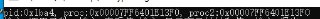- 04 November 2024 (1 messages)
-
Joined.
- 05 November 2024 (5 messages)
-
Will similar ept hooks created by smap and smep perform better?
-
Joined.
-
 Not sure if I understand the question. What do you mean by smap and smep? If you're talking about CPU features to prevent access/exec user code from supervisor, then how could it be related to EPT hooks? 🤔
Not sure if I understand the question. What do you mean by smap and smep? If you're talking about CPU features to prevent access/exec user code from supervisor, then how could it be related to EPT hooks? 🤔 -
I mean this : https://github.com/brew02/budgeteptGitHub - brew02/BudgetEPT: Create stealthy, inline, EPT-like hooks using SMAP and SMEP
Create stealthy, inline, EPT-like hooks using SMAP and SMEP - brew02/BudgetEPT
-
 From what I see in the source code (might be wrong), I could assume that they are some smap preventions for a granularity of one page. If that's the case, why not just using the page table attributes instead of smap or smep? 🤔
From what I see in the source code (might be wrong), I could assume that they are some smap preventions for a granularity of one page. If that's the case, why not just using the page table attributes instead of smap or smep? 🤔 - 06 November 2024 (1 messages)
-
Looks like just another interesting research analysis, far less practical than the current epthook
- 07 November 2024 (1 messages)
-
- 08 November 2024 (3 messages)
-
 Joined.
Joined. -

-
 It's not an unconditional VM-exit. HyperDbg doesn't handle it.
It's not an unconditional VM-exit. HyperDbg doesn't handle it. - 09 November 2024 (15 messages)
-
-
-
 The second address could not be greater than the first address.
The second address could not be greater than the first address. -
 You could also use 'l <size>' if it's not convenient to find the second address.
You could also use 'l <size>' if it's not convenient to find the second address. -
what is the maximum range that can be set in !monitor
-
 Theoretically, there is no limitation for it, but of course if you put a monitor on ~100MB of RAM, HyperDbg will have a hard time interpreting VM-exits in your computer. 😅
Theoretically, there is no limitation for it, but of course if you put a monitor on ~100MB of RAM, HyperDbg will have a hard time interpreting VM-exits in your computer. 😅 -
 Just keep in mind that the '!monitor' command in the Debugger mode (not in VMI mode) needs to have all of the page entries to be valid and available in the RAM. If it's not available (i.e., it's paged out or never paged in), then HyperDbg will show you an error and instruct you to use the '.pagein' command to force Windows to bring your address range into the memory.
Just keep in mind that the '!monitor' command in the Debugger mode (not in VMI mode) needs to have all of the page entries to be valid and available in the RAM. If it's not available (i.e., it's paged out or never paged in), then HyperDbg will show you an error and instruct you to use the '.pagein' command to force Windows to bring your address range into the memory. -
 I see people usually use this HyperDbg feature to monitor the execution in a section of a PE. If you want to do this, make sure that Windows has enough RAM so it won't page-out unused PE pages to the disk. HyperDbg won't check for this kind of situation, which might produce false positive results.
I see people usually use this HyperDbg feature to monitor the execution in a section of a PE. If you want to do this, make sure that Windows has enough RAM so it won't page-out unused PE pages to the disk. HyperDbg won't check for this kind of situation, which might produce false positive results. -
everything is a little simpler, I would like to track calls inside the text ntoskrnl section)))
-
-
 The $context is a pseudo-register, not a constant. It displays the address currently being modified or executed, rather than the address attempting to read, write, or call it. In those cases, you’ll need to check the stack to identify which address was pushed there.
The $context is a pseudo-register, not a constant. It displays the address currently being modified or executed, rather than the address attempting to read, write, or call it. In those cases, you’ll need to check the stack to identify which address was pushed there. -
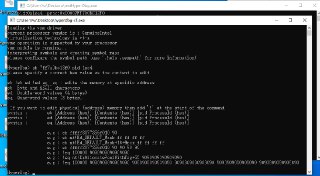
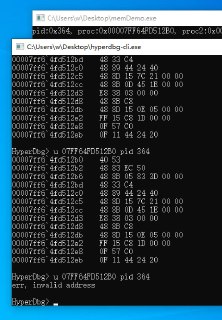
1: kHyperDbg> !monitor r fffff80441590000 fffff80442200000
err, invalid address (c0000005)
address may be paged-out or unavailable on the page table due to 'demand paging'
please refer to https://docs.hyperdbg.org/tips-and-tricks/considerations/accessing-invalid-address for further informationAccessing Invalid Address | HyperDbg DocumentationConsiderations for accessing memory in different modes
-
-
 Yes, as I mentioned earlier, pages should be available in the memory for the !monitor command since this command works on physical addresses. Follow the instructions (the documentation link) to fix it.
Yes, as I mentioned earlier, pages should be available in the memory for the !monitor command since this command works on physical addresses. Follow the instructions (the documentation link) to fix it. -
 [matrix] <pr0xy101 (@pr0xy101:matrix.org)> hello, can i debug easy anti-cheat using hyperdbg?
[matrix] <pr0xy101 (@pr0xy101:matrix.org)> hello, can i debug easy anti-cheat using hyperdbg? - 10 November 2024 (3 messages)
-
0: kHyperDbg> prealloc regular-event 1000000000
the requested pools are allocated and reserved
fffff805`3ad61292 0F 01 C1 vmcall
1: kHyperDbg> prealloc monitor 1000000000
the requested pools are allocated and reserved
fffff805`3ad61292 0F 01 C1 vmcall
0: kHyperDbg> !monitor r fffff80521600000+(0x140200000-0x140001000) fffff80521600000+(0x1405CB000-0x140001000)
err, the pre-allocated buffer is empty, usually this buffer will be filled at the next IOCTL when the debugger is continued (c0000023)
please visit the documentation for the 'prealloc' command or use '.help prealloc' to to reserve more pre-allocated pools
Do you need more pools? ;))) -
 Are you sure you're computing it correctly? It seems that you're trying to hook somewhere in the kernel, but the results of the expressions are in the user-mode?
Are you sure you're computing it correctly? It seems that you're trying to hook somewhere in the kernel, but the results of the expressions are in the user-mode? -

