- 01 February 2024 (35 messages)
-
Joined.
-
-
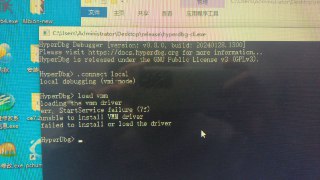
 Is the driver compiled and available in the target directory? hprdbghv.sys and hprdbgkd.sys
Is the driver compiled and available in the target directory? hprdbghv.sys and hprdbgkd.sys -
-
 Weird 🤔
Weird 🤔
What is your system information? I mean Windows version + Processor model? -
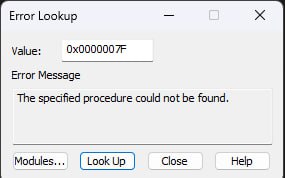
 Error 0x7f translates to this.
Error 0x7f translates to this. -
win10 1909,CPU e5-2696 v2
-
 This is a really old processor (3rd generation) probably that's why it didn't work.
This is a really old processor (3rd generation) probably that's why it didn't work. -
13 i5,also like this
-
 13th gen?
13th gen? -
 did you see the video describing how to run HyperDbg at this page?
did you see the video describing how to run HyperDbg at this page?
https://docs.hyperdbg.org/getting-started/build-and-installBuild & InstallThis document helps you to build and install HyperDbg
-
 All of the checks are performed ?
All of the checks are performed ? -
but ,
-
-
is ok
-
-
-
is not ok
-
-
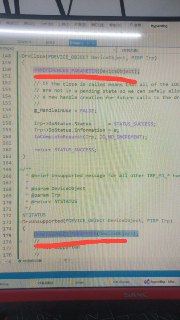
 Wait, is it failed on the DriverEntry part? HyperDbg doesn't load its driver on DriverEntry. The VT-x part is loaded through IOCTLs.
Wait, is it failed on the DriverEntry part? HyperDbg doesn't load its driver on DriverEntry. The VT-x part is loaded through IOCTLs. -
let me see
-
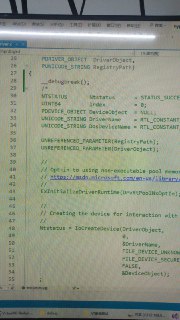
I find it.
-
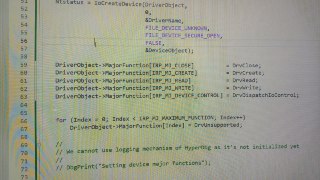
IoCreateDevice
-
-
this is ok
-
-
this is not ok
-
I found the problem.
-
-
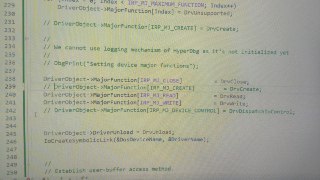
Plus this
-
 You mean once you remove UNREFERENCED_PARAMETER it works?
You mean once you remove UNREFERENCED_PARAMETER it works? -
add
-
but,DrvCreate and DrvDispatchIoControl ,is not ok
-
-
 This is really weird. I don't have any idea what's going on there. Because this seems to be a problem with Windows loading its driver rather than HyperDbg routines. 🤔
This is really weird. I don't have any idea what's going on there. Because this seems to be a problem with Windows loading its driver rather than HyperDbg routines. 🤔 - 02 February 2024 (1 messages)
-
Joined.
- 04 February 2024 (3 messages)
-
-
 13th gen intel still seems to have performance degradation
13th gen intel still seems to have performance degradation -
hi, I'm curious about how you guys found that the problem was from mtrr for 13th intel cpu?
since I cannot reproduce the error on my 10th cpu, I didn't notice the error existed
or is there intel manual for 13th cpu ? - 05 February 2024 (3 messages)
-
 I didn't reproduce the problem myself since I have a 12th gen processor, but usually if you get random crashes in the system usually on instructions where there is no reason for a VM-exit, then you can conclude that there is something wrong with EPT.
I didn't reproduce the problem myself since I have a 12th gen processor, but usually if you get random crashes in the system usually on instructions where there is no reason for a VM-exit, then you can conclude that there is something wrong with EPT. -
 And since we had a recent patch for MTRRs, then probably that's caused by MTRRs as I mentioned in the GitHub issue.
