined.
Joined. -
 Joined.
Joined. -
 Joined.
Joined. -
 Joined.
Joined. -
Joined.
-
-
 Joined.
Joined. -
Joined.
-
Joined.
-

-
 Joined.
Joined. -

-

-
 Joined.
Joined. -
 Joined.
Joined. -
-
Joined.
-
Joined.
-
Joined.
-
 Joined.
Joined. -

-
Joined.
-

-
 Joined.
Joined. -
Joined.
-
 Joined.
Joined. -
Joined.
-

-
-
-
-
Joined.
-
 Joined.
Joined. -
Joined.
-

-

-

-
 Joined.
Joined. -
 Joined.
Joined. -
Joined.
-
-

-
 Joined.
Joined. -
Joined.
-
-
 Joined.
Joined. -
 Joined.
Joined. -

-
Joined.
-
Joined.
-
-
-
Joined.
-

-

-
 Joined.
Joined. -
Joined.
-
-
Joined.
-

-
-
 Joined.
Joined. -
-
-
 Joined.
Joined. -
 Joined.
Joined. -
Joined.
-
Joined.
-
Joined.
-
-
-
 Joined.
Joined. -

-

-
-

-
-
-
-
-
Not talking about the community. I’m talking about the competency of the tool
-
 For what specific use?
For what specific use? -
Malware analysis and binary decompilation
-
 That is to broad. For example if it is usermode malware you are working with I don’t think there is a clear advantage in using HyperDbg. But in the other hand it can shine when working with kernel stuff. In that sense it compares to using IDA + vmware’ gdb stub (or some other VM with debugging)
That is to broad. For example if it is usermode malware you are working with I don’t think there is a clear advantage in using HyperDbg. But in the other hand it can shine when working with kernel stuff. In that sense it compares to using IDA + vmware’ gdb stub (or some other VM with debugging) -
 suddenly so many people, what happened
suddenly so many people, what happened - 05 May 2023 (51 messages)
-

-
Ya of course
-

-
Joined.
-

-
Joined.
-

-
 Joined.
Joined. -
Joined.
-
Joined.
-
Joined.
-

-
Joined.
-
 Joined.
Joined. -
-
Joined.
-
-
Joined.
-
About ept: For example, I used !epthook nt!ExAllocatePool for ExAllocatePool, which means hook in all process spaces, but I see that the code uses the current process id
-
 The kernel addresses are shared, when we set an EPT hook on the target function based on the current process (memory layout), it's like we set breakpoint on all of the processes.
The kernel addresses are shared, when we set an EPT hook on the target function based on the current process (memory layout), it's like we set breakpoint on all of the processes. -

-
If it is the kernel address then it doesn't matter if the process id is set or not, right? If it's a hook on the user process like !epthook test!exe.main then by default only the main function of the current process context is hooked, do I understand it correctly?
-
Joined.
-
-