- 11 November 2024 (1 messages)
-
for my vmware(windows 10 18363) is not working !monitor for ntoskrnl. Using the command !monitor is getting error 0x00005c (pagein). By entering .pagein commands for ntoskrnl addresses, the computer (vmware) restarts (((
- 12 November 2024 (9 messages)
-
 This is expected. The '.pagein' command injects a #PF (page-fault) into the system to force Windows to bring the page into the RAM.
This is expected. The '.pagein' command injects a #PF (page-fault) into the system to force Windows to bring the page into the RAM. -
 If the page is already in the RAM or it's available, Windows doesn't expect to receive a page-fault and what happens here? Windows assumes that something went wrong as the #PF is generated by CPU by error. Which might lead to double/triple-fault and break the system (restart).
If the page is already in the RAM or it's available, Windows doesn't expect to receive a page-fault and what happens here? Windows assumes that something went wrong as the #PF is generated by CPU by error. Which might lead to double/triple-fault and break the system (restart). -
 You should be cautious when using the '.pagein' command. If you use it on a wide-range of RAM, usually such errors will happen because somewhere in the middle of the range might be already available into RAM and it will cause system crash as #PF is not expected.
You should be cautious when using the '.pagein' command. If you use it on a wide-range of RAM, usually such errors will happen because somewhere in the middle of the range might be already available into RAM and it will cause system crash as #PF is not expected. -
 Guys, just because HyperDbg’s '!monitor' command can technically monitor unlimited address ranges doesn’t mean you can monitor any memory range you want. So let’s not go wild, alright? 😅
Guys, just because HyperDbg’s '!monitor' command can technically monitor unlimited address ranges doesn’t mean you can monitor any memory range you want. So let’s not go wild, alright? 😅
https://docs.hyperdbg.org/commands/extension-commands/monitor -
 It refers to you @instw0 😅
It refers to you @instw0 😅 -
what can go wrong
-