And since we had a recent patch for MTRRs, then probably that's caused by MTRRs as I mentioned in the GitHub issue. -
 What kind of behavior did you observe? Is there any crash? Or just make system slower?
What kind of behavior did you observe? Is there any crash? Or just make system slower? - 06 February 2024 (22 messages)
-
 I've had a number of crashes when using monitor, but that's when process crashes and I get some injected interrupt errors. The system is overall less responsive and slower once vmm is loaded and the behaviour persists on unload. I'm running an underclocked(!) i9 13900k
I've had a number of crashes when using monitor, but that's when process crashes and I get some injected interrupt errors. The system is overall less responsive and slower once vmm is loaded and the behaviour persists on unload. I'm running an underclocked(!) i9 13900k -
 I'm running on host in VMI mode.
I'm running on host in VMI mode. -
 I'm using the latest build. I also compiled with the usermode debugger, but it seems unstable so I haven't been using it much. I've also had issue with pa2va crashing my system, but that was due to incorrect usage (ntoskrnl address attempted to be resolved in a process)
I'm using the latest build. I also compiled with the usermode debugger, but it seems unstable so I haven't been using it much. I've also had issue with pa2va crashing my system, but that was due to incorrect usage (ntoskrnl address attempted to be resolved in a process) -
 Wait, I just update the !monitor command to fix a design issue on v0.8.1. I made tens of tests with different conditions on both user-mode and kernel-mode on my system and it was perfectly fine.
Wait, I just update the !monitor command to fix a design issue on v0.8.1. I made tens of tests with different conditions on both user-mode and kernel-mode on my system and it was perfectly fine. -
 Could you provide me a way that I can crash the system by using !monitor command? I mean is it reproducible?
Could you provide me a way that I can crash the system by using !monitor command? I mean is it reproducible? -
 Actually, the !monitor command has an issue that I figured it out last week.
Actually, the !monitor command has an issue that I figured it out last week.
If the user hooks a range of memory within two or more page boundaries then the second page entry's physical address might be lower than the first page's physical address entry (PFN) and in these cases as we check the hooking physical address to see whether it's within the hooking range or not then HyperDbg fails.
To solve this issue, I changed the event triggering mechanism to only trigger the event if a unique TAG of the target page is observed.
Remember we cannot change based on the virtual address range because the memory might be mapped in different addresses in different processes so each check should be performed based on the physical address range. -
 This is the problem that is solved last week. I can't think of way, this new approach (based on TAG) could be failed. If you can crash HyperDbg on !monitor then it's probably a stupid programming bug rather than a critical designing problem. 🤔
This is the problem that is solved last week. I can't think of way, this new approach (based on TAG) could be failed. If you can crash HyperDbg on !monitor then it's probably a stupid programming bug rather than a critical designing problem. 🤔 -
 monitor r l 8 user_va pid 0n24568 script { printf("%p", @rip);}
monitor r l 8 user_va pid 0n24568 script { printf("%p", @rip);} -
 I'm running win11 if that matters, I'm also having problems loading symbols.
I'm running win11 if that matters, I'm also having problems loading symbols. -
 It can't download some system ones and gives me error 2.
It can't download some system ones and gives me error 2. -
 Does it cause crash on all user-mode processes? 😳
Does it cause crash on all user-mode processes? 😳 -
 Error 2?
Error 2? -
 Haven't tested more, but the one I'm testing is unprotected.
Haven't tested more, but the one I'm testing is unprotected. -
 it doesn't always crash
it doesn't always crash -
 but if the program crashes, then the hv crashes after some time unless i unregister the event
but if the program crashes, then the hv crashes after some time unless i unregister the event -
 yes, failed to load symbols (2)
yes, failed to load symbols (2) -
 in src its getlasterror
in src its getlasterror -
 Can you also test it with HyperDbg v0.8.0 (not v0.8.1)?
Can you also test it with HyperDbg v0.8.0 (not v0.8.1)?
I'm just gonna see whether it's the new design that is problematic or it's something else. -
 it occured on both
it occured on both -
 I had 0.8 and upgraded to 0.8.1
I had 0.8 and upgraded to 0.8.1 -
 So, it should be a new error. I try to reproduce the error using your script tomorrow. But, if you could find a way to deterministically reproduce the error (like a condition that always crashes the debugger), pls let me know.