-
 Joined.
Joined. -
 If you want to hook a module test!exe.main you should specify the process id. Like
If you want to hook a module test!exe.main you should specify the process id. Like
!epthook test!MyFunctions pid 1c0
Otherwise, HyperDbg won't know where to look for the specific address and if the address is not valid in the context (CR3) of current process, then it shows and invalid address error. -
 Joined.
Joined. -
 The kernel addresses should be shared among all processes, that's why we use the memory layout of current process to set hook on them. (there are exceptions for some kernel addresses that are only mapped into specific processes)
The kernel addresses should be shared among all processes, that's why we use the memory layout of current process to set hook on them. (there are exceptions for some kernel addresses that are only mapped into specific processes) -
 For example, regular OS page-tables are not shared between different processes (addresses are still in the kernel) but in these cases, again you should specify the PID to switch to target process layout.
For example, regular OS page-tables are not shared between different processes (addresses are still in the kernel) but in these cases, again you should specify the PID to switch to target process layout. -
okay seems similar to the windbg bp /p command
-
 nice to see @horsicq here. congrats for being admin 🥳
nice to see @horsicq here. congrats for being admin 🥳 -
 Joined.
Joined. -
 Welcome @mrfearless 🌺
Welcome @mrfearless 🌺 -
-
 Joined.
Joined. -
Joined.
-
 Hyper-V is the worst hv that we've ever dealt with it. I'm not sure if HyperDbg currently works on Hyper V's nested virtualization or not. Last time that I test it on Hyper V, it was okay on 1 core VM. About EPT hooks, yes it's possible but I don't know where to put EPT hooks, generally there should be two ways of reaching to the user mode. One is by using SYSRET and another one is IRET, there are also other possible scenarios but I'm not sure if it gets everything or not. So, you have to put ept hook on these instructions.
Hyper-V is the worst hv that we've ever dealt with it. I'm not sure if HyperDbg currently works on Hyper V's nested virtualization or not. Last time that I test it on Hyper V, it was okay on 1 core VM. About EPT hooks, yes it's possible but I don't know where to put EPT hooks, generally there should be two ways of reaching to the user mode. One is by using SYSRET and another one is IRET, there are also other possible scenarios but I'm not sure if it gets everything or not. So, you have to put ept hook on these instructions. -
-
 But there are also other (better) options, one is using Mode Based Execution Controls and another one is disabling user mode execution in regular page tables. Both of them are implemented in hyperdbg but I never exposed it as a command.
But there are also other (better) options, one is using Mode Based Execution Controls and another one is disabling user mode execution in regular page tables. Both of them are implemented in hyperdbg but I never exposed it as a command.
The source code is here:
https://github.com/HyperDbg/HyperDbg/blob/master/hyperdbg/hprdbghv/code/hooks/ept-hook/ModeBasedExecHook.c
It gets the execution when it reaches to user mode.
You can modify it a little bit to achieve your goals.HyperDbg/hyperdbg/hprdbghv/code/hooks/ept-hook/ModeBasedExecHook.c at master · HyperDbg/HyperDbgState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 I'm not talking about its quality, just a bunch of shit they've added as TLFS. 😞
I'm not talking about its quality, just a bunch of shit they've added as TLFS. 😞
Read this tweet:
https://twitter.com/Intel80x86/status/1523033338407235585?t=c0WLKd3v1OFtP2PBR_HKQA&s=19 -
-
 TLFS is pretty bad yeah. That said most hypervisors will be using hyperv’s VMM on Windows. The thing is that by default hyperv partitions are created with support for bunch of hyperv specific stuff: synthIC, synthetic MSRs, hypercalls etc. instead what you probably want is to create an exo-partition. But I’m not sure if Microsoft has any documentation about it.
TLFS is pretty bad yeah. That said most hypervisors will be using hyperv’s VMM on Windows. The thing is that by default hyperv partitions are created with support for bunch of hyperv specific stuff: synthIC, synthetic MSRs, hypercalls etc. instead what you probably want is to create an exo-partition. But I’m not sure if Microsoft has any documentation about it. -

-

-
 What do you mean by exo-partition? 🤔
What do you mean by exo-partition? 🤔
Is it something related to hyper-v API? 🤨 -
 The problem is with invalidating EPT on hypercalls. We gonna use the nested virtualization feature of hyper-v.
The problem is with invalidating EPT on hypercalls. We gonna use the nested virtualization feature of hyper-v. -
 Yes when you create a partition you can control the characteristics of it: https://learn.microsoft.com/en-us/virtualization/api/hypervisor-platform/hypervisor-platformWindows Hypervisor Platform API Definitions
Yes when you create a partition you can control the characteristics of it: https://learn.microsoft.com/en-us/virtualization/api/hypervisor-platform/hypervisor-platformWindows Hypervisor Platform API DefinitionsDescribes Windows Hypervisor Platform API definitions and provides a high-level overview of the third-party architecture.
-
 This one in particular controls the things you mentioned: https://learn.microsoft.com/en-us/virtualization/api/hypervisor-platform/funcs/whvsetpartitionpropertyWHvSetPartitionProperty
This one in particular controls the things you mentioned: https://learn.microsoft.com/en-us/virtualization/api/hypervisor-platform/funcs/whvsetpartitionpropertyWHvSetPartitionPropertyUnderstaning how to work with WHvSetPartitionProperty and its parameters, syntax, and return value
-
 Joined.
Joined. -
Joined.
- 06 May 2023 (16 messages)
-
Joined.
-
 Joined.
Joined. -
 Joined.
Joined. -
Joined.
-
 lin from bbs.pediy ?
lin from bbs.pediy ? -
yes
-
 welcome 😊
welcome 😊 -
😊
-
 Joined.
Joined. -