-
-
 There is a limit to the number of '!epthook's you can place on a single 4 KB page. If you reach this limit, HyperDbg will display an error message tells you to adjust the constant and recompile HyperDbg. However, there’s no restriction on the number of !epthook`s across different pages. Essentially, there’s no practical limit, but be cautious not to overload the system with too many breakpoints!
There is a limit to the number of '!epthook's you can place on a single 4 KB page. If you reach this limit, HyperDbg will display an error message tells you to adjust the constant and recompile HyperDbg. However, there’s no restriction on the number of !epthook`s across different pages. Essentially, there’s no practical limit, but be cautious not to overload the system with too many breakpoints! - 13 November 2024 (151 messages)
-
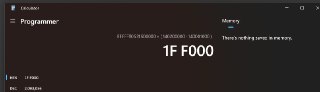
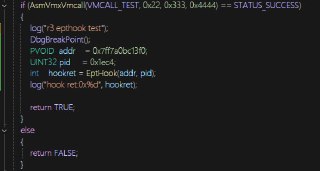
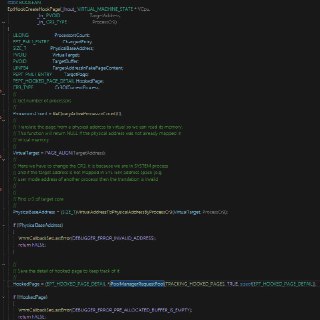
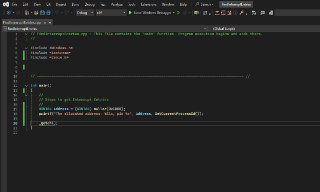
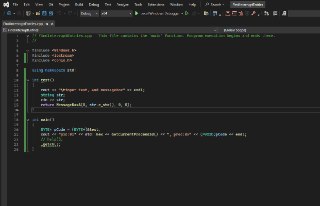
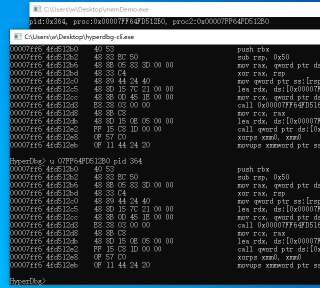
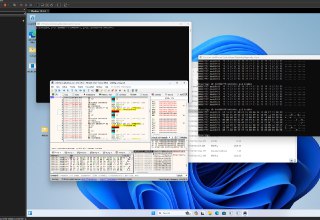
 guys, I want to test r3 epthook. The code is shown in the following image, This test runs on non-root mode
guys, I want to test r3 epthook. The code is shown in the following image, This test runs on non-root mode -
 Now I have encountered a problem, the function inside the function does not return (BroadcastEnableBreakpointExitingOnExceptionBitmapAllCores)
Now I have encountered a problem, the function inside the function does not return (BroadcastEnableBreakpointExitingOnExceptionBitmapAllCores) -
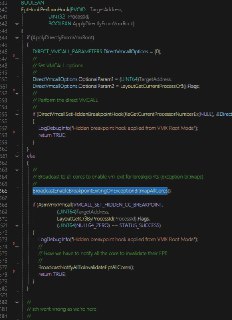
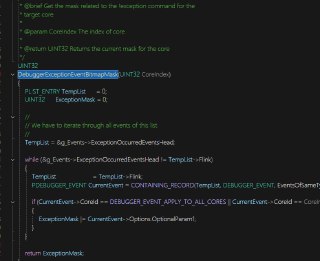
 After debugging, I found that it is caused by the following function
After debugging, I found that it is caused by the following function -
 When I tried to skip the BroadcastEnabled BreakpointExitingOnExceptionBitmapAllCores function and observe the program's response, the second error occurred.
When I tried to skip the BroadcastEnabled BreakpointExitingOnExceptionBitmapAllCores function and observe the program's response, the second error occurred.
The PoolManageRequestPool function returns 0. -
 What should I do now? 😢
What should I do now? 😢 -
 Can you explain about the environment? Like are you setting an EPT hook from a kernel driver and you're using the 'Hyperhv' project as an imported module? Or is it coming from the hyperdbg-cli.exe (libhyperdbg.dll)?
Can you explain about the environment? Like are you setting an EPT hook from a kernel driver and you're using the 'Hyperhv' project as an imported module? Or is it coming from the hyperdbg-cli.exe (libhyperdbg.dll)? -
 I am using hyperdbg-cli.exe, but I have made some minor modifications to hyperhv
I am using hyperdbg-cli.exe, but I have made some minor modifications to hyperhv -