So, it should be a new error. I try to reproduce the error using your script tomorrow. But, if you could find a way to deterministically reproduce the error (like a condition that always crashes the debugger), pls let me know. -
 Will do!
Will do! - 07 February 2024 (3 messages)
-
Joined.
-
怎么翻译成中文,我看不懂英文
-
Joined.
- 08 February 2024 (2 messages)
-

-
你们编译的驱动能正常加载么?
- 10 February 2024 (17 messages)
-
-
-
 Hey, just a friendly reminder to please use English in the group chat so that everyone can understand and participate. Thank you!
Hey, just a friendly reminder to please use English in the group chat so that everyone can understand and participate. Thank you! -
 Joined.
Joined. -
 hey there, I think this might be an issue but I'm not sure about it. when an ept violation occurs and a guest wants to write to the target page, we will put the original pfn of the page, but then this means that we will not write to our "shadow" page containing our hook. I think the hook can be detected this way, please correct me if I'm wrong
hey there, I think this might be an issue but I'm not sure about it. when an ept violation occurs and a guest wants to write to the target page, we will put the original pfn of the page, but then this means that we will not write to our "shadow" page containing our hook. I think the hook can be detected this way, please correct me if I'm wrong -
 Joined.
Joined. -
Joined.
-
 I suppose you mean !epthook or !epthook2 (not !monitor), usually executable pages are not writable, so one can easily check whether the page is writable or not, if writable then it means that it can be modify.
I suppose you mean !epthook or !epthook2 (not !monitor), usually executable pages are not writable, so one can easily check whether the page is writable or not, if writable then it means that it can be modify. -
 In either case, !epthook is supposed to let the page perform its normal execution (read/write), but you can easily modify this default behavior in HyperDbg (just need to mask page write attrib from the EPT PT Entry).
In either case, !epthook is supposed to let the page perform its normal execution (read/write), but you can easily modify this default behavior in HyperDbg (just need to mask page write attrib from the EPT PT Entry). -
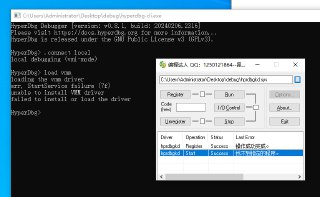
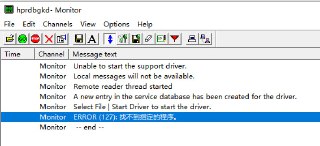
我的咋是加载的问题,加载的时候报错 0x7f
-
-
-
是不是很诡异
-
 作者建议使用英文交流,这样可以保证大家都可以看懂。
作者建议使用英文交流,这样可以保证大家都可以看懂。
看不懂英文的,可以去使用翻译软件或者GPT进行翻译。 -
Loading Driver, Error: 0x7F..... Why?
-
 what if our page is executable and writeable? if guest will attempt writing to our hooked page, then it will end up writing only to the original page because when ViolationQualification is ReadAccess or WriteAccess, we will put original page, and if it's ExecuteAccess, then we will put another page with our own code
what if our page is executable and writeable? if guest will attempt writing to our hooked page, then it will end up writing only to the original page because when ViolationQualification is ReadAccess or WriteAccess, we will put original page, and if it's ExecuteAccess, then we will put another page with our own code -
 Is it possible to run !track in a script?
Is it possible to run !track in a script? - 11 February 2024 (23 messages)
-
 That's also possible but the caveat is what if the target application changes the code and expects another behavior? I mean in this way, they could change the code and expect the code to be modified. 🤔
That's also possible but the caveat is what if the target application changes the code and expects another behavior? I mean in this way, they could change the code and expect the code to be modified. 🤔 -
 It is possible, I remember I add the same feature for the script engine as an export to the instrumentation step-in (the 'i' command). But I didn't document it. Let see if I remember how I configured it.
It is possible, I remember I add the same feature for the script engine as an export to the instrumentation step-in (the 'i' command). But I didn't document it. Let see if I remember how I configured it. -
 It's the '!trace' command and you should use with the following functions:
It's the '!trace' command and you should use with the following functions:
event_trace_step event_trace_step_in event_trace_step_out event_trace_instrumentation_step event_trace_instrumentation_step_in -
 But remember, it triggers event for each instruction (not just 'call's and 'ret's), you should filter the instructions (it's exactly the way that the actual '!track' is implemented).