-
Joined.
-
 Here's the new function tracing feature that just added to hdbg.
Here's the new function tracing feature that just added to hdbg.
In case you guys wanna test it (and provide feedback), switch to this commit and build hdbg:
https://github.com/HyperDbg/HyperDbg/commit/746320b35941ff01af64aaa74b55636e9ec0130b -

-

-

-
 It basically lets you trace function calls (and rets from user-to-kernel) and (kernel-to-user).
It basically lets you trace function calls (and rets from user-to-kernel) and (kernel-to-user). - 07 May 2023 (3 messages)
-
Joined.
-
 Joined.
Joined. -

- 08 May 2023 (66 messages)
-
any idea to add https://github.com/actions/upload-artifact so that we can play with the new features quicklyGitHub - actions/upload-artifact
Contribute to actions/upload-artifact development by creating an account on GitHub.
-

-
I noticed that the new version development environment has been upgraded to so this will encounter some compilation issues in vs2019.
-
reclone to resolve the issue
-

-
 Joined.
Joined. -
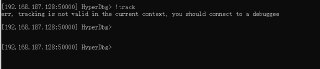
how do I stop !track command? i can't use ctrl+c to stop it. 😂
-
 Sure, I'll enable the artifacts. Previously it was enabled but I thought that it might be useless so we removed it.
Sure, I'll enable the artifacts. Previously it was enabled but I thought that it might be useless so we removed it. -
 CTRL+C should work, there should be an error if it didn't stop. How can I reproduce the error?
CTRL+C should work, there should be an error if it didn't stop. How can I reproduce the error? -
 I test it by using a user-mode application that triggers a simple network system-call.
I test it by using a user-mode application that triggers a simple network system-call. -
I'm using it in kernel debugging. User mode doesn't seem to be supported by default, it seems we need to enable a macro ourselves before compiling
-
https://github.com/HyperDbg/HyperDbg/issues/228 and i can't quit to reconnect hdbgUnable to reconnect to hyperdbg · Issue #228 · HyperDbg/HyperDbg
Describe the bug To Reproduce run hdbg in host run hdbg in guest press ctrl+c and press exit in host to exit hdbg run hdbg in host to reconnect guest Expected behavior we can reconnect to the guest...
-
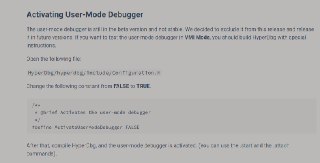
 no, don't enable it by changing the macro. It shouldn't work on VMI Mode. Test it in Debugger Mode. Are you using VMware Workstation?
no, don't enable it by changing the macro. It shouldn't work on VMI Mode. Test it in Debugger Mode. Are you using VMware Workstation? -
yes, I'm using VMware
-
I did not succeed in using hdbg in user mode. I will try again later
-
 So, whenever a user-mode application runs a 0xcc (int 3), the kernel debugger should be notified and from that point you can start tracing (!track). Or for example, put a breakpoint somewhere (either on a user address or kernel address).
So, whenever a user-mode application runs a 0xcc (int 3), the kernel debugger should be notified and from that point you can start tracing (!track). Or for example, put a breakpoint somewhere (either on a user address or kernel address). -
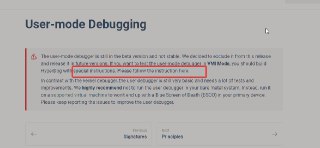
 yep, consider testing everything in the kernel debugger in the Debugger Mode. The user debugger is neither tested nor in a working state.
yep, consider testing everything in the kernel debugger in the Debugger Mode. The user debugger is neither tested nor in a working state. -
 and of course, !track command won't work in VMI mode.
and of course, !track command won't work in VMI mode. -
so how do I use !track on top of the user mode application
-
-
-
yes !track command can't work in VMI mode.
-
can't access the process space, what am I missing