-
 Something is wrong here. The following combination of code will crash HyperDbg, you're modifying the wrong place.
Something is wrong here. The following combination of code will crash HyperDbg, you're modifying the wrong place. -
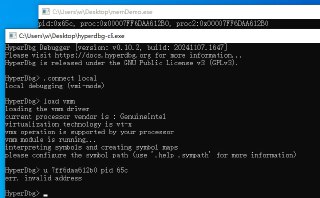
 Are you running HyperDbg in VMI-mode? or the Debugger-mode?
Are you running HyperDbg in VMI-mode? or the Debugger-mode? -
 .connect local
.connect local -
 load vmm
load vmm -
 It's VMI-mode. Now, are you trying to put an EPT hook the user-mode of another process?
It's VMI-mode. Now, are you trying to put an EPT hook the user-mode of another process? -
 Yes, that's what I want to do now
Yes, that's what I want to do now -
 What is the handler of the breakpoint? Is WinDbg handling the breakpoint? Like are you running it in a virtual machine (VMware) or in the baremetal?
What is the handler of the breakpoint? Is WinDbg handling the breakpoint? Like are you running it in a virtual machine (VMware) or in the baremetal? -
 I didn't do any additional processing, I just wanted to observe the phenomenon of EPT working
I didn't do any additional processing, I just wanted to observe the phenomenon of EPT working -
 Then, why don't you use the command line (scripts) for that?
Then, why don't you use the command line (scripts) for that?
https://docs.hyperdbg.org/commands/extension-commands/epthook!epthook (hidden hook with EPT - stealth breakpoints) | HyperDbg DocumentationDescription of the '!epthook' command in HyperDbg.
-
 Take a look at this video:
Take a look at this video:
https://www.youtube.com/watch?v=tjsFRBFGis4&ab_channel=OpenSecurityTraining2Dbg3301: HyperDbg 05 01 Intro and Classic Hidden HooksView the full free MOOC at https://ost2.fyi/Dbg3301. This course is an introductory guide to HyperDbg debugger, guiding you through the initial steps of using HyperDbg, covering essential concepts, principles, debugging functionalities, along with practical examples and numerous reverse engineering methods that are unique to HyperDbg. Whether you have an interest in reverse engineering or seek to elevate your reverse engineering skills with hypervisor-assisted approaches, this course provides a solid foundation for starting your journey.
-
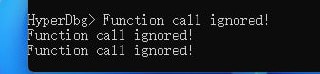
 This command has no effect.😢
This command has no effect.😢 -
 What was the command? Maybe you wrote an incorrect script.
What was the command? Maybe you wrote an incorrect script. -
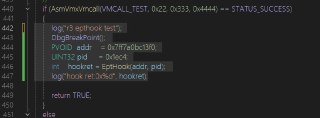
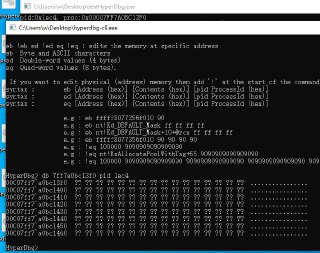
 !epthook 7ff7a0bc13f0 pid 1ec4 asm code {ret} this is my code.
!epthook 7ff7a0bc13f0 pid 1ec4 asm code {ret} this is my code. -
 This code, won't do anything!
This code, won't do anything! -
 The 'ret' is executed in the VMX-root mode as additional assembly code, it's not running in the target executable file!
The 'ret' is executed in the VMX-root mode as additional assembly code, it's not running in the target executable file! -
 Are you trying to bypass a 'CALL' instruction?
Are you trying to bypass a 'CALL' instruction? -
 Yes, I tried to make a function return directly
Yes, I tried to make a function return directly -
 okay, let me find the correct example. I'll send it here in a bit.
okay, let me find the correct example. I'll send it here in a bit. -
 i love you , bro 😂
i love you , bro 😂 -
 You need a script like this:
You need a script like this:
!epthook 7ff7a0bc13f0 pid 1ec4 script {
@rip = poi(@rsp); // pop the return address from stack
@rsp = @rsp + 8; // adjust the stack
printf("Function call ignored!\n");
} -
 Put it on the target function that is called (not the 'CALL' instruction that tries to call the target function).
Put it on the target function that is called (not the 'CALL' instruction that tries to call the target function). -
 thank you so much
thank you so much -

-
 vmware 17.5.1
vmware 17.5.1 -
 Is the process id still valid?
Is the process id still valid? -
 I used 1 CPU core
I used 1 CPU core -
 pid 1ec4
pid 1ec4 -
 I mean this one.
I mean this one. -
 yes, pid still valid
yes, pid still valid -
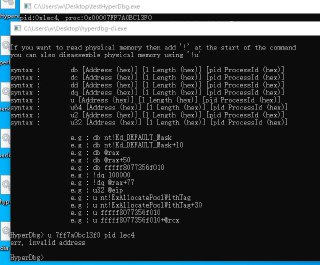
 Could you check it with:
Could you check it with:
eb 7ff7a0bc13f0 pid 1ec4 -
 Does it show anything?
Does it show anything? -

-
 Oh sorry
Oh sorry -
 db instead of eb
db instead of eb -
 db 7ff7a0bc13f0 pid 1ec4
db 7ff7a0bc13f0 pid 1ec4 -
 My mistake.
My mistake. -
 This one is the correct command.
This one is the correct command. -
 It seems that the process's memory cannot be read
It seems that the process's memory cannot be read -

-
 The target is not valid?
The target is not valid? -
 yes, but ... emm...... let me see
yes, but ... emm...... let me see -
 I don't know what happened, it used to work😂
I don't know what happened, it used to work😂 -
 The address is invalid (probably because of KASLR?).
The address is invalid (probably because of KASLR?). -
 I don't know.
I don't know.
I will try restarting VMware first, and then I will try to solve the problem with invalid address -
 thanks
thanks -
 Let me know, what happened if you find a way around it.
Let me know, what happened if you find a way around it. -
 ok
ok -
 This code can only work on the first attempt
This code can only work on the first attempt
The second time it stopped working -
 Let me check it on my system.
Let me check it on my system. -
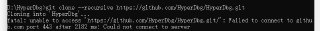
 maybe i should pull HyperDbg from GhuHub again?
maybe i should pull HyperDbg from GhuHub again? -
 Which version of HyperDbg do you use?
Which version of HyperDbg do you use? -
 0.10.2
0.10.2 -
 Nope, no need to pull. Give me a bit to test it.
Nope, no need to pull. Give me a bit to test it. -
 👍
👍 -
 I test it with a custom application:
I test it with a custom application: -

-
 Is there any anti-debugging method in your target application that leads to this behavior?
Is there any anti-debugging method in your target application that leads to this behavior? -

-
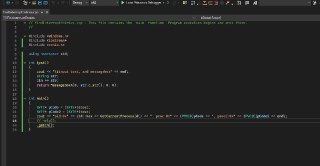
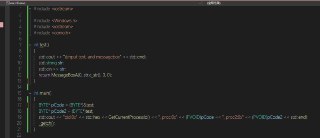
 this is my demo
this is my demo -
 what is &test?
what is &test? -