But remember, it triggers event for each instruction (not just 'call's and 'ret's), you should filter the instructions (it's exactly the way that the actual '!track' is implemented). -
 Please avoid mentioning specific commercial program names to prevent any potential issues.
Please avoid mentioning specific commercial program names to prevent any potential issues.
But as a general answer to your question, you can use the '!monitor' command combined with the short-circuiting mechanism to prevent memory read by any specific process.
Please check:
https://docs.hyperdbg.org/commands/extension-commands/monitor#short-circuiting
Here's an example:
https://docs.hyperdbg.org/tips-and-tricks/misc/event-short-circuiting#example-1!monitor (monitor read/write/execute to a range of memory)Description of the '!monitor' command in HyperDbg.
-
 You could also bypass (prevent) memory execution with the same command which also halts (pauses) the user-mode or kernel-mode execution of any specific process.
You could also bypass (prevent) memory execution with the same command which also halts (pauses) the user-mode or kernel-mode execution of any specific process. -
 Hey, bro this is legit software, if u ask questions about illegally use, u might be kicked and banned
Hey, bro this is legit software, if u ask questions about illegally use, u might be kicked and banned -
 Don’t put others and this group chat under legal risk
Don’t put others and this group chat under legal risk -
 @gamework888 will modify his/her question to avoid problems.
@gamework888 will modify his/her question to avoid problems. -
 There is no inherent legal risk as it's not a commercial software protector and the question doesn't pose a stance of building distributed circumvention software, but it's better to ask a technical question instead of a direct target.
There is no inherent legal risk as it's not a commercial software protector and the question doesn't pose a stance of building distributed circumvention software, but it's better to ask a technical question instead of a direct target. -
 This could cause troubles to sina
This could cause troubles to sina -
 no. but it's always better to keep discussions whitehat, i agree on that.
no. but it's always better to keep discussions whitehat, i agree on that. -
 Sina is working internationally, this can be risks for him, so keep these private at least
Sina is working internationally, this can be risks for him, so keep these private at least -
 Would it also work fine in VMI mode?
Would it also work fine in VMI mode? -
 also I don't know if you remember our conversation about physical COM debugging from a couple months ago, but I'm pretty sure the issue was caused by the USB-COM cable extension, I will be buying a laptop with a direct port and I'll try to give feedback on whether that will work fine, not sure if you verified already
also I don't know if you remember our conversation about physical COM debugging from a couple months ago, but I'm pretty sure the issue was caused by the USB-COM cable extension, I will be buying a laptop with a direct port and I'll try to give feedback on whether that will work fine, not sure if you verified already -
 you're right, for example, what if someone writes opcode "0xCC" to our hooked page and then expects their exception handler to catch it, but it never catches it
you're right, for example, what if someone writes opcode "0xCC" to our hooked page and then expects their exception handler to catch it, but it never catches it -
 Yes, it should work on VMI Mode, but it's not yet well-tested but it works. If it doesn't satisfy your needs I suggest to modify the source code, just follow the '!track' command in the kernel and you can easily write C codes to modify its behavior.
Yes, it should work on VMI Mode, but it's not yet well-tested but it works. If it doesn't satisfy your needs I suggest to modify the source code, just follow the '!track' command in the kernel and you can easily write C codes to modify its behavior. -
 That's great! Keep me informed. 👍
That's great! Keep me informed. 👍 -
 Yes, good catch. We cannot handle these cases in HyperDbg right now, maybe we should add somewhere that if some programs inject 0xcc into the memory and after triggering hooks, inject a #BP into the guest.
Yes, good catch. We cannot handle these cases in HyperDbg right now, maybe we should add somewhere that if some programs inject 0xcc into the memory and after triggering hooks, inject a #BP into the guest. -
 so, is there a way to perform a write operation on both original and hook pages inside of an ept hook handler?
so, is there a way to perform a write operation on both original and hook pages inside of an ept hook handler? -
 What do you mean by both original and Hook pages? 🤔
What do you mean by both original and Hook pages? 🤔 -
 by original page I mean the target page which we hook, by hook page I mean "hidden" page which is swapped when ViolationQualification is ExecuteAccess
by original page I mean the target page which we hook, by hook page I mean "hidden" page which is swapped when ViolationQualification is ExecuteAccess -
 if ViolationQualification is WriteAccess or ReadAccess then PageFrameNumber will be the original page, otherwise if it is ExecuteAccess it will be a fake page.
if ViolationQualification is WriteAccess or ReadAccess then PageFrameNumber will be the original page, otherwise if it is ExecuteAccess it will be a fake page.
sorry if this is not very clear, hope you understand what I'm trying to say - 12 February 2024 (10 messages)
-
sorry
-
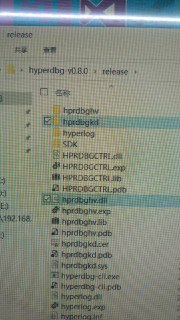
I want to sign the driver file, can you tell me which file it is?