-
 You don't need to use the user-debugger for that, whenever you have access to the kernel debugger (in debugger mode), you can easily debug all the user-mode applications by simply switch to them. Or simply putting breakpoint on them. Then everything is just like a normal debugger, you can step through the instructions, blah blah
You don't need to use the user-debugger for that, whenever you have access to the kernel debugger (in debugger mode), you can easily debug all the user-mode applications by simply switch to them. Or simply putting breakpoint on them. Then everything is just like a normal debugger, you can step through the instructions, blah blah -
how to switch it
-
i tried to enter the process space to test !track but no luck
-
 There might be two reasons for that. First, the process might never get executed! HyperDbg is different from Windbg in switching into the processes. WinDbg is compiled with Windows, so they can easily hook the process context switching, but we can't. Instead, we use two methods to intercept processes. One by intercepting accesses to gs:[188] and other one is by using the clock interrupts. Please visit:
There might be two reasons for that. First, the process might never get executed! HyperDbg is different from Windbg in switching into the processes. WinDbg is compiled with Windows, so they can easily hook the process context switching, but we can't. Instead, we use two methods to intercept processes. One by intercepting accesses to gs:[188] and other one is by using the clock interrupts. Please visit:
https://docs.hyperdbg.org/tips-and-tricks/considerations/difference-between-process-and-thread-switching-commandsDifference between process and thread switching commandsWhen to use '.process', '.process2', '.thread', and '.thread2' commands
-
-
 Okay, the reason for that is because of recent changes in Windows context switching mechanism in Windows (https://twitter.com/Intel80x86/status/1655461171280105472?s=20). I have to update the code, to make it work again, but there is a simple way to switch to the target process. Use the following script:
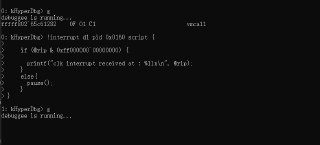
Okay, the reason for that is because of recent changes in Windows context switching mechanism in Windows (https://twitter.com/Intel80x86/status/1655461171280105472?s=20). I have to update the code, to make it work again, but there is a simple way to switch to the target process. Use the following script:
!interrupt d1 pid 0x27A4 script {
if (@rip & 0xff000000`00000000) {
printf("clk interrupt received at : %llx\n", @rip);
}
else{
pause();
}
} -
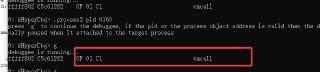
 0xd1 is the interrupt vector for nt!HalpTimerClockInterrupt. and please also change the process id: pid 0x27A4
0xd1 is the interrupt vector for nt!HalpTimerClockInterrupt. and please also change the process id: pid 0x27A4 -
-
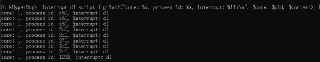
 can you give me the results for this command :
can you give me the results for this command :
!interrupt d1 script { printf("core: %x, process id: %x, interrupt: %llx\n", $core, $pid, $context); } -
Only change the pid, just try a quick test
-
 I wanna make sure that the clock interrupt reaches to all cores. Not just core 0.
I wanna make sure that the clock interrupt reaches to all cores. Not just core 0. -
-
 is there any cores other than core 1? like core 0? or core 2?
is there any cores other than core 1? like core 0? or core 2? -
vmware :
number of processors: 2
number of cores per processor: 1 -
 Use 1 processor, with 1, or two or whatever cores.
Use 1 processor, with 1, or two or whatever cores. -
 Just one processor.
Just one processor. -