-
 Could you please copy-paste these two functions here?
Could you please copy-paste these two functions here? -
 I'm gonna test it.
I'm gonna test it. -
 functions?
functions? -
 test() and main()
test() and main() -
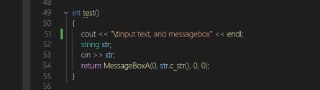
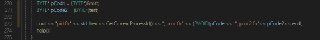
 int test()
int test()
{
cout << "\tinput text, and messagebox" << endl;
string str;
cin >> str;
return MessageBoxA(0, str.c_str(), 0, 0);
} -
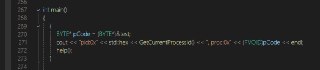
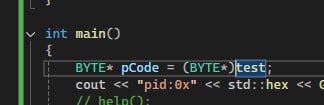
 int main()
int main()
{
{
BYTE* pCode = (BYTE*)&test;
cout << "pid:0x" << std::hex << GetCurrentProcessId() << ", proc:0x" << (PVOID)pCode << endl;
help();
} -
 Thanks, lemme check it
Thanks, lemme check it -
 I don't think it has anything to do with functions
I don't think it has anything to do with functions -
 Can you reproduce this phenomenon?
Can you reproduce this phenomenon? -

-

-
 I think the problem is not because of HyperDbg as it works for me.
I think the problem is not because of HyperDbg as it works for me. -
 Yes, I think so too
Yes, I think so too -
 It's probably because at some points the pCode is no longer valid.
It's probably because at some points the pCode is no longer valid. -
 Perhaps I accidentally modified the hyperhv code
Perhaps I accidentally modified the hyperhv code -
 You can remove your modifications and recompile HyperDbg.
You can remove your modifications and recompile HyperDbg. -
 ok, i do it now
ok, i do it now -
 Other than that, shouldn't it be like this?
Other than that, shouldn't it be like this? -
 I mean I removed the the '&'.
I mean I removed the the '&'. -
 Because you're creating a reference to the address of the 'test'. It's not the address of the 'test'. Am I right?
Because you're creating a reference to the address of the 'test'. It's not the address of the 'test'. Am I right? -
 Could you check it as well?
Could you check it as well? -
 ok
ok -
 i test remove &, but I don't think this has anything to do with it
i test remove &, but I don't think this has anything to do with it -

-

-
 🤣
🤣 -
 Fixed?
Fixed? -

-
 Why these two variables are the same? Is there any optimization? 😳
Why these two variables are the same? Is there any optimization? 😳 -
 I don't know how to say this
I don't know how to say this -
 There is no problem with using&for functions
There is no problem with using&for functions -
 Maybe we'll have to test it later, con't connect to github.
Maybe we'll have to test it later, con't connect to github. -
 😂
😂 -

-

-
 The only difference between your code and my code is that I commented the 'help' function. Could you add a '_getch()' before the help function and try it again?
The only difference between your code and my code is that I commented the 'help' function. Could you add a '_getch()' before the help function and try it again? -
 of course
of course -
 Alternatively, I can rewrite a clean demo
Alternatively, I can rewrite a clean demo -

-
 let me try again
let me try again -

-
 I just restarted the system in VMware
I just restarted the system in VMware -

-
 i do nothing
i do nothing -
 Did you add _getch() to your code?
Did you add _getch() to your code? -