-
I have signed the hprdbgkd.sys file, but I still get the above prompt?
-
 Well, it's only true for !epthook and !epthook (not monitor), in these cases, it's not possible to write on the hooked page which can be detected by an anti-hypervisor method.
Well, it's only true for !epthook and !epthook (not monitor), in these cases, it's not possible to write on the hooked page which can be detected by an anti-hypervisor method. -
 The !monitor on the other hand won't have a separate page.
The !monitor on the other hand won't have a separate page. -
 You need to sign: hprdbghv.dll hprdbgkd.sys hyperlog.dll and kdserial.dll.
You need to sign: hprdbghv.dll hprdbgkd.sys hyperlog.dll and kdserial.dll. -
When I load vmm then BSOD with "clock_watch_timeout", how to fix it?
-
I have enabled CPU virtualization.
-
 Can you provide your processor generation and Windows version?
Can you provide your processor generation and Windows version? -

- 14 February 2024 (1 messages)
-
 Joined.
Joined. - 15 February 2024 (1 messages)
-
- 16 February 2024 (1 messages)
-
Joined.
- 19 February 2024 (5 messages)
-
 The HyperDbg course is now accessible on YouTube. For the most comprehensive experience, including full lab instructions, please utilize it at https://ost2.fyi/Dbg3301. ✨
The HyperDbg course is now accessible on YouTube. For the most comprehensive experience, including full lab instructions, please utilize it at https://ost2.fyi/Dbg3301. ✨
This tutorial will guide you through the initial steps of using HyperDbg, covering essential concepts, principles, and debugging functionalities as well as numerous reverse engineering methods achievable by using HyperDbg, along with practical and real-world examples.
Check it out here: 🔗 https://www.youtube.com/watch?v=RDlp0PCFgxI&list=PLUFkSN0XLZ-kF1f143wlw8ujlH2A45nZY
Slides are available at: https://gitlab.com/opensecuritytraining/dbg3301_hyperdbg_slides_and_filesDebuggers 3301: HyperDbgThis class teaches you how to use HyperDbg, a virtualization-based debugger.
-
 None
None -
 does the hyperdbg support the intel pt?
does the hyperdbg support the intel pt? -
 HyperDbg is designed with a focus on using modern hardware technologies to provide new features to the debuggers' world. It operates on top of Windows by virtualizing an already running system using Intel VT-x and Intel PT.
HyperDbg is designed with a focus on using modern hardware technologies to provide new features to the debuggers' world. It operates on top of Windows by virtualizing an already running system using Intel VT-x and Intel PT. -
 thanks, i found it
thanks, i found it - 20 February 2024 (1 messages)
-
 Joined.
Joined. - 21 February 2024 (1 messages)
-
Joined.
- 24 February 2024 (2 messages)
-

-
 Joined.
Joined. - 27 February 2024 (1 messages)
-
- 28 February 2024 (1 messages)
-
 Joined.
Joined. - 29 February 2024 (1 messages)
-
Joined.
- 01 Feb 2024 (35)
- 02 Feb 2024 (1)
- 04 Feb 2024 (3)
- 05 Feb 2024 (3)
- 06 Feb 2024 (22)
- 07 Feb 2024 (3)
- 08 Feb 2024 (2)
- 10 Feb 2024 (17)
- 11 Feb 2024 (23)
- 12 Feb 2024 (10)
- 14 Feb 2024 (1)
- 15 Feb 2024 (1)
- 16 Feb 2024 (1)
- 19 Feb 2024 (5)
- 20 Feb 2024 (1)
- 21 Feb 2024 (1)
- 24 Feb 2024 (2)
- 27 Feb 2024 (1)
- 28 Feb 2024 (1)
- 29 Feb 2024 (1)