-

-
 Works for me, both .process command and !interrupt command. Just make sure to interact with the process, so the Windows puts it in the context switching queue.
Works for me, both .process command and !interrupt command. Just make sure to interact with the process, so the Windows puts it in the context switching queue. -
 and also .process2 is working.
and also .process2 is working. -
okay, I need to leave my computer for a while and test it later.
-
 But the problem with .process2 is that it intercepts the execution in the kernel-mode (not user-mode) but the .process and the !interrupt commands should be fine.
But the problem with .process2 is that it intercepts the execution in the kernel-mode (not user-mode) but the .process and the !interrupt commands should be fine. -
 Sure 👍
Sure 👍 -
 Btw, I made an update to the 'dev' branch to check for other cores (other than 0th core) in the .process command, please 'git pull' the dev branch before testing:
Btw, I made an update to the 'dev' branch to check for other cores (other than 0th core) in the .process command, please 'git pull' the dev branch before testing:
https://github.com/HyperDbg/HyperDbg/commit/d5fdc3a39d2efb0d6e0063bbf01111706cec0343checking for cores other the 0th core in process switching · HyperDbg/HyperDbg@d5fdc3aState-of-the-art native debugging tool. Contribute to HyperDbg/HyperDbg development by creating an account on GitHub.
-
 The key technique to work with this command is to interact with the process, so a clock interrupt is arrived and HyperDbg can intercept it. If the process finishes the execution faster than the clock interrupt interval, HyperDbg won't have a chance to intercept the process execution.
The key technique to work with this command is to interact with the process, so a clock interrupt is arrived and HyperDbg can intercept it. If the process finishes the execution faster than the clock interrupt interval, HyperDbg won't have a chance to intercept the process execution. -
 Personally, I prefer to use this script rather than the '.process' command. Because it guarantees that you'll intercept the execution in the user-mode (while the .process might intercept the execution in the kernel mode).
Personally, I prefer to use this script rather than the '.process' command. Because it guarantees that you'll intercept the execution in the user-mode (while the .process might intercept the execution in the kernel mode). -
Joined.
-

-
still doesn't seem to work, I've used the latest dev branch and set the processor to 1 core set to 1
-
-
-
-
 Why VMCALL happens here? There is something wrong, probably an error in code that you see VMCALL after running this command.
Why VMCALL happens here? There is something wrong, probably an error in code that you see VMCALL after running this command. -
 I have to investigate why you see a VMCALL in this command.
I have to investigate why you see a VMCALL in this command. -
 The gif quality is low btw. Probably telegram compressed it.
The gif quality is low btw. Probably telegram compressed it. -
I don't know why, I don't understand the principle behinds😂
-
Do you need any more logs from me, I can provide them to you now, I happen to be at the computer at the moment
-
 The principle behind the .process command is to intercept the clock interrupt. Whenever the processor (configured by OS) wants to switch to a new process, it throws a clock interrupt. HyperDbg will be noticied in this case and intercept the execution. That's how .process works.
The principle behind the .process command is to intercept the clock interrupt. Whenever the processor (configured by OS) wants to switch to a new process, it throws a clock interrupt. HyperDbg will be noticied in this case and intercept the execution. That's how .process works. -
 Can you investigate from where the VMCALL is invoked? It might be a little bit hard but in any case please tell me the commands that cause this VMCALLs. What process did you open? cmd.exe? Can you upload the gif videos with a better quality? Maybe in .zip format.
Can you investigate from where the VMCALL is invoked? It might be a little bit hard but in any case please tell me the commands that cause this VMCALLs. What process did you open? cmd.exe? Can you upload the gif videos with a better quality? Maybe in .zip format. -
-
 Thanks. I'll try to reproduce the error and will notify you. Did you open CMD.exe?
Thanks. I'll try to reproduce the error and will notify you. Did you open CMD.exe? -
yes, start cmd.exe by the administrator in the virtual machine and hyperdbg-cli.exe by cmd.exe
-
- 09 May 2023 (23 messages)
-
Infinite hardware breakpoints: https://bbs.kanxue.com/thread-277124.htm
-
 Joined.
Joined. -
Joined.
-

-

-
 Ollybone-like trick?
Ollybone-like trick? -
What
-
Do you speak Chinese?
-
 A very old ollydbg plugin that was used to implement hardware breakpoints” by removing pages execute permissions. It actually leveraged a TLB desync trick (similar to PaX’s pagexec) to do it, because at that time processors didn’t have NX bit so you had to toggle the P bit.
A very old ollydbg plugin that was used to implement hardware breakpoints” by removing pages execute permissions. It actually leveraged a TLB desync trick (similar to PaX’s pagexec) to do it, because at that time processors didn’t have NX bit so you had to toggle the P bit. -