-
 🤔🤔
🤔🤔 -
 I switched to Win11 and tried again
I switched to Win11 and tried again -
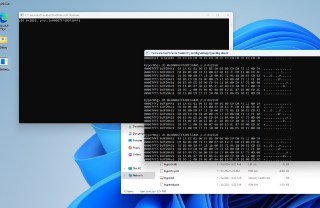
 I test this code one hundred time, it's still valid on my system. It's really weird.
I test this code one hundred time, it's still valid on my system. It's really weird. -
 Maybe you should try my exe
Maybe you should try my exe -
 Wait a moment, I'll try Win11
Wait a moment, I'll try Win11 -
 Currently, it can work on Win11
Currently, it can work on Win11 -
 Okay, but on the Windows 10 where it didn't work. Is it a very old (before meltdown) processor?
Okay, but on the Windows 10 where it didn't work. Is it a very old (before meltdown) processor? -
 no, it is 14900k
no, it is 14900k -
 Intel(R) Core(TM) i9-14900K 3.20 GHz
Intel(R) Core(TM) i9-14900K 3.20 GHz -
 So, it worked on your Windows 11 machine and didn't work on Windows 10 machine? Am I right?
So, it worked on your Windows 11 machine and didn't work on Windows 10 machine? Am I right? -
 yes , you are right
yes , you are right -
 10.0.19045.2486
10.0.19045.2486 -
 This is the version number of Win10
This is the version number of Win10 -
 That's super weird. I have a Win 10 here, I'm gonna test on it too.
That's super weird. I have a Win 10 here, I'm gonna test on it too. -
 But, probably, it would take a while. So, meanwhile you could enjoy using HyperDbg on your Win11, meanwhile I try to understand what goes wrong with this command in the Windows 10.
But, probably, it would take a while. So, meanwhile you could enjoy using HyperDbg on your Win11, meanwhile I try to understand what goes wrong with this command in the Windows 10. -
 You have already helped me a lot, thank you for your software, it's great
You have already helped me a lot, thank you for your software, it's great -
 Wait, I think I find the error.
Wait, I think I find the error. -
 great
great -
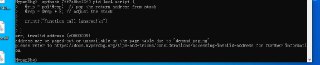
 After some time (around 30 minutes), it started to show the invalid error to me. I checked it with x64dbg as well). I accessed it from x64dbg and the address becomes available in HyperDbg.
After some time (around 30 minutes), it started to show the invalid error to me. I checked it with x64dbg as well). I accessed it from x64dbg and the address becomes available in HyperDbg. -
 So, it seems to be because of Windows paging.
So, it seems to be because of Windows paging. -
 That means the page has been replaced?
That means the page has been replaced? -
 Once the RAM is full, Windows tries to page-out that page and that's why you get this error. (I assume that you didn't give your virtual machine enough RAM?).
Once the RAM is full, Windows tries to page-out that page and that's why you get this error. (I assume that you didn't give your virtual machine enough RAM?). -
 Yes
Yes -
 o... you are right
o... you are right -
 I only allocated 2g to Win10
I only allocated 2g to Win10 -
 Allocated 4G to Win11
Allocated 4G to Win11 -
 Perhaps this is the reason for the problem
Perhaps this is the reason for the problem -
 That's the reason.
That's the reason. -
 Now I will try to allocate more memory
Now I will try to allocate more memory -
 Yes, that's right. After I allocated 4G of memory, the problem disappeared
Yes, that's right. After I allocated 4G of memory, the problem disappeared -
 👍
👍 -
 👍
👍 -
 I have to put a note in the documentation to tell this behavior to the users.
I have to put a note in the documentation to tell this behavior to the users. -
 I can't help but say one more thing, brother. You're amazing
I can't help but say one more thing, brother. You're amazing -

-
Joined.
- 14 November 2024 (1 messages)
-
Joined.
- 15 November 2024 (2 messages)
-
 Joined.
Joined. -
Joined.
- 19 November 2024 (2 messages)
-
-
- 20 November 2024 (6 messages)
-
Joined.
-
 Two new commands are now documented (and merged to the 'dev' branch) for dumping I/O APIC and Local APIC (in both XAPIC and X2APIC mode). If you want to test it before the official v0.11 release, you can switch to the 'dev' branch.
Two new commands are now documented (and merged to the 'dev' branch) for dumping I/O APIC and Local APIC (in both XAPIC and X2APIC mode). If you want to test it before the official v0.11 release, you can switch to the 'dev' branch.
https://docs.hyperdbg.org/commands/extension-commands/apic
https://docs.hyperdbg.org/commands/extension-commands/ioapic!apic (dump local APIC entries in XAPIC and X2APIC modes) | HyperDbg DocumentationDescription of '!apic' command in HyperDbg.
-
 Also, two other new commands for enumerating PCI Express devices + Reading/writing into PCI/PCI-e Config Address Space (CAM) will soon be available.
Also, two other new commands for enumerating PCI Express devices + Reading/writing into PCI/PCI-e Config Address Space (CAM) will soon be available. -
 We're sharing updates on #HyperDbg releases and debugging tips on #Bluesky and #Mastodon too!
We're sharing updates on #HyperDbg releases and debugging tips on #Bluesky and #Mastodon too!
You can also follow us there. 😊
- https://bsky.app/profile/hyperdbg.bsky.social
- https://infosec.exchange/@hyperdbg -

-
Amazing project! Keep it up!
- 21 November 2024 (1 messages)
-
Joined.
- 22 November 2024 (2 messages)
-
 [discord] <adam235513> Hi, Im trying to debug a process with anti debug. So I thought I use HyperDbg to avoid being detecting. So when I start the process in the VM HyperDbg will directly break in the process. When I press `g` it will break on the next instruction ... Is there a way to disable the behavior or at least some kind of logging to see why HyperDbg is breaking ? Is it page guard?!
[discord] <adam235513> Hi, Im trying to debug a process with anti debug. So I thought I use HyperDbg to avoid being detecting. So when I start the process in the VM HyperDbg will directly break in the process. When I press `g` it will break on the next instruction ... Is there a way to disable the behavior or at least some kind of logging to see why HyperDbg is breaking ? Is it page guard?! -
 Once you press 'g' it stops at the PE entrypoint, unless there is an anti debugging method (maybe TLS?) that breaks the debugging?
Once you press 'g' it stops at the PE entrypoint, unless there is an anti debugging method (maybe TLS?) that breaks the debugging? - 23 November 2024 (11 messages)
-
 [discord] <adam235513> Yeah, it has TLS. Can I disable the behavior? It doesn't have to break at the EP. I can set a breakpoint on one of the Windows APIs
[discord] <adam235513> Yeah, it has TLS. Can I disable the behavior? It doesn't have to break at the EP. I can set a breakpoint on one of the Windows APIs -
 It's actually possible but if you could modify the source code (and recompile HyperDbg), but could you run the PE and then attach to it? It would be easier.
It's actually possible but if you could modify the source code (and recompile HyperDbg), but could you run the PE and then attach to it? It would be easier. -
 Or another option that you have is putting some hooks in some APIs or system-calls and intercept it this way. It's probably a better approach.
Or another option that you have is putting some hooks in some APIs or system-calls and intercept it this way. It's probably a better approach. -
 [discord] <adam235513> No, because it directly breaks in HyperDbg even when I don't launch it through hyperdbg. Can modify the code, already compiled it myself
[discord] <adam235513> No, because it directly breaks in HyperDbg even when I don't launch it through hyperdbg. Can modify the code, already compiled it myself -
 What do you mean by "breaks HyperDbg"? Is it something like triggering infinite number of breakpoints?
What do you mean by "breaks HyperDbg"? Is it something like triggering infinite number of breakpoints? -
 [discord] <adam235513> Yes, exactly. After each instruction is executed it breaks. So hyperdbg becomes useless
[discord] <adam235513> Yes, exactly. After each instruction is executed it breaks. So hyperdbg becomes useless -
 [discord] <adam235513> Like a page guard is set on the memory page and hyprdbg is catching the exception
[discord] <adam235513> Like a page guard is set on the memory page and hyprdbg is catching the exception -
 You can disable triggering (intercepting breakpoints by HyperDbg) using this command:
You can disable triggering (intercepting breakpoints by HyperDbg) using this command:
test breakpoint off -
 If you need to disable intercepting traps (single stepping) like #DB, you could use this command:
If you need to disable intercepting traps (single stepping) like #DB, you could use this command:
test trap off -
 [discord] <adam235513> Ok, I will give it a try tomorrow. Thanks
[discord] <adam235513> Ok, I will give it a try tomorrow. Thanks -
 Sure thing. Let me know about the results. If it didn't work, probably there are other options like ignoring exceptions (using the !exception command).
Sure thing. Let me know about the results. If it didn't work, probably there are other options like ignoring exceptions (using the !exception command). - 24 November 2024 (5 messages)
-
 [discord] <adam235513> Test trap works. Now I can attach to the process and break on a Windows API.
[discord] <adam235513> Test trap works. Now I can attach to the process and break on a Windows API. -
 [discord] <adam235513> Thanks a lot
[discord] <adam235513> Thanks a lot -
 [discord] <adam235513> Did you ever thought to put a gdb server into it ? So one can easily attach with IDA?
[discord] <adam235513> Did you ever thought to put a gdb server into it ? So one can easily attach with IDA? -
 Great. 👍
Great. 👍 -
 Nope, unfortunately HyperDbg only uses its custom protocol, not gdb stub.
Nope, unfortunately HyperDbg only uses its custom protocol, not gdb stub. - 26 November 2024 (1 messages)
-
Joined.
- 28 November 2024 (4 messages)
-
Joined.
-
 [discord] <jamlee7879> Hi. What's the working principle of the EPT classic hook? I really can't figure out why a Windows running on a physical machine can also trigger an EPT violation.
[discord] <jamlee7879> Hi. What's the working principle of the EPT classic hook? I really can't figure out why a Windows running on a physical machine can also trigger an EPT violation. -
 [discord] <jamlee7879> How does an EPT violation trigger a VM Exit event? Windows isn't running in a virtual machine. Can't it be handled directly in a driver?
[discord] <jamlee7879> How does an EPT violation trigger a VM Exit event? Windows isn't running in a virtual machine. Can't it be handled directly in a driver? -
 [discord] <jamlee7879> https://tenor.com/view/hot-summer-scary-scared-creepy-gif-17494278817868935582
[discord] <jamlee7879> https://tenor.com/view/hot-summer-scary-scared-creepy-gif-17494278817868935582 - 29 November 2024 (9 messages)