-
Yeah
-
 Joined.
Joined. -
 The same feature for read/write is also available in Hdbg.
The same feature for read/write is also available in Hdbg.
https://docs.hyperdbg.org/commands/extension-commands/monitor
https://docs.hyperdbg.org/design/features/vmm-module/design-of-monitor!monitor (monitor read/write/execute to a range of memory)Description of the '!monitor' command in HyperDbg.
-
 But I still couldn't still convince myself why we need the same functionality for executable pages. Isn't breakpoints (hidden ept breakpoints) just enough?
But I still couldn't still convince myself why we need the same functionality for executable pages. Isn't breakpoints (hidden ept breakpoints) just enough? -
 How do hidden ept breakpoints work?
How do hidden ept breakpoints work? -

-
 Somehow
Somehow -
 Design of !epthook
Design of !epthookDesign of !epthook command
-
 Ah cool, kinda de opposite (handle potential read/writes)
Ah cool, kinda de opposite (handle potential read/writes) -

-
 Joined.
Joined. -
 Joined.
Joined. -
- 11 May 2023 (1 messages)
-
- 12 May 2023 (4 messages)
-

-

-
Joined.
-
- 13 May 2023 (1 messages)
-
 Joined.
Joined. - 15 May 2023 (1 messages)
-
- 17 May 2023 (1 messages)
-
- 18 May 2023 (1 messages)
-
 Joined.
Joined. - 19 May 2023 (1 messages)
-
- 20 May 2023 (2 messages)
-
Joined.
-

- 22 May 2023 (1 messages)
-
Joined.
- 23 May 2023 (1 messages)
-

- 24 May 2023 (1 messages)
-
 HyperDbg is updated to v0.2.1, some bugs relating to EPT hooks (!monitor and !epthook) are fixed. Please consider updating it: https://github.com/HyperDbg/HyperDbg/releases/tag/v0.2.1Release v0.2.1 · HyperDbg/HyperDbg
HyperDbg is updated to v0.2.1, some bugs relating to EPT hooks (!monitor and !epthook) are fixed. Please consider updating it: https://github.com/HyperDbg/HyperDbg/releases/tag/v0.2.1Release v0.2.1 · HyperDbg/HyperDbgHyperDbg v0.2.1 is released! If you’re enjoying HyperDbg, don’t forget to give a star 🌟 on GitHub! Please visit Build & Install to configure the environment for running HyperDbg. Check out the ...
- 25 May 2023 (4 messages)
-
Joined.
-
-
 Joined.
Joined. -
- 26 May 2023 (3 messages)
-
-
Joined.
-
- 27 May 2023 (1 messages)
-
 Joined.
Joined. - 28 May 2023 (11 messages)
-

-

-

-
 Hi and welcome
Hi and welcome -
 Hello! 😊☺️
Hello! 😊☺️
Welcomeeeeeeeeeeeee 👌👌👍
Thanks for joining here. -
-
Welcome, we're glad to have you here!
-
 Welcome 👍
Welcome 👍 -
 Welcome Duncan! 🌹🙏
Welcome Duncan! 🌹🙏 -
 Joined.
Joined. -
x32/64dbg surprise everyone 😄
- 29 May 2023 (3 messages)
-
 WelcoOoOme🙌
WelcoOoOme🙌 -

-
Joined.
- 31 May 2023 (1 messages)
-
- 04 May 2023 (103)
- 05 May 2023 (51)
- 06 May 2023 (16)
- 07 May 2023 (3)
- 08 May 2023 (66)
- 09 May 2023 (23)
- 11 May 2023 (1)
- 12 May 2023 (4)
- 13 May 2023 (1)
- 15 May 2023 (1)
- 17 May 2023 (1)
- 18 May 2023 (1)
- 19 May 2023 (1)
- 20 May 2023 (2)
- 22 May 2023 (1)
- 23 May 2023 (1)
- 24 May 2023 (1)
- 25 May 2023 (4)
- 26 May 2023 (3)
- 27 May 2023 (1)
- 28 May 2023 (11)
- 29 May 2023 (3)
- 31 May 2023 (1)