-
 HyperDbg is a bluepill style hypervisor, which means it virtualizes and already running system. Think of it as a system that is running and then you virtualize all system resources (starting from kernel).
HyperDbg is a bluepill style hypervisor, which means it virtualizes and already running system. Think of it as a system that is running and then you virtualize all system resources (starting from kernel). -
 EPT Violation is a form of VM-exit.
EPT Violation is a form of VM-exit. -
 Generally, VT-x is consist of some instructions, which gives you (VMM) the ability to control critical CPU components (like memory, interrupts, IO ports, PCIe bars) by triggering VM-exits.
Generally, VT-x is consist of some instructions, which gives you (VMM) the ability to control critical CPU components (like memory, interrupts, IO ports, PCIe bars) by triggering VM-exits. -
 If you're curious about these topics, you might be interested in checking Hypervisor From Scratch series which describes how HyperDbg works internally:
If you're curious about these topics, you might be interested in checking Hypervisor From Scratch series which describes how HyperDbg works internally:
https://rayanfam.com/tutorials/TutorialsWe write about Windows Internals, Hypervisors, Linux, and Networks.
-
 [discord] <jamlee7879> Yes, I've briefly read through the "Hypervisor From Scratch" series, but I didn't quite understand it. I can't imagine what a bluepill style hypervisor program is like. Here's what I know:
[discord] <jamlee7879> Yes, I've briefly read through the "Hypervisor From Scratch" series, but I didn't quite understand it. I can't imagine what a bluepill style hypervisor program is like. Here's what I know:
1. When the Virtual Machine Monitor (VMM) enters the VMX (Virtual Machine eXtensions) mode, it has already set up the conversions for the Virtual Machine Control Structure (VMCS) and Extended Page Table (EPT).
2. The state of the CPU that enters the operation will be stored in the VMCS. At this time, the virtualized CPU is being used.
3. Then it exits the VMX mode. The code runs on the physical CPU again.
The CPU running in VT (Virtualization Technology) and the physical CPU are like two completely different worlds. Why is it related to the MSR (Model Specific Register) hook? I must have missed some crucial information. -
 It’s the same cpu all the time, it just has different modes of operation. Depending on the mode of execution the CPU has either additional features or otherwise a reduced set of them. VMX root mode pretty much just allows the execution of VMX instructions. VMX guest mode allows auxiliary control structures (like vmcs) to back up its execution. The whole idea of trapping various events in the guest mode is to allow the hypervisor to properly emulate the platform. MSRs for example are shared between all modes, but you don’t want the guest to mess with MsRs that could affect VMX root mode, right? That’s why you have the ability to intercept them and manually handle in the root mode. If that’s your question.
It’s the same cpu all the time, it just has different modes of operation. Depending on the mode of execution the CPU has either additional features or otherwise a reduced set of them. VMX root mode pretty much just allows the execution of VMX instructions. VMX guest mode allows auxiliary control structures (like vmcs) to back up its execution. The whole idea of trapping various events in the guest mode is to allow the hypervisor to properly emulate the platform. MSRs for example are shared between all modes, but you don’t want the guest to mess with MsRs that could affect VMX root mode, right? That’s why you have the ability to intercept them and manually handle in the root mode. If that’s your question. -
 [discord] <jamlee7879> Yes, this is exactly the answer I was looking for. Actually, I asked ChatGPT to write example code like this before, but I can't be 100% sure that the MSR registers are shareable. I didn't have a deep enough understanding of virtualization before. Thank you. You've been a great help.
[discord] <jamlee7879> Yes, this is exactly the answer I was looking for. Actually, I asked ChatGPT to write example code like this before, but I can't be 100% sure that the MSR registers are shareable. I didn't have a deep enough understanding of virtualization before. Thank you. You've been a great help. -
 [discord] <jamlee7879> Next, I'll go on to read "Hypervisor From Scratch" in more depth.
[discord] <jamlee7879> Next, I'll go on to read "Hypervisor From Scratch" in more depth. -
 [discord] <jamlee7879> https://tenor.com/view/high-five-patrick-star-spongebob-squarepants-the-patrick-star-show-yes-gif-2201400520488940521High Five Patrick Star GIF - High Five Patrick Star Spongebob Squarepants - Discover & Share GIFs
[discord] <jamlee7879> https://tenor.com/view/high-five-patrick-star-spongebob-squarepants-the-patrick-star-show-yes-gif-2201400520488940521High Five Patrick Star GIF - High Five Patrick Star Spongebob Squarepants - Discover & Share GIFsThe perfect High Five Patrick Star Spongebob Squarepants Animated GIF for your conversation. Discover and Share the best GIFs on Tenor.
- 30 November 2024 (1 messages)
-
Joined.
- 04 Nov 2024 (1)
- 05 Nov 2024 (5)
- 06 Nov 2024 (1)
- 07 Nov 2024 (1)
- 08 Nov 2024 (3)
- 09 Nov 2024 (15)
- 10 Nov 2024 (3)
- 11 Nov 2024 (1)
- 12 Nov 2024 (9)
- 13 Nov 2024 (151)
- 14 Nov 2024 (1)
- 15 Nov 2024 (2)
- 19 Nov 2024 (2)
- 20 Nov 2024 (6)
- 21 Nov 2024 (1)
- 22 Nov 2024 (2)
- 23 Nov 2024 (11)
- 24 Nov 2024 (5)
- 26 Nov 2024 (1)
- 28 Nov 2024 (4)
- 29 Nov 2024 (9)
- 30 Nov 2024 (1)